S01E28 - How to Configure Policy Sets in Microsoft Intune - (I.T)
Published: Feb 11, 2020 by Intune.Training
Steve and Adam discuss how to use the new Policy Sets feature in Microsoft Intune to target groups settings/config/policies to devices/users.
- 00:00 - Intro
- 01:17 - Policy sets overview https://docs.microsoft.com/intune/fundamentals/policy-sets
- 05:40 - Creating policy sets
- 12:49 - Assigning policy sets discussion
- 16:38 - Recap
Policy sets known issues https://docs.microsoft.com/intune/fundamentals/policy-sets#policy-sets-known-issues
Latest Posts
- 00:30 - Spencer Shumway introduction https://twitter.com/spencershum
- 03:25 - Reporting in MEM
- 06:40 - Reporting the new way
- 19:36 - Log analytics
- 31:25 - S02E01 - Easily Create Power BI Reports with the Intune Data Warehouse - (I.T) https://youtu.be/2ICPKRBIews
- 31:44 - Paging vs Export
- 36:54 - Deprecating application inventory in datawarehouse https://docs.microsoft.com/en-us/mem/intune/fundamentals/in-development#intune-data-warehouse-updates https://docs.microsoft.com/en-us/mem/intune/fundamentals/in-development#export-underlying-discovered-apps-list-data
- 41:07 - Available reports/data today
- 45:52 - Roadmap
- 47:02 - Useful resources Initial reporting blog: https://techcommunity.microsoft.com/t5/intune-customer-success/new-reporting-framework-coming-to-intune/ba-p/1009553 2009 Reporting Blog Update: https://techcommunity.microsoft.com/t5/intune-customer-success/microsoft-endpoint-manager-reporting-blog-for-2009-release/ba-p/1685655 2011 Reporting Blog Update: https://techcommunity.microsoft.com/t5/intune-customer-success/introducing-new-policy-reports-amp-more-in-microsoft-endpoint/ba-p/1898027 Getting started with Intune and Log Analytics: https://techcommunity.microsoft.com/t5/device-management-in-microsoft/microsoft-intune-and-azure-log-analytics/ba-p/463145 Intune reporting export API documentation: https://docs.microsoft.com/mem/intune/fundamentals/reports-export-graph-apis Ignite reporting session 2020: https://techcommunity.microsoft.com/t5/video-hub/microsoft-endpoint-manager-reporting-graph-apis-and-log/m-p/1681560 Intune Automated reporting Github: https://github.com/phmehta94/IntuneAutomatedReporting
Sorry about Adam’s keyboard noise and yes, this could be a very short video but we felt like there are people who could use a more in-depth discussion.
- 00:10 - Jóhannes Geir Kristjánsson introduction
- 01:10 - Access on-premises resources from an Azure AD-joined device https://docs.microsoft.com/microsoft-365/business/access-resources
- 02:36 - Windows admins discord http://aka.ms/winadmins
- 04:31 - Migration process
- 06:40 - Blockers
- 10:24 - Lab environment
- 15:50 - Install Azure AD Connect
- 37:57 - Assign licences
- 52:40 - Enable single sign-on
- 1:03:38 - Internal websites and certificates
- 1:09:08 - Wrap up
- 02:12 - S01E07 - Publishing Win32 Applications using Microsoft Intune https://youtu.be/x-RMjhzGXxA
- 02:54 - Win32 Application Supersedence https://docs.microsoft.com/mem/intune/apps/apps-win32-supersedence
- 08:54 - Create a Supersedence relationship in Intune
- 13:13 - Supersedence behavior https://docs.microsoft.com/mem/intune/apps/apps-win32-supersedence#supersedence-behavior
- 14:33 - Supersedence limitations https://docs.microsoft.com/en-us/mem/intune/apps/apps-win32-supersedence#supersedence-limitations
- 23:19 - Discussion
- 28:58 - Wrap up
Secure Infrastructure Blog
by the Secure Infrastructure team at Microsoft

Microsoft Endpoint Manager – Intune – Policy Sets & Guided Scenarios
Howdy all! When working through Intune to setup configurations to be deployed to managed devices administrators may need to decide which configurations should be prioritized and applied as a standard across various device types. Historically this is achieved by uniquely assigning each item to respecitive groups and letting Intune deploy the assignments accordingly. In some cases, though, it makes sense to group configurations together and apply them as a unit to help arrive at that minimal required configuration set in a more planned and rational way. Policy Sets help you achieve exactly that. The video linked below walks through Policy Sets and demonstrates their use. The video also introduces Guided Scenarios which are different from Policy Sets but complimentary to Policy Sets.
Share this:
Leave a reply cancel reply, discover more from secure infrastructure blog.
Subscribe now to keep reading and get access to the full archive.
Type your email…
Continue reading

an endpoint admin's journal
- Recent Posts
- Popular Posts
- Recent Comments

Deploy Trusted sites zone assignment using Intune
November 6, 2023

Zoom Desktop Client – Download older build versions from Zoom
October 31, 2023

Uninstall Teams chat app using remediation script and a configuration profile in Intune
October 30, 2023

Intune Last Check-in date not updating for Windows device
October 25, 2023

How to use Event Viewer to check cause of Blue screen of Death (BSOD)
October 23, 2023
5 Quick Mac OS Terminal commands to make a Mac user life easier

Powershell : Find disabled users and computers in AD
- Active Directory (1)
- Windows (7)
- November 2023
- October 2023
Deploy a set of trusted sites overriding users’ ability to add trusted sites themselves. To acheive this, an Intune configuration profile Trusted site zone assignment can be deployed to devices/users group as required.
Login to Intune Portal and navigate to: Devices > Windows > Configuration Profiles .
Hit the Create button and Select New policy

From the Create a profile menu, select Windows 10 and later for Platform , Templates for Profile type. Select Administrative templates and click Create .

Give the profile desired name and click Next .

In Configurations settings, select Computer Configuration and search for keyword “ Site to Zone “, Site to Zone Assignment List setting will be listed under search results. Go ahead click on it to Select it.

Once selected, a Site to Zone Assignment List page will appear on right side explaining different zones and values required for these zone for setup. Since this profile is being used for trusted sites, we will use the Value “2” . Go ahead and select Enabled button and start entering the trusted sites as required. please ensure to set each value to “2” . See example below:
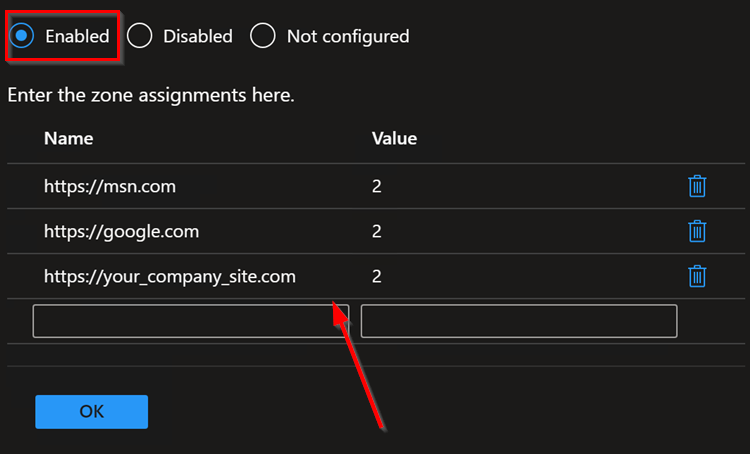
Once done adding the list of sites, click OK to close it and Hit Next on Configuration settings page.
Add Scope tags if needed.
Under Assignments , Click Add groups to target the policy deployment to specific group of devices/users. You can also select Add all users / All all devices .
Hit Next . Then Hit Review + Save button to save.
Tags: Intune Windows
You may also like...

