
Internet Research
- Submit your paper
- Author guidelines
- Editorial team
- Indexing & metrics
- Calls for papers & news

Before you start
Author responsibilities.
Our goal is to provide you with a professional and courteous experience at each stage of the review and publication process. There are also some responsibilities that sit with you as the author. Our expectation is that you will:
- Respond swiftly to any queries during the publication process.
- Be accountable for all aspects of your work. This includes investigating and resolving any questions about accuracy or research integrity
- Treat communications between you and the journal editor as confidential until an editorial decision has been made.
- Include anyone who has made a substantial and meaningful contribution to the submission (anyone else involved in the paper should be listed in the acknowledgements).
- Exclude anyone who hasn’t contributed to the paper, or who has chosen not to be associated with the research.
- In accordance with COPE’s position statement on AI tools , Large Language Models cannot be credited with authorship as they are incapable of conceptualising a research design without human direction and cannot be accountable for the integrity, originality, and validity of the published work. The author(s) must describe the content created or modified as well as appropriately cite the name and version of the AI tool used; any additional works drawn on by the AI tool should also be appropriately cited and referenced. Standard tools that are used to improve spelling and grammar are not included within the parameters of this guidance. The Editor and Publisher reserve the right to determine whether the use of an AI tool is permissible.
- If your article involves human participants, you must ensure you have considered whether or not you require ethical approval for your research, and include this information as part of your submission. Find out more about informed consent .
Generative AI usage key principles
- Copywriting any part of an article using a generative AI tool/LLM would not be permissible, including the generation of the abstract or the literature review, for as per Emerald’s authorship criteria, the author(s) must be responsible for the work and accountable for its accuracy, integrity, and validity.
- The generation or reporting of results using a generative AI tool/LLM is not permissible, for as per Emerald’s authorship criteria, the author(s) must be responsible for the creation and interpretation of their work and accountable for its accuracy, integrity, and validity.
- The in-text reporting of statistics using a generative AI tool/LLM is not permissible due to concerns over the authenticity, integrity, and validity of the data produced, although the use of such a tool to aid in the analysis of the work would be permissible.
- Copy-editing an article using a generative AI tool/LLM in order to improve its language and readability would be permissible as this mirrors standard tools already employed to improve spelling and grammar, and uses existing author-created material, rather than generating wholly new content, while the author(s) remains responsible for the original work.
- The submission and publication of images created by AI tools or large-scale generative models is not permitted.
Research and publishing ethics
Our editors and employees work hard to ensure the content we publish is ethically sound. To help us achieve that goal, we closely follow the advice laid out in the guidelines and flowcharts on the COPE (Committee on Publication Ethics) website .
We have also developed our research and publishing ethics guidelines . If you haven’t already read these, we urge you to do so – they will help you avoid the most common publishing ethics issues.
A few key points:
- Any manuscript you submit to this journal should be original. That means it should not have been published before in its current, or similar, form. Exceptions to this rule are outlined in our pre-print and conference paper policies . If any substantial element of your paper has been previously published, you need to declare this to the journal editor upon submission. Please note, the journal editor may use Crossref Similarity Check to check on the originality of submissions received. This service compares submissions against a database of 49 million works from 800 scholarly publishers.
- Your work should not have been submitted elsewhere and should not be under consideration by any other publication.
- If you have a conflict of interest, you must declare it upon submission; this allows the editor to decide how they would like to proceed. Read about conflict of interest in our research and publishing ethics guidelines .
- By submitting your work to Emerald, you are guaranteeing that the work is not in infringement of any existing copyright.
Third party copyright permissions
Prior to article submission, you need to ensure you’ve applied for, and received, written permission to use any material in your manuscript that has been created by a third party. Please note, we are unable to publish any article that still has permissions pending. The rights we require are:
- Non-exclusive rights to reproduce the material in the article or book chapter.
- Print and electronic rights.
- Worldwide English-language rights.
- To use the material for the life of the work. That means there should be no time restrictions on its re-use e.g. a one-year licence.
We are a member of the International Association of Scientific, Technical, and Medical Publishers (STM) and participate in the STM permissions guidelines , a reciprocal free exchange of material with other STM publishers. In some cases, this may mean that you don’t need permission to re-use content. If so, please highlight this at the submission stage.
Please take a few moments to read our guide to publishing permissions to ensure you have met all the requirements, so that we can process your submission without delay.
Open access submissions and information
All our journals currently offer two open access (OA) publishing paths; gold open access and green open access.
If you would like to, or are required to, make the branded publisher PDF (also known as the version of record) freely available immediately upon publication, you can select the gold open access route once your paper is accepted.
If you’ve chosen to publish gold open access, this is the point you will be asked to pay the APC (article processing charge) . This varies per journal and can be found on our APC price list or on the editorial system at the point of submission. Your article will be published with a Creative Commons CC BY 4.0 user licence , which outlines how readers can reuse your work.
Alternatively, if you would like to, or are required to, publish open access but your funding doesn’t cover the cost of the APC, you can choose the green open access, or self-archiving, route. As soon as your article is published, you can make the author accepted manuscript (the version accepted for publication) openly available, free from payment and embargo periods.
You can find out more about our open access routes, our APCs and waivers and read our FAQs on our open research page.
Find out about open
Transparency and Openness Promotion (TOP) guidelines
We are a signatory of the Transparency and Openness Promotion (TOP) Guidelines , a framework that supports the reproducibility of research through the adoption of transparent research practices. That means we encourage you to:
- Cite and fully reference all data, program code, and other methods in your article.
- Include persistent identifiers, such as a Digital Object Identifier (DOI), in references for datasets and program codes. Persistent identifiers ensure future access to unique published digital objects, such as a piece of text or datasets. Persistent identifiers are assigned to datasets by digital archives, such as institutional repositories and partners in the Data Preservation Alliance for the Social Sciences (Data-PASS).
- Follow appropriate international and national procedures with respect to data protection, rights to privacy and other ethical considerations, whenever you cite data. For further guidance please refer to our research and publishing ethics guidelines . For an example on how to cite datasets, please refer to the references section below.
Prepare your submission
Manuscript support services.
We are pleased to partner with Editage, a platform that connects you with relevant experts in language support, translation, editing, visuals, consulting, and more. After you’ve agreed a fee, they will work with you to enhance your manuscript and get it submission-ready.
This is an optional service for authors who feel they need a little extra support. It does not guarantee your work will be accepted for review or publication.
Visit Editage
Manuscript requirements
Before you submit your manuscript, it’s important you read and follow the guidelines below. You will also find some useful tips in our structure your journal submission how-to guide.
|
| Article files should be provided in Microsoft Word format While you are welcome to submit a PDF of the document alongside the Word file, PDFs alone are not acceptable. LaTeX files can also be used but only if an accompanying PDF document is provided. Acceptable figure file types are listed further below. |
|
| Articles should be between 2000 and 9500 words in length. This includes all text, for example, the structured abstract, references, all text in tables, and figures and appendices. Please allow 280 words for each figure or table. |
|
| A concisely worded title should be provided. |
|
| The names of all contributing authors should be added to the ScholarOne submission; please list them in the order in which you’d like them to be published. Each contributing author will need their own ScholarOne author account, from which we will extract the following details: . . We will reproduce it exactly, so any middle names and/or initials they want featured must be included. . This should be where they were based when the research for the paper was conducted.In multi-authored papers, it’s important that ALL authors that have made a significant contribution to the paper are listed. Those who have provided support but have not contributed to the research should be featured in an acknowledgements section. You should never include people who have not contributed to the paper or who don’t want to be associated with the research. Read about our for authorship. |
|
| If you want to include these items, save them in a separate Microsoft Word document and upload the file with your submission. Where they are included, a brief professional biography of not more than 100 words should be supplied for each named author. |
|
| Your article must reference all sources of external research funding in the acknowledgements section. You should describe the role of the funder or financial sponsor in the entire research process, from study design to submission. |
|
| All submissions must include a structured abstract, following the format outlined below. These four sub-headings and their accompanying explanations must always be included: The following three sub-headings are optional and can be included, if applicable:
The maximum length of your abstract should be 250 words in total, including keywords and article classification (see the sections below). |
|
| Your submission should include up to 12 appropriate and short keywords that capture the principal topics of the paper. Our how to guide contains some practical guidance on choosing search-engine friendly keywords. Please note, while we will always try to use the keywords you’ve suggested, the in-house editorial team may replace some of them with matching terms to ensure consistency across publications and improve your article’s visibility. |
|
| During the submission process, you will be asked to select a type for your paper; the options are listed below. You will also be asked to select a category for your paper. The options for this are listed below. If you don’t see an exact match, please choose the best fit: Reports on any type of research undertaken by the author(s), including: Covers any paper where content is dependent on the author's opinion and interpretation. This includes journalistic and magazine-style pieces. Describes and evaluates technical products, processes or services. Focuses on developing hypotheses and is usually discursive. Covers philosophical discussions and comparative studies of other authors’ work and thinking. Describes actual interventions or experiences within organizations. It can be subjective and doesn’t generally report on research. Also covers a description of a legal case or a hypothetical case study used as a teaching exercise. This category should only be used if the main purpose of the paper is to annotate and/or critique the literature in a particular field. It could be a selective bibliography providing advice on information sources, or the paper may aim to cover the main contributors to the development of a topic and explore their different views. Provides an overview or historical examination of some concept, technique or phenomenon. Papers are likely to be more descriptive or instructional (‘how to’ papers) than discursive. |
|
| Headings must be concise, with a clear indication of the required hierarchy. |
|
| Notes or endnotes should only be used if absolutely necessary. They should be identified in the text by consecutive numbers enclosed in square brackets. These numbers should then be listed, and explained, at the end of the article. |
|
| All figures (charts, diagrams, line drawings, webpages/screenshots, and photographic images) should be submitted electronically. Both colour and black and white files are accepted. |
|
| Tables should be typed and submitted in a separate file to the main body of the article. The position of each table should be clearly labelled in the main body of the article with corresponding labels clearly shown in the table file. Tables should be numbered consecutively in Arabic numerals. |
|
| Where tables, figures, appendices, and other additional content are supplementary to the article but not critical to the reader’s understanding of it, you can choose to host these supplementary files alongside your article on Insight, Emerald’s content hosting platform, or on an institutional or personal repository. All supplementary material must be submitted prior to acceptance. , you must submit these as separate files alongside your article. Files should be clearly labelled in such a way that makes it clear they are supplementary; Emerald recommends that the file name is descriptive and that it follows the format ‘Supplementary_material_appendix_1’ or ‘Supplementary tables’. . A link to the supplementary material will be added to the article during production, and the material will be made available alongside the main text of the article at the point of EarlyCite publication. Please note that Emerald will not make any changes to the material; it will not be copyedited, typeset, and authors will not receive proofs. Emerald therefore strongly recommends that you style all supplementary material ahead of acceptance of the article. Emerald Insight can host the following file types and extensions: , you should ensure that the supplementary material is hosted on the repository ahead of submission, and then include a link only to the repository within the article. It is the responsibility of the submitting author to ensure that the material is free to access and that it remains permanently available. Please note that extensive supplementary material may be subject to peer review; this is at the discretion of the journal Editor and dependent on the content of the material (for example, whether including it would support the reviewer making a decision on the article during the peer review process). |
|
| All references in your manuscript must be formatted using one of the recognised Harvard styles. You are welcome to use the Harvard style Emerald has adopted – we’ve provided a detailed guide below. Want to use a different Harvard style? That’s fine, our typesetters will make any necessary changes to your manuscript if it is accepted. Please ensure you check all your citations for completeness, accuracy and consistency; this enables your readers to exploit the reference linking facility on the database and link back to the works you have cited through Crossref.
References to other publications in your text should be written as follows: , 2006) Please note, ‘ ' should always be written in italics.A few other style points. These apply to both the main body of text and your final list of references. At the end of your paper, please supply a reference list in alphabetical order using the style guidelines below. Where a DOI is available, this should be included at the end of the reference. |
|
| Surname, initials (year), , publisher, place of publication. e.g. Harrow, R. (2005), , Simon & Schuster, New York, NY. |
|
| Surname, initials (year), "chapter title", editor's surname, initials (Ed.), , publisher, place of publication, page numbers. e.g. Calabrese, F.A. (2005), "The early pathways: theory to practice – a continuum", Stankosky, M. (Ed.), , Elsevier, New York, NY, pp.15-20. |
|
| Surname, initials (year), "title of article", , volume issue, page numbers. e.g. Capizzi, M.T. and Ferguson, R. (2005), "Loyalty trends for the twenty-first century", , Vol. 22 No. 2, pp.72-80. |
|
| Surname, initials (year of publication), "title of paper", in editor’s surname, initials (Ed.), , publisher, place of publication, page numbers. e.g. Wilde, S. and Cox, C. (2008), “Principal factors contributing to the competitiveness of tourism destinations at varying stages of development”, in Richardson, S., Fredline, L., Patiar A., & Ternel, M. (Ed.s), , Griffith University, Gold Coast, Qld, pp.115-118. |
|
| Surname, initials (year), "title of paper", paper presented at [name of conference], [date of conference], [place of conference], available at: URL if freely available on the internet (accessed date). e.g. Aumueller, D. (2005), "Semantic authoring and retrieval within a wiki", paper presented at the European Semantic Web Conference (ESWC), 29 May-1 June, Heraklion, Crete, available at: ;(accessed 20 February 2007). |
|
| Surname, initials (year), "title of article", working paper [number if available], institution or organization, place of organization, date. e.g. Moizer, P. (2003), "How published academic research can inform policy decisions: the case of mandatory rotation of audit appointments", working paper, Leeds University Business School, University of Leeds, Leeds, 28 March. |
|
| (year), "title of entry", volume, edition, title of encyclopaedia, publisher, place of publication, page numbers. e.g. (1926), "Psychology of culture contact", Vol. 1, 13th ed., Encyclopaedia Britannica, London and New York, NY, pp.765-771. (for authored entries, please refer to book chapter guidelines above) |
|
| Surname, initials (year), "article title", , date, page numbers. e.g. Smith, A. (2008), "Money for old rope", , 21 January, pp.1, 3-4. |
|
| (year), "article title", date, page numbers. e.g. (2008), "Small change", 2 February, p.7. |
|
| Surname, initials (year), "title of document", unpublished manuscript, collection name, inventory record, name of archive, location of archive. e.g. Litman, S. (1902), "Mechanism & Technique of Commerce", unpublished manuscript, Simon Litman Papers, Record series 9/5/29 Box 3, University of Illinois Archives, Urbana-Champaign, IL. |
|
| If available online, the full URL should be supplied at the end of the reference, as well as the date that the resource was accessed. Surname, initials (year), “title of electronic source”, available at: persistent URL (accessed date month year). e.g. Weida, S. and Stolley, K. (2013), “Developing strong thesis statements”, available at: (accessed 20 June 2018) Standalone URLs, i.e. those without an author or date, should be included either inside parentheses within the main text, or preferably set as a note (Roman numeral within square brackets within text followed by the full URL address at the end of the paper). |
|
| Surname, initials (year), , name of data repository, available at: persistent URL, (accessed date month year). e.g. Campbell, A. and Kahn, R.L. (2015), , ICPSR07218-v4, Inter-university Consortium for Political and Social Research (distributor), Ann Arbor, MI, available at: (accessed 20 June 2018) |
Submit your manuscript
There are a number of key steps you should follow to ensure a smooth and trouble-free submission.
Double check your manuscript
Before submitting your work, it is your responsibility to check that the manuscript is complete, grammatically correct, and without spelling or typographical errors. A few other important points:
- Give the journal aims and scope a final read. Is your manuscript definitely a good fit? If it isn’t, the editor may decline it without peer review.
- Does your manuscript comply with our research and publishing ethics guidelines ?
- Have you cleared any necessary publishing permissions ?
- Have you followed all the formatting requirements laid out in these author guidelines?
- If you need to refer to your own work, use wording such as ‘previous research has demonstrated’ not ‘our previous research has demonstrated’.
- If you need to refer to your own, currently unpublished work, don’t include this work in the reference list.
- Any acknowledgments or author biographies should be uploaded as separate files.
- Carry out a final check to ensure that no author names appear anywhere in the manuscript. This includes in figures or captions.
You will find a helpful submission checklist on the website Think.Check.Submit .
The submission process
All manuscripts should be submitted through our editorial system by the corresponding author.
The only way to submit to the journal is through the journal’s ScholarOne site as accessed via the Emerald website, and not by email or through any third-party agent/company, journal representative, or website. Submissions should be done directly by the author(s) through the ScholarOne site and not via a third-party proxy on their behalf.
A separate author account is required for each journal you submit to. If this is your first time submitting to this journal, please choose the Create an account or Register now option in the editorial system. If you already have an Emerald login, you are welcome to reuse the existing username and password here.
Please note, the next time you log into the system, you will be asked for your username. This will be the email address you entered when you set up your account.
Don't forget to add your ORCiD ID during the submission process. It will be embedded in your published article, along with a link to the ORCiD registry allowing others to easily match you with your work.
Don’t have one yet? It only takes a few moments to register for a free ORCiD identifier .
Visit the ScholarOne support centre for further help and guidance.
What you can expect next
You will receive an automated email from the journal editor, confirming your successful submission. It will provide you with a manuscript number, which will be used in all future correspondence about your submission. If you have any reason to suspect the confirmation email you receive might be fraudulent, please contact our Rights team .
Post submission
Review and decision process.
Each submission is checked by the editor. At this stage, they may choose to decline or unsubmit your manuscript if it doesn’t fit the journal aims and scope, or they feel the language/manuscript quality is too low.
If they think it might be suitable for the publication, they will send it to at least two independent referees for double blind peer review. Once these reviewers have provided their feedback, the editor may decide to accept your manuscript, request minor or major revisions, or decline your work.
This journal offers an article transfer service. If the editor decides to decline your manuscript, either before or after peer review, they may offer to transfer it to a more relevant Emerald journal in this field. If you accept, your ScholarOne author account, and the accounts of your co-authors, will automatically transfer to the new journal, along with your manuscript and any accompanying peer review reports. However, you will still need to log in to ScholarOne to complete the submission process using your existing username and password. While accepting a transfer does not guarantee the receiving journal will publish your work, an editor will only suggest a transfer if they feel your article is a good fit with the new title.
While all journals work to different timescales, the goal is that the editor will inform you of their first decision within 60 days.
During this period, we will send you automated updates on the progress of your manuscript via our submission system, or you can log in to check on the current status of your paper. Each time we contact you, we will quote the manuscript number you were given at the point of submission. If you receive an email that does not match these criteria, it could be fraudulent and we recommend you email [email protected] .
If your submission is accepted
Open access.
Once your paper is accepted, you will have the opportunity to indicate whether you would like to publish your paper via the gold open access route.
If you’ve chosen to publish gold open access, this is the point you will be asked to pay the APC (article processing charge). This varies per journal and can be found on our APC price list or on the editorial system at the point of submission. Your article will be published with a Creative Commons CC BY 4.0 user licence , which outlines how readers can reuse your work.
All accepted authors are sent an email with a link to a licence form. This should be checked for accuracy, for example whether contact and affiliation details are up to date and your name is spelled correctly, and then returned to us electronically. If there is a reason why you can’t assign copyright to us, you should discuss this with your journal content editor. You will find their contact details on the editorial team section above.
Proofing and typesetting
Once we have received your completed licence form, the article will pass directly into the production process. We will carry out editorial checks, copyediting, and typesetting and then return proofs to you (if you are the corresponding author) for your review. This is your opportunity to correct any typographical errors, grammatical errors or incorrect author details. We can’t accept requests to rewrite texts at this stage.
When the page proofs are finalised, the fully typeset and proofed version of record is published online. This is referred to as the EarlyCite version. While an EarlyCite article has yet to be assigned to a volume or issue, it does have a digital object identifier (DOI) and is fully citable. It will be compiled into an issue according to the journal’s issue schedule, with papers being added by chronological date of publication.
How to share your paper
Visit our author rights page to find out how you can reuse and share your work.
To find tips on increasing the visibility of your published paper, read about how to promote your work .
Correcting inaccuracies in your published paper
Sometimes errors are made during the research, writing and publishing processes. When these issues arise, we have the option of withdrawing the paper or introducing a correction notice. Find out more about our article withdrawal and correction policies .
Need to make a change to the author list? See our frequently asked questions (FAQs) below.
Frequently asked questions
|
| The only time we will ever ask you for money to publish in an Emerald journal is if you have chosen to publish via the gold open access route. You will be asked to pay an APC (article-processing charge) once your paper has been accepted (unless it is a sponsored open access journal), and never at submission.
At no other time will you be asked to contribute financially towards your article’s publication, processing, or review. If you haven’t chosen gold open access and you receive an email that appears to be from Emerald, the journal, or a third party, asking you for payment to publish, please contact our support team via . |
|
| Please contact the editor for the journal, with a copy of your CV. You will find their contact details on the editorial team tab on this page. |
|
| Typically, papers are added to an issue according to their date of publication. If you would like to know in advance which issue your paper will appear in, please contact the content editor of the journal. You will find their contact details on the editorial team tab on this page. Once your paper has been published in an issue, you will be notified by email. |
|
| Please email the journal editor – you will find their contact details on the editorial team tab on this page. If you ever suspect an email you’ve received from Emerald might not be genuine, you are welcome to verify it with the content editor for the journal, whose contact details can be found on the editorial team tab on this page. Alternatively, you can . |
|
| If you’ve read the aims and scope on the journal landing page and are still unsure whether your paper is suitable for the journal, please email the editor and include your paper's title and structured abstract. They will be able to advise on your manuscript’s suitability. You will find their contact details on the Editorial team tab on this page. |
|
| Authorship and the order in which the authors are listed on the paper should be agreed prior to submission. We have a right first time policy on this and no changes can be made to the list once submitted. If you have made an error in the submission process, please email the 8Journal Editorial Office who will look into your request – you will find their contact details on the editorial team tab on this page. |
- Christy M. K. Cheung Hong Kong Baptist University - Hong Kong, China [email protected]
Editors Emeriti
- 1995 – 1998: John Peters Emerald Publishing - UK
- 1998 – 2011: David G. Schwartz Bar-Ilan University - Israel
- 2011 – 2016: Bernard J. Jansen The Pennsylvania State University - USA and Qatar Computing Research Institute, Doha - Qatar
Distinguished Board of Advisors
- Izak Benbasat The University of British Columbia - Canada
- Alexander Benlian Darmstadt University of Technology - Germany
- Andrew Burton-Jones The University of Queensland - Australia
- Carol Hsu The University of Sydney - Australia
- Bernard J. Jansen The Pennsylvania State University - USA and Qatar Computing Research Institute, Doha - Qatar
- Atreyi Kankanhalli National University of Singapore - Singapore
- Matthew K.O. Lee City University of Hong Kong - Hong Kong
- Lynne Markus Bentley University - USA
- Chee-Wee Tan Hong Kong Polytechnic University - Hong Kong, China
- Monideepa Tarafdar University of Massachusetts Amherst - USA
- Jason Thatcher University of Colorado Boulder - USA
- Daniel Veit University of Augsburg - Germany
- Viswanath Venkatesh Virginia Polytechnic Institute and State University - USA
Senior Editors
- Yang Chen Southwestern University of Finance and Economics - People's Republic of China
- Juho Hamari Tampere University - Finland
- Zach W. Y. Lee University of Leicester - UK
- Christian Maier University of Bamberg - Germany
- Christian Matt University of Bern - Switzerland
- Xiao-Liang Shen Wuhan University - People's Republic of China
- Ayoung Suh Sungkyunkwan University - Republic of Korea
- Manuel Trenz University of Göttingen - Germany
- Ofir Turel The University of Melbourne - Australia
- Kem Z. K. Zhang Lakehead University - Canada
Associate Editors
- Zhao Cai University of Nottingham Ningbo China - People's Republic of China
- Tommy K. H. Chan University of Manchester - UK
- Xusen Cheng Renmin University of China - China
- Ben Choi Nanyang Technological University - Singapore
- Raffaele Filieri Audencia Business School - France
- Maryam Ghasemaghaei McMaster University - Canada
- Xitong Guo Harbin Institute of Technology - People's Republic of China
- Yaniv Gvili Ono Academic College - Israel
- Nima Kordzadeh Worcester Polytechnic Institute in Massachusetts - USA
- Satish Krishnan Indian Institute of Management, Kozhikode - India
- Hongxiu Li Tampere University - Finland
- Eric T. K. Lim University of New South Wales - Australia
- Yong Liu Aalto University School of Business - Finland
- Jian Mou Pusan National University - Republic of Korea
- Fiona Nah City University of Hong Kong - Hong Kong
- Tiago Oliveira New University of Lisbon - Portugal
- Hamed Qahri-Saremi Colorado State University - USA
- Marten Risius The University of Queensland - Australia
- Nick Roberts Oregon State University - USA
- Sebastian Schuetz Florida International University - USA
- Isabella Seeber Grenoble Ecole de Management - France
- Wen-Lung Shiau Chang Gung University - Taiwan
- Barney Tan University of New South Wales - Australia
- Christoph Weinert University of Bamberg - Germany
- Randy Wong The University of Auckland - New Zealand
- Zhijun Yan Beijing Institute of Technology - People's Republic of China
- Frederick Yim Hong Kong Baptist University - Hong Kong
Managing Editor for Marketing
- Grace Gao Hong Kong Baptist University - Hong Kong
Commissioning Editor
- Charlotte Eagles Emerald Publishing [email protected]
Journal Editorial Office (For queries related to pre-acceptance)
- Nikita Singh Emerald Publishing [email protected]
Supplier Project Manager (For queries related to post-acceptance)
- Sivakeerthika Saravanan Emerald Publishing [email protected]
Editorial Review Board
- Muhammad Naseer Akhtar University of East London - UK
- Mamoun Akroush German Jordanian University - Jordan and American University of Madaba - Jordan
- Joonheui Bae The Hong Kong Polytechnic University - Hong Kong
- Snehasish Banerjee University of York - UK
- Annika Baumann University of Potsdam - Germany
- Luis Vicente Casaló Ariño University of Zaragoza - Spain
- Hsiu-Hua Chang Feng Chia University - Taiwan
- Wei-Lun Chang National Taipei University of Technology - Taiwan
- Chongyang Chen Zhejiang University of Finance and Economics - People's Republic of China
- Meng Chen University of Science and Technology of China - People's Republic of China
- Xi Chen Zhejiang University - People's Republic of China
- Alton Y.K. Chua Nanyang Technological University - Singapore
- Francesca D’Errico University of Bari Aldo Moro - Italy
- Jie Fang University of Nottingham Ningbo China - People's Republic of China
- Samira Farivar Carleton University - Canada
- Steven M. Furnell University of Nottingham - UK
- Chunmian Ge South China University of Technology - People's Republic of China
- Xiang Gong Xi'an JiaoTong University - People's Republic of China
- Chong Guan Singapore University of Social Sciences - Singapore
- Chris Hand Kingston University - UK
- Maximilian Haug Neu-Ulm University of Applied Sciences - Germany
- Wei He Texas Tech University - USA
- Fangfang Hou Xi’an Jiaotong-Liverpool University - People's Republic of China
- Kuo-Lun Hsiao National Taichung University of Science and Technology - Taiwan
- Echo Huang National Kaohsiung University of Science and Technology - Taiwan
- Tseng-Lung Huang National Pingtung University - Taiwan
- Wendy Wan Yee Hui Singapore Institute of Technology - Singapore
- Lin Jia Beijing Institute of Technology - People's Republic of China
- Hyunjin Kang Nanyang Technological University - Singapore
- Ching-Jui Keng National Taipei University of Technology - Taiwan
- Hamid Khobzi University of Sussex - UK
- Austin Kwak Kent State University - USA
- Antonia Köster University of Potsdam - Germany
- Cong Li University of Miami - USA
- Wenwen Li Fudan University - People's Republic of China
- Yang-Jun Li Beijing Institute of Technology - People's Republic of China
- Yupeng Li Hong Kong Baptist University - Hong Kong
- Chih-Chin Liang National Formosa University - Taiwan
- Binshan Lin Louisiana State University in Shreveport - USA
- Hsiu-Fen Lin National Taiwan Ocean University - Taiwan
- Na Liu The University of Sydney - Australia
- Shan Liu Xi'an JiaoTong University - People's Republic of China
- William Maule Naval Postgraduate School - USA
- Felix Septianto The University of Queensland - Australia
- Rinat Shaanan-Satchi Open University of Israel - Israel
- Rong-An Shang Soochow University - Taiwan
- Chung-Chi Shen National Chiayi University - Taiwan
- Si Shi Southwestern University of Finance and Economics - People's Republic of China
- Donghee Don Shin Texas Tech University - USA
- Garry Wei Han Tan UCSI University - Malaysia
- Ching-I Teng Chang Gung University - Taiwan
- Leo R Vijayasarathy Colorado State University - USA
- Nianxin Wang Jiangsu University of Science and Technology - People's Republic of China
- Xiaohui Wang City University of Hong Kong - Hong Kong
- Yi Wu Tianjin University - People's Republic of China
- Nannan Xi Tampere University - Finland
- Vignesh Yoganathan Queen Mary University of London - UK
- Jie Yu (Joseph) University of Nottingham Ningbo China - People's Republic of China
- Chian-Son Yu Shih Chien University - Taiwan
- Xiabing Zheng University of Science and Technology of China - People's Republic of China
- Hangjung Zo Korea Advanced Institute of Science and Technology - Republic of Korea
Citation metrics
CiteScore 2023
Further information
CiteScore is a simple way of measuring the citation impact of sources, such as journals.
Calculating the CiteScore is based on the number of citations to documents (articles, reviews, conference papers, book chapters, and data papers) by a journal over four years, divided by the number of the same document types indexed in Scopus and published in those same four years.
For more information and methodology visit the Scopus definition
CiteScore Tracker 2024
(updated monthly)
CiteScore Tracker is calculated in the same way as CiteScore, but for the current year rather than previous, complete years.
The CiteScore Tracker calculation is updated every month, as a current indication of a title's performance.
2023 Impact Factor
The Journal Impact Factor is published each year by Clarivate Analytics. It is a measure of the number of times an average paper in a particular journal is cited during the preceding two years.
For more information and methodology see Clarivate Analytics
5-year Impact Factor (2023)
A base of five years may be more appropriate for journals in certain fields because the body of citations may not be large enough to make reasonable comparisons, or it may take longer than two years to publish and distribute leading to a longer period before others cite the work.
Actual value is intentionally only displayed for the most recent year. Earlier values are available in the Journal Citation Reports from Clarivate Analytics .
Publication timeline
Time to first decision
Time to first decision , expressed in days, the "first decision" occurs when the journal’s editorial team reviews the peer reviewers’ comments and recommendations. Based on this feedback, they decide whether to accept, reject, or request revisions for the manuscript.
Data is taken from submissions between 1st June 2023 and 31st May 2024
Acceptance to publication
Acceptance to publication , expressed in days, is the average time between when the journal’s editorial team decide whether to accept, reject, or request revisions for the manuscript and the date of publication in the journal.
Data is taken from the previous 12 months (Last updated July 2024)
Acceptance rate
The acceptance rate is a measurement of how many manuscripts a journal accepts for publication compared to the total number of manuscripts submitted expressed as a percentage %
Data is taken from submissions between 1st June 2023 and 31st May 2024 .
This figure is the total amount of downloads for all articles published early cite in the last 12 months
(Last updated: July 2024)
This journal is abstracted and indexed by
- ABI/INFORM Complete
- ABI/INFORM Global
- Academic Research Library
- Academic Search: Alumni Edition/ Complete/Premier
- BUBL Information Service
- Cabell's Directory of Publishing Opportunities in Management and Marketing
- CompuMath Citation Index
- Computer Literature Index
- Current Awareness Abstracts
- Computers and Applied Sciences Complete
- Current Abstracts
- Current Contents/Engineering Computing & Technology
- dblp Computer Science Bibliography
- ERIC Clearinghouse on Information Technology
- IEE INSPEC database
- Information Science Abstracts and Fulltext Sources Online
- The Informed Librarian
- Library and Information Science Abstracts (LISA)
- Library, Information Science and Technology Abstracts (LISTA)
- Library Literature
- Norwegian Scientific Index
- PAIS indexes
- Polish Ministry of Science and Higher Education
- Professional ABI/INFORM Complete
- Professional ProQuest Central
- ProQuest Advanced Technologies & Aerospace Journals
- ProQuest Central
- ProQuest Computer Science Journals
- ProQuest Curriculum Essentials
- ProQuest Education Journals
- ProQuest Library Science
- ProQuest SciTech Journals
- ProQuest Technology Journals
- ReadCube Discover
- Research Alert
- Research Library
- Science Citation Index Expanded ®
- SciSearch ®
- Social Sciences Citation Index ®
This journal is ranked by
- The Chartered Association of Business Schools' Academic Journal Guide: 3
- Australian Business Deans Council: A
- BFI (Denmark): 2
- German Association for Business Research (VHB) Publication Media Rating: B
- The Publication Forum (Finland): 2
Reviewer information
Peer review process.
This journal engages in a double-anonymous peer review process, which strives to match the expertise of a reviewer with the submitted manuscript. Reviews are completed with evidence of thoughtful engagement with the manuscript, provide constructive feedback, and add value to the overall knowledge and information presented in the manuscript.
The mission of the peer review process is to achieve excellence and rigour in scholarly publications and research.
Our vision is to give voice to professionals in the subject area who contribute unique and diverse scholarly perspectives to the field.
The journal values diverse perspectives from the field and reviewers who provide critical, constructive, and respectful feedback to authors. Reviewers come from a variety of organizations, careers, and backgrounds from around the world.
All invitations to review, abstracts, manuscripts, and reviews should be kept confidential. Reviewers must not share their review or information about the review process with anyone without the agreement of the editors and authors involved, even after publication. This also applies to other reviewers’ “comments to author” which are shared with you on decision.