[Windows 10] How to completely uninstall Flash player
- Previous Zoom Desktop Client – Download older build versions from Zoom
thanks! I was just looking for this exact solution!
Designing and building your Microsoft Endpoint Manager/Intune environment for Operations
In my work as a modern workplace consultant, I see a lot of Microsoft Endpoint Manager/Intune environments. Many of these environments have been build based on trial and therefore it lacks structure and overview. Most of the environments have been built from scratch, adding and removing functionality until a point was reached where the solution was taken into production.
A solution that works, doesn’t necessarily have to be a solution which is consistent and therefore easily manageable.
Some of the situation I encountered:
- Sometimes Applications are assigned to user groups, sometimes to all devices and sometimes to a device group without any logical reasoning behind it
- Configuration profiles assigned to device groups, user groups, all devices, all users without any logical reasoning behind it
- Not all devices have the same settings applied for unspecific reasons
- When investigating devices have errors or receive conflicting settings
- When device limit for “accounts used to test” are reached
- When a group membership necessary for the solution to work is forgotten to be added
Based on my experience so far, we can solve many issues by introducing consistency. But consistency comes with a price, you’ll have to make some choices and probably lose some flexibility.
In this article I’m going to share a (for me) most common scenario, implementing an MEM/Intune managed Windows 10 device deployed using Autopilot. There are many more scenario’s which are supported by MEM/Intune, and if implemented with the same consistency they will have the same properties.
Disclaimer : This post reflects the status of MEM/Intune and Azure AD as of November 29, 2020. Functionality may change, even right after this post has been published.
Goals for success and designing for Operations
I consider an MEM/Intune solution successful when:
- The requirements of the customer are met
- Device configuration is consistent and error free
- People administering the solution after being handed over know what to do and have a stable environment
- There is a process in place, to introduce changes in a controlled way into the environment.
Note from the field: Modern Workplaces are not the same devices like we used to know. When implementing Modern Workplaces people have to unlearn and let go of some of the principles they have been using for many years. Many concepts require a new view on how to manage (Windows 10) devices, and those are things that you cannot explain in a short note, or during an afternoon. It takes time, and as a Consultant you need to accompany IT Administrators while they relearn this new way of managing devices, you can do this be challenging every decision being made, especially decisions which are backported from their old environment.
Green field versus existing environments
When building new MEM/Intune environments, you have a luxury – you can start implementing your “template” environment and work from there. The challenge is most often in restructuring existing environments to a structured design keeping the impact for the already installed machines to a minimum.
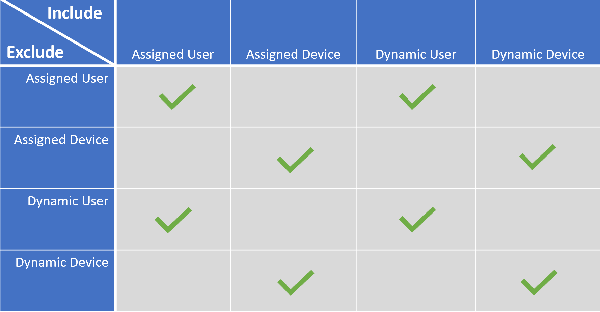
Assigning to users or devices?
In November last year, I wrote the article: “ Intune: Choosing whether to assign to User or Device Groups “, the article explained the case where Microsoft adopted the documentation and give some examples on when to assign to either user or device groups. While the documentation added makes sense, in practical you can really struggle to determine the best setup. Which setup you use doesn’t really matter, as long as it’s consistent and logical.
How I do it, the case for assigning to user groups.
Based on my experience so far, I try to assign to user groups as much as possible . I only see a case for assigning to device based groups in special scenario’s where a user doesn’t log on to the device, like for example the KIOSK scenario. For the rest I can say that assigning to user groups works the best for me.
I’ve also experienced some issues with assignment to Dynamic Device groups, where the group membership update mechanism is not really consistent and sometimes devices don’t end up in the device group while you need them for your settings, another reason for me to use user groups as much as possible.
This does have some disadvantages though, when assigning to a user, you can for example not let that user test on a device with new settings for example. This is because it’s not supported to exclude a device group when you assigned settings to a user group, as detailed in the Microsoft documentation here: Exclude groups from a profile assignment
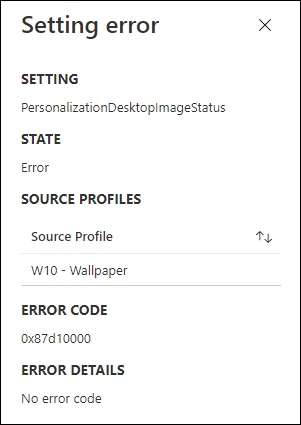
I also had several issues with the System account, which will actual cause some device configuration profiles to give an error since they cannot be applied to the system account successfully. Some examples are setting a wallpaper, or configuring OneDrive settings. Personally I don’t like to see errors, even though they can be ignored as per Microsoft recommendation.
For reference I created an overview of all the settings which can be assigned. You can download the spreadsheet from my Github page .
The following abbreviations are being used:
- UG = User Group
- DG =Device Group
- AU = All Users
- AD = All Devices
- AUD = All Users and Devices
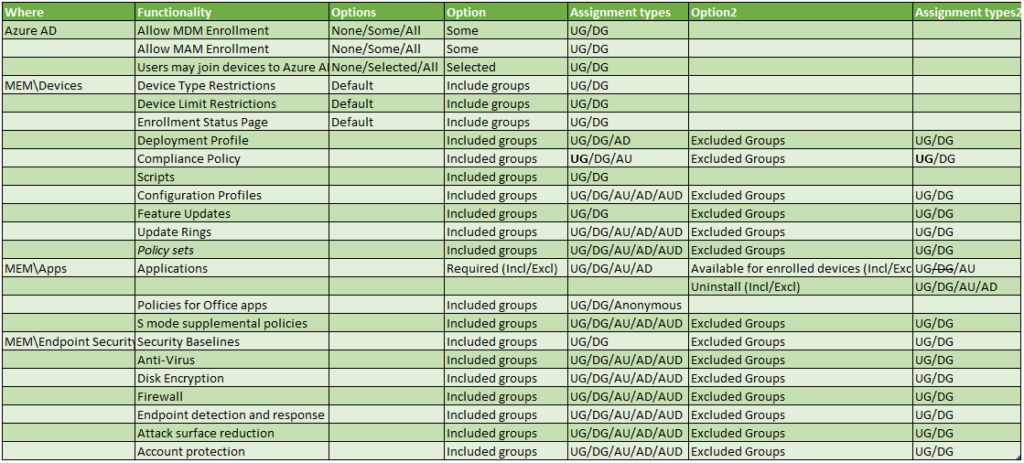
Some of the settings in the table require some extra explanation:
Applications are something special, since they support three methods (Required, Available for enrolled devices and Uninstall). For each of the methods you can define groups to include, or groups to exclude. Even though it’s possible to make assign Available for enrolled devices to a Device Group, it’s only supported when targeting Android Enterprise fully managed devices (COBO) and Android enterprise corporate owned (COPE) devices.
Compliance policies can be set to Device groups, but this has caused some issues for me, some examples below:
- https://microsoftintune.uservoice.com/forums/291681-ideas/suggestions/35775991-intune-duplicate-compliance-policies
- https://techcommunity.microsoft.com/t5/microsoft-intune/device-compliance/m-p/296721
This is the reason, why I always assign my Compliance policies to users, even though this can cause some issues while testing, for example if you want to test something on a device not compliant (like a VM or quick test) you might have issues with Conditional Access if the compliance status is used to determine if access to Office 365 is granted. For this reason I use test accounts.
The other thing I find interesting by making a table you actually see the discrepancies popping up, which are also not documented. Why for example would you only be able to assign a Security baseline to a User/Device Group only while other settings support All Users/All Devices or even All Users and Devices?
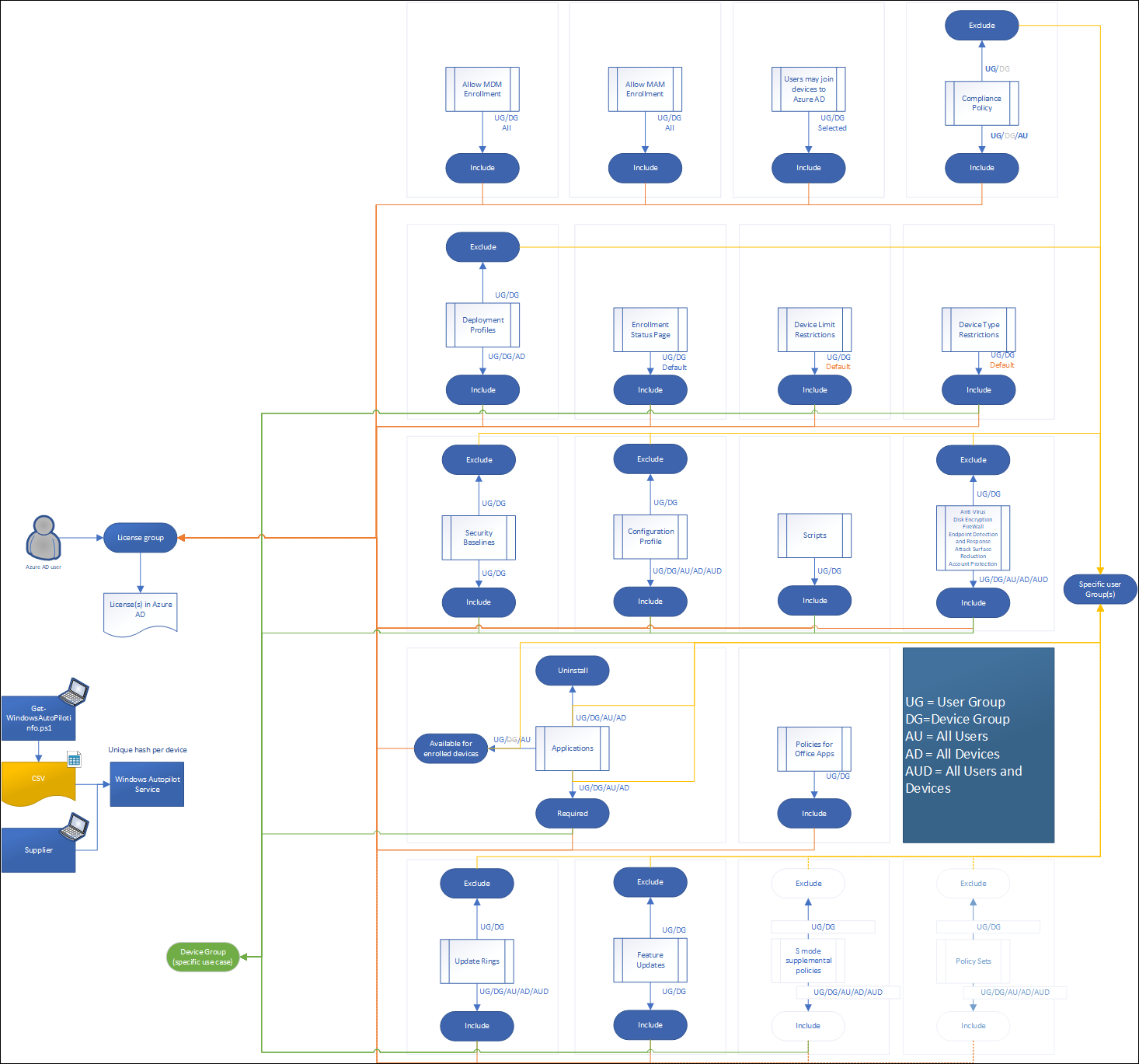
Setting up the environment
There are many settings to found in several locations which eventually determine the way Autopilot works, but also how the device behaves (based on the settings and applications it received).
My starting point is always the user, in this case an account in Azure AD. That users must be licensed in order to use the functionality provided by the Windows 10 Modern Workplace which is managed by MEM/Intune. In most cases this license is based on Microsoft 365, but it can also be a combination of any of the sublicenses of course.
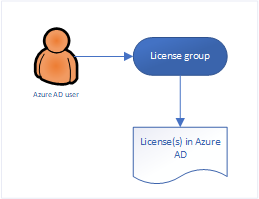
Make sure that you use the license group (which is an Azure AD security group) to provide the necessary licenses via this membership. You can configure this in Azure Active Directory. You can assign one or more product licenses to a group. Azure AD ensures that the licenses are assigned to all members of the group. Any new members who join the group are assigned the appropriate licenses. When they leave the group, those licenses are removed. See: What is group-based licensing in Azure Active Directory? for more information.
If you have more license variations all needing access to MEM/Intune Windows 10 enrollment, you could use group nesting to put users in their corresponding license group, add those groups to another Azure AD group which you use to configure the settings below. There is one remark though when doing this, assigning apps to nested groups is not supported (it works though, but keep this in mind).