Resources to guide you through the review process
Discover practical tips and guidance on all aspects of peer review in our reviewers' section. See how being a reviewer could benefit your career, and discover what's involved in shaping a review.
More reviewer information
Calls for papers
Ai for a better future.
Click here to Submit! Introduction: Artificial intelligence (AI) is permeating individuals’ daily live...
Thank you to the 2023 Reviewer
The publishing and editorial teams would like to thank the following, for their invaluable service as 2023 reviewers for this journal. We are very grateful for the contributions made. With their help, the journal has been able to publish such high...
Thank you to the 2022 Reviewers
The publishing and editorial teams would like to thank the following, for their invaluable service as 2022 reviewers for this journal. We are very grateful for the contributions made. With their help, the journal has been able to publish such high...
Thank you to the 2021 Reviewers
The publishing and editorial teams would like to thank the following, for their invaluable service as 2021 reviewers for this journal. We are very grateful for the contributions made. With their help, the journal has been able to publish such high...
Internet Research Emerald Literati Awards for Excellence 2021
We are pleased to announce the 2021 winners of the Internet Research Emerald Literati Awards for Excellence. The awards celebrate and reward the outstanding contributions of our authors, reviewers, and editorial ...
Internet Research Emerald Literati Awards for Excellence 2015-2020
We are pleased to announce the winners of the Internet Research Emerald Literati Awards for Excellence in 2015 - 2020. The awards celebrate and reward the outstanding contributions of o...
Literati awards

Internet Research - Literati Award Winners 2023
We are pleased to announce our 2023 Literati Award winners. Outstanding Paper Laziness as an explanation for the privacy paradox: a longitudinal ...

Internet Research Emerald Literati Awards for Excellence 2022
We are pleased to announce the 2022 winners of the Internet Research Emerald Literati Awards for Excellence. The awards celebrate and reward the outstanding contributions of our authors, reviewers, and editorial team....

Internet Research - Literati Award Winners 2021
We are pleased to announce our 2021 Literati Award winners. Outstanding Paper Wang, X. and Song, Y. (2020), "Viral misinformation and echo chambers: the diffusion of rumors about genetically mo...

Internet Research - Literati Award Winners 2020
We are pleased to announce our 2020 Literati Award winners. Outstanding paper Hornik, J., Shaanan Satchi, R. and Rachamim, M. (2019), "The joy of pain: A gloating account of negative electronic...
This wide-ranging interdisciplinary journal looks at the social, ethical, economic, managerial and political implications of the internet. Recent issues have focused on metaverse, interpretable AI, digital health, online and mobile gaming, the sharing economy, and the dark side of social media.

Aims and scope
Internet Research is an international, refereed journal that aims to describe, assess and foster understanding of the role of wide-area, multi-purpose computer networks such as the Internet.
The Internet continues to gather influence and momentum, and it becomes increasingly important to be aware of the potential applications of this powerful resource throughout professional, political, personal and academic life. We therefore strongly encourage research that develops theoretical insights and understanding on topics and issues addressing the potential social, ethical, economic, managerial and political implications which arise from mass public access to information resources.
Coverage includes but is not limited to:
- Societal and ethical issues (e.g., internet addiction, doxing, cyberbullying, misinformation, fear of missing out)
- Economic implications (e.g., electronic commerce, mobile commerce, and social commerce)
- Managerial and organisational issues (e.g., Internet use practices, cyberloafing, management policies and governance mechanisms)
- Political implications (e.g., civic engagement, collective action, Internet-related policy research)
Latest articles
These are the latest articles published in this journal (Last updated: July 2024)
Seeking Social Support on Social Media: A Coping Perspective
The role of omnichannel integration and digital value in building brand trust: a customer psychological perception perspective, platform control and multi-realized platform benefits: a meta-analysis, top downloaded articles.
These are the most downloaded articles over the last 12 months for this journal (Last updated: July 2024)
AI Governance: Themes, Knowledge Gaps, and Future Agendas
Personal use of smartphones in the workplace and work-life conflict: a natural quasi-experiment, examining technostress and its impact on worker wellbeing in the digital gig economy.
These are the top cited articles for this journal, from the last 12 months according to Crossref (Last updated: July 2024)
Exploring the association between the Proteus effect and intention to play massive multiplayer online role-playing games (MMORPGs)
A review of the literature on the metaverse: definition, technologies, and user behaviors, enterprise social media usage and social cyberloafing: an empirical investigation using the jd-r model, related journals.
This journal is part of our Information & knowledge management collection. Explore our Information & knowledge management subject area to find out more.
See all related journals
Journal of Information, Communication and Ethics in Society
Journal of Information, Communication and Ethics in Society promotes thoughtful dialogue regarding the wider social and...

Kybernetes is an important forum for the exchange of knowledge and information among all those who are interested in...

Reference Services Review
Reference Services Review is dedicated to the enrichment and advancement of reference knowledge and the improvement of...

Internet Research.
- January 2011
- In book: Qualitative Research: Theory, Method, and Practices, 3rd Edition
- Publisher: Sage

- RMIT University
Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- Fem Media Stud
- Radhika Gajjala
- Anthony Giddens
- Elizabeth Buchanan

- E. Buchanan

- Lori. Kendall
- NEW MEDIA SOC
- Susannah R. Stern

- William K. Rawlins

- Daniel Miller

- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
Education During Coronavirus
A Smithsonian magazine special report
Science | June 15, 2020
Seventy-Five Scientific Research Projects You Can Contribute to Online
From astrophysicists to entomologists, many researchers need the help of citizen scientists to sift through immense data collections
:focal(300x157:301x158)/https://tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer/e2/ca/e2ca665f-77b7-4ba2-8cd2-46f38cbf2b60/citizen_science_mobile.png)
Rachael Lallensack
Former Assistant Editor, Science and Innovation
If you find yourself tired of streaming services, reading the news or video-chatting with friends, maybe you should consider becoming a citizen scientist. Though it’s true that many field research projects are paused , hundreds of scientists need your help sifting through wildlife camera footage and images of galaxies far, far away, or reading through diaries and field notes from the past.
Plenty of these tools are free and easy enough for children to use. You can look around for projects yourself on Smithsonian Institution’s citizen science volunteer page , National Geographic ’s list of projects and CitizenScience.gov ’s catalog of options. Zooniverse is a platform for online-exclusive projects , and Scistarter allows you to restrict your search with parameters, including projects you can do “on a walk,” “at night” or “on a lunch break.”
To save you some time, Smithsonian magazine has compiled a collection of dozens of projects you can take part in from home.

American Wildlife
If being home has given you more time to look at wildlife in your own backyard, whether you live in the city or the country, consider expanding your view, by helping scientists identify creatures photographed by camera traps. Improved battery life, motion sensors, high-resolution and small lenses have made camera traps indispensable tools for conservation.These cameras capture thousands of images that provide researchers with more data about ecosystems than ever before.
Smithsonian Conservation Biology Institute’s eMammal platform , for example, asks users to identify animals for conservation projects around the country. Currently, eMammal is being used by the Woodland Park Zoo ’s Seattle Urban Carnivore Project, which studies how coyotes, foxes, raccoons, bobcats and other animals coexist with people, and the Washington Wolverine Project, an effort to monitor wolverines in the face of climate change. Identify urban wildlife for the Chicago Wildlife Watch , or contribute to wilderness projects documenting North American biodiversity with The Wilds' Wildlife Watch in Ohio , Cedar Creek: Eyes on the Wild in Minnesota , Michigan ZoomIN , Western Montana Wildlife and Snapshot Wisconsin .
"Spend your time at home virtually exploring the Minnesota backwoods,” writes the lead researcher of the Cedar Creek: Eyes on the Wild project. “Help us understand deer dynamics, possum populations, bear behavior, and keep your eyes peeled for elusive wolves!"

If being cooped up at home has you daydreaming about traveling, Snapshot Safari has six active animal identification projects. Try eyeing lions, leopards, cheetahs, wild dogs, elephants, giraffes, baobab trees and over 400 bird species from camera trap photos taken in South African nature reserves, including De Hoop Nature Reserve and Madikwe Game Reserve .
With South Sudan DiversityCam , researchers are using camera traps to study biodiversity in the dense tropical forests of southwestern South Sudan. Part of the Serenegeti Lion Project, Snapshot Serengeti needs the help of citizen scientists to classify millions of camera trap images of species traveling with the wildebeest migration.
Classify all kinds of monkeys with Chimp&See . Count, identify and track giraffes in northern Kenya . Watering holes host all kinds of wildlife, but that makes the locales hotspots for parasite transmission; Parasite Safari needs volunteers to help figure out which animals come in contact with each other and during what time of year.
Mount Taranaki in New Zealand is a volcanic peak rich in native vegetation, but native wildlife, like the North Island brown kiwi, whio/blue duck and seabirds, are now rare—driven out by introduced predators like wild goats, weasels, stoats, possums and rats. Estimate predator species compared to native wildlife with Taranaki Mounga by spotting species on camera trap images.
The Zoological Society of London’s (ZSL) Instant Wild app has a dozen projects showcasing live images and videos of wildlife around the world. Look for bears, wolves and lynx in Croatia ; wildcats in Costa Rica’s Osa Peninsula ; otters in Hampshire, England ; and both black and white rhinos in the Lewa-Borana landscape in Kenya.

Under the Sea
Researchers use a variety of technologies to learn about marine life and inform conservation efforts. Take, for example, Beluga Bits , a research project focused on determining the sex, age and pod size of beluga whales visiting the Churchill River in northern Manitoba, Canada. With a bit of training, volunteers can learn how to differentiate between a calf, a subadult (grey) or an adult (white)—and even identify individuals using scars or unique pigmentation—in underwater videos and images. Beluga Bits uses a “ beluga boat ,” which travels around the Churchill River estuary with a camera underneath it, to capture the footage and collect GPS data about the whales’ locations.
Many of these online projects are visual, but Manatee Chat needs citizen scientists who can train their ear to decipher manatee vocalizations. Researchers are hoping to learn what calls the marine mammals make and when—with enough practice you might even be able to recognize the distinct calls of individual animals.
Several groups are using drone footage to monitor seal populations. Seals spend most of their time in the water, but come ashore to breed. One group, Seal Watch , is analyzing time-lapse photography and drone images of seals in the British territory of South Georgia in the South Atlantic. A team in Antarctica captured images of Weddell seals every ten minutes while the seals were on land in spring to have their pups. The Weddell Seal Count project aims to find out what threats—like fishing and climate change—the seals face by monitoring changes in their population size. Likewise, the Año Nuevo Island - Animal Count asks volunteers to count elephant seals, sea lions, cormorants and more species on a remote research island off the coast of California.
With Floating Forests , you’ll sift through 40 years of satellite images of the ocean surface identifying kelp forests, which are foundational for marine ecosystems, providing shelter for shrimp, fish and sea urchins. A project based in southwest England, Seagrass Explorer , is investigating the decline of seagrass beds. Researchers are using baited cameras to spot commercial fish in these habitats as well as looking out for algae to study the health of these threatened ecosystems. Search for large sponges, starfish and cold-water corals on the deep seafloor in Sweden’s first marine park with the Koster seafloor observatory project.
The Smithsonian Environmental Research Center needs your help spotting invasive species with Invader ID . Train your eye to spot groups of organisms, known as fouling communities, that live under docks and ship hulls, in an effort to clean up marine ecosystems.
If art history is more your speed, two Dutch art museums need volunteers to start “ fishing in the past ” by analyzing a collection of paintings dating from 1500 to 1700. Each painting features at least one fish, and an interdisciplinary research team of biologists and art historians wants you to identify the species of fish to make a clearer picture of the “role of ichthyology in the past.”

Interesting Insects
Notes from Nature is a digitization effort to make the vast resources in museums’ archives of plants and insects more accessible. Similarly, page through the University of California Berkeley’s butterfly collection on CalBug to help researchers classify these beautiful critters. The University of Michigan Museum of Zoology has already digitized about 300,000 records, but their collection exceeds 4 million bugs. You can hop in now and transcribe their grasshopper archives from the last century . Parasitic arthropods, like mosquitos and ticks, are known disease vectors; to better locate these critters, the Terrestrial Parasite Tracker project is working with 22 collections and institutions to digitize over 1.2 million specimens—and they’re 95 percent done . If you can tolerate mosquito buzzing for a prolonged period of time, the HumBug project needs volunteers to train its algorithm and develop real-time mosquito detection using acoustic monitoring devices. It’s for the greater good!

For the Birders
Birdwatching is one of the most common forms of citizen science . Seeing birds in the wilderness is certainly awe-inspiring, but you can birdwatch from your backyard or while walking down the sidewalk in big cities, too. With Cornell University’s eBird app , you can contribute to bird science at any time, anywhere. (Just be sure to remain a safe distance from wildlife—and other humans, while we social distance ). If you have safe access to outdoor space—a backyard, perhaps—Cornell also has a NestWatch program for people to report observations of bird nests. Smithsonian’s Migratory Bird Center has a similar Neighborhood Nest Watch program as well.
Birdwatching is easy enough to do from any window, if you’re sheltering at home, but in case you lack a clear view, consider these online-only projects. Nest Quest currently has a robin database that needs volunteer transcribers to digitize their nest record cards.
You can also pitch in on a variety of efforts to categorize wildlife camera images of burrowing owls , pelicans , penguins (new data coming soon!), and sea birds . Watch nest cam footage of the northern bald ibis or greylag geese on NestCams to help researchers learn about breeding behavior.
Or record the coloration of gorgeous feathers across bird species for researchers at London’s Natural History Museum with Project Plumage .

Pretty Plants
If you’re out on a walk wondering what kind of plants are around you, consider downloading Leafsnap , an electronic field guide app developed by Columbia University, the University of Maryland and the Smithsonian Institution. The app has several functions. First, it can be used to identify plants with its visual recognition software. Secondly, scientists can learn about the “ the ebb and flow of flora ” from geotagged images taken by app users.
What is older than the dinosaurs, survived three mass extinctions and still has a living relative today? Ginko trees! Researchers at Smithsonian’s National Museum of Natural History are studying ginko trees and fossils to understand millions of years of plant evolution and climate change with the Fossil Atmospheres project . Using Zooniverse, volunteers will be trained to identify and count stomata, which are holes on a leaf’s surface where carbon dioxide passes through. By counting these holes, or quantifying the stomatal index, scientists can learn how the plants adapted to changing levels of carbon dioxide. These results will inform a field experiment conducted on living trees in which a scientist is adjusting the level of carbon dioxide for different groups.
Help digitize and categorize millions of botanical specimens from natural history museums, research institutions and herbaria across the country with the Notes from Nature Project . Did you know North America is home to a variety of beautiful orchid species? Lend botanists a handby typing handwritten labels on pressed specimens or recording their geographic and historic origins for the New York Botanical Garden’s archives. Likewise, the Southeastern U.S. Biodiversity project needs assistance labeling pressed poppies, sedums, valerians, violets and more. Groups in California , Arkansas , Florida , Texas and Oklahoma all invite citizen scientists to partake in similar tasks.

Historic Women in Astronomy
Become a transcriber for Project PHaEDRA and help researchers at the Harvard-Smithsonian Center for Astrophysics preserve the work of Harvard’s women “computers” who revolutionized astronomy in the 20th century. These women contributed more than 130 years of work documenting the night sky, cataloging stars, interpreting stellar spectra, counting galaxies, and measuring distances in space, according to the project description .
More than 2,500 notebooks need transcription on Project PhaEDRA - Star Notes . You could start with Annie Jump Cannon , for example. In 1901, Cannon designed a stellar classification system that astronomers still use today. Cecilia Payne discovered that stars are made primarily of hydrogen and helium and can be categorized by temperature. Two notebooks from Henrietta Swan Leavitt are currently in need of transcription. Leavitt, who was deaf, discovered the link between period and luminosity in Cepheid variables, or pulsating stars, which “led directly to the discovery that the Universe is expanding,” according to her bio on Star Notes .
Volunteers are also needed to transcribe some of these women computers’ notebooks that contain references to photographic glass plates . These plates were used to study space from the 1880s to the 1990s. For example, in 1890, Williamina Flemming discovered the Horsehead Nebula on one of these plates . With Star Notes, you can help bridge the gap between “modern scientific literature and 100 years of astronomical observations,” according to the project description . Star Notes also features the work of Cannon, Leavitt and Dorrit Hoffleit , who authored the fifth edition of the Bright Star Catalog, which features 9,110 of the brightest stars in the sky.
Microscopic Musings
Electron microscopes have super-high resolution and magnification powers—and now, many can process images automatically, allowing teams to collect an immense amount of data. Francis Crick Institute’s Etch A Cell - Powerhouse Hunt project trains volunteers to spot and trace each cell’s mitochondria, a process called manual segmentation. Manual segmentation is a major bottleneck to completing biological research because using computer systems to complete the work is still fraught with errors and, without enough volunteers, doing this work takes a really long time.
For the Monkey Health Explorer project, researchers studying the social behavior of rhesus monkeys on the tiny island Cayo Santiago off the southeastern coast of Puerto Rico need volunteers to analyze the monkeys’ blood samples. Doing so will help the team understand which monkeys are sick and which are healthy, and how the animals’ health influences behavioral changes.
Using the Zooniverse’s app on a phone or tablet, you can become a “ Science Scribbler ” and assist researchers studying how Huntington disease may change a cell’s organelles. The team at the United Kingdom's national synchrotron , which is essentially a giant microscope that harnesses the power of electrons, has taken highly detailed X-ray images of the cells of Huntington’s patients and needs help identifying organelles, in an effort to see how the disease changes their structure.
Oxford University’s Comprehensive Resistance Prediction for Tuberculosis: an International Consortium—or CRyPTIC Project , for short, is seeking the aid of citizen scientists to study over 20,000 TB infection samples from around the world. CRyPTIC’s citizen science platform is called Bash the Bug . On the platform, volunteers will be trained to evaluate the effectiveness of antibiotics on a given sample. Each evaluation will be checked by a scientist for accuracy and then used to train a computer program, which may one day make this process much faster and less labor intensive.
Out of This World
If you’re interested in contributing to astronomy research from the comfort and safety of your sidewalk or backyard, check out Globe at Night . The project monitors light pollution by asking users to try spotting constellations in the night sky at designated times of the year . (For example, Northern Hemisphere dwellers should look for the Bootes and Hercules constellations from June 13 through June 22 and record the visibility in Globe at Night’s app or desktop report page .)
For the amateur astrophysicists out there, the opportunities to contribute to science are vast. NASA's Wide-field Infrared Survey Explorer (WISE) mission is asking for volunteers to search for new objects at the edges of our solar system with the Backyard Worlds: Planet 9 project .
Galaxy Zoo on Zooniverse and its mobile app has operated online citizen science projects for the past decade. According to the project description, there are roughly one hundred billion galaxies in the observable universe. Surprisingly, identifying different types of galaxies by their shape is rather easy. “If you're quick, you may even be the first person to see the galaxies you're asked to classify,” the team writes.
With Radio Galaxy Zoo: LOFAR , volunteers can help identify supermassive blackholes and star-forming galaxies. Galaxy Zoo: Clump Scout asks users to look for young, “clumpy” looking galaxies, which help astronomers understand galaxy evolution.
If current events on Earth have you looking to Mars, perhaps you’d be interested in checking out Planet Four and Planet Four: Terrains —both of which task users with searching and categorizing landscape formations on Mars’ southern hemisphere. You’ll scroll through images of the Martian surface looking for terrain types informally called “spiders,” “baby spiders,” “channel networks” and “swiss cheese.”
Gravitational waves are telltale ripples in spacetime, but they are notoriously difficult to measure. With Gravity Spy , citizen scientists sift through data from Laser Interferometer Gravitational-Wave Observatory, or LIGO , detectors. When lasers beamed down 2.5-mile-long “arms” at these facilities in Livingston, Louisiana and Hanford, Washington are interrupted, a gravitational wave is detected. But the detectors are sensitive to “glitches” that, in models, look similar to the astrophysical signals scientists are looking for. Gravity Spy teaches citizen scientists how to identify fakes so researchers can get a better view of the real deal. This work will, in turn, train computer algorithms to do the same.
Similarly, the project Supernova Hunters needs volunteers to clear out the “bogus detections of supernovae,” allowing researchers to track the progression of actual supernovae. In Hubble Space Telescope images, you can search for asteroid tails with Hubble Asteroid Hunter . And with Planet Hunters TESS , which teaches users to identify planetary formations, you just “might be the first person to discover a planet around a nearby star in the Milky Way,” according to the project description.
Help astronomers refine prediction models for solar storms, which kick up dust that impacts spacecraft orbiting the sun, with Solar Stormwatch II. Thanks to the first iteration of the project, astronomers were able to publish seven papers with their findings.
With Mapping Historic Skies , identify constellations on gorgeous celestial maps of the sky covering a span of 600 years from the Adler Planetarium collection in Chicago. Similarly, help fill in the gaps of historic astronomy with Astronomy Rewind , a project that aims to “make a holistic map of images of the sky.”
Get the latest Science stories in your inbox.
/https://tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/accounts/headshot/rachael.png)
Rachael Lallensack | READ MORE
Rachael Lallensack is the former assistant web editor for science and innovation at Smithsonian .
Conducting Internet Research
Considerations for participant protections when conducting internet research.