Azure AD configuration settings
Within Azure AD we can configure several settings which make up for the experience.
Users may join devices to Azure AD
By default, all users are allowed to join devices to Azure AD, in my opinion if you want more control I would modify this setting to only allow users who are licensed to be able to join devices to Azure AD.
You can find these settings under Devices -> Device settings in the Azure AD portal
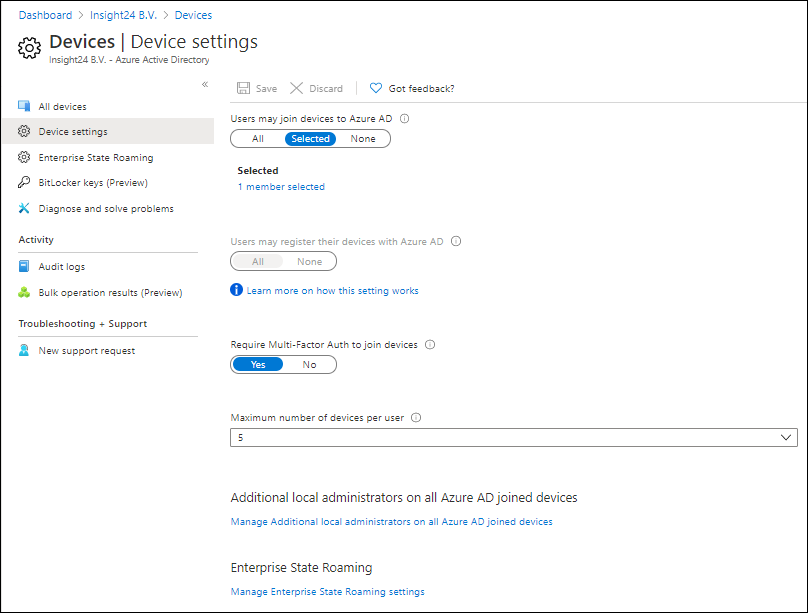
Enterprise State Roaming
By default Enterprise State Roaming is disabled, you can either enable it for All users or for a selection. You can enable the functionality for all users, but since only licensed users will start using it my advice is to use your license group again to give access.
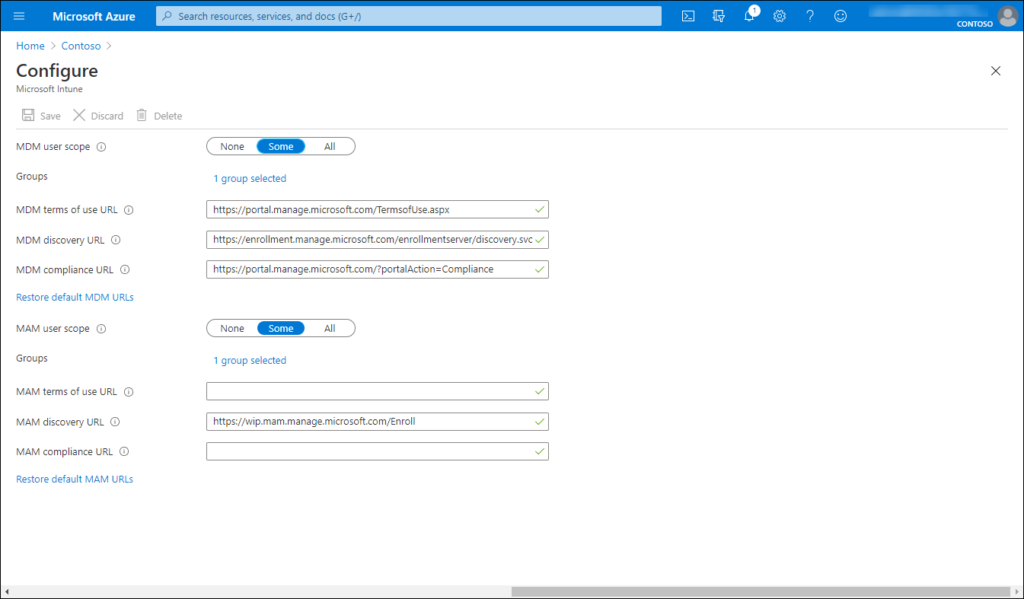
Allow MDM and MAM enrollment
You can configure who is able to do an MDM and MAM enrollment by selecting Mobility (MDM and MAM) in the Azure AD management portal, selecting the Microsoft Intune application and configure the settings as detailed in the figure below.
Also here, make sure to only give the option to do MDM and MAM enrollment to your license group for consistency.
Microsoft Endpoint Manager configuration settings
Within Microsoft Endpoint Manager there are also different settings that you can set
Enrollment restrictions
The Enrollment restrictions are defined using device type restrictions and device limit restrictions. By default, all device types are enabled for enrollment for both Corporate as personally owned devices.
Device limit restrictions can be set between 1 and 15, my suggestion is to keep this the same as the “Maximum number of devices per user setting” in the Azure AD device configuration. Unfortunately you cannot set this to 0, this would have allowed us to create a new device limit restriction, set the value to 5 and assign it to our license group. You might one to do this even how, and set the limit for All users to 1
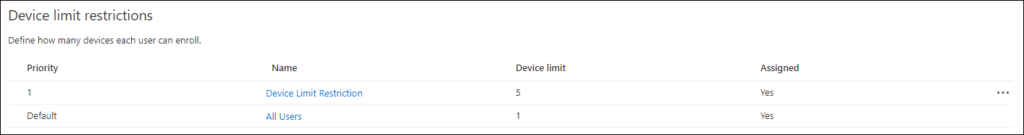
Device type restrictions by default allow all types of registrations, my advice is would be to disable all the scenario’s in the default settings applied to all users, and create a new device type restrictions where you define what you want to support and assign it to the license group.