If an activity falls under the category of human subjects research, it is regulated by the federal government and Teachers College (TC) Institutional Review Board (IRB). TC IRB has provided a guide to help researchers determine if their activities can be considered human subjects research.
Internet research is a common practice of using Internet information, especially free information on the World Wide Web or Internet-based resources (e.g., discussion forums, social media), in research. This guide will cover considerations pertaining to participant protections when conducting Internet research, including:
- Private versus public spaces for exempt research
- Identifiable data available in public databases
- Minimizing risks when using sensitive Internet data
- Common Internet research approaches
The following information is from an NIH videocast . ( Odwanzy, L. (2014, May 8). Conducting Internet Research: Challenges and Strategies for IRBs [Video]. VideoCast NIH. https://videocast.nih.gov/summary.asp?Live=13932&bhcp=1 )
Private Versus Public Spaces for Exempt Research
Federal regulations define a category of human subjects research that is exempt from IRB review as:
“ Research that only includes interactions involving educational tests (cognitive, diagnostic, aptitude, achievement), survey procedures, interview procedures, or observation of public behavior (including visual or auditory recording) .”
With regards to online information, if the data is publicly available (such as Census data or labor statistics), it is usually not considered human subjects research. However, if the data includes identifiable information—meaning the data can be linked back to a specific individual—then it may need to undergo IRB review. Additionally, de-identified data pulled from a private source, such as data provided by a company, may also be considered human subjects research.
Public behavior is any behavior that a subject would or could perform in public without special devices or interventions. Public behavior on the Internet, however, is more difficult to pinpoint. Federal regulations indicate that an environment may be private if a reasonable user would consider their interactions in that environment to be private. To help identify public behavior on the Internet, consider:
- Typically, posts on a private or password-protected social media profile or site are not considered public behavior.
- Even if a website is publicly available, the information on the website may be protected by other measures (e.g., community guidelines, terms of use, etc.).
- Sites that require users to pay for access to their content (e.g., purchasing a dataset) are not always considered private, even if the information is behind a paywall.
- Discussions and chats on public forums, news broadcasts, and free podcasts or videos are typically considered public communications.
- Emails and person-to-person chat messages are often private, rather than public, communications.
- However, institutions may dictate that any activity on their devices (e.g., a company laptop or phone) is subject to review. In these cases, the institutions can limit an individual’s privacy.
- Some websites explicitly state that the interactions on their site are not to be used for research purposes.
- Other sites may not explicitly refuse research activities, but they may require users to be respectful of others’ experiences. Depending on the website, “respect” may have a variety of meanings, including respect of user privacy.
- Expectations of privacy may not always equate to the reality of privacy.
- For example, individuals may share personal information on an open forum because there is an expectation within the community that other users will respect their privacy. However, the community guidelines may not explicitly state that their website is private.
- Forums and websites directed towards youth may require extra precautions, as the youth may be on the website with or without their guardian’s permission.
- If a user shares media on a private profile, but then that media becomes publicly available through re-posts, the media should still be considered private. It is likely that a reasonable user would expect shares on private profiles to remain private.
- A site may only be open to certain types of users based on demographics or life experiences (e.g., cancer survivors, support groups for addiction, etc.). In these cases, a reasonable user may expect greater privacy based on the types of users they expect to interact with.
TC IRB will determine whether an Internet environment is private or public based on the IRB protocol submission.
Identifiable Data in Public Datasets
Identifiable data is information or records about a research participant that allows others to identify that person. Names, social security numbers, and bank account numbers are considered personal identifiers and are protected under the Health Insurance Portability and Accountability Act of 1996 (HIPAA). TC IRB has a blog posted on Understanding Identifiable Data that further explains the different types of identifiers. Data that includes personal identifiers does not fall under the Exempt category.
Other types of participant information may include indirect identifiers , such as birthdate, age, ethnicity, gender, etc. Taken alone, these pieces of information are not enough to identify any single participant. However, researchers have shown that certain combinations of these identifiers may identify participants. For example, Sweeny (2000) demonstrated that 87% of the United States population could be uniquely identified based solely on their ZIP code, gender, and date of birth.
It is important to remember that while data may be publicly available, it may still contain identifiable information. In these cases, the IRB will decide the risk to participants on a case-by-case basis. With Internet information, consider these to be possible identifiers:

Users may include their partial or full name in a username. When collecting usernames from a site, researchers should consider replacing usernames with pseudonyms.
IP addresses are unique identifiers for devices. Researchers should be wary of pairing IP addresses with other information.
Purchase Habits
With the surge in online shopping, individuals’ unique online purchase habits are shown to be possible identifiers.
Digital Images, Audio, & Video
Photos, audio recordings, or videos of an individual are typically considered identifiable, unless the images or audio are ascertained in a way that protects the subject’s identity.
Avatars or Profile Pictures
Although avatars and profile pictures may not include real photos of the user, it is possible that they were chosen because of a resemblance to the user.
Keystroke Dynamics or Typing Biometrics
The detailed information of an individual’s timing and rhythm when typing on a keyboard is a unique identifier. "Keystroke rhythm" measures when each key is pressed and released while a user is typing. These rhythm combinations are as unique to an individual as a fingerprint or a signature.
Minimizing Risk When Using Sensitive Internet Data
In cases where sensitive Internet data must be used for research purposes, researchers should take precautions to ensure the safety and privacy of participants. The nature of online research increases risk to participants in some areas. Researchers should develop a plan to minimize risk in the following areas:
- Reduced Participant Contact : when research is conducted over the Internet, researchers have limited or no direct contact with subjects. This makes it more difficult for researchers to gauge subjects' reactions to the study interventions.
- Researchers should think through multiple possibilities for interventions, debriefing, and follow-up, if applicable.
- Researcher and TC IRB contact information should be presented on the informed consent before beginning the study. This will ensure that participants know whom to contact if they have questions or concerns.
- Breach of Confidentiality: when storing or collecting data on devices connected to the Internet, there is a heightened risk for identifiable participant data to be leaked.
- TC IRB has published a Data Security Plan outlining best practices for securing and transmitting data. Researchers should implement these practices as they apply to their specific study.
- In the case of a breach of confidentiality, researchers must file an adverse event with TC IRB.
Common Internet Research Approaches
The Secretary’s Advisory Committee on Human Research Protections (SACHRP) has provided examples of common Internet research practices. These include elements of research conducted over the Internet. Below are possible examples of Internet research where human subjects may be involved:
- Existing datasets (secondary data analysis)
- Social media/blog posts
- Chat room interactions
- Amazon Mechanical Turk
- Social media
- Patterns on social media or websites
- Evolution of privacy issues
- Spread of false information
- Online shopping patterns and personalized digital marketing
- Online interventions such as “nudging"
Increased Internet use for research requires researchers and IRBs to become familiar with Internet research-related topics and concerns. Research submitted to the IRB will be reviewed on a case-by-case basis. The Institutional Review Board at Teachers College will make the final determination of whether a study requires review. Researchers should email [email protected] if they have any questions or concerns about their study design and whether it should be IRB reviewed.
Institutional Review Board
Address: Russell Hall, Room 13
* Phone: 212-678-4105 * Email: [email protected]
Appointments are available by request . Make sure to have your IRB protocol number (e.g., 19-011) available. If you are unable to access any of the downloadable resources, please contact OASID via email [email protected] .
Internet Research
Issue(s) available: 166 – From Volume: 1 Issue: 1 , to Volume: 34 Issue: 7

- Issue 7 2024 Open Access Issue in Progress
- Issue 4 2024
- Issue 3 2024
- Issue 2 2024
- Issue 1 2024 The Opportunities and Challenges in the Metaverse
- Issue 7 2023 Open Access Issue
- Issue 6 2023
- Issue 5 2023 The social, ethical, economic, and political implications of misinformation
- Issue 4 2023
- Issue 3 2023
- Issue 2 2023
- Issue 1 2023
- Issue 7 2022 Open Access Issue
- Issue 6 2022
- Issue 5 2022
- Issue 4 2022
- Issue 3 2022
- Issue 2 2022 Interpretable AI-enabled Online Behavior Analytics
- Issue 1 2022
- Issue 6 2021 The Bright Side and the Dark Side of Digital Health
- Issue 5 2021
- Issue 4 2021
- Issue 3 2021
- Issue 2 2021
- Issue 1 2021
- Issue 6 2020
- Issue 5 2020
- Issue 4 2020
- Issue 3 2020
- Issue 2 2020
- Issue 1 2020
- Issue 6 2019
- Issue 5 2019 The Sharing Economy: Promises and Challenges
- Issue 4 2019
- Issue 3 2019 Internet research using partial least squares
- Issue 2 2019 Online and mobile gaming
- Issue 1 2019
- Issue 5 2018 The Dark Side of Social Media
- Issue 4 2018
- Issue 3 2018
- Issue 2 2018
- Issue 1 2018
- Issue 5 2017
- Issue 4 2017
- Issue 3 2017
- Issue 2 2017
- Issue 1 2017
- Issue 5 2016
- Issue 4 2016
- Issue 3 2016
- Issue 2 2016 Internet of Things
- Issue 1 2016
- Issue 5 2015
- Issue 4 2015
- Issue 3 2015
- Issue 2 2015
- Issue 1 2015
- Issue 5 2014
- Issue 4 2014
- Issue 3 2014
- Issue 2 2014
- Issue 1 2014
- Issue 5 2013 The power of prediction with social media
- Issue 4 2013
- Issue 3 2013
- Issue 2 2013
- Issue 1 2013
- Issue 5 2012
- Issue 4 2012
- Issue 3 2012
- Issue 2 2012
- Issue 1 2012
- Issue 5 2011
- Issue 4 2011
- Issue 3 2011
- Issue 2 2011
- Issue 1 2011
- Issue 5 2010
- Issue 4 2010 Internet Research 20th Anniversary Commemorative Issue
- Issue 3 2010 Intelligent eservices applied to B2C ecommerce
- Issue 2 2010
- Issue 1 2010
- Issue 5 2009
- Issue 4 2009
- Issue 3 2009
- Issue 2 2009 Intelligent ubiquitous computing applications and security issues
- Issue 1 2009
- Issue 5 2008
- Issue 4 2008
- Issue 3 2008
- Issue 2 2008 Information credibility on the web
- Issue 1 2008
- Issue 5 2007 Selected research papers from the TERENA networking conference 2007
- Issue 4 2007
- Issue 3 2007
- Issue 2 2007
- Issue 1 2007 The Sixth International Network Conference INC, 2006
- Issue 5 2006 Apartthemed issue on internet security
- Issue 4 2006
- Issue 3 2006
- Issue 2 2006 Privacy and anonymity in the digital era
- Issue 1 2006
- Issue 5 2005
- Issue 4 2005
- Issue 3 2005
- Issue 2 2005
- Issue 1 2005
- Issue 5 2004
- Issue 4 2004
- Issue 3 2004
- Issue 2 2004
- Issue 1 2004
- Issue 5 2003
- Issue 4 2003
- Issue 3 2003
- Issue 2 2003
- Issue 1 2003
- Issue 5 2002
- Issue 4 2002
- Issue 3 2002
- Issue 2 2002
- Issue 1 2002
- Issue 5 2001
- Issue 4 2001
- Issue 3 2001
- Issue 2 2001
- Issue 1 2001
- Issue 5 2000
- Issue 4 2000
- Issue 3 2000
- Issue 2 2000
- Issue 1 2000
- Issue 5 1999
- Issue 4 1999
- Issue 3 1999
- Issue 2 1999
- Issue 1 1999
- Issue 5 1998
- Issue 4 1998
- Issue 3 1998
- Issue 2 1998
- Issue 1 1998
- Issue 4 1997
- Issue 3 1997
- Issue 2 1997
- Issue 1 1997
- Issue 4 1996
- Issue 2/3 1996
- Issue 1 1996
- Issue 4 1995
- Issue 3 1995
- Issue 2 1995
- Issue 1 1995
- Issue 4 1994
- Issue 3 1994
- Issue 1 1994
- Issue 4 1993
- Issue 3 1993
- Issue 2 1993
- Issue 1 1993
- Issue 4 1992
- Issue 3 1992
- Issue 2 1992
- Issue 1 1992
- Issue 2 1991
- Issue 1 1991
The impact of social support chatbots on patients’ value co-creation behavior in online health communities: a moderated mediation model
Online health communities (OHCs) have emerged on the Internet, substantially changing the conventional healthcare delivery model. Despite this emergence, the lack of patient…
From resistance to acceptance: developing health task measures to boost mHealth adoption among older adults: mixed-methods approach and innovation resistance
There are two main objectives in this study. First, we aim to develop a set of constructs for health task management support (HTMS) features to evaluate which health-related tasks…
How representational fidelity affects sociability and cyberself engagement in the Metaverse
This study examines how users' multidimensional representational fidelity factors affect sociability and cyberself engagement in the Metaverse platform; that is, how they interact…
Digital-intelligence transformation, for better or worse? The roles of pace, scope and rhythm
Although digital transformation (DT) has emerged as an important phenomenon for both research and practices, the influences remain inconclusive and inadequate. The emerging…
“I like the sound of that”: understanding the effectiveness of audio in ads
Sports advertisements such as the Super Bowl showcase products and brands that have invested increasingly large sums financially to gain viewers’ attention. However, how audio…
The effect of blockability affordance on confrontation against cyberbullying on social networking sites: theoretical and methodological implications
Social networking sites (SNS) have become popular mediums for individuals to interact with others. However, despite the positive impact of SNS on people’s lives, cyberbullying has…
The golden zone of AI’s emotional expression in frontline chatbot service failures
The purpose of this study is twofold: first, to identify the categories of artificial intelligence (AI) chatbot service failures in frontline, and second, to examine the effect of…
Social comparisons at social networking sites: how social Media-induced fear of missing out and envy drive compulsive use
A major portion of our social interaction now occurs online, facilitated by social networking sites (SNSs) that enable people to connect and communicate at will. However, the…
Exploring the impact of forced teleworking on counterproductive work behavior: the role of event strength and work-family conflict
Most employees are forced to telework due to the COVID-19 pandemic, which brings novel, disruptive, and critical challenges both in work and life. Based on event system theory and…
Is information normalization helpful in online communication? Evidence from online healthcare consultation
This study aims to investigate the role of information normalization in online healthcare consultation, a typical complex human-to-human communication requiring both effectiveness…
Effect of autonomous vehicle-related eWOM on (fe)males’ attitude and perceived risk as passengers and pedestrians
This study investigates how autonomous vehicle (AV)-related electronic word-of-mouth (eWOM) of different polarities affects attitude and perceived risk from the perspectives of…
Optimizing live streaming engagement through store atmospheric cues: exploring prosocial behavior and social comparison—insights from streamers and viewers
Live Streaming Marketing has emerged as a transformative medium, facilitating real-time product promotion and brand messaging and reshaping consumer engagement. However, knowledge…
Gamification as a panacea to workplace cyberloafing: an application of self-determination and social bonding theories
Gamification has been constantly demonstrated as an effective mechanism for employee engagement. However, little is known about how gamification reduces cyberloafing and the…
Constant or inconstant? The time-varying effect of danmaku on user engagement in online video platforms
As an emerging video comment feature, danmaku is gaining more traction and increasing user interaction, thereby altering user engagement. However, existing research seldom…
CEO social media celebrity status and credit rating assessment
This paper aims to investigate the effect of CEO social media celebrity status on credit ratings and to determine whether potential threats on the CEO celebrity status negatively…
Potential treatments of technology addiction: insights for information systems scholars
In this current review, we aimed to understand technology addiction interventions and provide guidelines for IS scholars to use IT to prevent or attenuate technology addiction.
Platform control and multi-realized platform benefits: a meta-analysis
Platform owners need to encourage yet control complementors in ways that generate benefits. Retaining too much control can restrict innovation and knowledge flows; giving up too…
Corporate social responsibility and firm value: exploring the moderating effects of information technology-enabled knowledge capabilities
A substantial amount of research has examined the firm value impact of corporate social responsibility (CSR). Nevertheless, the findings have been inconsistent, prompting…
Seeing the forest and the trees: a meta-analysis of the antecedents to online self-disclosure
A wealth of studies have identified numerous antecedents to online self-disclosure. However, the number of competing theoretical perspectives and inconsistent findings have…
Understanding first aid knowledge adoption on social media with an extended information adoption model
Social media provides a convenient way to popularise first aid knowledge amongst the general public. So far, little is known about the factors influencing individuals’ adoption of…
How emotions affect the outcomes of information overload: information avoidance or information consumption?
Information overload has become ubiquitous during a public health emergency. The research purpose is to examine the role of mixed emotions in the influence of perceived…
Does corporate digitalization improve disclosure quality?
This study investigates the potential association between corporate digitization and disclosure quality, and how this relationship is moderated by non-state ownership and…
How perceived overload leads to WeChat passive usage intention: the mediating roles of social network exhaustion and discontented feeling
The principal purposes of the research are to empirically investigate three forms of perceived overload on social media and shed light on their associations with users’ passive…
Good for all, good for me: the influences of dedication- and constraint-based switching barriers on user-generated contributions
Prior research on user-generated content (UGC) contributions has primarily focused on self-centered or other-centered motives, paying limited attention to the concept of…
The role of omnichannel integration and digital value in building brand trust: a customer psychological perception perspective
In the dynamic landscape of the digital economy, companies are increasingly adopting omnichannel integration strategies to enhance customer experiences. However, the interplay…
Seeking social support on social media: a coping perspective
This paper aims to examine the strength characteristics of a stressful event (i.e. novelty, disruption, and criticality) as factors that drive people’s social media use for…
Value implications of followers in social marketplaces: insights into ego network structures
In social marketplaces, follower ego networks are integral social capital assets for online sellers. While previous research has underscored the positive impact of the follower…
My online self identifies with you, but my offline self skips you: the duality of online and offline personalities in identification with the endorser
The current study examines a novel model that examines how the online and offline or general personality of the same person predicts social identification with the endorser in a…
Pay with a smile? Modelling the continuance use intention of facial recognition payment
This study synthesises the self-determination theory (SDT), expectation-confirmation model (ECM), and protection motivation theory (PMT) to formulate an integrated theoretical…
How do small-to-medium-sized e-commerce businesses stay competitive? Evidence on the critical roles of IT capability, innovation and multihoming
Small-to-medium-sized enterprises (SMEs) in e-commerce often invest in information technology (IT) to stay competitive. However, whether and how IT capability (ITC) translates…
A study on the cross-platform influence mechanism of physicians’ live streaming behavior on performance
The advent of online live streaming platforms (OLSPs) and online health communities (OHCs) has expedited the integration of traditional medical services with Internet new media…
Selling by contributing: the monetization strategy of individual content providers in the light of human brand
The integration of social media and e-commerce has resulted in a rising phenomenon among individual content providers (ICPs), who used to offer free content, to provide consumers…
How do NPOs’ topics and moral foundations in gun-related issues influence public engagement on Twitter?
Drawing on the moral foundations theory (MFT), we examine what nonprofit organizations (NPOs) discuss and how NPOs engage in gun-related issues on Twitter. Specifically, we…
Archetypes of influential users in social question-answering sites
This paper seeks to address the following two research questions. RQ1: What are the influential user archetypes in the social question-answering (SQA) community? RQ2: To what…
Social influence and the choice of product upgrades: evidence from virtual product adoption in online games
Previous studies on social influence and virtual product adoption have mainly taken users’ purchase behavior as a dichotomous variable (i.e. purchasing or not). Given the…
Mitigating perceived overload of communication visibility: the role of ESM policies
This study aims to explore how communication visibility affects employees’ work engagement from the negative perspective of employees’ perceived overload in the context of…
Sharenting in China: perspectives from mothers and adolescents
Mothers sharing images and information on social media about their children is a contemporary cultural norm. While the practice has been heavily discussed in popular media, there…
Inducing shoppers’ impulsive buying tendency in live-streaming: integrating signaling theory with social exchange theory
The increasing popularity of live-streaming commerce has provided a new opportunity for e-retailers to boost sales. This study integrated signaling theory and social exchange…
Exploring the dual routes in influencing sales and adoption in augmented reality retailing: a mixed approach of SEM and FsQCA
This study investigates augmented reality (AR) retailing and attempts to develop a profound understanding of consumer decision-making processes in AR-enabled e-retailing.
Examining the effects of cognitive load on information systems security policy compliance
Enforcing employee compliance with information systems security policies (ISSP) is a herculean task for organizations as security breaches due to non-compliance continue to soar…
Not all IT addictions are handled equally: guilt-vs shame-driven coping with IT addiction
We build on the transactional model of stress and coping and the appraisal theory of emotions to theorize how users cognitively and emotionally cope with IT addiction-induced…
Stimulating positive reviews by combining financial and compassionate incentives
The objective of this study is to investigate the interaction effect between incentive type (financial and compassionate incentives) and the ethicality of merchant strategy on…
Rethinking privacy in the Internet of Things: a comprehensive review of consumer studies and theories
This study aims to analyze and synthesize literature on consumer privacy-related behavior and intelligent device-to-device interactions within the Internet of Things (IoT).
Beyond lazy; external locus of control as an alternative explanation for the privacy paradox
The privacy paradox refers to the situation where users of online services continue to disclose personal information even when they are concerned about their privacy. One recent…
Service quality in cloud gaming: instrument development and validation
The global market for cloud gaming is growing rapidly. How gamers evaluate the service quality of this emerging form of cloud service has become a critical issue for both…
How tie strength influences purchasing intention in social recommendation: evidence from behavioral model and brain activity
Social recommendation has been recognized as a kind of e-commerce with large potential, but how social recommendations influence consumer decisions is still unclear. This paper…
Spillover effects of data breach on consumer perceptions: evidence from the E-commerce industry
This study aims to explore the spillover effects of data breaches from a consumer perspective in the e-commerce context. Specifically, we investigate how an online retailer’s data…
Generativity of enterprise IT infrastructure for digital innovation
Digital innovation requires organizations to reconfigure their information technology infrastructure (ITI) to cultivate creativity and implement fast experimentation. This…
Building bonds: an examination of relational bonding in continuous content contribution behaviors on metaverse-based non-fungible token platforms
The proliferation of non-fungible token (NFT)-based crypto-art platforms has transformed how creators manage, own and earn money through the creation, assets and identity of their…
A meta-analysis of antecedents and consequences of trust in the sharing economy
Trust plays a crucial role in overcoming uncertainty and reducing risks. Uncovering the trust mechanism in the sharing economy may enable sharing platforms to design more…
The role of para-social relationship in live streaming virtual gift purchase: a two-stage SEM-neural network analysis
Despite the burgeoning popularity of virtual gifting in live streaming, research lacks an in-depth understanding of the drivers behind this behavior. Using para-social…
Effect of consistency of the review set on causal attribution: the moderating roles of repeating purchase cues and product knowledge
The study examines the potential moderating effects of repeating purchase cues and product knowledge on the relationship between the varying consistency of the review set and…
Longitudinal relationship between parental and adolescent smartphone addiction: serial mediating effects of adolescent self-esteem and depression
This study longitudinally investigated the predictors and mediators of adolescent smartphone addiction by examining the impact of parental smartphone addiction at T1 on adolescent…
Understanding users' voice assistant exploration intention: unraveling the differential mechanisms of the multiple dimensions of perceived intelligence
The purpose of this study is to develop a framework for the perceived intelligence of VAs and explore the mechanisms of different dimensions of the perceived intelligence of VAs…
Moment or movement – the heterogeneous impact of the Black Lives Matter movement on personal and societal charitable crowdfunding campaigns
Whenever social injustice tackled by social movements receives heightened media attention, charitable crowdfunding platforms offer an opportunity to proactively advocate for…
Consumer vulnerability: understanding transparency and control in the online environment
In the online environment, consumers increasingly feel vulnerable due to firms’ expanding capabilities of collecting and using their data in an unsanctioned manner. Drawing from…
How does social media use in the workplace affect employee voice? Uncovering the mediation effects of social identity and contingency role of job-social media fit
Employee voice is crucial for organizations to identify problems and make timely adjustments. However, promoting voice in organizations is challenging. This study aims to…
Fostering the digital mindset to mitigate technostress: an empirical study of empowering individuals for using digital technologies
Technostress reduces employees' work performance and increases their turnover intentions, such that technostress harms organizations' success. This paper investigates how the…
How review content, sentiment and helpfulness votes jointly affect trust of reviews and attitude
We investigate the joint impacts of three trust cues – content, sentiment and helpfulness votes – of online product reviews on the trust of reviews and attitude toward the…
Gaining customer engagement in social media recovery: the moderating roles of timeliness and personalization
This research investigates the role of customer forgiveness as the result of online service recovery transparency in predicting customer engagement. It also examines the…
Using machine learning to investigate consumers' emotions: the spillover effect of AI defeating people on consumers' attitudes toward AI companies
The purpose of this study is to investigate consumers' emotional responses to artificial intelligence (AI) defeating people. Meanwhile, the authors investigate the negative…
Factors influencing TikTok-based user purchase intention: comparison between potential customers and repeat customers
The purpose of this paper is to examine how different types of user experience in TikTok impact purchase intention via commitment to the influencer and commitment to the platform…
Fake news detection using machine learning: an adversarial collaboration approach
Purveyors of fake news perpetuate information that can harm society, including businesses. Social media's reach quickly amplifies distortions of fake news. Research has not yet…
What enhances or worsens the user-generated metaverse experience? An application of BERTopic to Roblox user eWOM
Given its growing economic potential and social impact, this study aims to understand the motivations and concerns regarding metaverse usage. It identifies user needs and risks…
Motivation for writing long online reviews: a big data analysis of an anime community
Based on self-determination theory (SDT), this study aims to determine the motivation factors of reviewers writing long reviews in the anime industry.
Motivational profile and knowledge creation in eSports: examining the roles of mutualistic co-presence
Research on knowledge creation within eSports learning is scarce. This study extends the understanding of competition-oriented collaborative learning in eSports by examining the…
Performance implications of match between social media–enabled interactions and contracts in interfirm governance
Integrating transaction costs economics and task-technology fit theory, this study distinguishes two categories of social media–enabled interactions, namely task-related…
Value creation for online collaboration between doctors and medical institutions: empirical evidence from online health communities
Doctor–medical institution collaboration (DMIC) services are an emerging service mode in focal online health communities (OHCs). This new service mode is anticipated to affect…
Herd behavior in social commerce: understanding the interplay between self-awareness and environment-awareness
This study investigates how individuals' self-awareness (specifically, private and public self-awareness) and environment-awareness (perceived expertise, similarity and…
Social media as a living laboratory for researchers: the relationship between linguistics and online user responses
Today, individuals use social media to express their opinions and feelings, which offers a living laboratory to researchers in various fields, such as management, innovation…
A mixed-methods investigation of the factors affecting the use of facial recognition as a threatening AI application
Artificial intelligence (AI) applications pose a potential threat to users' data security and privacy due to their high data-dependence nature. This paper aims to investigate an…
Wealth effects of firm's strategic technology investments: evidence from Ethereum blockchain
Ethereum-based blockchain technology (EBT) affords members of the Enterprise Ethereum Alliance (EEA) a market advantage in deploying blockchain within their organizations…
Effect of the fit between situational regulatory focus and feedback focus on customers' co-design behavior
Customers' co-design behavior is an important source of knowledge for product innovation. Firms can regulate the focus of information interaction with customers to set goals and…
Learning for success: understanding crowdfunding relaunch performance after initial failures
Fierce competition in the crowdfunding market has resulted in high failure rates. Owing to their dedication and efforts, many founders have relaunched failed campaigns as a…
How intergroup counter-empathy drives media consumption and engagement
Social media is replete with malicious and unempathetic rhetoric yet few studies explain why these emotions are publicly dispersed. The purpose of the study is to investigate how…
It pays to be forthcoming: timing of data breach announcement, trust violation, and trust restoration
This research examines the relationship between the timeliness in announcing the discovery of a data breach and consumer trust in an e-commerce company, as well as later…
Determinants of debunking information sharing behaviour in social media users: perspective of persuasive cues
Sharing and disseminating debunking information are critical to correcting rumours and controlling disease when dealing with public health crises. This study investigates the…
Competitive peer influence on knowledge contribution behaviors in online Q&A communities: a social comparison perspective
Users' knowledge contribution behaviors are critical for online Q&A communities to thrive. Well-organized question threads in online Q&A communities enable users to clearly read…
Leading for employees' enterprise system ambidextrous use through contextual ambidexterity: the mediating role of user empowerment and moderating role of leader–member exchange
This study aims to develop a cross-level research model to explore the relationship between team-level contextual ambidexterity and employees' enterprise system (ES) ambidextrous…
The impacts of within-task and between-task personal Internet usage on employee creative performance: the moderating role of perceived organisational support
Employees' personal Internet usage (PIU) has become increasingly common at work. It is important for both researchers and managers to understand how PIU affects employee creative…
Online date, start – end:
Copyright holder:, open access:.
- Dr Christy Cheung
Further Information
- About the journal (opens new window)
- Purchase information (opens new window)
- Editorial team (opens new window)
- Write for this journal (opens new window)
All feedback is valuable
Please share your general feedback
Report an issue or find answers to frequently asked questions
Contact Customer Support

- About the Center
- Center Leadership
- The Disruption Project
- Senior Fellows
- Research Fellows
- Board of Governors
- World Internet Project: International Partners
- Research Overview
World Internet Project
- Digital Future Project
- COVID Reset Project
- The Future of Transportation Project
- The Future of Money and Banking
- Jeffrey Cole: Perspectives on the Digital Realm
- Center Strategic Advisor Brad Berens
- All columns
- Reports Overview
- The Future of Money and Banking Project
- Television Violence Reports
We have created a growing body of data and insights on the impact of the Internet on users and non-users – behavior that supports the needs of corporate and public agency leaders to understand the impact of the Internet and stay ahead of the changes that online technology is bringing worldwide.
The World Internet Project operates through the Center for the Digital Future in collaboration with 39 partner countries. Studies explore the evolution of communication technology through findings on more than 80 subject areas in broad categories that include:
- Internet users and non-users
- Information-seeking online
- Access to online services
- Politics and the Internet
- Online media use
- Media reliability and importance
- User-generated content and social media
- Online entertainment
- Online purchasing
- Personal privacy
- Online communication
- Credit card security
- Offline media use
- The Internet and education
Visit the World Internet Project website .
List of World Internet Project partners . __________
The World Internet Project Reports
World Internet Project Report: Ninth Edition (2018) Participants: Cyprus, Middle East (Egypt, Lebanon, Qatar, Saudi Arabia, Tunisia, United Arab Emirates), France, Sweden, Taiwan, United States Download report
World Internet Project Report: Eighth Edition (2017) Participants: Egypt, Greece, Lebanon, New Zealand, Qatar, Saudi Arabia, Sweden, Switzerland, Taiwan, Tunisia, United Arab Emirates, and the United States. Download report
World Internet Project Report: Seventh Edition (2016) Participants: Cyprus, Czech Republic, Israel, Russia, Sweden, Taiwan, and the United States. Download report
World Internet Project Report: Sixth Edition (2015) Participants: Australia, Bahrain, Chile, China, Egypt, Italy, Jordan, Lebanon, New Zealand, Poland, Qatar, Saudi Arabia, Spain, Sweden, Switzerland, Tunisia, United Arab Emirates, the United Kingdom, the United States, and Uruguay Download report
World Internet Project Report: Fifth Edition (2013) Participants: Cyprus, Mexico, Poland, Russia, South Africa, Sweden, Taiwan, United States Download report
World Internet Project Report: Fourth Edition (2012) Participants: Australia, Canada, Colombia, Italy, Mexico, New Zealand, Poland, Spain, Sweden, Switzerland, United Kingdom Download report
World Internet Project Report: Third Edition (2012) Participants: Australia, Chile, Colombia, Cyprus, Hungary, Israel, Japan, Mexico, New Zealand, Poland, Portugal, Sweden, Taiwan, United Arab Emirates, United Kingdom, United States Download report
World Internet Project Report (2010) Participants: Chile, Colombia, Cyprus, Czech Republic, Italy, Macao, Mexico, Portugal, Sweden, United States. Download report
World Internet Project Report (2009) Participants: Australia, Canada, China, Colombia, Czech Republic, Hungary, Israeli, Macao, New Zealand, Singapore, Sweden, United Kingdom, United States Download report
Our teams leverage research developments across domains to build tools and technology that impact billions of people. Sharing our learnings and tools to fuel progress in the field is core to our approach.

Our resources are available to everyone
We regularly share datasets, tools and services with the broader scientific community to be used, shared, and built on.

Network of Interdisciplinary Internet & Society Research Centers
The global Network of Internet & Society Centers (NoC) is a collaborative initiative among over 100 Centers with a focus on interdisciplinary research on the development, social impact, policy implications, and legal issues concerning the Internet. For more information please visit https://networkofcenters.net .
Our Work 12

Global AI Regulation: Protecting Rights; Leveraging Collaboration
Policy experts from Africa, Europe, Latin America, and North America outlined next steps for global AI regimes and networked capacity building
BKC Senior Director of Programs and Strategy Lis Sylvan summarizes the Global Network of Internet and Society Research Center's spring learning call, which gathered experts on the…


Co-Designing Generative Futures: A Global Conversation About AI
BKC hosted an international workshop to address the opportunities and challenges of generative AI...

BKC incorporating "#GoodID" into research and programs
#GoodID, an effort to catalyze constructive conversation around digital identity, will be a part of the Center's research and programming in the coming year.

BKC Research Clinic Explores Challenges & Opportunities of Public Sector AI Policy in Partnership with City of Helsinki
Early career scholars from around the world navigate the legal, technical, social, and ethical dimensions of successful implementation of AI policy
BKC announces a new education program bringing students together to examine AI policy in a real-world context

Research sprint participants explore digital transformation in time of crisis with focus on education
Students from all over world join international dialogue on the ethics of digitalization

International Dialogue on “The Ethics of Digitalisation” Kicks Off in Berlin
BKC Joins German President, HIIG, Digital Asia Hub, and NoC to Launch Global Interdisciplinary Research on Digital Transformation and Policy
We are pleased to announce a new joint project by the Global Network of Internet & Society Centers (NoC) exploring ”The Ethics of Digitalisation: From Principles to Practice.”…

Global Perspectives on Data Collection, Contact Tracing, and COVID-19
Network of Centers discussion focuses on uses of data to combat COVID-19

Global Perspectives on COVID-19
Takeaways from a special discussion with the Global Network of Internet & Society Centers (NoC)

Designing Successful Governance Groups
Lessons for Leaders from Real-World Examples
The Berkman Center for Internet & Society, together with the Global Network of Internet and Society Research Centers (NoC), is pleased to announce the release of a new publication…

Liability of Online Intermediaries: New Study by the Global Network of Internet and Society Centers
The Global Network of Internet and Society Research Centers (NoC) and the Berkman Center for Internet & Society at Harvard University are pleased to announce the release of a new…

Multistakeholder as Governance Groups: New Study by Global Network of Internet and Society Centers
The Global Network of Internet and Society Research Centers (NoC) and the Berkman Center for Internet & Society at Harvard University are pleased to announce the release of a new…

Symposium on Internet-Driven Developments: Structural Changes and Tipping Points
Towards a Global Network of Internet and Society Centers
On December 6-8, 2012, the Berkman Center for Internet & Society hosted an international Symposium on Internet-Driven Developments: Structural Changes and Tipping Points (SCTP),…
Community 01
BKC Senior Director of Programs and Strategy Lis Sylvan and former BKC Research Assistant Niharika Vattikonda summarize the Global Network of Internet and Society Research Center…

Elisabeth Sylvan
Point of contact.

Armando Guio Español

Sandra Cortesi
Faculty Associate

Chinmayi Arun

Maja Bogataj Jančič

Lionel Brossi

Juan Carlos De Martin

Elizabeth Dubois

Christian Fieseler

Malavika Jayaram

Andres Lombana-Bermudez

Florian Martin-Bariteau

Sabelo Mhlambi

- Find Provider
We have detected that JavaScript has been disabled.
While we have taken every precaution to allow our site to run in every environment, it is highly recommended that you enable JavaScript for the best possible experience.
The Student's Internet Research Guide - 2024 Edition
Research skills are the foundation of academic growth. our 2024 edition equips students with the latest tools and techniques..

Lyndon Seitz - Editor-in-Chief
Date Modified: April 18, 2024
In today's digital age, internet research stands as an indispensable skill for students worldwide. As Bill Gates once remarked, "The Internet is becoming the town square for the global village of tomorrow." Recent studies indicate that 96.4% of students rely on the internet for academic research, emphasizing its pivotal role in education.
However, while the vast expanse of the internet offers immense resources, discerning credible information remains a challenge. This guide aims to equip students with strategies to navigate and harness the web's potential, ensuring academic rigor and success.
Understanding Internet Research
Basics of internet research for students.
Internet research refers to the systematic process of seeking, collecting, and evaluating online information to draw meaningful conclusions or aid in decision-making . Its significance is underscored by the rich reservoir of data and perspectives it unlocks for students, granting them access to a universe of knowledge beyond traditional textbooks.
Types of Internet Research
- Academic Research: Primarily focuses on scholarly pursuits, involving the utilization of journals, educational databases, and official publications to procure credible and in-depth information pertaining to various subjects.
- Comparative Research: This involves juxtaposing various sources, opinions, or datasets available online. It aids students in developing analytical acumen, enabling a multifaceted understanding of topics through comparative analysis.
- Data-driven Research: Grounded in statistical exploration, this type leverages online databases, government publications , and credible organizations’ resources to obtain factual, quantitative information essential for objective analytical assignments.
The diligent use of internet research is directly proportional to academic success . A student's capacity to discern quality sources, synthesize varied information, and utilize it effectively in their academic pursuits is a testament to not just their research acumen but also their readiness for higher education and professional life.
Challenges in Online Research
As the digital landscape burgeons with information, the complexities of sourcing, interpreting, and leveraging this information grow in tandem. It's not just about finding data anymore; it's about finding the right data and understanding its context .
Key Challenges in Online Research:
- Information Overload: With billions of pages at our fingertips, filtering pertinent information can be overwhelming. One must skillfully use search operators and specialized databases to hone in on relevant content.
- Evaluation of Credible Sources: Not all information is created equal. According to a report from the Stanford History Education Group, many students struggle to evaluate the reliability and credibility of online sources. It's essential to scrutinize the authority, accuracy, and objectivity of any source.
- Spotting Red Flags: The web is rife with skewed perspectives, intentionally false data, and biased content. Recognizing these pitfalls is a critical skill to prevent being misled.
- Avoiding Plagiarism: Directly lifting content from the web without proper attribution is not only unethical but can have serious academic and professional repercussions . Platforms like Turnitin and Copyscape have become essential tools to ensure originality.
The challenges of internet research are manifold, but with the right strategies and a discerning approach, one can transform these challenges into opportunities for enriched understanding.
Starting Your Research
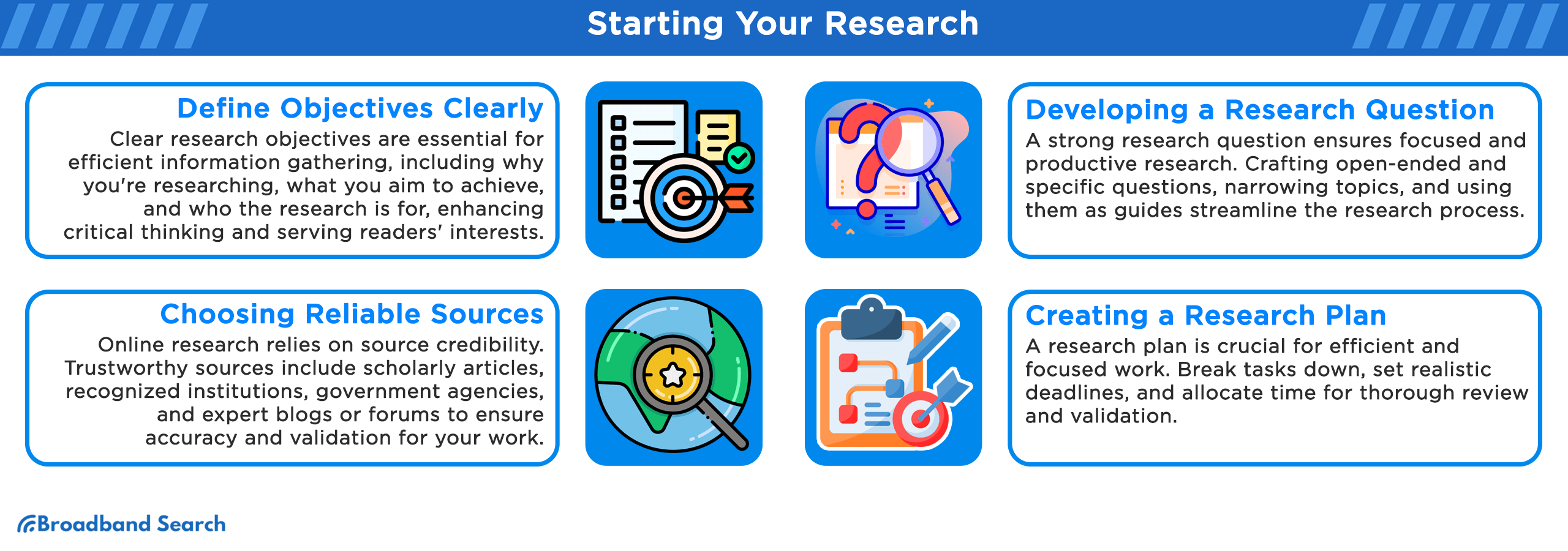
Define Objectives Clearly
Embarking on a research journey without a clear map can lead to wandering aimlessly in the vast ocean of information that the internet presents.
Starting your research rightly not only sharpens your focus but also streamlines the process, ensuring efficiency and accuracy. The fundamental step in this endeavor is to define the research objectives with clarity, acting as a guiding light throughout your journey.
- Purpose: The primary step in any research journey. It's about answering the 'why' of the research. What is the main goal? Whether it's understanding consumer behavior, exploring a historical event, or gauging the impact of a technological advancement, the purpose sets the tone and direction.
- Achievement: This answers the 'what' of the research. What milestones need to be reached? It can be gathering specific data, drawing certain insights, or producing a comprehensive report.
- Target Audience: Knowing the 'who' can shape the 'how' of research. Is the research intended for academics, businesses, policymakers, or general audiences? Tailoring the research to the needs and preferences of the intended audience ensures its relevance and usability.
Efficient research leads to well-informed arguments, fosters critical thinking, and elevates the quality of academic output . Moreover, by serving the genuine interests of its readers, the research becomes a beacon of knowledge, contributing significantly to the academic community and beyond.
Choosing Reliable Sources
In online research, source credibility is crucial to maintain integrity. Choosing reliable sources ensures accuracy and validates your work to critical readers , as scholarly work depends on trustworthy sources.
- Scholarly Articles: Peer-reviewed journals and publications are gold standards in research. They undergo rigorous evaluation by experts in the field , ensuring accuracy and credibility. Sources like Google Scholar or JSTOR can be invaluable.
- Recognized Institutions: Universities, research centers, and professional organizations often publish studies, papers, and reports. Their reputation hinges on the quality of information they disseminate, making them trustworthy sources.
- Government Agencies: Government publications, statistics, and reports are typically well-researched and factual. Websites with domains ending in '.gov' or similar official extensions indicate authentic government-associated resources.
- Expert Blogs and Forums: While they may lack the formal scrutiny of academic journals, expert-authored blogs or niche forums can offer insights, especially on contemporary or emerging topics. However, they always cross-reference their claims with established sources .
Developing a Research Question
The essence of fruitful research often lies in the strength of the question that guides it. A well-phrased research question not only provides clarity but also ensures that your exploratory journey remains productive, purposeful, and focused.
Crafting Questions
Forming open-ended and focused questions is crucial. While open-ended questions such as "What are the impacts of social media on mental health?" provide a broader perspective, focused questions like "How does social media usage among teenagers in the US correlate with anxiety levels?" delve into specifics, ensuring depth in research.
Focused Topics
A research project's success often hinges on the specificity of its subject matter. Instead of attempting to cover the vast expanse of a topic like "The history of art," narrowing it down to "The influence of Renaissance art on modern graphic design" can provide more actionable insights and allow for a thorough exploration.
Guided Search
A well-constructed research question is a researcher's compass. For instance, if one were to investigate the " Economic impact of the 2008 financial crisis on small businesses in New York ," search engines and databases can be used more effectively to filter relevant studies, articles, and data pertaining to that precise topic, making the process efficient.
The art of formulating a research question is a blend of curiosity and precision . In an age where the internet offers an overwhelming abundance of information, the ability to ask the right questions is the key to unlocking valuable insights.
Creating a Research Plan
Crafting a research plan offers a blueprint, illuminating each step of the process and ensuring efficiency and direction. Given the sea of information available online, this blueprint becomes especially pivotal in maximizing productivity and maintaining focus.
Task Breakdown
Deconstructing your research into granular tasks and steps ensures a systematic approach. For instance, researching the impact of AI in healthcare can be broken down into tasks like "Study AI algorithms," "Analyze AI applications in diagnostics," and "Evaluate AI's role in patient management."
Realistic Deadlines
Establishing a timeline fosters accountability and pace. If you're researching for a 10-page paper on "Sustainable Energy Solutions for Urban Areas" due in a month, you might allocate the first week for background reading, the next two for detailed research, and the final week for drafting and refining.
Review Time
No research is complete without thorough revision and validation. Setting aside ample time to revisit gathered information ensures accuracy and comprehensiveness . For a topic like "Blockchain in Financial Transactions," after accumulating data and drafting initial findings, dedicating a few days to validate sources, cross-check facts, and tighten arguments can make all the difference.
Developing Effective Research Strategies
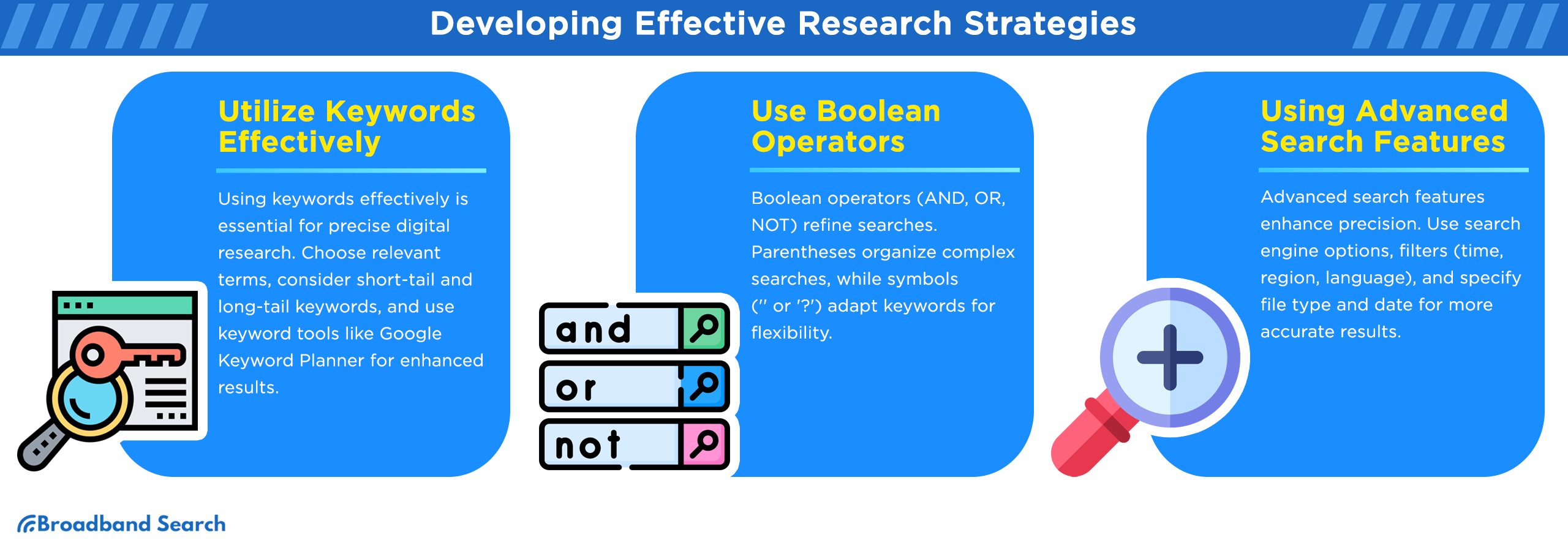
Utilizing Keywords Effectively
Keywords are crucial in digital research because they help filter and find relevant information in a vast digital archive. Using keywords effectively is not just about searching well; it's about getting precise and in-depth results in an age of information overload.
Relevant Keywords
Central to any search process, understanding and selecting appropriate search terms is paramount. For instance, while researching the "Impact of climate change on marine life," terms like "ocean acidification," "coral bleaching," and "sea temperature rise" can hone in on niche topics within the broader subject.
Long-tail vs Short-tail
Short-tail keywords, like "climate change," provide a broader scope, ideal for an initial exploratory phase. In contrast, long-tail keywords, such as "effects of climate change on Antarctic penguins," offer a narrow, in-depth perspective, beneficial for detailed investigations.
Keyword Tools
While search engines are powerful, tools like Google Keyword Planner can elevate the search experience. It provides keyword suggestions, search volume data, and competitive insights. Alternatives such as SEMrush or Ahrefs' Keywords Explorer can offer expanded functionalities, catering to diverse research needs.
Boolean Operators
Boolean operators act as a refined toolkit, enabling scholars to navigate vast datasets with surgical precision. Mastering these operators transforms searches from simple queries into strategic endeavors, streamlining access to desired content .
Using AND, OR, NOT
The Boolean operators AND, OR, NOT are the guardians of search relevance. Using "AND" unites terms, narrowing results (e.g., cats AND dogs). "OR" broadens searches by embracing multiple terms (e.g., cats OR dogs), while "NOT" excludes unrelated information (e.g., cats NOT lions).
Nested Searches
Parentheses breathe structure into complex searches. They help manage the chaos, allowing for intricate combinations of terms and operators, thus sharpening the sword of specificity. For example, using parentheses in a search like (cats OR dogs) AND (pets OR animals) refines and organizes the onslaught of information.
Truncation and Wildcards
Symbols like '' or '?' are the allies of adaptability in search queries, allowing for variations of keywords to be included. Truncation (e.g., teach) would embrace 'teacher', 'teaching', or 'teachable', while wildcards (e.g., wom?n) allow for flexibility, capturing terms like 'woman' or 'women'.
Using Advanced Search Features
Advanced search functionalities, often underutilized, are akin to a master key, unlocking doors to refined results. Their adept use can streamline the research process, bringing accuracy and efficiency to the forefront.
- Search Engine Features: Leverage specialized functionalities such as Google’s "verbatim" or "similar" searches to cultivate richer, more precise results. These features, when adeptly utilized, transform generic searches into focused, purpose-driven queries, offering a gateway to more relevant information.
- Filters: Applying filters like "time," "region," or "language," elevates the specificity of search outcomes. For instance, filtering news articles to display results from the past week can significantly refine the timeliness and relevance of the information retrieved, ensuring it aligns more closely with current trends or discussions.
- File Type and Date: Direct your search towards specific document types such as PDFs or PowerPoint presentations, or focus on publication dates to ensure the relevance of sourced materials. For example, seeking academic research papers published in the last two years and filtering for PDF file types can help locate the most recent scholarly discussions available in a ready-to-use format.
Evaluating Online Sources
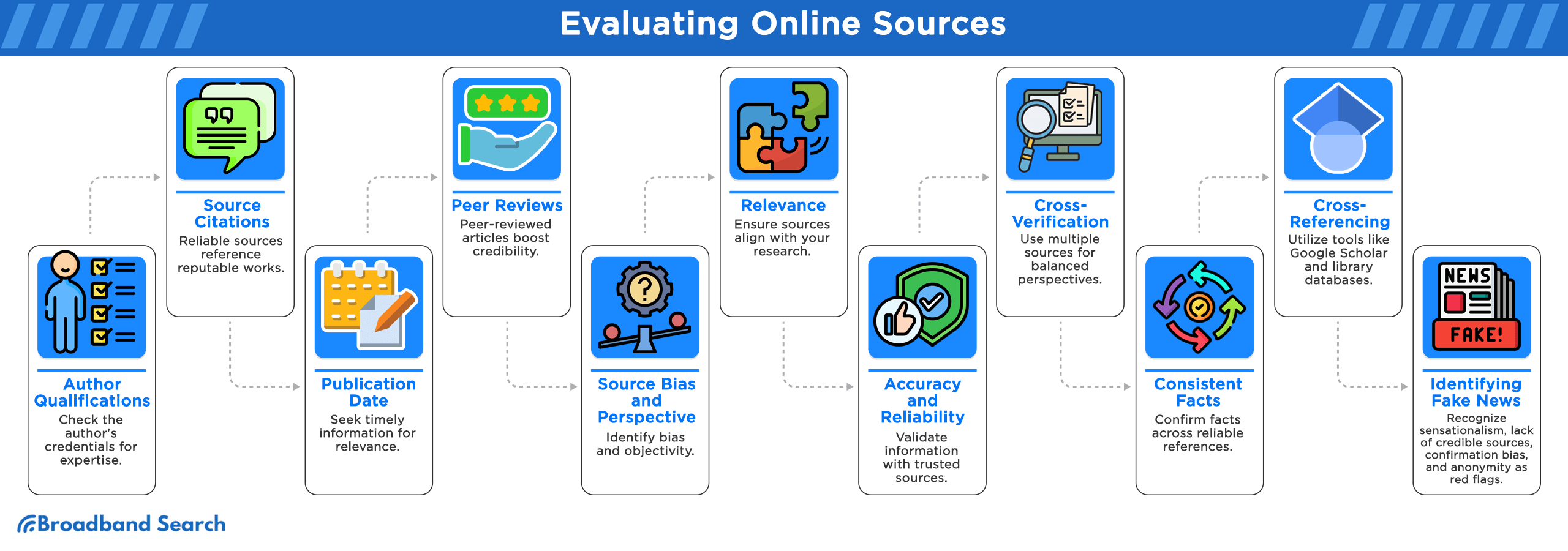
Criteria for Assessing Source Credibility
The credibility of sources shapes the foundation upon which our knowledge and arguments stand. But how do we differentiate the trustworthy from the deceptive? The following criteria offer a guiding light.
- Author Qualifications: A discerning eye towards the author's credentials is fundamental. For instance, a scientific article authored by a Ph.D. holder with expertise in the relevant field carries more weight , ensuring that the content is steeped in knowledge and experience.
- Source Citations: The robustness of a source is often reflected in its citations. A well-sourced article, referencing reputable and relevant works , stands as a pillar of reliability. For example, a health-related article citing recent medical journals demonstrates a strong foundation.
- Publication Date: Timeliness is key. An article on technology trends from a reputable source but dated five years ago may not contribute valuable, up-to-date insights. It's imperative to seek information that echoes the current state of knowledge or developments .
- Peer Reviews: In academic circles, peer-reviewed articles are golden standards. They undergo rigorous scrutiny, ensuring that the research presented is sound and validated by experts. For instance, in scientific research, journals like "Nature" and "Science" are esteemed for their peer-review process, bolstering the credibility of their publications.
Meticulous evaluation using these criteria doesn't just elevate the quality of research; it ensures integrity, fostering trustworthiness and excellence.
Understanding Source Bias and Perspective
In the age of information, discerning the neutrality of online content is paramount. As every source carries its undertones, identifying bias and recognizing objectivity becomes the linchpin of credible research.
Bias/Objectivity
Content often mirrors the perspective of its creator. For instance, a tech review may lean favorably towards a product if sponsored by its manufacturer, while independent reviewers might provide a more balanced assessment. Hence, researchers should cross-reference multiple sources, ensuring a holistic understanding devoid of undue influence .
Relevance to Your Topic
Ensure the source directly addresses your research query. For example, a study focusing on the impacts of social media on mental health is pertinent when researching mental wellness trends among teenagers in the digital age. This focused approach promotes relevant and valuable insights, bolstering the integrity of your research outcomes.
Accuracy and Reliability
Always validate the trustworthiness of information. For instance, a claim stating " 93% of global youth use social media daily " should be corroborated with reputable datasets or studies, such as those from Pew Research Center. Such a rigorous approach filters out discrepancies, ensuring research is rooted in undeniable facts.
Cross-Verification Techniques
Cross-verification stands as a researcher's sentinel, ensuring online information withstands scrutiny and consistently aligns with multiple trusted sources, thereby cultivating a garden of genuinely insightful and trustworthy knowledge.
Multiple Sources
The key to a well-rounded perspective lies in comparing information from various reliable sources.
- When researching climate change, cross-referencing data from the IPCC (Intergovernmental Panel on Climate Change), NASA, and NOAA (National Oceanic and Atmospheric Administration) ensures a comprehensive view.
- For political analysis, combining insights from The New York Times, The Guardian, BBC, and Al Jazeera offers a balanced outlook.
- In health research, verifying findings from the World Health Organization (WHO), CDC (Centers for Disease Control and Prevention), and respected medical journals reinforces credibility.
- Exploring tech trends becomes more insightful when data from MIT Technology Review, Wired, Forbes, BroadbandSearch and TechCrunch converge, providing multifaceted perspectives.
Consistent Facts
One of the cornerstones of evaluating online sources is identifying consistent facts across multiple reputable references. For instance, in researching the health benefits of a particular diet, cross-referencing sources like Mayo Clinic and Harvard Medical School can validate consistent claims about its positive impacts. This verification approach strengthens the credibility of the information and minimizes the influence of bias, fostering more reliable research outcomes .
Cross-referencing
Efficient cross-referencing is a key element in source evaluation, empowering researchers to navigate the digital landscape with precision. Utilizing specialized tools and strategies ensures accuracy and minimizes the influence of bias.
- Google Scholar: An invaluable resource for academics , it allows users to explore academic papers, patents, and legal opinions across multiple disciplines, aiding in thorough source comparison.
- Library Databases: University libraries often offer access to databases like JSTOR, facilitating cross-referencing across peer-reviewed journals.
- Fact-checking Websites: Platforms like Snopes or FactCheck.org verify claims, helping researchers debunk or substantiate information.
- Media Bias/Fact Check: This online resource rates news outlets on their bias and credibility, offering insights into the reliability of news sources.
Identifying Fake News and Misinformation
Spotting characteristics of misleading content misinformation and fake news are rampant online, threatening to erode trust in information sources. Understanding their common characteristics is essential:
- Sensationalism: Content with exaggerated claims or alarmist language, such as "Groundbreaking Cure Found for All Diseases!" often aims to evoke strong emotions , leading to uncritical acceptance.
- Lack of Credible Sources: Misleading information often lacks reputable references, making it challenging to verify claims. For example, an article claiming a new scientific discovery without citing any scientific journals or experts.
- Confirmation Bias: Misinformation often reinforces existing beliefs or prejudices, resonating with preconceived notions. This bias can cloud critical judgment , as individuals are more inclined to accept information that aligns with their beliefs.
- Anonymity or Pseudonymity: Sources that conceal the identity of authors or organizations may raise suspicion. Misinformation can thrive in the shadows, as accountability is often absent.
By recognizing these characteristics, individuals can become more adept at evaluating online sources and safeguarding themselves against the spread of misinformation.
Managing and Organizing Information
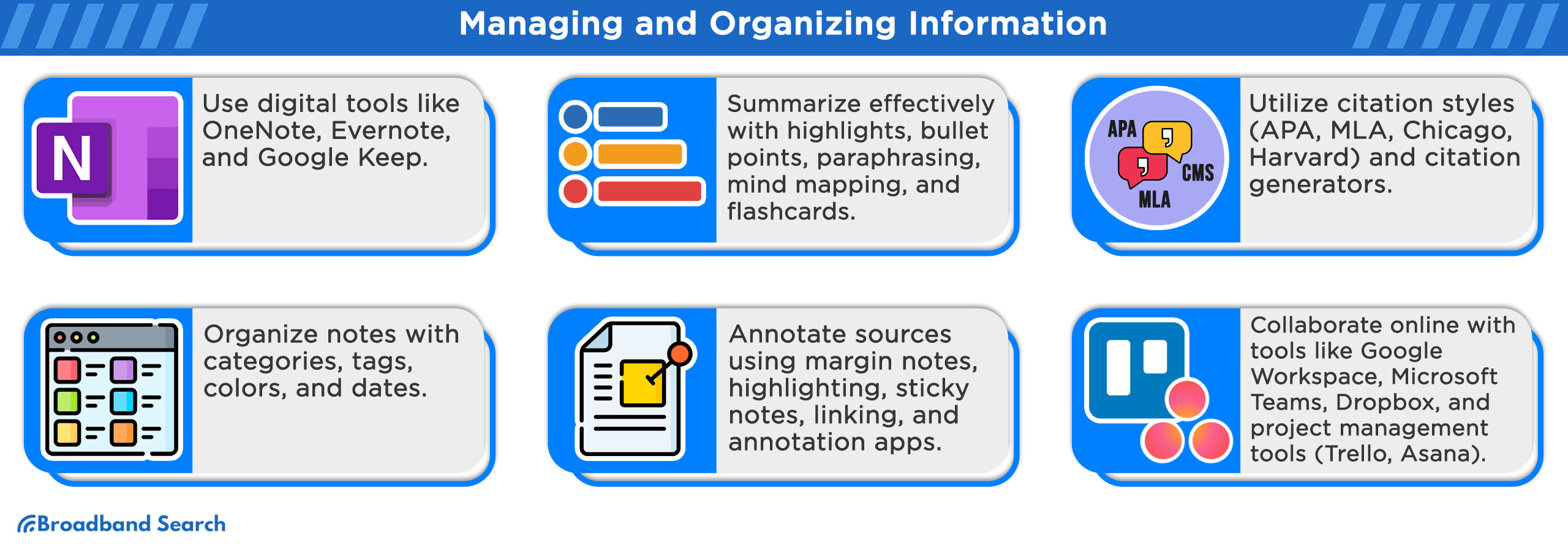
Effective Note-taking Strategies
Effective note-taking is a superpower. It's the compass that guides us through the mystery of knowledge, helping us capture insights, facilitate learning, and stay organized.
Digital Tools for Note-taking
Digital note-taking tools have revolutionized the way we capture and organize information . Discover how these versatile tools, like OneNote, Evernote, and Google Keep, empower users to streamline note-taking, enhance productivity, and effortlessly manage digital information, making them essential assets in the digital age.
- OneNote: Microsoft's OneNote is a versatile digital notebook that seamlessly integrates with other Microsoft apps. Users can create notebooks, organize notes into sections, and incorporate multimedia content. For instance, students can create dedicated notebooks for different subjects, enhancing study efficiency.
- Evernote: Evernote is a cross-platform note-taking app that excels in organization. It offers features like notebooks, tags, and a powerful search function. Business professionals can use Evernote to collate meeting notes, research, and ideas, streamlining workflow.
- Google Keep: Google Keep is a user-friendly, cloud-based note-taking app ideal for quick, accessible notes. Its integration with Google Workspace enhances collaboration. For instance, teams can use Google Keep to brainstorm ideas, create to-do lists, and share them seamlessly.
Strategies for Organizing Notes Effectively
Effective note-taking isn't just about jotting down information; it's about organizing it systematically:
- Create Categories: Organize notes by themes or subjects. For instance, a student can categorize biology notes into subtopics like "Cell Structure" or "Genetics."
- Use Tags: Apply descriptive tags to notes. In a work setting, tags like "Meeting Minutes" or "Project Updates" help quick retrieval.
- Color Coding: Assign colors to categories or priorities. For example, in a to-do list, urgent tasks can be highlighted in red.
- Date Stamping: Always date your notes. This practice aids in tracking the timeline of events or progress on projects.
- Table of Contents: Create a summary or table of contents for longer documents, facilitating quick navigation within extensive notes.
Effective Summarizing Techniques
Efficient summarizing techniques are essential for distilling complex information into concise, comprehensible notes:
- Highlight Key Points: Identify and underline the most important details within your notes to create a quick reference.
- Use Bullet Points: Condense information into bullet points, simplifying content while retaining crucial data.
- Paraphrase Succinctly: Rewrite information in your own words, ensuring clarity without losing the essence of the content.
- Mind Mapping: Visualize relationships between ideas with mind maps, aiding in grasping concepts holistically.
- Create Flashcards: Summarize key facts or concepts on flashcards for efficient revision and memorization.
Annotating Sources
Annotating sources enhances note-taking efficiency and comprehension:
- Margin Notes: Jot down key insights and thoughts directly in the margins of physical texts or PDFs, providing context and quick reference.
- Highlighting and Underlining : Use colors to emphasize essential information within texts, aiding later review and understanding.
- Sticky Notes: Digital sticky notes in applications like Adobe Acrobat or Microsoft Edge enable you to add comments, questions, or insights to specific pages.
- Linking to Notes: Create hyperlinks between notes and related source materials, facilitating seamless navigation and cross-referencing.
- Commenting and Annotating Apps: Apps like Notability and GoodNotes allow for in-depth annotations, including handwriting, diagrams, and multimedia, transforming notes into comprehensive resources.
Citation Styles
Citation styles are the unsung heroes of research, ensuring that credit is given where it's due and lending credibility to academic and professional work.
APA, MLA, Chicago, and Harvard
- APA (American Psychological Association): Predominantly used in social sciences and education , APA focuses on clarity, conciseness, and precision in citation. Example: "Smith, J. (2019). The Impact of Social Media on Adolescents."
- MLA (Modern Language Association): Commonly used in humanities, arts, and literature, MLA emphasizes author-page format for in-text citations . Example: "(Smith 22)."
- Chicago (Chicago Manual of Style): Adopted in history, arts, and social sciences, Chicago offers two styles—author-date and notes-bibliography. Example (Notes-Bibliography): Smith, John. "The Chicago Skyline." In Chicago: A Visual Journey, 2019, 45-60.
- Harvard: Widely used in various disciplines, Harvard employs author-date citations, prioritizing accessibility. Example: "(Smith 2019) "The Impact of Climate Change on Agriculture."
Citation Generators
Citation generators are invaluable aids in maintaining the accuracy and consistency of citations. Here are a few reliable tools and their correct usage:
- Citation Machine : A user-friendly tool that generates citations in various styles, from APA and MLA to Chicago and Harvard. Simply enter the source information, and it formats it correctly. This is ideal for students and researchers looking for a hassle-free experience.
- Zotero : A robust tool for collecting, organizing, and citing research materials. It seamlessly integrates with your browser to save sources and generate citations. Perfect for scholars managing extensive references.
- Mendeley : A reference manager and academic social network that assists in generating citations, creating bibliographies, and collaborating with peers. It's favored by researchers who want an all-in-one solution.
- EndNote : A comprehensive citation management software often used in research institutions, EndNote offers advanced features for organizing and citing sources. It's particularly useful for large-scale research projects.
These tools save time and ensure accurate citations, reducing the risk of errors in academic and professional work .
Collaborating with Peers Online
Online collaboration has become an indispensable tool for individuals and teams seeking to work together efficiently, regardless of geographical boundaries.
Leveraging Collaboration Tools
Google Workspace and Microsoft Teams offer real-time document editing and communication features, streamlining collaborative work for teams worldwide. Google Workspace allows seamless collaboration on documents, spreadsheets, and presentations, fostering productivity and teamwork. Meanwhile, Microsoft Teams facilitates secure online meetings and file sharing , making it ideal for remote collaboration.
Sharing Resources and Insights Effectively and Securely
With secure cloud storage and file-sharing platforms like Dropbox or SharePoint, you can easily distribute and access resources while maintaining data security. For instance, Dropbox Business provides secure file storage and sharing, ensuring efficient collaboration without compromising data integrity.
Coordinating and Managing Group Research Projects Online
Tools like Trello or Asana enable teams to manage projects efficiently. For example, Trello offers a visual project management approach with boards, lists, and cards, making it simple to assign tasks, track progress, and collaborate effectively on research projects.
These strategies empower you to collaborate seamlessly, sharing resources and knowledge while maintaining security and efficiency in an increasingly digital workspace.
Advanced Research Tools
Utilizing Academic Databases
Knowledge is power, and academic databases stand as digital treasure troves, offering access to a wealth of scholarly resources and research materials.
Access Methods
Navigating databases like PubMed, JSTOR, and Google Scholar involves utilizing specific search queries, filters, and advanced search options to unearth precise scholarly content.
Database Benefits
Academic databases offer curated, peer-reviewed content, ensuring the accuracy and reliability of research materials. In contrast, standard search engines may yield less credible sources , making databases indispensable for academic and professional research.
Subscription vs. Free
Subscription-based databases like ProQuest provide extensive collections of academic resources, while free databases like DOAJ (Directory of Open Access Journals) offer open-access content. Subscription databases often grant access to premium research journals and archives , while free databases promote open knowledge sharing.
Essential Software and Extensions
Specialized software and browser extensions have become indispensable assets for researchers, amplifying productivity and information retrieval.
- Research-friendly Browsers (Chrome, Firefox, Edge): These browsers offer a multitude of extensions and plugins designed to enhance research, from reference management tools to PDF annotators. For example, the Zotero extension for Firefox allows seamless citation management and reference organization.
- Grammarly: Beyond correcting grammar, Grammarly analyzes context, offering suggestions for writing clarity and correctness. Whether you're composing an academic paper or a professional email, Grammarly ensures your message is precise and polished.
- Turnitin: An essential tool for academia, Turnitin aids in plagiarism detection and prevention . It scans documents for similarities with an extensive database of academic content, ensuring the originality and integrity of research papers.
AI and Machine Learning Tools
Artificial Intelligence and Machine Learning tools are revolutionizing research by analyzing vast datasets, predicting trends, and automating tasks, empowering researchers with unparalleled insights and efficiency.
AI-Powered Search
Tools like Semantic Scholar employ AI to provide relevant, context-aware search results, helping researchers discover articles, journals, and studies tailored to their interests. For instance, Iris.ai employs natural language processing to understand research papers and generate connections between them and Citeulike's AI-driven recommendations enhance academic discovery.
Machine Learning for Data Analysis
Machine Learning algorithms enable researchers to identify intricate patterns in vast datasets, aiding in fields like genomics and climate modeling. Example: TensorFlow, used for natural language processing in sentiment analysis.
AI Applications
AI-driven tools like IBM Watson and GPT-4 assist researchers in automating tasks, from literature reviews to data extraction, improving research efficiency and accuracy. Watson Discovery offers AI-driven data insights, while GPT-3 generates human-like text.
Ethical Considerations in Online Research
Respecting copyright laws.
Maintaining ethical standards in online research involves respecting copyright laws, acknowledging the importance of intellectual property , and seeking permission when using others' work to ensure a responsible and lawful online research practice.
Overview of Copyright, Fair Use, and Public Domain
Copyright laws grant creators exclusive rights to their work, but fair use exceptions exist for purposes like education and commentary. Materials in the public domain can be freely used. For instance, a public domain image can be used without restrictions.
Guidelines for Using Images, Videos, and Text from the Internet
When using online content, ensure proper attribution , adhere to usage restrictions , and obtain permissions when necessary .
- Pixabay: Offers high-quality images and videos for free use.
- Unsplash: Provides a vast collection of professional photos.
- Pexels: Features free stock photos and videos.
- Flickr Commons: Offers historical images and cultural heritage content.
Ethical Use of Data and Privacy Considerations
Respecting data privacy and ethical data use are imperative in online research, safeguarding individuals' rights and ensuring responsible research practices.
Implications of Using Sensitive Data
Researchers must comprehend the legal and ethical consequences of handling sensitive or private data, especially in healthcare or financial studies, to protect participants and avoid data breaches. Comply with laws like the General Data Protection Regulation (GDPR) when handling personal data. For instance, GDPR ensures the lawful and transparent processing of individuals' data.
Respecting Participants’ Privacy and Confidentiality
Informed consent, anonymization, and secure data storage are crucial. Research ethics boards and organizations like the American Psychological Association (APA) provide guidelines. For example, in medical research, patient data should be de-identified to protect confidentiality.
Following Ethical Guidelines for Data Handling
Platforms like Institutional Review Boards (IRBs) and journals have specific ethical standards for research data. In social sciences, researchers must gain consent, store data securely, and follow ethical guidelines during analysis and publication.
Engaging with Online Communities Ethically
Engaging with online communities ethically entails respecting their norms, privacy, and trust. It involves upholding the principles of informed consent and ensuring that the research contributes positively to the community.
Participating Responsibly in Online Forums and Groups
Uphold respectful and responsible conduct when engaging in online communities such as Reddit, Quora, and Stack Exchange. Respect community norms, obtain consent if necessary, and avoid spamming or self-promotion.
Understanding the Implications of Misinformation and Disinformation
Misinformation and disinformation have profound societal impacts . Recognizing their consequences helps researchers address these issues effectively, as highlighted by studies conducted by organizations like the Pew Research Center.
Avoiding and Addressing Cyberbullying and Harassment
Online harassment is a growing concern . Referencing recent statistics from platforms like Twitter or academic research on online harassment trends can shed light on the prevalence and strategies for addressing this issue.
The Takeaway
In the realm of academia, mastering the art of internet research is akin to unlocking a treasure trove of knowledge. Throughout this comprehensive guide, we've navigated through the essential principles of internet research, from formulating precise research questions to employing advanced research tools. We've explored ethical considerations, source evaluation, note-taking strategies, and the ethical use of data, equipping students with a robust skill set to excel in their academic journeys.
As students, your capacity for growth is boundless. Embrace internet research as a lifelong skill, an ever-evolving art that can open doors to new discoveries and insights . In a world brimming with information, your ability to discern, evaluate, and synthesize knowledge will set you apart.
So, here's the call to action: embark on your research endeavors with confidence, apply the techniques learned, and approach each quest for knowledge with curiosity and critical thinking. As you do, you not only enhance your academic prowess but also contribute to the broader culture of continuous learning and intellectual advancement. Your journey as a researcher has just begun; the virtual library of the internet awaits your exploration, so keep learning, keep growing, and keep researching.
Can I rely solely on open-source information for my research?
Open-source information can be valuable, but it's essential to diversify your sources. Depending on your topic, you may need peer-reviewed articles, data from academic databases, or expert insights not readily available in open sources.
What role do social media platforms play in research?
Social media can be a resource for real-time data and discussions, but it should complement, not replace, traditional sources. Use it cautiously, considering issues like bias and privacy, and cite social media posts properly in academic work.
Is it necessary to pay for academic databases when much information is available for free?
Paid academic databases offer access to extensive, peer-reviewed content critical for in-depth research. While free sources are valuable, consider the depth and quality of information required for your study when deciding.
How can I improve my research efficiency without compromising on the quality of information?
Enhance research efficiency by refining your search queries, using advanced search tools, and organizing sources effectively. Prioritize sources based on credibility, relevance, and recency to streamline your research process.
What steps can I take if I cannot find information on my research topic?
If information is scarce, broaden your search terms, explore related fields, or consult with experts. Additionally, consider adjusting your research question or exploring unconventional sources for insights.
- Service Areas
Also on BroadbandSearch
- Internet Tools
- Data Usage Calculator
- Definitions
- Privacy Policy
- Terms & Conditions
Connection Types
- Fixed Wireless
Affiliate Disclaimer: BroadbandSearch.net is an independent, review, availability, comparison, and research website that is supported by advertisement, referral, and affiliate compensation. We provide information collected from providers, publicly available websites, and government sources. We continuously update the website to provide you with the latest deals and most accurate information. Certain providers listed on our website offer us affiliate revenue, or a referral fee when you order their service. Disclaimer: All rights reserved. BroadbandSearch.net is a website intended for research, review and comparison and, as such, falls under "Fair Use". BroadbandSearch.net does not offer internet, TV , or home phone service. All trademarks, logos, etc. remain the property of their respective owners and are used by BroadbandSearch.net only to describe products and services offered by each respective trademark holder. The use of any third party trademarks on this site in no way indicates any relationship between BroadbandSearch.net and the holders of said trademarks, nor any endorsement of BroadbandSearch.net by the holders of said trademarks. Sitemap
Moving or just moved? Yes No
How we make money
Allconnect is an independent, advertising-supported publisher and comparison service. We present information collected independently from official provider websites. We regularly update the site in an effort to keep this information up-to-date and accurate at all times. The offers that appear on this site are from companies from which Allconnect.com receives compensation. This compensation may impact how, where and in what order products appear.
Allconnect.com does not include every service provider available. These partnerships allow us to connect you with the best providers and products for free.
- Resource Center
Student’s internet research guide for 2024