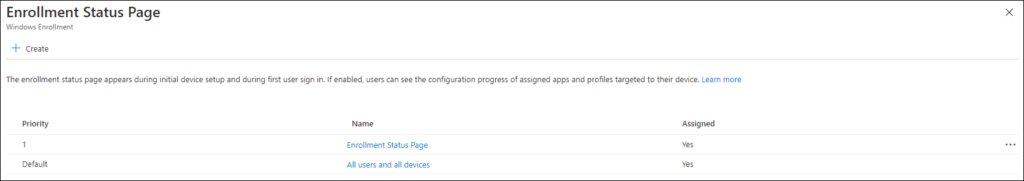
Enrollment Status page
The enrollment status page (ESP) settings can be found under the Windows Enrollment Settings in the Microsoft Endpoint Manager admin center .
The default setting for the ESP is that it’s not configured for All users and all devices, which is nice. It’s now simple to create a new Enrollment Status page setting, and assign it to the license group.
Deployment Profile
The deployment profile settings can also be found under the Windows Enrollment Settings in the Microsoft Endpoint Manager admin center . You should assign these settings to a device group containing the devices which should receive the deployment profile. (Dynamic Device Group with Autopilot devices for example)
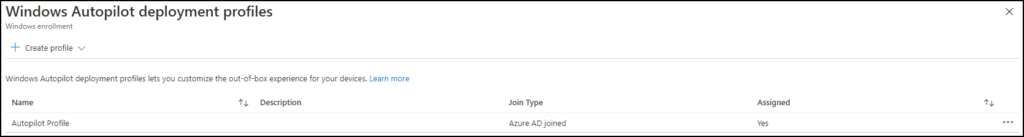
Policy sets
In October last year, I wrote an article about Policy sets: “ What are Intune Policy Sets? ” – even though I think that policy sets can become really handy especially for consistency, there are many caveats with the functionality it provides today. There my advice for now is not to use it, until Microsoft fixes some of the current limitations. See: Policy sets known issues
All the other settings
There are many other settings which can be applied, all support assigning to user groups so they can be assigned to our license group as well.
- Configuration profiles
- Compliance policies
- Feature updates
- Update rings
- Applications
- Policies for office apps
- S mode supplemental policies
- Security baselines
- Disk Encryption
- Endpoint detection and response
- Attack surface reduction
- Account protection
Fixing conflicts and errors
After you have built your environment, spent some time to make sure that you don’t have conflicting settings in your configuration. Even though Microsoft has documented that what happens when conflicts occur , I personally like a situation where each setting is set once conform the defined standard.
The best is to start over with your new standard, you can do this by creating a new group for users and a group with all current users. Also create a new group for devices and a group with current devices. Use these groups to exclude as much as possible (so on the current settings exclude the new user/device group and vice-versa).
Azure AD conditional access
Last week I published a blog article titled: “ Conditional Access demystified: My recommended default set of policies “. One of the mentioned policies was the CAU011-All: Block access for All users except licensed when Browser and Modern Auth Clients-v1.0 which actually blocks all users, except the “License Groups”
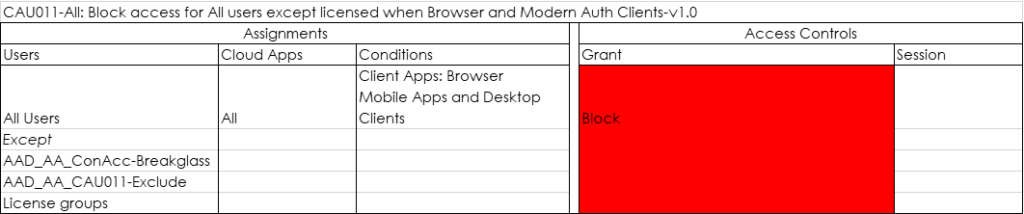
In my opinion this Conditional Access policy, while being very dangerous when implemented wrong can help to make the experience consistent. If you are not licensed, you don’t get functionality.
In the figure below I created an overview of the setup I’m using for my default Autopilot setup within MEM/Intune. As you can see most settings are applied to the license group. We have options to exclude certain setting for specific groups, allow us to test new settings on a subset of users (our test users). If you want to have a closer look, I also made the overview available as PDF for download on my GitHub page.
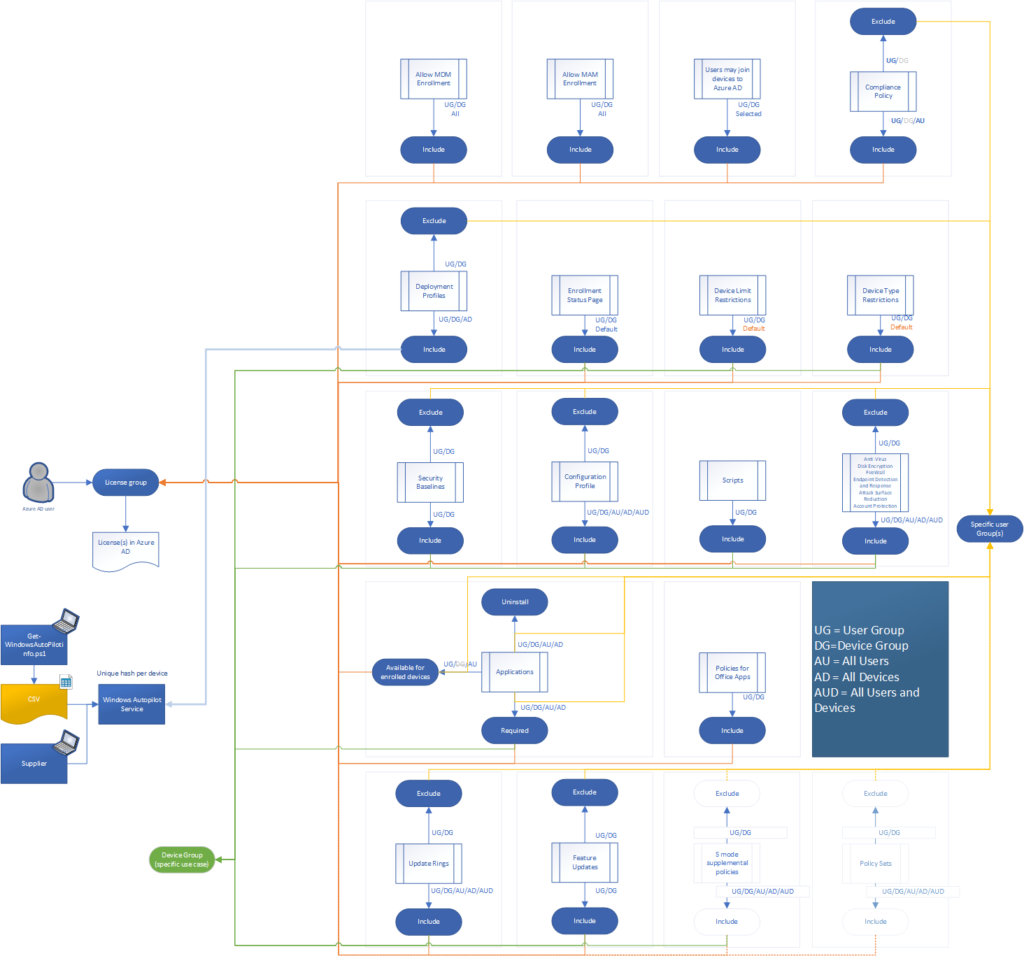
It could be though that I forgot some scenario’s which require you to use assignment towards Device Groups. If so, please leave a comment. I would be very curious to find out these use cases.
Exclude groups from a profile assignment – https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-assign#exclude-groups-from-a-profile-assignment
Microsoft Intune planning guide – https://docs.microsoft.com/en-us/mem/intune/fundamentals/intune-planning-guide
Common questions and answers with device policies and profiles in Microsoft Intune – https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-troubleshoot
How Application Context, Assignment and Exclusions Work in Intune – https://techcommunity.microsoft.com/t5/intune-customer-success/how-application-context-assignment-and-exclusions-work-in-intune/ba-p/1073357
7 thoughts on “ Designing and building your Microsoft Endpoint Manager/Intune environment for Operations ”
- Pingback: Intune: Choosing whether to assign to User or Device Groups | Modern Workplace Blog
Thanks for the write up. This will give some good insight as to how to make things consistent in your environment. There are just some things that I’ve found that don’t line up with what you recommend as far as user vs device assignments as I’m in the middle of a mostly green field deployment for my company.
It’s really dependent on the feature or setting. For instance, online store apps can only be assigned to users. Disk Encryption must happen prior to first user sign in during ESP so if settings at all differ from what Windows does by default they therefore need to be assigned to devices so it happens between device and user ESP. As for certificates, do you recommend that to users as well, or do you use device groups?
Feature Update (Preview) can only be assigned to devices (per MSFT docs). Which then you have to be careful not to mix your update rings with user groups and feature updates with devices. Either use only Update Rings as user assignments and no Feature Update, or use both modules but assign to device groups.
While I agree using user groups makes the most sense for most things, there are certain situations that device groups are the only way possible.
- Pingback: Designing and configuring compliance policies for your Windows Modern Workplace using Microsoft Endpoint Manager | Modern Workplace Blog
- Pingback: A first look at filtering when assigning apps, compliance policies and configuration profiles in Microsoft Endpoint Manager | Modern Workplace Blog
- Pingback: A first look at filtering when assigning apps, compliance policies and configuration profiles in Microsoft Endpoint Manager - Tech Daily Chronicle
- Pingback: MDM policy processing on Windows 10 with Microsoft Endpoint Manager, a closer look | Modern Workplace Blog
- Pingback: MDM policy processing on Windows 10 with Microsoft Endpoint Manager, a closer look - Tech Daily Chronicle

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Privacy Overview
All about Microsoft Intune
Peter blogs about Microsoft Intune, Microsoft Intune Suite, Windows Autopilot, Configuration Manager and more
Using filters for assigning apps, policies and profiles to specific devices
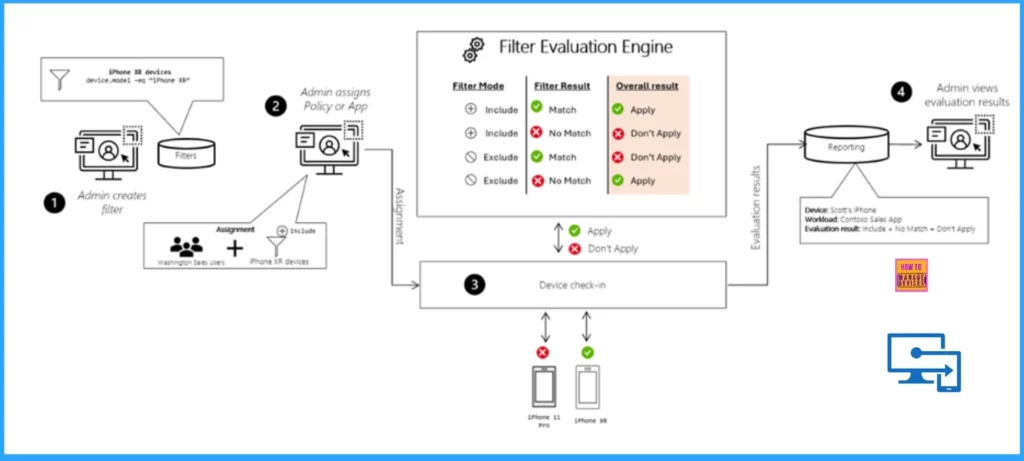
This week is all about filters. Filters are basically a super-set of the functionalities of applicability rules – already available for a while for Windows 10 – and are a great new addition to assigning apps policies and profiles to specific devices. Those specific devices are only the devices that meet the specific properties that are configured in the filters. A great method for specifically targeting apps, policies and profiles. This post starts with a short introduction about filters, followed with information about creating and using filters (including the steps for using and creating filters). This post ends with the administrator experience with filters.
Introducing filters
For device configuration profiles for Windows 10 devices it was already possible to use applicability rules. Applicability rules would enable the IT administrator to assign or not assign the profile based on the version or the edition of Windows 10. Filters could be seen as the enhanced platform independent version of those applicability rules. The main enhancements are that filters can be used for all the different platforms, filters can be used for apps, policies and profiles, and filters can be used with many different Intune device properties. Besides that, filters can be used in combination with any Azure AD group assignment and even in combination with the default All users or All device s groups. In that case the targeted devices of the assignment will be dynamically filtered based on the configured device properties.
One of the best characteristics of filters is the reusability. Unlike applicability rules – that are created per profile – filters are created once and can be reused for different objects of apps, policies and profiles. That enables the IT administrator to create a filter – with an expression that for example filters personal devices – for usage across different assignments. During the check-in of the device, the filter evaluation engine will determine the applicability of the assignment. The expression in a filter can be created by using different Intune device properties. Those properties are available for all the managed devices in Intune. There is – however – a slight difference in availability of the different properties for devices of different platforms. The table below provides a quick overview of the available properties, the shape of the value and the supported platforms.
| Device name | deviceName | String | Android device administrator, Android Enterprise, iOS/iPadOS, macOS, Windows 10 |
| Device manufacturer | manufacturer | String | |
| Device model | model | String | |
| Device category | deviceCategory | String | |
| Platform version | osVersion | String | |
| Rooted/ jailbroken | isRooted | Selection | |
| Device ownership | deviceOwnership | Selection | |
| Enrollment profile name | enrollmentProfileName | String | iOS/iPadOS, Windows 10 |
| Operating system SKU | operatingSystemSKU | String | Windows 10 |
Note : For the correct string values, of the different device properties, simply verify the different columns in the devices overview of the Microsoft Endpoint Manager admin center.
Creating filters
Filters are reusable. That is an important starting point for creating filters, as filters are not related to a specific assignment. That means that filters can be created as separate configurations. The following six steps walk through the required steps for creating a filter with multiple expressions.
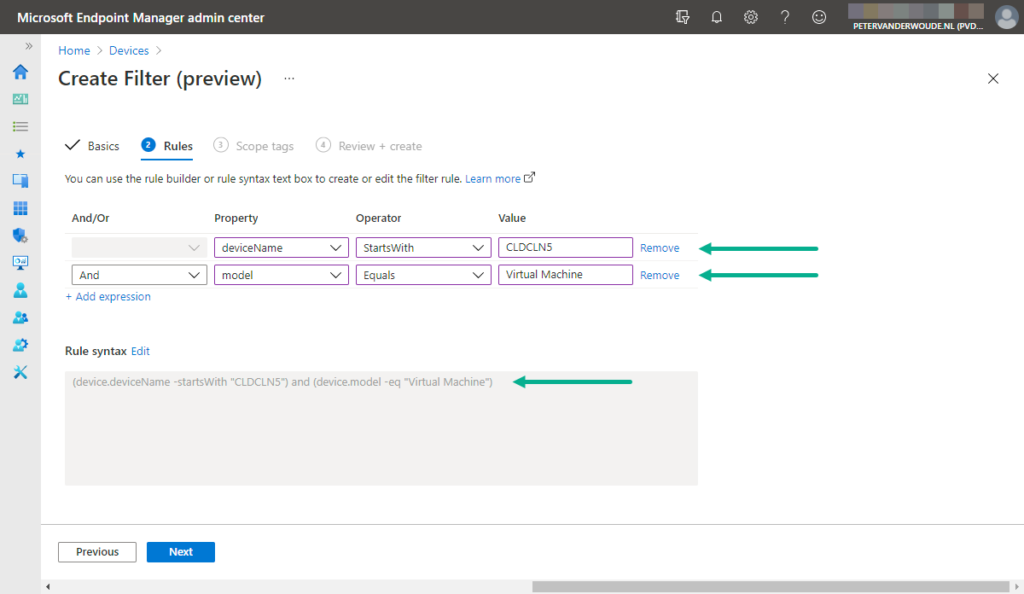
Note : The steps below show the creation of a filter for the Windows 10 virtual machines in Azure. In this example, those devices can be filtered by using a combination of the Device name and Model .
Important : At the moment of writing filters are still in preview. That requires the IT administrator to specifically enable filters for evaluation. That can be achieved by clicking at the purple bar on top of the page at step 2 below an switching the slider with Filters (preview) to On .
- Open the Microsoft Endpoint Manager admin center portal and navigate Devices > Filters (alternative roads to the same configuration are Apps > Filters or Tenant admin > Filters )
- On the Devices | Overview page, click Create to open the Create Filter wizard
- On the Basics page, provide the following information and click Next
- Filter name : Specify a unique name to distinguish the filter from other filters
- Description : (Optional) Specify a description to further explain the usage of the filter
- Platform : Select Windows 10 as the platform
- On the Rules page, as shown below in Figure 1, create the following configuration and click Next
- And/Or : Not applicable
- Property : Select deviceName as value
- Operator : Select StartsWith as value
- Value : Specify the required string as value
- And/Or : Select And as value
- Property : Select model as value
- Operator : Select Equals as value
- Value : Specify Virtual Machine as value
- On the Scope tags page, configure the required scope tags and click Next
- On the Review + create page, verify the configuration and click Create
Using filters
Filters are used on top of the normal group assignments. That means that an IT administrator still configures the group assignment and combines that with the created filter, to filter the applicable devices. Also, filters can only be used on top of the included groups of an assignment and not on top of the excluded groups of an assignment. That actually makes perfect sense, as a filter already makes sure that only the specifically filtered devices will eventually receive the assignment. Besides that, using filters also provides more flexibility, as it enables mixing user groups with device properties. Excluding groups can, however, still be useful for filtering users from a user group assignment.
So, in general, the include and exclude groups are still the starting point of an assignment. Using filters on top of that enables the IT administrator to only target the required devices. An example of using filters in an assignment is described in the following six steps.
Note : The steps below show the usage of a filter for an existing app assignment. The idea and steps are similar when configuring a filter with a new app app assignment or any policy or profile assignment.
- Open the Microsoft Endpoint Manager admin center portal and navigate Apps > Windows > Select the app that should be assigned to only specific Windows 10 devices > Properties
- In the properties of the select app, click Edit with Assignments
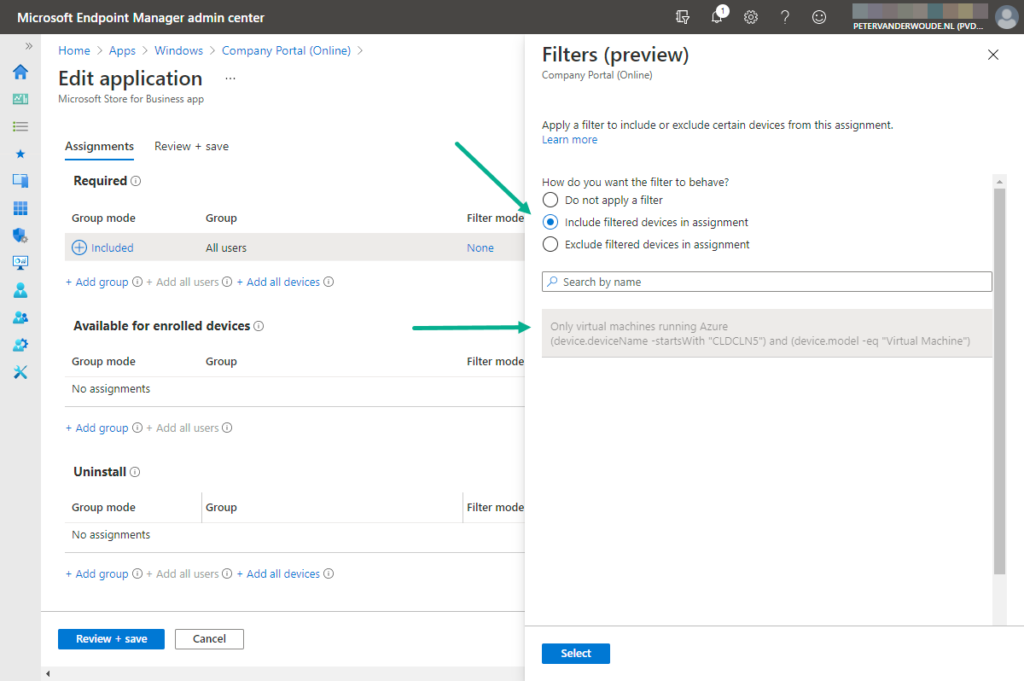
- On the Edit application page, as shown below in Figure 2, create the following configuration and click Review + save
- Group mode : Select Included as value
- Group : Select the required group of users or devices as value
- Filter mode : Select Include filtered devices in assignment as value
- Filter : Select the just created filters as value
Note : The Filters page is shown when clicking on either None with Filter mode or None with Filter . In both cases the IT administrator must configure both settings at the same time.
Experiencing filters
The best place to look at the results of filters is not the device of the user, but the Microsoft Endpoint Manager admin center. That provides the IT administrator with two different views (or reports) with information about the evaluation of filters. The first view is available as the Filter evaluation monitor in the overview of a specific device. The second view is available by clicking on Filters evaluated in the Device install status monitor. That provides the Filter evaluation blade that is shown below in Figure 3. That blade provides an overview about the evaluated filter, the status of the evaluation and the details that are used for that evaluation. On top of the blade is the actual result of the filter on the assignment. In the example below, the app is not offered as the evaluation is not a match.
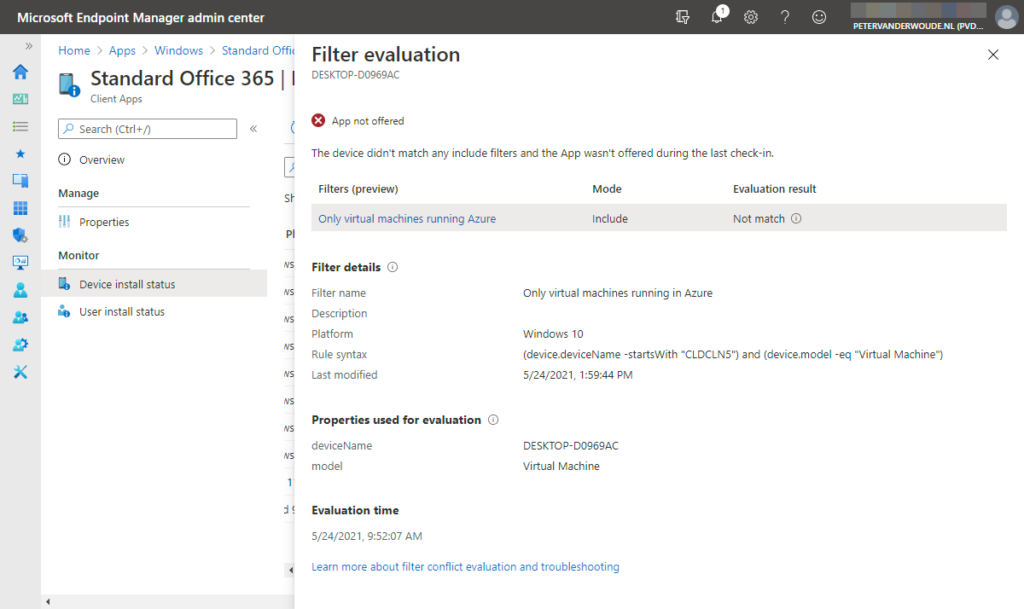
More information
For more information about using filters in Microsoft Intune, refer to the following docs.
- Use Microsoft Endpoint Manager filters to target apps and policies to specific devices
- Filters Public Preview – Overview and Known Issues
- Use filters (preview) when assigning your apps, policies, and profiles in Microsoft Endpoint Manager
- Device properties, operators, and rule editing when creating filters in Microsoft Endpoint Manager
- List of platforms, policies, and app types supported by filters in Microsoft Endpoint Manager
- Filter reports and troubleshooting in Microsoft Endpoint Manager
Share this:
- Click to share on Twitter (Opens in new window)
- Click to share on Facebook (Opens in new window)
- Click to share on LinkedIn (Opens in new window)
- Click to share on Reddit (Opens in new window)
10 thoughts on “Using filters for assigning apps, policies and profiles to specific devices”
It seems that filters is not available for Win32-apps? Until there is support for Win32-apps, this feature is pretty useless at the moment. at least for us. Too bad.
Filters are already available for the assignments of Win32 apps.
Regards, Peter
Hm, interesting. I could’ve sworn it wasn’t there when I looked. But now it is. ? Maybe it just took a little longer, or I needed to log out of Endpoint Managemt to activate it. Sorry, and thanks!
No problem Pär! Enjoy the possibilities!
I have one query on feature “Enable Filters Public Preview”, Basically I would like to know if we can see from admin logs or any other source that who has enable this feature from Intune console tenant ? Or do we have to depend only on Microsoft ?
Hi Yogesh, I haven’t looked at that specific message, but I would expect it to be in the Audit logs. Regards, Peter
Hi. Is it possible to apply two filters in a compliance policy? So I want to have a filter that rules all Mac OS devices and one filter that includes that includes all windows devices azure ad joined. Then to create a compliance policy set to a group of users and exclude both filters above, so the policy is applied to only windows users as well as to not personal devices not Azure AD joined. Can I include two filters? Thank you
Hi Dorjana, In that case you need to combine those filter to a single filter. Regards, Peter
Is it possible to apply a device filter to an application protection policy? I am only seeing where it allows me to apply a managed apps filter but I want to use a managed device filter. Can you even work with devices in an application protection policy or can that only be applied to users/group?
No, that’s not possible. It’s a different service that contains different properties. See for more information also: https://learn.microsoft.com/en-us/mem/intune/fundamentals/filters Regards, Peter
Leave a Comment Cancel reply
Notify me of follow-up comments by email.
Notify me of new posts by email.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
How to use Intune Filter cpuArchitecture Device Property for App and Policy Assignments
Let’s discuss using Intune Filter cpuArchitecture Device Property for App and Policy Assignments. Device filters now support the cpuArchitecture property, allowing organizations to specify processor types such as AMD64, Arm64, and x86 in their device management platforms.
This enhancement enables more control over the app and policy assignments. It ensures that software and settings are only sent to devices with the correct processor typ e. This feature makes management easier, improves compatibility , and ensures that resources are used efficiently across different devices.
The cpuArchitecture filter device property is a newly introduced feature for managing app and policy assignments on Windows and macOS devices. It allows IT administrators to simplify software deployments, compliance policies, and configuration profiles based on the architecture of a device’s processor.
In this post, you will find all the details about the new device filters that bring cpuArchitecture support for AMD64, Arm64, and x86 processors in Intune. All the details are explained below.