Apr 29, 2024 — 5 min read
Read our student internet research guide for ways to search smart, check for credible sources and cite your sources.

The internet is crowded! It’s brimming with all kinds of information and resources. With so many choices online, it can be tricky to narrow down what you’re looking for.
But, with the right tips and tricks, you’ll learn how to responsibly navigate the internet and give credit to your sources when doing research.
Read through our student internet research guide below for ways to search smart, check for credible sources and cite your sources.
- Where do you start
Search smart
- Is your source credible ?
- Cite carefully
Let’s get started!
Where do you start?
Before you embark on your research, you should: • Ask lots of questions. • Brainstorm and think out of the box! • Make a list of what kinds of sites would work best for your topic. • Break down your research assignment into small parts to tackle it easier.
What types of resources will you come across in your research? • Opinion : Based on personal feelings, thought, belief or anything that can’t be proven. Often contain stories and experiences. • Fact-Based : Can be proven and observed. Often based on reports and studies. Use fact-based sources to guide your research!
Don’t forget to use your school network! It’s likely that your teacher or a librarian can give you access to paid subscriptions or journals that aren’t available in a regular internet search.
Lastly, be patient and stay focused. Search engines turn up millions of results, so it’s easy to get distracted.
Tips to stay focused: • Log off of your email or social networks before you start. • Mark your place and take 5 to 10 minutes to refresh and stretch if you need a break.
How to search smart: Start your research with a well-known search engine, like Google or Bing. Always check your spelling and be clear when typing in the search bar.
Narrow down your search by using unique and specific words. Specific searches can make a huge difference in finding what you need!
Example: If you’re researching the history of mobile cell phones, typing in “cell phone” is too broad. This will bring up cell phone companies or products to buy. Narrow it down by typing in “When did cell phones become popular?” Try putting quotation marks around “your search” to limit the results.
Although the search engine may list your results in a certain way, this doesn’t mean the ones at the top are the most relevant for your topic. Sort through your results!
Is your source credible?
You are in the middle of research and come across a new source you’ve never seen before! How do you know if it’s credible?
Follow this checklist:
Type of website
A college or university website that ends in .edu or a government website that ends in .gov are typically safe choices. Government websites are good for statistics and reports!
Sites that end in .org are run by a nonprofit organization. These can be good resources but may have a strong bias or opinion. Check with your teacher if it’s a good site for your project.
A business or commercial site that ends in .com is in most cases created to help sell a product. Blogs, personal sites and social media platforms that end in .com are likely to give you an opinion, not facts. Be wary of these sites when doing online research!
Established news sites are often safe to use, but always check that it’s an original source. If the article cites another source, go directly to that source for the information.
Subjective vs. objective
Remember earlier in the guide when we talked about opinion vs. fact-based sources?
A subjective source is opinion-based. You may come across Wikipedia.org in your search. This is a very popular site, but the info can be edited by anyone, no matter what the topic is! It’s best not to rely on Wikipedia. Treat it like any other site, and double-check the sources that the article cites.
An objective source is fact-driven. It’s unbiased, meaning it is not swayed by a person’s opinion. Examples of objective sources are research studies and government statistics.
Is your source credible? (Cont.)
• Currency ◦ Is there a publish date listed? If an article or study was written 10 or more years ago, it may not be the most reliable. Dig deeper to see if your topic has newer, fresher information. If not, it may be that the topic doesn’t change frequently. • Authority ◦ Is the name of the author on the page? Look for the author’s occupation, years of experience, job position or education. With what organization or institution are they with? Is the author qualified to write on this topic and why? Ask these questions to verify. • Cited Sources ◦ If you find a list of references for your resource, this is a good sign! People can write anything they want online, so it’s a good idea to check the info against other sources to make sure it’s reliable. • Functionality ◦ If the site looks very poorly made, has misspellings or security warnings pop up, it’s best to steer clear! But be careful, just because a site may look good, it doesn’t mean it’s always reliable.
Cite carefully
When you research online, it can be easy to copy and paste text, then forget to go back later and cite it. However, this is considered plagiarism!
Plagiarism is when you take someone else’s words or ideas and pass them off as your own. There are tools your teacher can use to quickly check your work for plagiarism. This can have serious consequences, so it’s best to stay on the safe side and always give credit to your source!
If you don’t think you can express an idea better in your own words, you can directly quote the source. It’s helpful to cite as you go and keep track of what you quote from a source each time.
There are many different formats to cite your source. Read on to the next slide for common citation styles!
Citation Styles
The two most common formats are MLA and APA. If you aren’t sure what format to use for your project, check with your teacher!
MLA – This format is commonly used by the Humanities.
The core elements of this citation include: Author. Title. Title of the container. Other contributors, Version, Number, Publisher’s name, Date of publication, Location
APA – This format is commonly used by Education, Psychology and Sciences.
The core elements of this citation include: Contributors. (Date). Title. Publication Information.
Be sure to check the MLA and APA websites for additional details. There are also online citation generators that can help you cite your source. Always remember to give credit to other people’s work!
What are some examples of reliable sources?
Peer reviewed journals or websites ending in .edu or .gov are great places to start if you’re looking for reliable sources.
Are websites ending in .net reliable?
They are not necessarily unreliable, but they should be used with caution. Sites ending in .com are generally considered more reliable than .net sites.
How can search engines be used effectively for research?
Search engines can be extremely helpful when researching, but make sure you use clear and specific wording. You can narrow down your results by using keywords, Boolean operators and specific indexes while searching.

Written by:
Editor, Broadband Content
- Featured 5G is on the rise: Is this the tech that will change everything? Lisa Iscrupe — 6 min read
- Featured Guide to low-income internet options and affordable internet plans Robin Layton — 4 min read
- Featured Student internet plans and discounts Camryn Smith — 6 min read
Tuesday, September 3, 2024
Robin Layton — 5 min read
Camryn Smith — 5 min read
Friday, August 30, 2024
By subscribing, you agree to receive Allconnect promotional emails. Your privacy is important to us.
Thanks for subscribing!
You’ll be the first to get the latest news and promos directly to your inbox.
Check your inbox and stay tuned for deals, news and more.
Want to stay connected with the latest deals?
Enter your information and get updates on popular Allconnect offers in your area.
Enter your address to view what's available near you
Need help? Speak to one of our experts.
Call: (844) 451-2720
The limits a provider sets on the amount of data you’re able to use while online
Download speeds
Transfers data to your home for activities like streaming, shopping and browsing social media
Mbps (Megabits per second)
A unit of measurement used to indicate download and upload speeds
Upload speeds
Transfer data from your home for activities like video calls, uploading large files, working on online documents and live gaming
Stay tuned for the latest news and tips each week.
Get the latest internet, streaming, wireless, TV and home security news directly to your inbox.

- Request new password
- Create a new account
Race, Ethnicity, Gender, and Class - The Sociology of Group Conflict and Change
Student resources, internet research projects, modern slavery.
Americans today might look at slavery as a distant relic of history, remote and bizarre. The idea that a person could be owned by another person, defined as a piece of property, and bought and sold like livestock probably seems alien to people who live in a culture devoted to individual happiness and personal well-being. Yet, as you saw in the “Applying Concepts” activity in this chapter, this ancient institution can still be found around the world, on every continent, in societies at every level of development, and in the United States.
In this project, you will use sources of information readily available on the Internet to gather facts and estimate the volume and scope of modern slavery. You will also collect some case studies or personal examples of slavery, analyze the nature of the practice today, compare it to American slavery, and find out what is being done to combat the practice. This project will also provide an opportunity to review some of the important points and ideas presented in this chapter.
To begin, consider the list of questions below. Next, visit the websites listed here and search for answers to the questions. Also, search the Internet on your own for additional sources that may help you develop an understanding of modern slavery. ( NOTE: Your instructor may have additional or different instructions for gathering information. )
As you search the Internet, remember that you will need to practice a healthy skepticism about the information, ideas, and arguments that you find—including the information on the websites listed here. Of course, you should always be careful and critical when doing research, but, as you know, the Internet includes unregulated sites that present incomplete, deeply biased, or false information, and an extra note of caution is justified. Also, recognize at the outset that many of the facts you gather (e.g., the number of people currently enslaved) will be approximations and, in some cases, mere guesswork.
Questions for Research and Discussion
What is the scope and volume of modern slavery? Note any important difference with the estimates provided in the “Applying Concepts” activity in this chapter develop the best answers possible to these questions:
How many people are enslaved?
What is the composition of the enslaved population in terms of gender, age, race, and nationality?
Where in the world are modern slaves most numerous?
For the slave population that is transported across national lines, what are the major sending and receiving nations?
What are the experiences of modern slaves?
Describe the mechanisms and practices by which slave status is enforced. What is the role of debt bondage? How often are coercion and violence used? How do these practices vary across different types of slavery (e.g., sex trafficking versus involuntary labor)?
Find at least three to five case studies of people who have been victimized by modern slavery.
Sociologically, what do these people have in common? That is, what important social characteristics (age, gender, social class, race, and ethnicity) do they share?
What are the dynamics and causes of modern slavery?
American slavery was shaped by the level of development and labor-intensive subsistence technology of the colonial era. Can you find ways in which similar factors shape modern slavery?
Can you apply elements of the Noel hypothesis to modern slavery? Does ethnocentrism, prejudice, or sexism play a role? How? What resources and abilities do modern slaves have that make them the objects of competition? What role does power play in shaping and maintaining these practices?
How do labor markets operate in modern slavery? Do the “Laws of Supply and Demand” operate in these markets? How?
What roles do modern slaves play in the job market? What economic niches are being filled? Who profits? Who loses? Describe the minority-dominant group situations you find in your search for facts.
What are some of the enforcement efforts designed to stop slavery? What human rights are being violated?
Find at least three national and international programs aimed at stopping modern slavery and describe what they are doing.
What specific human rights are at stake here? Is slavery illegal? Where? By what authority?
Websites for this Project
The Home Page of “ Free the Slaves” includes information, resources for teachers, and a description of the organization’s efforts to combat modern slavery.
Home Page for the International Justice Mission , a Christian advocacy and activist group dedicated to combating slavery .
U.S. Department of State’s annual “Trafficking in Persons” report. The report can be downloaded in pdf format.
The International Labour Organization (an agency of the UN). Their annual report on involuntary labor can be downloaded in pdf format.
Optional Discussion: Bring your findings to class and discuss with classmates. Focus your discussion on comparing and contrasting modern slavery and colonial American slavery, especially the roles of ethnocentrism and power, subsistence technology, demand and supply, human rights, and enforcement efforts. ( Your instructor may have more specific or different instructions . )

A Brief History of the Internet
Introduction, published 1997.
Barry M. Leiner, Vinton G. Cerf, David D. Clark, Robert E. Kahn, Leonard Kleinrock, Daniel C. Lynch, Jon Postel, Larry G. Roberts, Stephen Wolff
The Internet has revolutionized the computer and communications world like nothing before. The invention of the telegraph, telephone, radio, and computer set the stage for this unprecedented integration of capabilities. The Internet is at once a world-wide broadcasting capability, a mechanism for information dissemination, and a medium for collaboration and interaction between individuals and their computers without regard for geographic location. The Internet represents one of the most successful examples of the benefits of sustained investment and commitment to research and development of information infrastructure. Beginning with the early research in packet switching, the government, industry and academia have been partners in evolving and deploying this exciting new technology. Today, terms like “ [email protected] ” and “ http://www.acm.org ” trip lightly off the tongue of the random person on the street. 1
This is intended to be a brief, necessarily cursory and incomplete history. Much material currently exists about the Internet, covering history, technology, and usage. A trip to almost any bookstore will find shelves of material written about the Internet. 2
Learn more about how we are building a bigger, stronger Internet.
In this paper, 3 several of us involved in the development and evolution of the Internet share our views of its origins and history. This history revolves around four distinct aspects. There is the technological evolution that began with early research on packet switching and the ARPANET (and related technologies), and where current research continues to expand the horizons of the infrastructure along several dimensions, such as scale, performance, and higher-level functionality. There is the operations and management aspect of a global and complex operational infrastructure. There is the social aspect, which resulted in a broad community of Internauts working together to create and evolve the technology. And there is the commercialization aspect, resulting in an extremely effective transition of research results into a broadly deployed and available information infrastructure.
The Internet today is a widespread information infrastructure, the initial prototype of what is often called the National (or Global or Galactic) Information Infrastructure. Its history is complex and involves many aspects – technological, organizational, and community. And its influence reaches not only to the technical fields of computer communications but throughout society as we move toward increasing use of online tools to accomplish electronic commerce, information acquisition, and community operations.
Origins of the Internet
The first recorded description of the social interactions that could be enabled through networking was a series of memos written by J.C.R. Licklider of MIT in August 1962 discussing his “Galactic Network” concept. He envisioned a globally interconnected set of computers through which everyone could quickly access data and programs from any site. In spirit, the concept was very much like the Internet of today. Licklider was the first head of the computer research program at DARPA, 4 starting in October 1962. While at DARPA he convinced his successors at DARPA, Ivan Sutherland, Bob Taylor, and MIT researcher Lawrence G. Roberts, of the importance of this networking concept.
Leonard Kleinrock at MIT published the first paper on packet switching theory in July 1961 and the first book on the subject in 1964. Kleinrock convinced Roberts of the theoretical feasibility of communications using packets rather than circuits, which was a major step along the path towards computer networking. The other key step was to make the computers talk together. To explore this, in 1965 working with Thomas Merrill, Roberts connected the TX-2 computer in Mass. to the Q-32 in California with a low speed dial-up telephone line creating the first (however small) wide-area computer network ever built . The result of this experiment was the realization that the time-shared computers could work well together, running programs and retrieving data as necessary on the remote machine, but that the circuit switched telephone system was totally inadequate for the job. Kleinrock’s conviction of the need for packet switching was confirmed.
In late 1966 Roberts went to DARPA to develop the computer network concept and quickly put together his plan for the “ARPANET” , publishing it in 1967. At the conference where he presented the paper, there was also a paper on a packet network concept from the UK by Donald Davies and Roger Scantlebury of NPL. Scantlebury told Roberts about the NPL work as well as that of Paul Baran and others at RAND. The RAND group had written a paper on packet switching networks for secure voice in the military in 1964. It happened that the work at MIT (1961-1967), at RAND (1962-1965), and at NPL (1964-1967) had all proceeded in parallel without any of the researchers knowing about the other work. The word “packet” was adopted from the work at NPL and the proposed line speed to be used in the ARPANET design was upgraded from 2.4 kbps to 50 kbps. 5
In August 1968, after Roberts and the DARPA funded community had refined the overall structure and specifications for the ARPANET, an RFQ was released by DARPA for the development of one of the key components, the packet switches called Interface Message Processors (IMP’s). The RFQ was won in December 1968 by a group headed by Frank Heart at Bolt Beranek and Newman (BBN). As the BBN team worked on the IMP’s with Bob Kahn playing a major role in the overall ARPANET architectural design, the network topology and economics were designed and optimized by Roberts working with Howard Frank and his team at Network Analysis Corporation, and the network measurement system was prepared by Kleinrock’s team at UCLA. 6
Due to Kleinrock’s early development of packet switching theory and his focus on analysis, design and measurement, his Network Measurement Center at UCLA was selected to be the first node on the ARPANET. All this came together in September 1969 when BBN installed the first IMP at UCLA and the first host computer was connected. Doug Engelbart’s project on “Augmentation of Human Intellect” (which included NLS, an early hypertext system) at Stanford Research Institute (SRI) provided a second node. SRI supported the Network Information Center, led by Elizabeth (Jake) Feinler and including functions such as maintaining tables of host name to address mapping as well as a directory of the RFC’s.
One month later, when SRI was connected to the ARPANET, the first host-to-host message was sent from Kleinrock’s laboratory to SRI. Two more nodes were added at UC Santa Barbara and University of Utah. These last two nodes incorporated application visualization projects, with Glen Culler and Burton Fried at UCSB investigating methods for display of mathematical functions using storage displays to deal with the problem of refresh over the net, and Robert Taylor and Ivan Sutherland at Utah investigating methods of 3-D representations over the net. Thus, by the end of 1969, four host computers were connected together into the initial ARPANET, and the budding Internet was off the ground. Even at this early stage, it should be noted that the networking research incorporated both work on the underlying network and work on how to utilize the network. This tradition continues to this day.
Computers were added quickly to the ARPANET during the following years, and work proceeded on completing a functionally complete Host-to-Host protocol and other network software. In December 1970 the Network Working Group (NWG) working under S. Crocker finished the initial ARPANET Host-to-Host protocol, called the Network Control Protocol (NCP). As the ARPANET sites completed implementing NCP during the period 1971-1972, the network users finally could begin to develop applications.
In October 1972, Kahn organized a large, very successful demonstration of the ARPANET at the International Computer Communication Conference (ICCC). This was the first public demonstration of this new network technology to the public. It was also in 1972 that the initial “hot” application, electronic mail, was introduced. In March Ray Tomlinson at BBN wrote the basic email message send and read software, motivated by the need of the ARPANET developers for an easy coordination mechanism. In July, Roberts expanded its utility by writing the first email utility program to list, selectively read, file, forward, and respond to messages. From there email took off as the largest network application for over a decade. This was a harbinger of the kind of activity we see on the World Wide Web today, namely, the enormous growth of all kinds of “people-to-people” traffic.
The Initial Internetting Concepts
The original ARPANET grew into the Internet. Internet was based on the idea that there would be multiple independent networks of rather arbitrary design, beginning with the ARPANET as the pioneering packet switching network, but soon to include packet satellite networks, ground-based packet radio networks and other networks. The Internet as we now know it embodies a key underlying technical idea, namely that of open architecture networking. In this approach, the choice of any individual network technology was not dictated by a particular network architecture but rather could be selected freely by a provider and made to interwork with the other networks through a meta-level “Internetworking Architecture”. Up until that time there was only one general method for federating networks. This was the traditional circuit switching method where networks would interconnect at the circuit level, passing individual bits on a synchronous basis along a portion of an end-to-end circuit between a pair of end locations. Recall that Kleinrock had shown in 1961 that packet switching was a more efficient switching method. Along with packet switching, special purpose interconnection arrangements between networks were another possibility. While there were other limited ways to interconnect different networks, they required that one be used as a component of the other, rather than acting as a peer of the other in offering end-to-end service.
In an open-architecture network, the individual networks may be separately designed and developed and each may have its own unique interface which it may offer to users and/or other providers. including other Internet providers. Each network can be designed in accordance with the specific environment and user requirements of that network. There are generally no constraints on the types of network that can be included or on their geographic scope, although certain pragmatic considerations will dictate what makes sense to offer.
The idea of open-architecture networking was first introduced by Kahn shortly after having arrived at DARPA in 1972. This work was originally part of the packet radio program, but subsequently became a separate program in its own right. At the time, the program was called “Internetting”. Key to making the packet radio system work was a reliable end-end protocol that could maintain effective communication in the face of jamming and other radio interference, or withstand intermittent blackout such as caused by being in a tunnel or blocked by the local terrain. Kahn first contemplated developing a protocol local only to the packet radio network, since that would avoid having to deal with the multitude of different operating systems, and continuing to use NCP.
However, NCP did not have the ability to address networks (and machines) further downstream than a destination IMP on the ARPANET and thus some change to NCP would also be required. (The assumption was that the ARPANET was not changeable in this regard). NCP relied on ARPANET to provide end-to-end reliability. If any packets were lost, the protocol (and presumably any applications it supported) would come to a grinding halt. In this model NCP had no end-end host error control, since the ARPANET was to be the only network in existence and it would be so reliable that no error control would be required on the part of the hosts. Thus, Kahn decided to develop a new version of the protocol which could meet the needs of an open-architecture network environment. This protocol would eventually be called the Transmission Control Protocol/Internet Protocol (TCP/IP). While NCP tended to act like a device driver, the new protocol would be more like a communications protocol.
Four ground rules were critical to Kahn’s early thinking:
- Each distinct network would have to stand on its own and no internal changes could be required to any such network to connect it to the Internet.
- Communications would be on a best effort basis. If a packet didn’t make it to the final destination, it would shortly be retransmitted from the source.
- Black boxes would be used to connect the networks; these would later be called gateways and routers. There would be no information retained by the gateways about the individual flows of packets passing through them, thereby keeping them simple and avoiding complicated adaptation and recovery from various failure modes.
- There would be no global control at the operations level.
Other key issues that needed to be addressed were:
- Algorithms to prevent lost packets from permanently disabling communications and enabling them to be successfully retransmitted from the source.
- Providing for host-to-host “pipelining” so that multiple packets could be enroute from source to destination at the discretion of the participating hosts, if the intermediate networks allowed it.
- Gateway functions to allow it to forward packets appropriately. This included interpreting IP headers for routing, handling interfaces, breaking packets into smaller pieces if necessary, etc.
- The need for end-end checksums, reassembly of packets from fragments and detection of duplicates, if any.
- The need for global addressing
- Techniques for host-to-host flow control.
- Interfacing with the various operating systems
- There were also other concerns, such as implementation efficiency, internetwork performance, but these were secondary considerations at first.
Kahn began work on a communications-oriented set of operating system principles while at BBN and documented some of his early thoughts in an internal BBN memorandum entitled “ Communications Principles for Operating Systems “. At this point he realized it would be necessary to learn the implementation details of each operating system to have a chance to embed any new protocols in an efficient way. Thus, in the spring of 1973, after starting the internetting effort, he asked Vint Cerf (then at Stanford) to work with him on the detailed design of the protocol. Cerf had been intimately involved in the original NCP design and development and already had the knowledge about interfacing to existing operating systems. So armed with Kahn’s architectural approach to the communications side and with Cerf’s NCP experience, they teamed up to spell out the details of what became TCP/IP.
The give and take was highly productive and the first written version of the resulting approach was distributed as INWG#39 at a special meeting of the International Network Working Group (INWG) at Sussex University in September 1973. Subsequently a refined version was published in 1974 7 . The INWG was created at the October 1972 International Computer Communications Conference organized by Bob Kahn, et al, and Cerf was invited to chair this group.
Some basic approaches emerged from this collaboration between Kahn and Cerf:
- Communication between two processes would logically consist of a very long stream of bytes (they called them octets). The position of any octet in the stream would be used to identify it.
- Flow control would be done by using sliding windows and acknowledgments (acks). The destination could select when to acknowledge and each ack returned would be cumulative for all packets received to that point.
- It was left open as to exactly how the source and destination would agree on the parameters of the windowing to be used. Defaults were used initially.
- Although Ethernet was under development at Xerox PARC at that time, the proliferation of LANs were not envisioned at the time, much less PCs and workstations. The original model was national level networks like ARPANET of which only a relatively small number were expected to exist. Thus a 32 bit IP address was used of which the first 8 bits signified the network and the remaining 24 bits designated the host on that network. This assumption, that 256 networks would be sufficient for the foreseeable future, was clearly in need of reconsideration when LANs began to appear in the late 1970s.
The original Cerf/Kahn paper on the Internet described one protocol, called TCP, which provided all the transport and forwarding services in the Internet. Kahn had intended that the TCP protocol support a range of transport services, from the totally reliable sequenced delivery of data (virtual circuit model) to a datagram service in which the application made direct use of the underlying network service, which might imply occasional lost, corrupted or reordered packets. However, the initial effort to implement TCP resulted in a version that only allowed for virtual circuits. This model worked fine for file transfer and remote login applications, but some of the early work on advanced network applications, in particular packet voice in the 1970s, made clear that in some cases packet losses should not be corrected by TCP, but should be left to the application to deal with. This led to a reorganization of the original TCP into two protocols, the simple IP which provided only for addressing and forwarding of individual packets, and the separate TCP, which was concerned with service features such as flow control and recovery from lost packets. For those applications that did not want the services of TCP, an alternative called the User Datagram Protocol (UDP) was added in order to provide direct access to the basic service of IP.
A major initial motivation for both the ARPANET and the Internet was resource sharing – for example allowing users on the packet radio networks to access the time sharing systems attached to the ARPANET. Connecting the two together was far more economical that duplicating these very expensive computers. However, while file transfer and remote login (Telnet) were very important applications, electronic mail has probably had the most significant impact of the innovations from that era. Email provided a new model of how people could communicate with each other, and changed the nature of collaboration, first in the building of the Internet itself (as is discussed below) and later for much of society.
There were other applications proposed in the early days of the Internet, including packet based voice communication (the precursor of Internet telephony), various models of file and disk sharing, and early “worm” programs that showed the concept of agents (and, of course, viruses). A key concept of the Internet is that it was not designed for just one application, but as a general infrastructure on which new applications could be conceived, as illustrated later by the emergence of the World Wide Web. It is the general purpose nature of the service provided by TCP and IP that makes this possible.
Proving the Ideas
DARPA let three contracts to Stanford (Cerf), BBN (Ray Tomlinson) and UCL (Peter Kirstein) to implement TCP/IP (it was simply called TCP in the Cerf/Kahn paper but contained both components). The Stanford team, led by Cerf, produced the detailed specification and within about a year there were three independent implementations of TCP that could interoperate.
This was the beginning of long term experimentation and development to evolve and mature the Internet concepts and technology. Beginning with the first three networks (ARPANET, Packet Radio, and Packet Satellite) and their initial research communities, the experimental environment has grown to incorporate essentially every form of network and a very broad-based research and development community. [REK78] With each expansion has come new challenges.
The early implementations of TCP were done for large time sharing systems such as Tenex and TOPS 20. When desktop computers first appeared, it was thought by some that TCP was too big and complex to run on a personal computer. David Clark and his research group at MIT set out to show that a compact and simple implementation of TCP was possible. They produced an implementation, first for the Xerox Alto (the early personal workstation developed at Xerox PARC) and then for the IBM PC. That implementation was fully interoperable with other TCPs, but was tailored to the application suite and performance objectives of the personal computer, and showed that workstations, as well as large time-sharing systems, could be a part of the Internet. In 1976, Kleinrock published the first book on the ARPANET . It included an emphasis on the complexity of protocols and the pitfalls they often introduce. This book was influential in spreading the lore of packet switching networks to a very wide community.
Widespread development of LANS, PCs and workstations in the 1980s allowed the nascent Internet to flourish. Ethernet technology, developed by Bob Metcalfe at Xerox PARC in 1973, is now probably the dominant network technology in the Internet and PCs and workstations the dominant computers. This change from having a few networks with a modest number of time-shared hosts (the original ARPANET model) to having many networks has resulted in a number of new concepts and changes to the underlying technology. First, it resulted in the definition of three network classes (A, B, and C) to accommodate the range of networks. Class A represented large national scale networks (small number of networks with large numbers of hosts); Class B represented regional scale networks; and Class C represented local area networks (large number of networks with relatively few hosts).
A major shift occurred as a result of the increase in scale of the Internet and its associated management issues. To make it easy for people to use the network, hosts were assigned names, so that it was not necessary to remember the numeric addresses. Originally, there were a fairly limited number of hosts, so it was feasible to maintain a single table of all the hosts and their associated names and addresses. The shift to having a large number of independently managed networks (e.g., LANs) meant that having a single table of hosts was no longer feasible, and the Domain Name System (DNS) was invented by Paul Mockapetris of USC/ISI. The DNS permitted a scalable distributed mechanism for resolving hierarchical host names (e.g. www.acm.org ) into an Internet address.
The increase in the size of the Internet also challenged the capabilities of the routers. Originally, there was a single distributed algorithm for routing that was implemented uniformly by all the routers in the Internet. As the number of networks in the Internet exploded, this initial design could not expand as necessary, so it was replaced by a hierarchical model of routing, with an Interior Gateway Protocol (IGP) used inside each region of the Internet, and an Exterior Gateway Protocol (EGP) used to tie the regions together. This design permitted different regions to use a different IGP, so that different requirements for cost, rapid reconfiguration, robustness and scale could be accommodated. Not only the routing algorithm, but the size of the addressing tables, stressed the capacity of the routers. New approaches for address aggregation, in particular classless inter-domain routing (CIDR), have recently been introduced to control the size of router tables.
As the Internet evolved, one of the major challenges was how to propagate the changes to the software, particularly the host software. DARPA supported UC Berkeley to investigate modifications to the Unix operating system, including incorporating TCP/IP developed at BBN. Although Berkeley later rewrote the BBN code to more efficiently fit into the Unix system and kernel, the incorporation of TCP/IP into the Unix BSD system releases proved to be a critical element in dispersion of the protocols to the research community. Much of the CS research community began to use Unix BSD for their day-to-day computing environment. Looking back, the strategy of incorporating Internet protocols into a supported operating system for the research community was one of the key elements in the successful widespread adoption of the Internet.
One of the more interesting challenges was the transition of the ARPANET host protocol from NCP to TCP/IP as of January 1, 1983. This was a “flag-day” style transition, requiring all hosts to convert simultaneously or be left having to communicate via rather ad-hoc mechanisms. This transition was carefully planned within the community over several years before it actually took place and went surprisingly smoothly (but resulted in a distribution of buttons saying “I survived the TCP/IP transition”).
TCP/IP was adopted as a defense standard three years earlier in 1980. This enabled defense to begin sharing in the DARPA Internet technology base and led directly to the eventual partitioning of the military and non- military communities. By 1983, ARPANET was being used by a significant number of defense R&D and operational organizations. The transition of ARPANET from NCP to TCP/IP permitted it to be split into a MILNET supporting operational requirements and an ARPANET supporting research needs.
Thus, by 1985, Internet was already well established as a technology supporting a broad community of researchers and developers, and was beginning to be used by other communities for daily computer communications. Electronic mail was being used broadly across several communities, often with different systems, but interconnection between different mail systems was demonstrating the utility of broad based electronic communications between people.
Transition to Widespread Infrastructure
At the same time that the Internet technology was being experimentally validated and widely used amongst a subset of computer science researchers, other networks and networking technologies were being pursued. The usefulness of computer networking – especially electronic mail – demonstrated by DARPA and Department of Defense contractors on the ARPANET was not lost on other communities and disciplines, so that by the mid-1970s computer networks had begun to spring up wherever funding could be found for the purpose. The U.S. Department of Energy (DoE) established MFENet for its researchers in Magnetic Fusion Energy, whereupon DoE’s High Energy Physicists responded by building HEPNet. NASA Space Physicists followed with SPAN, and Rick Adrion, David Farber, and Larry Landweber established CSNET for the (academic and industrial) Computer Science community with an initial grant from the U.S. National Science Foundation (NSF). AT&T’s free-wheeling dissemination of the UNIX computer operating system spawned USENET, based on UNIX’ built-in UUCP communication protocols, and in 1981 Ira Fuchs and Greydon Freeman devised BITNET, which linked academic mainframe computers in an “email as card images” paradigm.
With the exception of BITNET and USENET, these early networks (including ARPANET) were purpose-built – i.e., they were intended for, and largely restricted to, closed communities of scholars; there was hence little pressure for the individual networks to be compatible and, indeed, they largely were not. In addition, alternate technologies were being pursued in the commercial sector, including XNS from Xerox, DECNet, and IBM’s SNA. 8 It remained for the British JANET (1984) and U.S. NSFNET (1985) programs to explicitly announce their intent to serve the entire higher education community, regardless of discipline. Indeed, a condition for a U.S. university to receive NSF funding for an Internet connection was that “… the connection must be made available to ALL qualified users on campus.”
In 1985, Dennis Jennings came from Ireland to spend a year at NSF leading the NSFNET program. He worked with the community to help NSF make a critical decision – that TCP/IP would be mandatory for the NSFNET program. When Steve Wolff took over the NSFNET program in 1986, he recognized the need for a wide area networking infrastructure to support the general academic and research community, along with the need to develop a strategy for establishing such infrastructure on a basis ultimately independent of direct federal funding. Policies and strategies were adopted (see below) to achieve that end.
NSF also elected to support DARPA’s existing Internet organizational infrastructure, hierarchically arranged under the (then) Internet Activities Board (IAB). The public declaration of this choice was the joint authorship by the IAB’s Internet Engineering and Architecture Task Forces and by NSF’s Network Technical Advisory Group of RFC 985 (Requirements for Internet Gateways ), which formally ensured interoperability of DARPA’s and NSF’s pieces of the Internet.
In addition to the selection of TCP/IP for the NSFNET program, Federal agencies made and implemented several other policy decisions which shaped the Internet of today.
- Federal agencies shared the cost of common infrastructure, such as trans-oceanic circuits. They also jointly supported “managed interconnection points” for interagency traffic; the Federal Internet Exchanges (FIX-E and FIX-W) built for this purpose served as models for the Network Access Points and “*IX” facilities that are prominent features of today’s Internet architecture.
- To coordinate this sharing, the Federal Networking Council 9 was formed. The FNC also cooperated with other international organizations, such as RARE in Europe, through the Coordinating Committee on Intercontinental Research Networking, CCIRN, to coordinate Internet support of the research community worldwide.
- This sharing and cooperation between agencies on Internet-related issues had a long history. An unprecedented 1981 agreement between Farber, acting for CSNET and the NSF, and DARPA’s Kahn, permitted CSNET traffic to share ARPANET infrastructure on a statistical and no-metered-settlements basis.
- Subsequently, in a similar mode, the NSF encouraged its regional (initially academic) networks of the NSFNET to seek commercial, non-academic customers, expand their facilities to serve them, and exploit the resulting economies of scale to lower subscription costs for all.
- On the NSFNET Backbone – the national-scale segment of the NSFNET – NSF enforced an “Acceptable Use Policy” (AUP) which prohibited Backbone usage for purposes “not in support of Research and Education.” The predictable (and intended) result of encouraging commercial network traffic at the local and regional level, while denying its access to national-scale transport, was to stimulate the emergence and/or growth of “private”, competitive, long-haul networks such as PSI, UUNET, ANS CO+RE, and (later) others. This process of privately-financed augmentation for commercial uses was thrashed out starting in 1988 in a series of NSF-initiated conferences at Harvard’s Kennedy School of Government on “The Commercialization and Privatization of the Internet” – and on the “com-priv” list on the net itself.
- In 1988, a National Research Council committee, chaired by Kleinrock and with Kahn and Clark as members, produced a report commissioned by NSF titled “Towards a National Research Network”. This report was influential on then Senator Al Gore, and ushered in high speed networks that laid the networking foundation for the future information superhighway.
- In 1994, a National Research Council report, again chaired by Kleinrock (and with Kahn and Clark as members again), Entitled “Realizing The Information Future: The Internet and Beyond” was released. This report, commissioned by NSF, was the document in which a blueprint for the evolution of the information superhighway was articulated and which has had a lasting affect on the way to think about its evolution. It anticipated the critical issues of intellectual property rights, ethics, pricing, education, architecture and regulation for the Internet.
- NSF’s privatization policy culminated in April, 1995, with the defunding of the NSFNET Backbone. The funds thereby recovered were (competitively) redistributed to regional networks to buy national-scale Internet connectivity from the now numerous, private, long-haul networks.
The backbone had made the transition from a network built from routers out of the research community (the “Fuzzball” routers from David Mills) to commercial equipment. In its 8 1/2 year lifetime, the Backbone had grown from six nodes with 56 kbps links to 21 nodes with multiple 45 Mbps links. It had seen the Internet grow to over 50,000 networks on all seven continents and outer space, with approximately 29,000 networks in the United States.
Such was the weight of the NSFNET program’s ecumenism and funding ($200 million from 1986 to 1995) – and the quality of the protocols themselves – that by 1990 when the ARPANET itself was finally decommissioned 10 , TCP/IP had supplanted or marginalized most other wide-area computer network protocols worldwide, and IP was well on its way to becoming THE bearer service for the Global Information Infrastructure.
The Role of Documentation
A key to the rapid growth of the Internet has been the free and open access to the basic documents, especially the specifications of the protocols.
The beginnings of the ARPANET and the Internet in the university research community promoted the academic tradition of open publication of ideas and results. However, the normal cycle of traditional academic publication was too formal and too slow for the dynamic exchange of ideas essential to creating networks.
In 1969 a key step was taken by S. Crocker (then at UCLA) in establishing the Request for Comments (or RFC) series of notes. These memos were intended to be an informal fast distribution way to share ideas with other network researchers. At first the RFCs were printed on paper and distributed via snail mail. As the File Transfer Protocol (FTP) came into use, the RFCs were prepared as online files and accessed via FTP. Now, of course, the RFCs are easily accessed via the World Wide Web at dozens of sites around the world. SRI, in its role as Network Information Center, maintained the online directories. Jon Postel acted as RFC Editor as well as managing the centralized administration of required protocol number assignments, roles that he continued to play until his death, October 16, 1998.
The effect of the RFCs was to create a positive feedback loop, with ideas or proposals presented in one RFC triggering another RFC with additional ideas, and so on. When some consensus (or a least a consistent set of ideas) had come together a specification document would be prepared. Such a specification would then be used as the base for implementations by the various research teams.
Over time, the RFCs have become more focused on protocol standards (the “official” specifications), though there are still informational RFCs that describe alternate approaches, or provide background information on protocols and engineering issues. The RFCs are now viewed as the “documents of record” in the Internet engineering and standards community.
The open access to the RFCs (for free, if you have any kind of a connection to the Internet) promotes the growth of the Internet because it allows the actual specifications to be used for examples in college classes and by entrepreneurs developing new systems.
Email has been a significant factor in all areas of the Internet, and that is certainly true in the development of protocol specifications, technical standards, and Internet engineering. The very early RFCs often presented a set of ideas developed by the researchers at one location to the rest of the community. After email came into use, the authorship pattern changed – RFCs were presented by joint authors with common view independent of their locations.
The use of specialized email mailing lists has been long used in the development of protocol specifications, and continues to be an important tool. The IETF now has in excess of 75 working groups, each working on a different aspect of Internet engineering. Each of these working groups has a mailing list to discuss one or more draft documents under development. When consensus is reached on a draft document it may be distributed as an RFC.
As the current rapid expansion of the Internet is fueled by the realization of its capability to promote information sharing, we should understand that the network’s first role in information sharing was sharing the information about its own design and operation through the RFC documents. This unique method for evolving new capabilities in the network will continue to be critical to future evolution of the Internet.
Formation of the Broad Community
The Internet is as much a collection of communities as a collection of technologies, and its success is largely attributable to both satisfying basic community needs as well as utilizing the community in an effective way to push the infrastructure forward. This community spirit has a long history beginning with the early ARPANET. The early ARPANET researchers worked as a close-knit community to accomplish the initial demonstrations of packet switching technology described earlier. Likewise, the Packet Satellite, Packet Radio and several other DARPA computer science research programs were multi-contractor collaborative activities that heavily used whatever available mechanisms there were to coordinate their efforts, starting with electronic mail and adding file sharing, remote access, and eventually World Wide Web capabilities. Each of these programs formed a working group, starting with the ARPANET Network Working Group. Because of the unique role that ARPANET played as an infrastructure supporting the various research programs, as the Internet started to evolve, the Network Working Group evolved into Internet Working Group.
In the late 1970s, recognizing that the growth of the Internet was accompanied by a growth in the size of the interested research community and therefore an increased need for coordination mechanisms, Vint Cerf, then manager of the Internet Program at DARPA, formed several coordination bodies – an International Cooperation Board (ICB), chaired by Peter Kirstein of UCL, to coordinate activities with some cooperating European countries centered on Packet Satellite research, an Internet Research Group which was an inclusive group providing an environment for general exchange of information, and an Internet Configuration Control Board (ICCB), chaired by Clark. The ICCB was an invitational body to assist Cerf in managing the burgeoning Internet activity.
In 1983, when Barry Leiner took over management of the Internet research program at DARPA, he and Clark recognized that the continuing growth of the Internet community demanded a restructuring of the coordination mechanisms. The ICCB was disbanded and in its place a structure of Task Forces was formed, each focused on a particular area of the technology (e.g. routers, end-to-end protocols, etc.). The Internet Activities Board (IAB) was formed from the chairs of the Task Forces.
It of course was only a coincidence that the chairs of the Task Forces were the same people as the members of the old ICCB, and Dave Clark continued to act as chair. After some changing membership on the IAB, Phill Gross became chair of a revitalized Internet Engineering Task Force (IETF), at the time merely one of the IAB Task Forces. As we saw above, by 1985 there was a tremendous growth in the more practical/engineering side of the Internet. This growth resulted in an explosion in the attendance at the IETF meetings, and Gross was compelled to create substructure to the IETF in the form of working groups.
This growth was complemented by a major expansion in the community. No longer was DARPA the only major player in the funding of the Internet. In addition to NSFNet and the various US and international government-funded activities, interest in the commercial sector was beginning to grow. Also in 1985, both Kahn and Leiner left DARPA and there was a significant decrease in Internet activity at DARPA. As a result, the IAB was left without a primary sponsor and increasingly assumed the mantle of leadership.
The growth continued, resulting in even further substructure within both the IAB and IETF. The IETF combined Working Groups into Areas, and designated Area Directors. An Internet Engineering Steering Group (IESG) was formed of the Area Directors. The IAB recognized the increasing importance of the IETF, and restructured the standards process to explicitly recognize the IESG as the major review body for standards. The IAB also restructured so that the rest of the Task Forces (other than the IETF) were combined into an Internet Research Task Force (IRTF) chaired by Postel, with the old task forces renamed as research groups.
The growth in the commercial sector brought with it increased concern regarding the standards process itself. Starting in the early 1980’s and continuing to this day, the Internet grew beyond its primarily research roots to include both a broad user community and increased commercial activity. Increased attention was paid to making the process open and fair. This coupled with a recognized need for community support of the Internet eventually led to the formation of the Internet Society in 1991, under the auspices of Kahn’s Corporation for National Research Initiatives (CNRI) and the leadership of Cerf, then with CNRI.
In 1992, yet another reorganization took place. In 1992, the Internet Activities Board was re-organized and re-named the Internet Architecture Board operating under the auspices of the Internet Society. A more “peer” relationship was defined between the new IAB and IESG, with the IETF and IESG taking a larger responsibility for the approval of standards. Ultimately, a cooperative and mutually supportive relationship was formed between the IAB, IETF, and Internet Society, with the Internet Society taking on as a goal the provision of service and other measures which would facilitate the work of the IETF.
The recent development and widespread deployment of the World Wide Web has brought with it a new community, as many of the people working on the WWW have not thought of themselves as primarily network researchers and developers. A new coordination organization was formed, the World Wide Web Consortium (W3C). Initially led from MIT’s Laboratory for Computer Science by Tim Berners-Lee (the inventor of the WWW) and Al Vezza, W3C has taken on the responsibility for evolving the various protocols and standards associated with the Web.
Thus, through the over two decades of Internet activity, we have seen a steady evolution of organizational structures designed to support and facilitate an ever-increasing community working collaboratively on Internet issues.
Commercialization of the Technology
Commercialization of the Internet involved not only the development of competitive, private network services, but also the development of commercial products implementing the Internet technology. In the early 1980s, dozens of vendors were incorporating TCP/IP into their products because they saw buyers for that approach to networking. Unfortunately they lacked both real information about how the technology was supposed to work and how the customers planned on using this approach to networking. Many saw it as a nuisance add-on that had to be glued on to their own proprietary networking solutions: SNA, DECNet, Netware, NetBios. The DoD had mandated the use of TCP/IP in many of its purchases but gave little help to the vendors regarding how to build useful TCP/IP products.
In 1985, recognizing this lack of information availability and appropriate training, Dan Lynch in cooperation with the IAB arranged to hold a three day workshop for ALL vendors to come learn about how TCP/IP worked and what it still could not do well. The speakers came mostly from the DARPA research community who had both developed these protocols and used them in day-to-day work. About 250 vendor personnel came to listen to 50 inventors and experimenters. The results were surprises on both sides: the vendors were amazed to find that the inventors were so open about the way things worked (and what still did not work) and the inventors were pleased to listen to new problems they had not considered, but were being discovered by the vendors in the field. Thus a two-way discussion was formed that has lasted for over a decade.
After two years of conferences, tutorials, design meetings and workshops, a special event was organized that invited those vendors whose products ran TCP/IP well enough to come together in one room for three days to show off how well they all worked together and also ran over the Internet. In September of 1988 the first Interop trade show was born. 50 companies made the cut. 5,000 engineers from potential customer organizations came to see if it all did work as was promised. It did. Why? Because the vendors worked extremely hard to ensure that everyone’s products interoperated with all of the other products – even with those of their competitors. The Interop trade show has grown immensely since then and today it is held in 7 locations around the world each year to an audience of over 250,000 people who come to learn which products work with each other in a seamless manner, learn about the latest products, and discuss the latest technology.
In parallel with the commercialization efforts that were highlighted by the Interop activities, the vendors began to attend the IETF meetings that were held 3 or 4 times a year to discuss new ideas for extensions of the TCP/IP protocol suite. Starting with a few hundred attendees mostly from academia and paid for by the government, these meetings now often exceed a thousand attendees, mostly from the vendor community and paid for by the attendees themselves. This self-selected group evolves the TCP/IP suite in a mutually cooperative manner. The reason it is so useful is that it is composed of all stakeholders: researchers, end users and vendors.
Network management provides an example of the interplay between the research and commercial communities. In the beginning of the Internet, the emphasis was on defining and implementing protocols that achieved interoperation.
As the network grew larger, it became clear that the sometime ad hoc procedures used to manage the network would not scale. Manual configuration of tables was replaced by distributed automated algorithms, and better tools were devised to isolate faults. In 1987 it became clear that a protocol was needed that would permit the elements of the network, such as the routers, to be remotely managed in a uniform way. Several protocols for this purpose were proposed, including Simple Network Management Protocol or SNMP (designed, as its name would suggest, for simplicity, and derived from an earlier proposal called SGMP) , HEMS (a more complex design from the research community) and CMIP (from the OSI community). A series of meeting led to the decisions that HEMS would be withdrawn as a candidate for standardization, in order to help resolve the contention, but that work on both SNMP and CMIP would go forward, with the idea that the SNMP could be a more near-term solution and CMIP a longer-term approach. The market could choose the one it found more suitable. SNMP is now used almost universally for network-based management.
In the last few years, we have seen a new phase of commercialization. Originally, commercial efforts mainly comprised vendors providing the basic networking products, and service providers offering the connectivity and basic Internet services. The Internet has now become almost a “commodity” service, and much of the latest attention has been on the use of this global information infrastructure for support of other commercial services. This has been tremendously accelerated by the widespread and rapid adoption of browsers and the World Wide Web technology, allowing users easy access to information linked throughout the globe. Products are available to facilitate the provisioning of that information and many of the latest developments in technology have been aimed at providing increasingly sophisticated information services on top of the basic Internet data communications.
History of the Future
On October 24, 1995, the FNC unanimously passed a resolution defining the term Internet. This definition was developed in consultation with members of the internet and intellectual property rights communities. RESOLUTION: The Federal Networking Council (FNC) agrees that the following language reflects our definition of the term “Internet”. “Internet” refers to the global information system that — (i) is logically linked together by a globally unique address space based on the Internet Protocol (IP) or its subsequent extensions/follow-ons; (ii) is able to support communications using the Transmission Control Protocol/Internet Protocol (TCP/IP) suite or its subsequent extensions/follow-ons, and/or other IP-compatible protocols; and (iii) provides, uses or makes accessible, either publicly or privately, high level services layered on the communications and related infrastructure described herein.
The Internet has changed much in the two decades since it came into existence. It was conceived in the era of time-sharing, but has survived into the era of personal computers, client-server and peer-to-peer computing, and the network computer. It was designed before LANs existed, but has accommodated that new network technology, as well as the more recent ATM and frame switched services. It was envisioned as supporting a range of functions from file sharing and remote login to resource sharing and collaboration, and has spawned electronic mail and more recently the World Wide Web. But most important, it started as the creation of a small band of dedicated researchers, and has grown to be a commercial success with billions of dollars of annual investment.
One should not conclude that the Internet has now finished changing. The Internet, although a network in name and geography, is a creature of the computer, not the traditional network of the telephone or television industry. It will, indeed it must, continue to change and evolve at the speed of the computer industry if it is to remain relevant. It is now changing to provide new services such as real time transport, in order to support, for example, audio and video streams.
The availability of pervasive networking (i.e., the Internet) along with powerful affordable computing and communications in portable form (i.e., laptop computers, two-way pagers, PDAs, cellular phones), is making possible a new paradigm of nomadic computing and communications. This evolution will bring us new applications – Internet telephone and, slightly further out, Internet television. It is evolving to permit more sophisticated forms of pricing and cost recovery, a perhaps painful requirement in this commercial world. It is changing to accommodate yet another generation of underlying network technologies with different characteristics and requirements, e.g. broadband residential access and satellites. New modes of access and new forms of service will spawn new applications, which in turn will drive further evolution of the net itself.
The most pressing question for the future of the Internet is not how the technology will change, but how the process of change and evolution itself will be managed. As this paper describes, the architecture of the Internet has always been driven by a core group of designers, but the form of that group has changed as the number of interested parties has grown. With the success of the Internet has come a proliferation of stakeholders – stakeholders now with an economic as well as an intellectual investment in the network.
We now see, in the debates over control of the domain name space and the form of the next generation IP addresses, a struggle to find the next social structure that will guide the Internet in the future. The form of that structure will be harder to find, given the large number of concerned stakeholders. At the same time, the industry struggles to find the economic rationale for the large investment needed for the future growth, for example to upgrade residential access to a more suitable technology. If the Internet stumbles, it will not be because we lack for technology, vision, or motivation. It will be because we cannot set a direction and march collectively into the future.
Did you find this resource helpful? By donating any amount, you help fund more research and content like this.
1 Perhaps this is an exaggeration based on the lead author’s residence in Silicon Valley. 2 On a recent trip to a Tokyo bookstore, one of the authors counted 14 English language magazines devoted to the Internet. 3 An abbreviated version of this article appears in the 50th anniversary issue of the CACM, Feb. 97. The authors would like to express their appreciation to Andy Rosenbloom, CACM Senior Editor, for both instigating the writing of this article and his invaluable assistance in editing both this and the abbreviated version. 4 The Advanced Research Projects Agency (ARPA) changed its name to Defense Advanced Research Projects Agency (DARPA) in 1971, then back to ARPA in 1993, and back to DARPA in 1996. We refer throughout to DARPA, the current name. 5 It was from the RAND study that the false rumor started claiming that the ARPANET was somehow related to building a network resistant to nuclear war. This was never true of the ARPANET, only the unrelated RAND study on secure voice considered nuclear war. However, the later work on Internetting did emphasize robustness and survivability, including the capability to withstand losses of large portions of the underlying networks. 6 Including amongst others Vint Cerf, Steve Crocker, and Jon Postel. Joining them later were David Crocker who was to play an important role in documentation of electronic mail protocols, and Robert Braden, who developed the first NCP and then TCP for IBM mainframes and also was to play a long term role in the ICCB and IAB. 7 This was subsequently published as V. G. Cerf and R. E. Kahn, “A protocol for packet network intercommunication”, IEEE Trans. Comm. Tech., vol. COM-22, V 5, pp. 627-641, May 1974. 8 The desirability of email interchange, however, led to one of the first “Internet books”: !%@:: A Directory of Electronic Mail Addressing and Networks, by Frey and Adams, on email address translation and forwarding. 9 Originally named Federal Research Internet Coordinating Committee, FRICC. The FRICC was originally formed to coordinate U.S. research network activities in support of the international coordination provided by the CCIRN. 10 The decommissioning of the ARPANET was commemorated on its 20th anniversary by a UCLA symposium in 1989.
P. Baran, “On Distributed Communications Networks”, IEEE Trans. Comm. Systems, March 1964. V. G. Cerf and R. E. Kahn, “A protocol for packet network interconnection”, IEEE Trans. Comm. Tech., vol. COM-22, V 5, pp. 627-641, May 1974. S. Crocker, RFC001 Host software, Apr-07-1969. R. Kahn, Communications Principles for Operating Systems. Internal BBN memorandum, Jan. 1972. Proceedings of the IEEE, Special Issue on Packet Communication Networks, Volume 66, No. 11, November 1978. (Guest editor: Robert Kahn, associate guest editors: Keith Uncapher and Harry van Trees) L. Kleinrock, “Information Flow in Large Communication Nets”, RLE Quarterly Progress Report, July 1961. L. Kleinrock, Communication Nets: Stochastic Message Flow and Delay, Mcgraw-Hill (New York), 1964. L. Kleinrock, Queueing Systems: Vol II, Computer Applications, John Wiley and Sons (New York), 1976 J.C.R. Licklider & W. Clark, “On-Line Man Computer Communication”, August 1962. L. Roberts & T. Merrill, “Toward a Cooperative Network of Time-Shared Computers”, Fall AFIPS Conf., Oct. 1966. L. Roberts, “Multiple Computer Networks and Intercomputer Communication”, ACM Gatlinburg Conf., October 1967.
Barry M. Leiner was Director of the Research Institute for Advanced Computer Science . He passed away in April 2003. Vinton G. Cerf is Vice President and Chief Internet Evangelist at Google . David D. Clark is Senior Research Scientist at the MIT Laboratory for Computer Science . Robert E. Kahn is President of the Corporation for National Research Initiatives . Leonard Kleinrock is a Distinguished Professor of Computer Science at the University of California, Los Angeles, and is a Founder of Linkabit Corp., TTI/Vanguard, Nomadix Inc., and Platformation Inc. Daniel C. Lynch is a founder of the Interop networking trade show and conferences . Jon Postel served as Director of the Computer Networks Division of the Information Sciences Institute of the University of Southern California until his untimely death October 16, 1998. Dr. Lawrence G. Roberts was CEO, President, and Chairman of Anagran, Inc . He passed away in December 2019. Stephen Wolff is Principal Scientist of Internet2 .
We need your support today
Independent journalism is more important than ever. Vox is here to explain this unprecedented election cycle and help you understand the larger stakes. We will break down where the candidates stand on major issues, from economic policy to immigration, foreign policy, criminal justice, and abortion. We’ll answer your biggest questions, and we’ll explain what matters — and why. This timely and essential task, however, is expensive to produce.
We rely on readers like you to fund our journalism. Will you support our work and become a Vox Member today?
The internet, explained
by Timothy B. Lee