Sign up to get the best of How To Manage Devices straight to your inbox!

Table of Contents
What is the new cpuarchitecture filter device property.
The new cpuArchitecture filter device property allows you to filter app and policy assignments based on the processor architecture of Windows and macOS devices. You can specify whether assignments should apply to devices with AMD64, Arm64, or x86 processors.
Which Devices Support the cpuArchitecture Filter?
The cpuArchitecture filter is available for Windows and macOS devices.

What Processor Architectures can be Filtered with this Property?
The filter supports processor architectures such as AMD64, Arm64, and x86 .
Device Filters Bring cpuArchitecture AMD64 Arm64 x86 in Intune
This Device filter feature is beneficial when you have devices with different types of processors, like ARM and x86. It lets you manage and deploy software and settings more accurately, ensuring they are only sent to devices that can use them properly.
Read More – What’s New in Microsoft Intune August 2024 Update
- Enhanced Reporting Multi-Administrative Approval Microsoft Home Page via Intune August 2024 Update
- Microsoft Intune 2407 New Features Early July Update
- Managing Activation Lock on Apple Devices with Intune
- How to Use Intune Assignment Filters Comparison Property gt ge lt le with OS Version
How to Create a Filter
Filters are available for devices enrolled in Intune , which Intune manages, and for apps also managed by Intune. Managed apps are used in mobile application management ( MAM ) scenarios, where apps are managed on devices not enrolled in Intune .
- Sign in to the Microsoft Intune admin portal
- Managed Devices – These devices are managed by Intune, allowing for comprehensive control and configuration.
- Managed Apps – These are applications that Intune manages, including those deployed to enrolled devices.
Filters improve flexibility and precision when assigning Intune policies and apps. They help you target managed devices and apps based on specific properties , like device type or version.
You can use filters to include or exclude devices or apps in specific groups according to your criteria. Filters can be customized to match various properties and applied repeatedly to include or exclude items as needed in different scenarios.
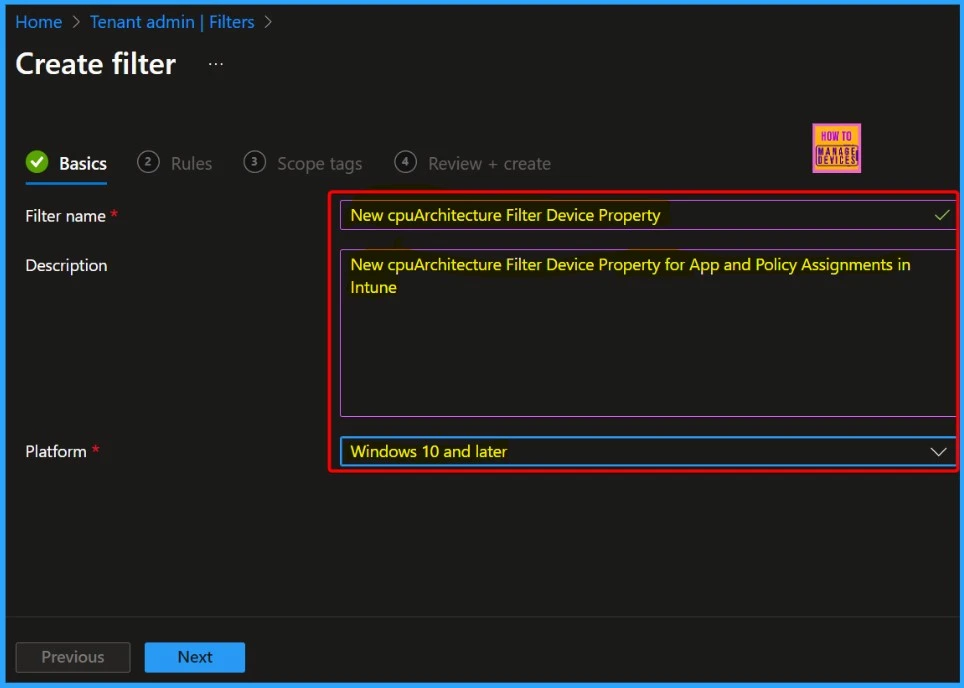
- Filter Name – Enter a descriptive name for the filter.
- Description – Enter a description for the filter.
- Platform – Select your platform.
- Enforce Users to use Intune Approved Apps with App Protection Policies using Conditional Access Policies
- Issue on Minimum PIN Length for Startup in Disk Encryption Policies in Intune
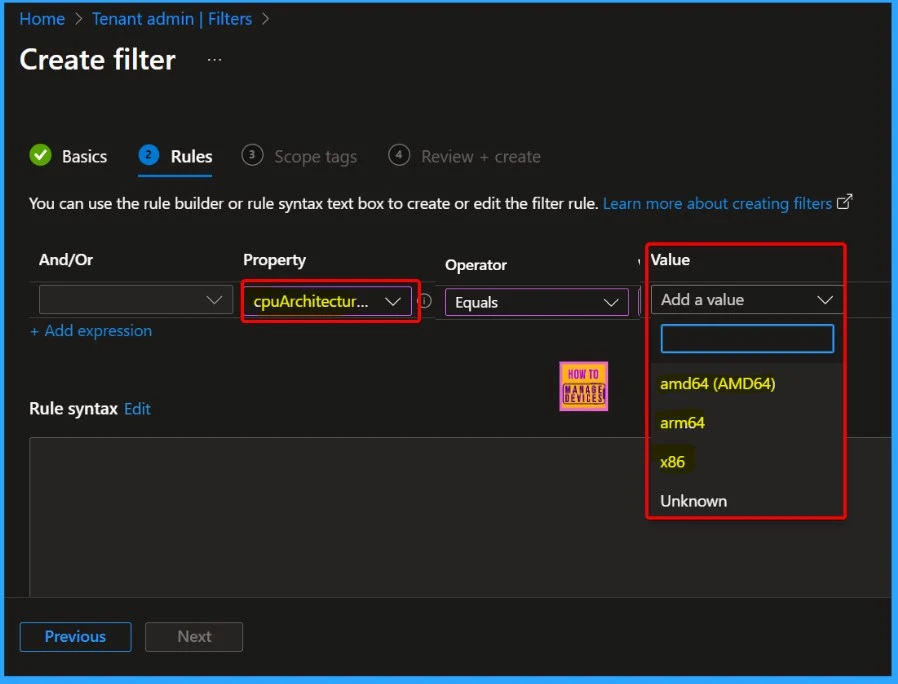
You have two rule creation options in the Rules tab: the Rule Builder and the Rule Syntax . Rule Builder is a user-friendly graphical interface that allows you to create rules by selecting menu options and criteria . It’s designed for ease of use, so you can set up rules without writing code.
Rule Syntax —This method involves writing rules using a specific syntax or language. It offers more flexibility and precision for advanced users who are comfortable with coding and need to create more complex rules than may be possible with the rule builder.
| And/or | Property | Operator | Value |
|---|---|---|---|
| Equals NotEquals In NotIn | amd64 (AMD64) arm64 x86 Unknown |
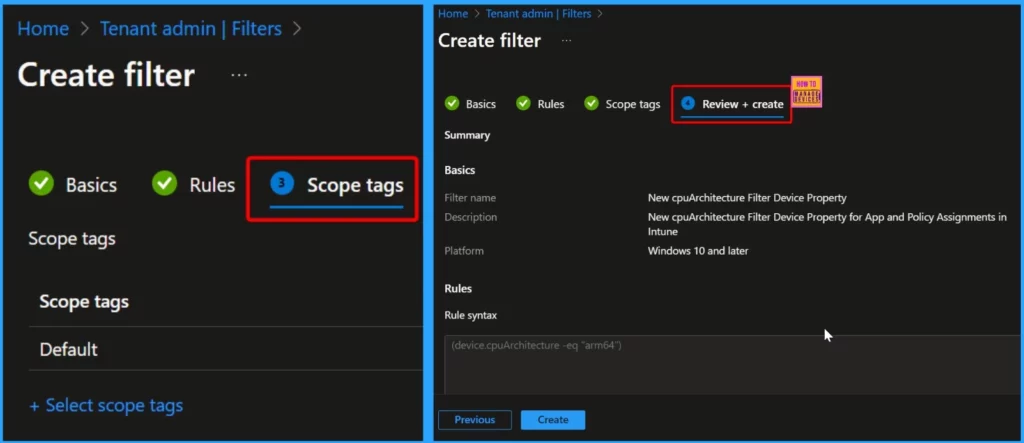
Scope tags (optional) help you assign a tag to limit the profile to specific IT groups. In the Review + Create section, check your settings. When you select Create, your changes are saved , and the filter is created. The new filter will also appear in the list of filters.
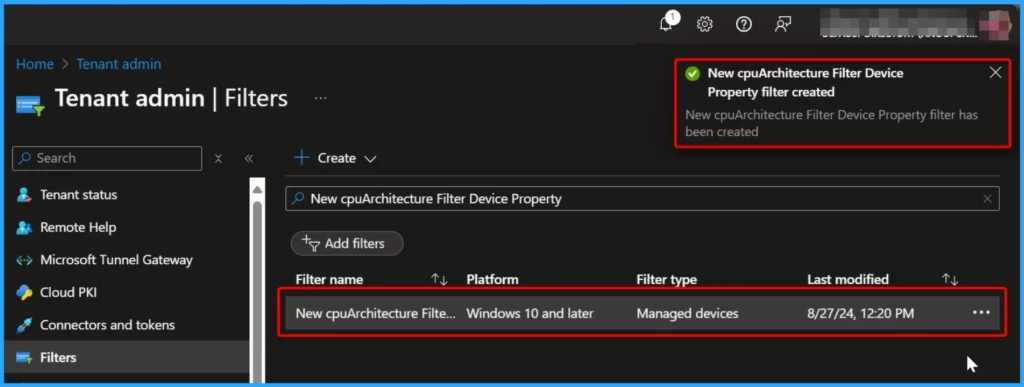
The image below demonstrates that the new cpuArchitecture filter device property for app and policy assignments in Intune has been successfully created.
- Microsoft Added New 160+ Apps on Intune Enterprise App Catalog
- MS Intune Stop Supporting User Enrollment with Company Portal for iOS iPadOS
Device Properties for Managed Device Filter Rules cpuarchitecture
Based on the cpuarchitecture , you can use the following device properties in your managed device filter rules. You can use these properties to filter devices based on their CPU architecture in your Intune -managed device rules.
| cpuArchitecture | Operator Options |
|---|---|
| – Windows | -eq, -ne, -in, -notIn |
| – Windows | -eq, -ne, -in, -notIn |
| – Windows | -eq, -ne, -in, -notIn |
| – Windows | -eq, -ne, -in, -notIn |
| x64 – | -eq, -ne, -in, -notIn |
| arm64 – | -eq, -ne, -in, -notIn |
| unknown – | -eq, -ne, -in, -notIn |
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp .
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
Leave a Comment Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Create a compliance policy in Microsoft Intune
- 9 contributors
Device compliance policies are a key feature when using Intune to protect your organization's resources. In Intune, you can create rules and settings that devices must meet to be considered compliant, such as a minimum OS version. If the device isn't compliant, you can then block access to data and resources using Conditional Access .
You can also take actions for noncompliance, such as sending a notification email to the user. For an overview of what compliance policies do, and how they're used, see get started with device compliance .
This article:
- Lists the prerequisites and steps to create a compliancy policy.
- Shows you how to assign the policy to your user and device groups.
- Describes other features, including scope tags to "filter" your policies, and steps you can take on devices that aren't compliant.
- Lists the check-in refresh cycle times when devices receive policy updates.
Before you begin
To use device compliance policies, be sure you:
Use the following subscriptions:
- If you use Conditional Access, then you need Microsoft Entra ID P1 or P2 edition. Microsoft Entra pricing lists what you get with the different editions. Intune compliance doesn't require Microsoft Entra ID.
Use a supported platform:
- Android device administrator
- Android AOSP
- Android Enterprise
- Linux - Ubuntu Desktop, version 20.04 LTS and 22.04 LTS
- Windows 10/11
Microsoft Intune is ending support for Android device administrator management on devices with access to Google Mobile Services (GMS) on December 31, 2024. After that date, device enrollment, technical support, bug fixes, and security fixes will be unavailable. If you currently use device administrator management, we recommend switching to another Android management option in Intune before support ends. For more information, see Ending support for Android device administrator on GMS devices .
Enroll devices in Intune (required to see the compliance status)
Enroll devices to one user, or enroll without a primary user. Single devices can't be enrolled to multiple users.
In addition to compliance settings that are built in to Intune, the following platforms support adding custom compliance settings to compliance policies:
- Ubuntu Desktop, version 20.04 LTS and 22.04 LTS
Before you can add custom settings, you must prepare a custom JSON file that defines the settings you want to base your custom compliance on, and a script that runs on devices to detect the settings defined in the JSON.
For more information about using custom compliance settings, including supported platforms, prerequisites, and how to configure the Custom Compliance category while creating a policy, see Use custom compliance settings .
Create the policy
Sign in to the Microsoft Intune admin center .
Go to Devices > Compliance and choose Create policy .
Select a Platform for this policy from the following options:
- Android (AOSP)
- Linux - (Ubuntu Desktop, version 20.04 LTS and 22.04 LTS, RedHat Enterprise Linux 8, or RedHat Enterprise Linux 9)
- Windows 8.1 and later
- Windows 10 and later
For Android Enterprise , you also select a Policy type :
- Fully managed, dedicated, and corporate-owned work profile
- Personally-owned work profile
Then select Create to open the configuration page.
On the Basics tab, specify a Name that helps you identify them later. For example, a good policy name is Mark iOS/iPadOS jailbroken devices as not compliant .
You can also choose to specify a Description .
On the Compliance settings tab, expand the available categories, and configure settings for your policy. The following articles describe the available compliance settings for each platform:
Add custom settings to policies for supported platforms.
This is an optional step that’s supported only for the following platforms:
- Windows 10/11 Before you can add custom settings to a policy, you must have uploaded a detection script to Intune, and have ready a JSON file that defines the settings you want to use for compliance. See Custom compliance settings .
On the Compliance settings page, expand the Custom Compliance category:
For Windows :
- On the Compliance settings page, expand Custom Compliance and set Custom compliance to Require .
- For Select your discovery script , select Click to select , and then specify a script that’s been previously added to the Microsoft Intune admin center. This script must be uploaded before you begin to create the policy.
- For Upload and validate the JSON file with your custom compliance settings , select the folder icon and then locate and add the JSON file for Windows that you want to use with this policy. For assistance with the JSON, see Create a JSON for custom compliance settings .
For Linux :
- On the Compliance settings page, select Add settings to open the Settings picker pane.
- Select Custom Compliance , and then select 8.
- Back on the Compliance settings page, select the toggle for Require Custom Compliance to change it to be True .
- For Select your discovery script , select Set reusable settings , and then specify a script that’s been previously added to the Microsoft Intune admin center. This script must have been uploaded before you begin to create the policy.
- For Select your rules file , select the folder icon and then locate and add the JSON file for Linux that you want to use with this policy. For assistance with the JSON, see Create a JSON for custom compliance settings .
The JSON you enter is validated and any problems are displayed. After validation of the JSON contents, the rules from the JSON are displayed in table format.
On the Actions for noncompliance tab, specify a sequence of actions to apply automatically to devices that don't meet this compliance policy.
You can add multiple actions, and configure schedules and details for some actions. For example, you might change the schedule of the default action Mark device noncompliant to occur after one day. You can then add an action to send an email to the user when the device isn't compliant to warn them of that status. You can also add actions that lock or retire devices that remain noncompliant.
For information about the actions you can configure, see Add actions for noncompliant devices , including how to create notification emails to send to your users.
Another example includes the use of Locations where you add at least one location to a compliance policy. In this case, the default action for noncompliance applies when you select at least one location. If the device isn't connected to any of the selected locations, it's considered not compliant. You can configure the schedule to give your users a grace period, such as one day.
On the Scope tags tab, select tags to help filter policies to specific groups, such as US-NC IT Team or JohnGlenn_ITDepartment . After you add the settings, you can also add a scope tag to your compliance policies.
For information on using scope tags, see Use scope tags to filter policies .
On the Assignments tab, assign the policy to your groups.
Select + Select groups to include and then assign the policy to one or more groups. The policy will apply to these groups when you save the policy after the next step.
Policies for Linux don't support user-based assignments and can only be assigned to device groups.
On the Review + create tab, review the settings and select Create when ready to save the compliance policy.
The users or devices targeted by your policy are evaluated for compliance when they check in with Intune.
Refresh cycle times
Intune uses different refresh cycles to check for updates to compliance policies. If the device recently enrolled, the check-in runs more frequently. Policy and profile refresh cycles lists the estimated refresh times.
At any time, users can open the Company Portal app, and sync the device to immediately check for policy updates.
Assign an InGracePeriod status
The InGracePeriod status for a compliance policy is a value. This value is determined by the combination of a device's grace period, and a device's actual status for that compliance policy.
Specifically, if a device has a NonCompliant status for an assigned compliance policy, and:
- The device has no grace period assigned to it, then the assigned value for the compliance policy is NonCompliant
- The device has a grace period that's expired, then the assigned value for the compliance policy is NonCompliant
- The device has a grace period that's in the future, then the assigned value for the compliance policy is InGracePeriod
The following table summarizes these points:
| Actual compliance status | Value of assigned grace period | Effective compliance status |
|---|---|---|
| NonCompliant | No grace period assigned | NonCompliant |
| NonCompliant | Yesterday's date | NonCompliant |
| NonCompliant | Tomorrow's date | InGracePeriod |
For more information about monitoring device compliance policies, see Monitor Intune Device compliance policies .
Assign a resulting compliance policy status
If a device has multiple compliance policies, and the device has different compliance statuses for two or more of the assigned compliance policies, then a single resulting compliance status is assigned. This assignment is based on a conceptual severity level assigned to each compliance status. Each compliance status has the following severity level:
| Status | Severity |
|---|---|
| Unknown | 1 |
| NotApplicable | 2 |
| Compliant | 3 |
| InGracePeriod | 4 |
| NonCompliant | 5 |
| Error | 6 |
When a device has multiple compliance policies, then the highest severity level of all the policies is assigned to that device.
For example, a device has three compliance policies assigned to it: one Unknown status (severity = 1), one Compliant status (severity = 3), and one InGracePeriod status (severity = 4). The InGracePeriod status has the highest severity level. So, all three policies have the InGracePeriod compliance status.
Monitor your policies .
Was this page helpful?
Additional resources