What is the internet?
The internet is the world’s most popular computer network. It began as an academic research project in 1969, and became a global commercial network in the 1990s. Today it is used by more than 2 billion people around the world.
The internet is notable for its decentralization. No one owns the internet or controls who can connect to it. Instead, thousands of different organizations operate their own networks and negotiate voluntary interconnection agreements.
Most people access internet content using a web browser. Indeed, the web has become so popular that many people incorrectly treat the internet and the web as synonymous. But in reality, the web is just one of many internet applications. Other popular Internet applications include email and BitTorrent.
Where is the internet?
The internet has three basic parts:
The last mile is the part of the internet that connects homes and small businesses to the internet. Currently, about 60 percent of residential internet connections in the United States are provided by cable TV companies such as Comcast and Time Warner. Of the remaining 40 percent, a growing fraction use new fiber optic cables, most of which are part of Verizon’s FiOS program or AT&T’s U-Verse. Finally, a significant but shrinking number use outdated DSL service provided over telephone cables.
The last mile also includes the towers that allow people to access the internet with their cell phones. Wireless internet service accounts for a large and growing share of all internet usage.
- Data centers are rooms full of servers that store user data and host online apps and content. Some are owned by large companies such as Google and Facebook. Others are commercial facilities that provide service to many smaller websites. Data centers have very fast internet connections, allowing them to serve many users simultaneously. Data centers can be located anywhere in the world, but they are often located in remote areas where land and electricity are cheap. For example, Google , Facebook , and Microsoft have all constructed vast data centers in Iowa.
- The backbone consists of long-distance networks — mostly on fiber optic cables — that carry data between data centers and consumers. The backbone market is highly competitive. Backbone providers frequently connect their networks together at internet exchange points , usually located in major cities. Establishing a presence at IEPs makes it much easier for backbone providers to improve their connections to others.

Cables at an Internet Exchange Point. ( Fabienne Serriere )
Who created the internet?
The internet began as ARPANET , an academic research network that was funded by the military’s Advanced Research Projects Agency (ARPA, now DARPA). The project was led by Bob Taylor , an ARPA administrator, and the network was built by the consulting firm of Bolt, Beranek and Newman. It began operations in 1969.
In 1973, software engineers Vint Cerf and Bob Kahn began work on the next generation of networking standards for the ARPANET. These standards, known as TCP/IP , became the foundation of the modern internet. ARPANET switched to using TCP/IP on January 1, 1983.
During the 1980s, funding for the internet shifted from the military to the National Science Foundation. The NSF funded the long-distance networks that served as the internet’s backbone from 1981 until 1994. In 1994, the Clinton Administration turned control over the internet backbone to the private sector. It has been privately operated and funded ever since.
Did Al Gore invent the internet?
Former Vice President Al Gore is frequently quoted as claiming credit for the invention of the internet, but what he actually said in a 1999 CNN interview was “I took the initiative in creating the internet.” Gore was widely mocked for this statement. But the men who did invent the internet, TCP/IP designers Bob Kahn and Vint Cerf, wrote in Gore’s defense in 2000. They argue that Gore was “the first political leader to recognize the importance of the internet and to promote and support its development.”
“As far back as the 1970s Congressman Gore promoted the idea of high speedtelecommunications,” the pair wrote. “As a Senator in the 1980s Gore urged government agencies to consolidate what at the time were several dozen different and unconnected networks into an ‘Interagency Network.’” Gore sponsored the 1991 High Performance Computing and Communications Act , which Kahn and Cerf say “became one of the major vehicles for the spread of the internet beyond the field of computer science.“
Who runs the internet?
No one runs the internet. It’s organized as a decentralized network of networks. Thousands of companies, universities, governments, and other entities operate their own networks and exchange traffic with each other based on voluntary interconnection agreements.
The shared technical standards that make the internet work are managed by an organization called the Internet Engineering Task Force. The IETF is an open organization; anyone is free to attend meetings, propose new standards, and recommend changes to existing standards. No one is required to adopt standards endorsed by the IETF, but the IETF’s consensus-based decision-making process helps to ensure that its recommendations are generally adopted by the internet community.
The Internet Corporation for Assigned Names and Numbers (ICANN) is sometimes described as being responsible for internet governance. As its name implies, ICANN is in charge of distributing domain names (like vox.com) and IP addresses . But ICANN doesn’t control who can connect to the internet or what kind of information can be sent over it.
What’s an IP address?
Internet Protocol addresses are numbers that computers use to identify each other on the internet. For example, an IP address for vox.com is 216.146.46.10.
An ICANN department known as the Internet Assigned Numbers Authority is responsible for distributing IP addresses to ensure that two different organizations don’t use the same address.
What is IPv6?
The current internet standard, known as IPv4, only allows for about 4 billion IP addresses. This was considered a very big number in the 1970s, but today, the supply of IPv4 addresses is nearly exhausted.
So internet engineers have developed a new standard called IPv6. IPv6 allows for a mind-boggling number of unique addresses — the exact figure is 39 digits long — ensuring that the world will never again run out.
At first, the transition to IPv6 was slow. Technical work on the standard was completed in the 1990s, but the internet community faced a serious chicken-and-egg problem: as long as most people were using IPv4, there was little incentive for anyone to switch to IPv6.
But as IPv4 addresses became scarce, IPv6 adoption accelerated. The fraction of users who connected to Google via IPv6 grew from 1 percent at the beginning of 2013 to 6 percent in mid-2015.
How does wireless internet work?
In its early years, internet access was carried over physical cables. But more recently, wireless internet access has become increasingly common.
There are two basic types of wireless internet access: wifi and cellular. Wifi networks are relatively simple. Anyone can purchase wifi networking equipment in order to provide internet access in a home or business. Wifi networks use unlicensed spectrum: electromagnetic frequencies that are available for anyone to use without charge. To prevent neighbors’ networks from interfering with each other, there are strict limits on the power (and therefore the range) of wifi networks.
Cellular networks are more centralized. They work by breaking up the service territory into cells. In the densest areas, cells can be as small as a single city block; in rural areas a cell can be miles across. Each cell has a tower at its center providing services to devices there. When a device moves from one cell to another, the network automatically hands off the device from one tower to another, allowing the user to continue communicating without interruption.
Cells are too large to use the unlicensed, low-power spectrum used by wifi networks. Instead, cellular networks use spectrum licensed for their exclusive use. Because this spectrum is scarce, it is usually awarded by auction. Wireless auctions have generated tens of billions of dollars in revenue for the US treasury since the first one was held in 1994.
What is the cloud?
The cloud describes an approach to computing that has become popular in the early 2000s. By storing files on servers and delivering software over the internet, cloud computing provides users with a simpler, more reliable computing experience. Cloud computing allows consumers and businesses to treat computing as a utility, leaving the technical details to technology companies.
For example, in the 1990s, many people used Microsoft Office to edit documents and spreadsheets. They stored documents on their hard drives. And when a new version of Microsoft Office was released, customers had to purchase it and manually install it on their PCs.
In contrast, Google Docs is a cloud office suite. When a user visits docs.google.com, she automatically gets the latest version of Google Docs. Because her files are stored on Google’s servers, they’re available from any computer. Even better, she doesn’t have to worry about losing her files in a hard drive crash. (Microsoft now has its own cloud office suite called Office 365.)
There are many other examples. Gmail and Hotmail are cloud email services that have largely replaced desktop email clients such as Outlook. Dropbox is a cloud computing service that automatically synchronizes data between devices, saving people from having to carry files around on floppy disks. Apple’s iCloud automatically copies users’ music and other files from their desktop computer to their mobile devices, saving users the hassle of synchronizing via a USB connection.
Cloud computing is having a big impact for businesses too. In the 1990s, companies wanting to create a website needed to purchase and operate their own servers. But in 2006, Amazon.com launched Amazon Web Services, which allows customers to rent servers by the hour. That has lowered the barrier to entry for creating websites and made it much easier for sites to quickly expand capacity as they grow more popular.
What is a packet?
A packet is the basic unit of information transmitted over the internet. Splitting information up into small, digestible pieces allows the network’s capacity to be used more efficiently.
A packet has two parts. The header contains information that helps the packet get to its destination, including the length of the packet, its source and destination, and a checksum value that helps the recipient detect if a packet was damaged in transit. After the header comes the actual data. A packet can contain up to 64 kilobytes of data, which is roughly 20 pages of plain text.
If internet routers experience congestion or other technical problems, they are allowed to deal with it by simply discarding packets. It’s the sending computer’s responsibility to detect that a packet didn’t reach its destination and send another copy. This approach might seem counterintuitive, but it simplifies the internet’s core infrastructure, leading to higher performance at lower cost.
What is the World Wide Web?
The World Wide Web is a popular way to publish information on the internet. The web was created by Timothy Berners-Lee , a computer programmer at the European scientific research organization CERN , in 1991. It offered a more powerful and user-friendly interface than other internet applications. The web supported hyperlinks, allowing users to browse from one document to another with a single click.
Over time, the web became increasingly sophisticated, supporting images, audio, video, and interactive content. In the mid-1990s, companies such as Yahoo and Amazon.com began building profitable businesses based on the web. In the 2000s, full-featured web-based applications such as Yahoo Maps and Google Docs were created.
In 1994, Berners-Lee created the World Wide Web Consortium (W3C) to be the web’s official standards organization. He is still the W3C’s director and continues to oversee the development of web standards. However, the web is an open platform, and the W3C can’t compel anyone to adopt its recommendations. In practice, the organizations with the most influence over the web are Microsoft, Google, Apple, and Mozilla, the companies that produce the leading web browsers. Any technologies adopted by these four become de facto web standards.
The web has become so popular that many people now regard it as synonymous with the internet itself. But technically, the web is just one of many internet applications. Other applications include email and BitTorrent.
What’s a web browser?
A web browser is a computer program that allows users to download and view websites. Web browsers are available for desktop computers, tablets, and mobile phones.
The first widely used browser was Mosaic , created by researchers at the University of Illinois. The Mosaic team moved to California to found Netscape , which built the first commercially successful web browser in 1994.
Netscape’s popularity was soon eclipsed by Microsoft’s Internet Explorer , but an open source version of Netscape’s browser became the modern Firefox browser. Apple released its Safari browser in 2003, and Google released a browser called Chrome in 2008. By 2015, Chrome had grown to be the most popular web browser with a market share around 50 percent. Internet Explorer, Firefox, and Safari also had significant market share.
What is SSL?
SSL, short for Secure Sockets Layer, is a family of encryption technologies that allows web users to protect the privacy of information they transmit over the internet.
When you visit a secure website such as Gmail.com, you’ll see a lock next to the URL, indicating that your communications with the site are encrypted. Here’s what that looks like in Google’s Chrome browser:

That lock is supposed to signal that third parties won’t be able to read any information you send or receive. Under the hood, SSL accomplishes that by transforming your data into a coded message that only the recipient knows how to decipher. If a malicious party is listening to the conversation, it will only see a seemingly random string of characters, not the contents of your emails, Facebook posts, credit card numbers, or other private information.
SSL was introduced by Netscape in 1994. In its early years, it was only used on a few types of websites, such as online banking sites. By the early 2010s, Google, Yahoo, and Facebook all used SSL encryption for their websites and online services. More recently, there has been a movement toward making the use of SSL universal. In 2015, Mozilla announced that future versions of the Firefox browser would treat the lack of SSL encryption as a security flaw, as a way to encourage all websites to upgrade. Google is considering taking the same step with Chrome.
What is the Domain Name System?
The Domain Name System (DNS) is the reason you can access Vox by typing vox.com into your browser rather than a hard-to-remember numeric address such as 216.146.46.10.
The system is hierarchical. For example, the .com domain is administered by a company called Verisign. Verisign assigns sub-domains like google.com and vox.com. Owners of these second-level domains, in turn, can create sub-domains such as mail.google.com and maps.google.com.
Because popular websites use domain names to identify themselves to the public, the security of DNS has become an increasing concern. Criminals and government spies alike have sought to compromise DNS in order to impersonate popular websites such as facebook.com and gmail.com and intercept their private communications. A standard called DNSSEC seeks to beef up DNS security with encryption, but few people have adopted it.
Who decides what domain names exist and who gets them?
The domain name system is administered by the Internet Corporation for Assigned Names and Numbers (ICANN), a non-profit organization based in California. ICANN was founded in 1998. It was granted authority over DNS by the US Commerce Department, though it has increasingly asserted its independence from the US government.
There are two types of domain names. The first is generic top-level domains (gTLDs) such as .com, .edu, .org, and .gov. Because the internet originated in the United States, these domains tend to be most popular there. Authority over these domains is usually delegated to private organizations.
There are also country-code top-level domains (ccTLDs). Each country in the world has its own 2-letter code. For example, the ccTLD for the United States is .us, Great Britain’s is .uk, and China’s is .cn. These domains are administered by authorities in each country. Some ccTLDs, such as .tv (for the island nation of Tuvalu) and .io (the British Indian Ocean Territory), have become popular for use outside of their home countries.
In 2011, ICANN voted to make it easier to create new gTLDs. As a result, there may be dozens or even hundreds of new domains in the next few years.
Most Popular
- The state of the 2024 race, explained in 7 charts
- What the polls show about Harris’s chances against Trump
- America isn’t ready for another war — because it doesn’t have the troops
- Two astronauts are stranded in space. This one is jealous.
- Take a mental break with the newest Vox crossword
Today, Explained
Understand the world with a daily explainer plus the most compelling stories of the day.
This is the title for the native ad
More in archives

Given the Court’s Republican supermajority, this case is unlikely to end well for trans people.

Learn about saving, spending, investing, and more in a monthly personal finance advice column written by Nicole Dieker.

The latest news, analysis, and explainers coming out of the GOP Iowa caucuses.

The economy’s stacked against us.