IMAGES
VIDEO
COMMENTS
Creating a policy set enables you to select many different objects at once, and assign them from a single place. As your organization changes, you can revisit a policy set to add or remove its objects and assignments. You can use a policy set to associate and assign existing objects, such as apps, policies, and VPNs in a single package.
Open the Microsoft Endpoint Manager admin center portal and navigate to Devices > Policy sets to open the Policy sets blade. On the Policy sets blade, select Policy sets and click Create to open the Create a policy set wizard. On the Basics page, provide the following information (see Figure 1) and click Next: Application management.
In your given example, the policy set named Policy_Set1 is assigned to All Devices excluding Kiosk. This implies that all policies within the set (CP_setting1, CP_setting2, CP_setting3) will be applied to all devices except those designated as Kiosk. The individual assignments of policies within the set are overridden by the policy set assignment.
When the policy set is created, you can assign the policy set from a single place in the Microsoft Intune admin center. For more information, go to Use policy sets to group collections of management objects in Microsoft Intune. Scope tags are a great way to filter policies to specific groups, such as US-NC IT Team or JohnGlenn_ITDepartment.
In the Intune admin center, you can use the built-in reporting features to help find and resolve conflicts. In the Intune admin center, select Devices > Manage devices > Configuration. In the list, select the policy you created using the settings catalog. The Profile type column shows Settings Catalog:
The policy set functionality can be found under Devices in the new setup of the Intune portal. Go to Devices and choose Policy sets (Preview) Policy Sets. You can create a policy set, by clicking on "+ Create" on the Policy sets page, which will start a wizard guiding you to creating your first policy set. Create Policy Set Wizard.
Steve and Adam discuss how to use the new Policy Sets feature in Microsoft Intune to target groups settings/config/policies to devices/users.00:00 - Intro01:...
To access policy sets in Microsoft Intune, navigate to the In Tune button in your web browser. Scroll down to find the "Policy Sets" section. If you don't see it immediately, don't worry. It may take a moment to load, especially if you're using the preview version. Once loaded, you can start exploring policy sets and planning your ...
S01E28 - How to Configure Policy Sets in Microsoft Intune - (I.T) Published: Feb 11, 2020 by Intune.Training. Steve and Adam discuss how to use the new Policy Sets feature in Microsoft Intune to target groups settings/config/policies to devices/users. 00:00 - Intro. 01:17 - Policy sets overview.
Historically this is achieved by uniquely assigning each item to respecitive groups and letting Intune deploy the assignments accordingly. In some cases, though, it makes sense to group configurations together and apply them as a unit to help arrive at that minimal required configuration set in a more planned and rational way. Policy Sets help ...
Select Device Enrollment workflows. Windows autopilot deployment profiles. Enrollment status page. Intune Policy Sets Collection of Workflows Admin Friendly MEM - Fig.5. Select Azure AD Device or User Groups and complete the Intune policy set assignment. Intune Policy Sets Collection of Workflows Admin Friendly MEM - Fig.6.
The admin may use the following steps to achieve this: Set the assignment to "all devices". Set the Android Teams device filter to "include". Create an Azure AD device group with the devices that need USB debugging enabled and add it to the device filter as "exclude". Apply the policy.
==>>A special thanks to Timmy Andersson for the PowerShell script!!<<== Dear Microsoft Intune Friends, In Microsoft Intune, it is possible to work with co..
To set the availability of an app, you include and exclude app assignments to a group of users or devices by using a combination of include and exclude group assignments. This capability can be useful when you make the app available by including a large group, and then narrow the selected users by also excluding a smaller group.
Deploy a set of trusted sites overriding users' ability to add trusted sites themselves. To acheive this, an Intune configuration profile Trusted site zone assignment can be deployed to devices/users group as required. Login to Intune Portal and navigate to: Devices > Windows > Configuration Profiles. Hit the Create button and Select New policy.
MEM/Intune assignment options. ... In October last year, I wrote an article about Policy sets: "What are Intune Policy Sets?" - even though I think that policy sets can become really handy especially for consistency, there are many caveats with the functionality it provides today. There my advice for now is not to use it, until Microsoft ...
Strange one.... I created two policy sets and two groups. Both groups are dynamic and cloud based. The Intune - Autopilot Self-Deploying i can see when assigning to the policy set, however for the Autopilot User-Driven policy set, it will not let me assigned the Intune - Autopilot User-Driven group. when i go to search for it, the Intune - Autopilot User-Driven group does not appear only ...
Intune managed apps will check-in with an interval of 30 minutes for Intune App Configuration Policy status, when deployed in conjunction with an Intune App Protection Policy. If an Intune App Protection Policy isn't assigned to the user, then the Intune App Configuration Policy check-in interval is set to 720 minutes.
An example of using filters in an assignment is described in the following six steps. Note: The steps below show the usage of a filter for an existing app assignment. The idea and steps are similar when configuring a filter with a new app app assignment or any policy or profile assignment.
Rule builder: And/Or: After you add an expression, you can add to the expression using the and or or options.Property: Select a property for your rule, such as device or operating system SKU.Operator: Select the operator from the list, such as equals or contains.Value: Enter the value in your expression. For example, enter 10.0.18362 for the OS version, or Microsoft for the manufacturer.
Device compliance policies are discrete sets of platform-specific rules and settings you deploy to groups of users or devices. Devices evaluate the rules in the policy to report a device compliance status. A noncompliant status can result in one or more actions for noncompliance. Microsoft Entra Conditional Access policies can also use that ...
Let's discuss using Intune Filter cpuArchitecture Device Property for App and Policy Assignments. Device filters now support the cpuArchitecture property, allowing organizations to specify processor types such as AMD64, Arm64, and x86 in their device management platforms. This enhancement enables more control over the app and policy assignments.
On the Compliance settings page, expand Custom Compliance and set Custom compliance to Require. For Select your discovery script, select Click to select, and then specify a script that's been previously added to the Microsoft Intune admin center. This script must be uploaded before you begin to create the policy.