A Texas judge issued a national ruling against medication abortion. Here’s what you need to know.
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
- How Teens Do Research in the Digital World
Table of Contents
- Part I: Introduction
- Part II: The Mixed Impact of Digital Technologies on Student Research
- Part III: The Changing Definition of “Research”
- Part IV: Teaching Research Skills in Today’s Digital Environment
- Part V: Teachers’ Concerns About Broader Impacts of Digital Technologies on Their Students
- Methodology
Three-quarters of AP and NWP teachers say that the internet and digital search tools have had a “mostly positive” impact on their students’ research habits, but 87% say these technologies are creating an “easily distracted generation with short attention spans” and 64% say today’s digital technologies “do more to distract students than to help them academically.”
These complex and at times contradictory judgments emerge from 1) an online survey of more than 2,000 middle and high school teachers drawn from the Advanced Placement (AP) and National Writing Project (NWP) communities; and 2) a series of online and offline focus groups with middle and high school teachers and some of their students. The study was designed to explore teachers’ views of the ways today’s digital environment is shaping the research and writing habits of middle and high school students. Building on the Pew Internet Project’s prior work about how people use the internet and, especially, the information-saturated digital lives of teens, this research looks at teachers’ experiences and observations about how the rise of digital material affects the research skills of today’s students.
Overall, teachers who participated in this study characterize the impact of today’s digital environment on their students’ research habits and skills as mostly positive, yet multi-faceted and not without drawbacks. Among the more positive impacts they see: the best students access a greater depth and breadth of information on topics that interest them; students can take advantage of the availability of educational material in engaging multimedia formats; and many become more self-reliant researchers.
At the same time, these teachers juxtapose these benefits against some emerging concerns. Specifically, some teachers worry about students’ overdependence on search engines; the difficulty many students have judging the quality of online information; the general level of literacy of today’s students; increasing distractions pulling at students and poor time management skills; students’ potentially diminished critical thinking capacity; and the ease with which today’s students can borrow from the work of others.
These teachers report that students rely mainly on search engines to conduct research, in lieu of other resources such as online databases, the news sites of respected news organizations, printed books, or reference librarians.
Overall, the vast majority of these teachers say a top priority in today’s classrooms should be teaching students how to “judge the quality of online information.” As a result, a significant portion of the teachers surveyed here report spending class time discussing with students how search engines work, how to assess the reliability of the information they find online, and how to improve their search skills. They also spend time constructing assignments that point students toward the best online resources and encourage the use of sources other than search engines.
These are among the main findings of an online survey of a non-probability sample of 2,462 middle and high school teachers currently teaching in the U.S., Puerto Rico and the U.S. Virgin Islands, conducted between March 7 and April 23, 2012. Some 1,750 of the teachers are drawn from a sample of advanced placement (AP) high school teachers, while the remaining 712 are from a sample of National Writing Project teachers. Survey findings are complemented by insights from a series of online and in-person focus groups with middle and high school teachers and students in grades 9-12, conducted between November, 2011 and February, 2012.
This particular sample is quite diverse geographically, by subject matter taught, and by school size and community characteristics. But it skews towards “cutting edge” educators who teach some of the most academically successful students in the country. Thus, the findings reported here reflect the realities of their special place in American education, and are not necessarily representative of all teachers in all schools. At the same time, these findings are especially powerful given that these teachers’ observations and judgments emerge from some of the nation’s most advanced classrooms.
The internet and digital technologies are significantly impacting how students conduct research: 77% of these teachers say the overall impact is “mostly positive,” but they sound many cautionary notes
Asked to assess the overall impact of the internet and digital technologies on students’ research habits, 77% of these teachers say it has been “mostly positive.” Yet, when asked if they agree or disagree with specific assertions about how the internet is impacting students’ research, their views are decidedly mixed.
On the more encouraging side, virtually all (99%) AP and NWP teachers in this study agree with the notion that the internet enables students to access a wider range of resources than would otherwise be available, and 65% also agree that the internet makes today’s students more self-sufficient researchers.
At the same time, 76% of teachers surveyed “ strongly agree” with the assertion that internet search engines have conditioned students to expect to be able to find information quickly and easily. Large majorities also agree with the assertion that the amount of information available online today is overwhelming to most students (83%) and that today’s digital technologies discourage students from using a wide range of sources when conducting research (71%). Fewer teachers, but still a majority of this sample (60%), agree with the assertion that today’s technologies make it harder for students to find credible sources of information.
The internet has changed the very meaning of “research”
Perhaps the greatest impact this group of teachers sees today’s digital environment having on student research habits is the degree to which it has changed the very nature of “research” and what it means to “do research.” Teachers and students alike report that for today’s students, “research” means “Googling.” As a result, some teachers report that for their students “doing research” has shifted from a relatively slow process of intellectual curiosity and discovery to a fast-paced, short-term exercise aimed at locating just enough information to complete an assignment.
These perceptions are evident in teachers’ survey responses: 94% of the teachers surveyed say their students are “very likely ” to use Google or other online search engines in a typical research assignment, placing it well ahead of all other sources that we asked about. Second and third on the list of frequently used sources are online encyclopedias such as Wikipedia, and social media sites such as YouTube. In descending order, the sources teachers in our survey say students are “very likely” to use in a typical research assignment:
- Google or other online search engine (94%)
- Wikipedia or other online encyclopedia (75%)
- YouTube or other social media sites (52%)
- Their peers (42%)
- Spark Notes, Cliff Notes, or other study guides (41%)
- News sites of major news organizations (25%)
- Print or electronic textbooks (18%)
- Online databases such as EBSCO, JSTOR, or Grolier (17%)
- A research librarian at their school or public library (16%)
- Printed books other than textbooks (12%)
- Student-oriented search engines such as Sweet Search (10%)
In response to this trend, many teachers say they shape research assignments to address what they feel can be their students’ overdependence on search engines and online encyclopedias. Nine in ten (90%) direct their students to specific online resources they feel are most appropriate for a particular assignment, and 83% develop research questions or assignments that require students to use a wider variety of sources, both online and offline.
Most teachers encourage online research, including the use of digital technologies such as cell phones to find information quickly, yet point to barriers in the school environment impeding quality online research
Asked which online activities they have students engage in, 95% of the teachers in this survey report having students “do research or search for information online,” making it the most common online task. Conducting research online is followed by accessing or downloading assignments (79%) or submitting assignments (75%) via online platforms.
These teachers report using a wide variety of digital tools in their classrooms and assignments, well beyond the typical desktop and laptop computers. Specifically, majorities say they and/or their students use cell phones (72%), digital cameras (66%), and digital video recorders (55%) either in the classroom or to complete school assignments. Cell phones are becoming particularly popular learning tools, and are now as common to these teachers’ classrooms as computer carts. According to respondents, the most popular school task students use cell phones for is “to look up information in class,” cited by 42% of the teachers participating in the survey.
Yet, survey results also indicate teachers face a variety of challenges in incorporating digital tools into their classrooms, some of which, they suggest, may hinder how students are taught to conduct research online. Virtually all teachers surveyed work in a school that employs internet filters (97%), formal policies about cell phone use (97%) and acceptable use policies or AUPs (97%). The degree to which teachers feel these policies impact their teaching varies, with internet filters cited most often as having a “major impact” on survey participants’ teaching (32%). One in five teachers (21%) say cell phone policies have a “major” impact on their teaching, and 16% say the same about their school’s AUP. These impacts are felt most strongly among those teaching the lowest income students.
Teachers give students’ research skills modest ratings
Despite viewing the overall impact of today’s digital environment on students’ research habits as “mostly positive,” teachers rate the actual research skills of their students as “good” or “fair” in most cases. Very few teachers rate their students “excellent” on any of the research skills included in the survey. This is notable, given that the majority of the sample teaches Advanced Placement courses to the most academically advanced students.
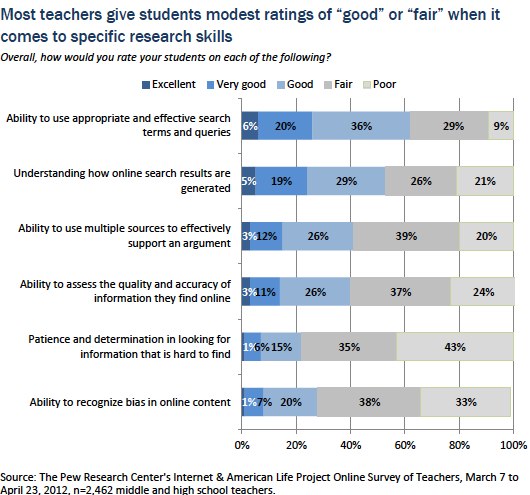
Students receive the highest marks from these teachers for their ability to use appropriate and effective search queries and their understanding of how online search results are generated. Yet even for these skills, only about one-quarter of teachers surveyed here rate their students “excellent” or “very good.” Indeed, in our focus groups, many teachers suggest that despite being raised in the “digital age,” today’s students are surprisingly lacking in their online search skills. Students receive the lowest marks for “patience and determination in looking for information that is hard to find,” with 43% of teachers rating their students “poor” in this regard, and another 35% rating their students “fair.”
Given these perceived deficits in key skills, it is not surprising that 80% of teachers surveyed say they spend class time discussing with students how to assess the reliability of online information, and 71% spend class time discussing how to conduct research online in general. Another 57% spend class time helping students improve their search skills and 35% devote class time to helping students understand how search engines work and how search results are generated. In addition, asked what curriculum changes might be necessary in middle and high schools today, 47% “strongly agree” and 44% “somewhat agree” that courses or content focusing on digital literacy must be incorporated into every school’s curriculum.
A richer information environment, but at the price of distracted students?
Teachers are evenly divided on the question of whether today’s students are fundamentally different from previous generations; 47% agree and 52% disagree with the statement that “today’s students are really no different than previous generations, they just have different tools through which to express themselves.” Responses to this item were consistent across the full sample of teachers regardless of the teachers’ age or experience level, the subject or grade level taught, or the type of community in which they teach.
At the same time, asked whether they agree or disagree that “today’s students have fundamentally different cognitive skills because of the digital technologies they have grown up with,” 88% of the sample agree, including 40% who “strongly agree.” Teachers of the lowest income students are the most likely to “strongly agree” with this statement (46%) but the differences across student socioeconomic status are slight, and there are no other notable differences across subgroups of teachers in the sample.
Overwhelming majorities of these teachers also agree with the assertions that “today’s digital technologies are creating an easily distracted generation with short attention spans” (87%) and “today’s students are too ‘plugged in’ and need more time away from their digital technologies” (86%). Two-thirds (64%) agree with the notion that “today’s digital technologies do more to distract students than to help them academically.” In focus groups, some teachers commented on the connection they see between students’ “overexposure” to technology, and the resulting lack of focus and diminished ability to retain knowledge they see among some students. Time management is also becoming a serious issue among students, according to some teachers; in their experience, today’s digital technologies not only encourage students to assume all tasks can be finished quickly and at the last minute, but students also use various digital tools at their disposal to “waste time” and procrastinate.
Thus, despite 77% of the survey respondents describing the overall impact of the internet and digital technologies on students’ research habits as “mostly positive,” the broad story is more complex. While majorities of teachers surveyed see the internet and other digital technologies encouraging broader and deeper learning by connecting students to more resources about topics that interest them, enabling them to access multimedia content, and broadening their worldviews, these teachers are at the same time concerned about digital distractions and students’ abilities to focus on tasks and manage their time. While some frame these issues as stemming directly from digital technologies and the particular students they teach, others suggest the concerns actually reflect a slow response from parents and educators to shape their own expectations and students’ learning environments in a way that better reflects the world today’s students live in.
About the data collection
Data collection was conducted in two phases. In phase one, Pew Internet conducted two online and one in-person focus group with middle and high school teachers; focus group participants included Advanced Placement (AP) teachers, teachers who had participated in the National Writing Project’s Summer Institute (NWP), as well as teachers at a College Board school in the Northeast U.S. Two in-person focus groups were also conducted with students in grades 9-12 from the same College Board school. The goal of these discussions was to hear teachers and students talk about, in their own words, the different ways they feel digital technologies such as the internet, search engines, social media, and cell phones are shaping students’ research and writing habits and skills. Teachers were asked to speak in depth about teaching research and writing to middle and high school students today, the challenges they encounter, and how they incorporate digital technologies into their classrooms and assignments.
Focus group discussions were instrumental in developing a 30-minute online survey, which was administered in phase two of the research to a national sample of middle and high school teachers. The survey results reported here are based on a non-probability sample of 2,462 middle and high school teachers currently teaching in the U.S., Puerto Rico, and the U.S. Virgin Islands. Of these 2,462 teachers, 2,067 completed the entire survey; all percentages reported are based on those answering each question. The sample is not a probability sample of all teachers because it was not practical to assemble a sampling frame of this population. Instead, two large lists of teachers were assembled: one included 42,879 AP teachers who had agreed to allow the College Board to contact them (about one-third of all AP teachers), while the other was a list of 5,869 teachers who participated in the National Writing Project’s Summer Institute during 2007-2011 and who were not already part of the AP sample. A stratified random sample of 16,721 AP teachers was drawn from the AP teacher list, based on subject taught, state, and grade level, while all members of the NWP list were included in the final sample.
The online survey was conducted from March 7–April 23, 2012. More details on how the survey and focus groups were conducted are included in the Methodology section at the end of this report, along with focus group discussion guides and the survey instrument.
About the teachers who participated in the survey
There are several important ways the teachers who participated in the survey are unique, which should be considered when interpreting the results reported here. First, 95% of the teachers who participated in the survey teach in public schools, thus the findings reported here reflect that environment almost exclusively. In addition, almost one-third of the sample (NWP Summer Institute teachers) has received extensive training in how to effectively teach writing in today’s digital environment. The National Writing Project’s mission is to provide professional development, resources and support to teachers to improve the teaching of writing in today’s schools. The NWP teachers included here are what the organization terms “teacher-consultants” who have attended the Summer Institute and provide local leadership to other teachers. Research has shown significant gains in the writing performance of students who are taught by these teachers. 1
Moreover, the majority of teachers participating in the survey (56%) currently teach AP, honors, and/or accelerated courses, thus the population of middle and high school students they work with skews heavily toward the highest achievers. These teachers and their students may have resources and support available to them—particularly in terms of specialized training and access to digital tools—that are not available in all educational settings. Thus, the population of teachers participating in this research might best be considered “leading edge teachers” who are actively involved with the College Board and/or the National Writing Project and are therefore beneficiaries of resources and training not common to all teachers. It is likely that teachers in this study are developing some of the more innovative pedagogical approaches to teaching research and writing in today’s digital environment, and are incorporating classroom technology in ways that are not typical of the entire population of middle and high school teachers in the U.S. Survey findings represent the attitudes and behaviors of this particular group of teachers only, and are not representative of the entire population of U.S. middle and high school teachers.
Every effort was made to administer the survey to as broad a group of educators as possible from the sample files being used. As a group, the 2,462 teachers participating in the survey comprise a wide range of subject areas, experience levels, geographic regions, school type and socioeconomic level, and community type (detailed sample characteristics are available in the Methodology section of this report). The sample includes teachers from all 50 states, Puerto Rico, and the U.S. Virgin Islands. All teachers who participated in the survey teach in physical schools and classrooms, as opposed to teaching online or virtual courses.
English/language arts teachers make up a significant portion of the sample (36%), reflecting the intentional design of the study, but history, social science, math, science, foreign language, art, and music teachers are also represented. About one in ten teachers participating in the survey are middle school teachers, while 91% currently teach grades 9-12. There is wide distribution across school size and students’ socioeconomic status, though half of the teachers participating in the survey report teaching in a small city or suburb. There is also a wide distribution in the age and experience levels of participating teachers. The survey sample is 71% female.
About the Pew Research Center’s Internet & American Life Project
The Pew Research Center’s Internet & American Life Project is one of seven projects that make up the Pew Research Center, a nonpartisan, nonprofit “fact tank” that provides information on the issues, attitudes and trends shaping America and the world. The Project produces reports exploring the impact of the internet on families, communities, work and home, daily life, education, health care, and civic and political life. The Pew Internet Project takes no positions on policy issues related to the internet or other communications technologies. It does not endorse technologies, industry sectors, companies, nonprofit organizations, or individuals. While we thank our research partners for their helpful guidance, the Pew Internet Project had full control over the design, implementation, analysis and writing of this survey and report.
About the College Board
The College Board is a mission-driven not-for-profit organization that connects students to college success and opportunity. Founded in 1900, the College Board was created to expand access to higher education. Today, the membership association is made up of over 6,000 of the world’s leading educational institutions and is dedicated to promoting excellence and equity in education. Each year, the College Board helps more than seven million students prepare for a successful transition to college through programs and services in college readiness and college success — including the SAT ® and the Advanced Placement Program ® . The organization also serves the education community through research and advocacy on behalf of students, educators and schools. For further information, visit www.collegeboard.org .
About the National Writing Project
The National Writing Project (NWP) is a nationwide network of educators working together to improve the teaching of writing in the nation’s schools and in other settings. NWP provides high-quality professional development programs to teachers in a variety of disciplines and at all levels, from early childhood through university. Through its nearly 200 university-based sites serving all 50 states, the District of Columbia, Puerto Rico and the U.S. Virgin Islands, NWP develops the leadership, programs and research needed for teachers to help students become successful writers and learners. For more information, visit www.nwp.org .
- More specific information on this population of teachers, the training they receive, and the outcomes of their students are available at the National Writing Project website at www.nwp.org . ↩
Sign up for our weekly newsletter
Fresh data delivery Saturday mornings
Sign up for The Briefing
Weekly updates on the world of news & information
- Online Search
- Teens & Tech
- Teens & Youth
72% of U.S. high school teachers say cellphone distraction is a major problem in the classroom
U.s. public, private and charter schools in 5 charts, is college worth it, half of latinas say hispanic women’s situation has improved in the past decade and expect more gains, a quarter of u.s. teachers say ai tools do more harm than good in k-12 education, most popular.
901 E St. NW, Suite 300 Washington, DC 20004 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
© 2024 Pew Research Center
The University of Chicago The Law School
Innovation clinic—significant achievements for 2023-24.
The Innovation Clinic continued its track record of success during the 2023-2024 school year, facing unprecedented demand for our pro bono services as our reputation for providing high caliber transactional and regulatory representation spread. The overwhelming number of assistance requests we received from the University of Chicago, City of Chicago, and even national startup and venture capital communities enabled our students to cherry-pick the most interesting, pedagogically valuable assignments offered to them. Our focus on serving startups, rather than all small- to medium-sized businesses, and our specialization in the needs and considerations that these companies have, which differ substantially from the needs of more traditional small businesses, has proven to be a strong differentiator for the program both in terms of business development and prospective and current student interest, as has our further focus on tackling idiosyncratic, complex regulatory challenges for first-of-their kind startups. We are also beginning to enjoy more long-term relationships with clients who repeatedly engage us for multiple projects over the course of a year or more as their legal needs develop.
This year’s twelve students completed over twenty projects and represented clients in a very broad range of industries: mental health and wellbeing, content creation, medical education, biotech and drug discovery, chemistry, food and beverage, art, personal finance, renewable energy, fintech, consumer products and services, artificial intelligence (“AI”), and others. The matters that the students handled gave them an unparalleled view into the emerging companies and venture capital space, at a level of complexity and agency that most junior lawyers will not experience until several years into their careers.
Representative Engagements
While the Innovation Clinic’s engagements are highly confidential and cannot be described in detail, a high-level description of a representative sample of projects undertaken by the Innovation Clinic this year includes:
Transactional/Commercial Work
- A previous client developing a symptom-tracking wellness app for chronic disease sufferers engaged the Innovation Clinic again, this time to restructure its cap table by moving one founder’s interest in the company to a foreign holding company and subjecting the holding company to appropriate protections in favor of the startup.
- Another client with whom the Innovation Clinic had already worked several times engaged us for several new projects, including (1) restructuring their cap table and issuing equity to an additional, new founder, (2) drafting several different forms of license agreements that the company could use when generating content for the platform, covering situations in which the company would license existing content from other providers, jointly develop new content together with contractors or specialists that would then be jointly owned by all creators, or commission contractors to make content solely owned by the company, (3) drafting simple agreements for future equity (“Safes”) for the company to use in its seed stage fundraising round, and (4) drafting terms of service and a privacy policy for the platform.
- Yet another repeat client, an internet platform that supports independent artists by creating short films featuring the artists to promote their work and facilitates sales of the artists’ art through its platform, retained us this year to draft a form of independent contractor agreement that could be used when the company hires artists to be featured in content that the company’s Fortune 500 brand partners commission from the company, and to create capsule art collections that could be sold by these Fortune 500 brand partners in conjunction with the content promotion.
- We worked with a platform using AI to accelerate the Investigational New Drug (IND) approval and application process to draft a form of license agreement for use with its customers and an NDA for prospective investors.
- A novel personal finance platform for young, high-earning individuals engaged the Innovation Clinic to form an entity for the platform, including helping the founders to negotiate a deal among them with respect to roles and equity, terms that the equity would be subject to, and other post-incorporation matters, as well as to draft terms of service and a privacy policy for the platform.
- Students also formed an entity for a biotech therapeutics company founded by University of Chicago faculty members and an AI-powered legal billing management platform founded by University of Chicago students.
- A founder the Innovation Clinic had represented in connection with one venture engaged us on behalf of his other venture team to draft an equity incentive plan for the company as well as other required implementing documentation. His venture with which we previously worked also engaged us this year to draft Safes to be used with over twenty investors in a seed financing round.
More information regarding other types of transactional projects that we typically take on can be found here .
Regulatory Research and Advice
- A team of Innovation Clinic students invested a substantial portion of our regulatory time this year performing highly detailed and complicated research into public utilities laws of several states to advise a groundbreaking renewable energy technology company as to how its product might be regulated in these states and its clearest path to market. This project involved a review of not only the relevant state statutes but also an analysis of the interplay between state and federal statutes as it relates to public utilities law, the administrative codes of the relevant state executive branch agencies, and binding and non-binding administrative orders, decisions and guidance from such agencies in other contexts that could shed light on how such states would regulate this never-before-seen product that their laws clearly never contemplated could exist. The highly varied approach to utilities regulation in all states examined led to a nuanced set of analysis and recommendations for the client.
- In another significant research project, a separate team of Innovation Clinic students undertook a comprehensive review of all settlement orders and court decisions related to actions brought by the Consumer Financial Protection Bureau for violations of the prohibition on unfair, deceptive, or abusive acts and practices under the Consumer Financial Protection Act, as well as selected relevant settlement orders, court decisions, and other formal and informal guidance documents related to actions brought by the Federal Trade Commission for violations of the prohibition on unfair or deceptive acts or practices under Section 5 of the Federal Trade Commission Act, to assemble a playbook for a fintech company regarding compliance. This playbook, which distilled very complicated, voluminous legal decisions and concepts into a series of bullet points with clear, easy-to-follow rules and best practices, designed to be distributed to non-lawyers in many different facets of this business, covered all aspects of operations that could subject a company like this one to liability under the laws examined, including with respect to asset purchase transactions, marketing and consumer onboarding, usage of certain terms of art in advertising, disclosure requirements, fee structures, communications with customers, legal documentation requirements, customer service and support, debt collection practices, arrangements with third parties who act on the company’s behalf, and more.
Miscellaneous
- Last year’s students built upon the Innovation Clinic’s progress in shaping the rules promulgated by the Financial Crimes Enforcement Network (“FinCEN”) pursuant to the Corporate Transparency Act to create a client alert summarizing the final rule, its impact on startups, and what startups need to know in order to comply. When FinCEN issued additional guidance with respect to that final rule and changed portions of the final rule including timelines for compliance, this year’s students updated the alert, then distributed it to current and former clients to notify them of the need to comply. The final bulletin is available here .
- In furtherance of that work, additional Innovation Clinic students this year analyzed the impact of the final rule not just on the Innovation Clinic’s clients but also its impact on the Innovation Clinic, and how the Innovation Clinic should change its practices to ensure compliance and minimize risk to the Innovation Clinic. This also involved putting together a comprehensive filing guide for companies that are ready to file their certificates of incorporation to show them procedurally how to do so and explain the choices they must make during the filing process, so that the Innovation Clinic would not be involved in directing or controlling the filings and thus would not be considered a “company applicant” on any client’s Corporate Transparency Act filings with FinCEN.
- The Innovation Clinic also began producing thought leadership pieces regarding AI, leveraging our distinct and uniquely University of Chicago expertise in structuring early-stage companies and analyzing complex regulatory issues with a law and economics lens to add our voice to those speaking on this important topic. One student wrote about whether non-profits are really the most desirable form of entity for mitigating risks associated with AI development, and another team of students prepared an analysis of the EU’s AI Act, comparing it to the Executive Order on AI from President Biden, and recommended a path forward for an AI regulatory environment in the United States. Both pieces can be found here , with more to come!
Innovation Trek
Thanks to another generous gift from Douglas Clark, ’89, and managing partner of Wilson, Sonsini, Goodrich & Rosati, we were able to operationalize the second Innovation Trek over Spring Break 2024. The Innovation Trek provides University of Chicago Law School students with a rare opportunity to explore the innovation and venture capital ecosystem in its epicenter, Silicon Valley. The program enables participating students to learn from business and legal experts in a variety of different industries and roles within the ecosystem to see how the law and economics principles that students learn about in the classroom play out in the real world, and facilitates meaningful connections between alumni, students, and other speakers who are leaders in their fields. This year, we took twenty-three students (as opposed to twelve during the first Trek) and expanded the offering to include not just Innovation Clinic students but also interested students from our JD/MBA Program and Doctoroff Business Leadership Program. We also enjoyed four jam-packed days in Silicon Valley, expanding the trip from the two and a half days that we spent in the Bay Area during our 2022 Trek.
The substantive sessions of the Trek were varied and impactful, and enabled in no small part thanks to substantial contributions from numerous alumni of the Law School. Students were fortunate to visit Coinbase’s Mountain View headquarters to learn from legal leaders at the company on all things Coinbase, crypto, and in-house, Plug & Play Tech Center’s Sunnyvale location to learn more about its investment thesis and accelerator programming, and Google’s Moonshot Factory, X, where we heard from lawyers at a number of different Alphabet companies about their lives as in-house counsel and the varied roles that in-house lawyers can have. We were also hosted by Wilson, Sonsini, Goodrich & Rosati and Fenwick & West LLP where we held sessions featuring lawyers from those firms, alumni from within and outside of those firms, and non-lawyer industry experts on topics such as artificial intelligence, climate tech and renewables, intellectual property, biotech, investing in Silicon Valley, and growth stage companies, and general advice on career trajectories and strategies. We further held a young alumni roundtable, where our students got to speak with alumni who graduated in the past five years for intimate, candid discussions about life as junior associates. In total, our students heard from more than forty speakers, including over twenty University of Chicago alumni from various divisions.
The Trek didn’t stop with education, though. Throughout the week students also had the opportunity to network with speakers to learn more from them outside the confines of panel presentations and to grow their networks. We had a networking dinner with Kirkland & Ellis, a closing dinner with all Trek participants, and for the first time hosted an event for admitted students, Trek participants, and alumni to come together to share experiences and recruit the next generation of Law School students. Several speakers and students stayed in touch following the Trek, and this resulted not just in meaningful relationships but also in employment for some students who attended.
More information on the purposes of the Trek is available here , the full itinerary is available here , and one student participant’s story describing her reflections on and descriptions of her experience on the Trek is available here .
The Innovation Clinic is grateful to all of its clients for continuing to provide its students with challenging, high-quality legal work, and to the many alumni who engage with us for providing an irreplaceable client pipeline and for sharing their time and energy with our students. Our clients are breaking the mold and bringing innovations to market that will improve the lives of people around the world in numerous ways. We are glad to aid in their success in any way that we can. We look forward to another productive year in 2024-2025!

IMAGES
VIDEO
COMMENTS
About half of TikTok users under 30 say they use it to keep up with politics, news. TikTok users under 30 see its impact on democracy more positively than older users, with 45% of this group saying it's mostly good for American democracy. short readsJun 12, 2024.
This wide-ranging interdisciplinary journal looks at the social, ethical, economic, managerial and political implications of the internet. Recent issues have focused on metaverse, interpretable AI, digital health, online and mobile gaming, the sharing economy, and the dark side of social media. ISSN: 1066-2243.
The internet is a social phenomenon, a tool, and also a field site for qualitative research. Depending on the role the internet plays in the qualitative research project or how it is ...
Take, for example, Beluga Bits, a research project focused on determining the sex, age and pod size of beluga whales visiting the Churchill River in northern Manitoba, Canada. With a bit of ...
This is the second of two reports emerging from the 13th "Future of the Internet" canvassing Pew Research Center and Elon University's Imagining the Internet Center have conducted together to gather expert views about important digital issues. In this report, the questions focused on the prospects for improvements in the tone and activities of the digital public sphere by 2035.
Internet research is a common practice of using Internet information, especially free information on the World Wide Web or Internet-based resources (e.g., discussion forums, social media), in research. This guide will cover considerations pertaining to participant protections when conducting Internet research, including:
Internet research is the practice of using Internet information, especially free information on the World Wide Web, or Internet-based resources (like Internet discussion forum) ... The goal is to collect information relevant to a specific research project in one place, so that it can be found and accessed again quickly. ...
Internet Research 20th Anniversary Commemorative Issue. Intelligent eservices applied to B2C ecommerce. Volume 19. Intelligent ubiquitous computing applications and security issues. Volume 18. Information credibility on the web. Volume 17. Selected research papers from the TERENA networking conference 2007.
The World Internet Project operates through the Center for the Digital Future in collaboration with 39 partner countries. Studies explore the evolution of communication technology through findings on more than 80 subject areas in broad categories that include: Internet users and non-users. Information-seeking online. Access to online services.
As AI Spreads, Experts Predict the Best and Worst Changes in Digital Life by 2035. As they watch the splashy emergence of generative artificial intelligence and an array of other AI applications, experts participating in a new Pew Research Center canvassing say they have deep concerns about people's and society's overall well-being.
Advancing the state of the art. Our teams advance the state of the art through research, systems engineering, and collaboration across Google. We publish hundreds of research papers each year across a wide range of domains, sharing our latest developments in order to collaboratively progress computing and science. Learn more about our philosophy.
All Publications →. The Pew Research Center's Internet & American Life Project, a nonprofit, nonpartisan research organization, provides free data and analysis on the social impact of the internet on families, communities, work and home, daily life, education, health care, and civic and political life.
Projects. Our teams leverage research developments across domains to build tools and technology that impact billions of people. Sharing our learnings and tools to fuel progress in the field is core to our approach. Languages. How Google is expanding support for thousands of the world's languages. Learn More.
The global Network of Internet & Society Centers (NoC) is a collaborative initiative among over 100 Centers with a focus on interdisciplinary research on the development, social impact, policy implications, and legal issues concerning the Internet. For more information please visit https://networkofcenters.net.
Our 2024 edition equips students with the latest tools and techniques. Lyndon Seitz - Editor-in-Chief. Date Modified: April 18, 2024. In today's digital age, internet research stands as an indispensable skill for students worldwide. As Bill Gates once remarked, "The Internet is becoming the town square for the global village of tomorrow."
Student's internet research guide for 2024. CS. Camryn Smith. Apr 29, 2024 — 5 min read. Read our student internet research guide for ways to search smart, check for credible sources and cite your sources. The internet is crowded! It's brimming with all kinds of information and resources. With so many choices online, it can be tricky to ...
The invited respondents were identified in previous research about the future of the Internet, from those identified by the Pew Research Center's Internet Project, and solicited through major technology-oriented listservs. They registered their answers online between November 25, 2013 and January 13, 2014.
This project will also provide an opportunity to review some of the important points and ideas presented in this chapter. To begin, consider the list of questions below. Next, visit the websites listed here and search for answers to the questions. Also, search the Internet on your own for additional sources that may help you develop an ...
Elon University and Pew Internet Project researchers regularly conducted surveys asking leaders in technology, business, research, governance or other expertise to weigh in on the impact of current and oncoming digital change. ... From 2003 to 2023 Imagining the Internet partnered with Pew Research to ask thousands of digital experts questions ...
In this paper, 3 several of us involved in the development and evolution of the Internet share our views of its origins and history. This history revolves around four distinct aspects. There is the technological evolution that began with early research on packet switching and the ARPANET (and related technologies), and where current research continues to expand the horizons of the ...
The internet is the world's most popular computer network. It began as an academic research project in 1969, and became a global commercial network in the 1990s.
1996. 77% of online users send or receive e-mail at least once every few weeks, up from 65% in 1995. Nokia releases the Nokia 9000 Communicator, the first cellphone with internet capabilities. HoTMaiL launches as one of the world's first Webmail services, its name a reference to the HTML internet language used to build webpages.
About the Pew Research Center's Internet & American Life Project. The Pew Research Center's Internet & American Life Project is one of seven projects that make up the Pew Research Center, a nonpartisan, nonprofit "fact tank" that provides information on the issues, attitudes and trends shaping America and the world.
General The Innovation Clinic continued its track record of success during the 2023-2024 school year, facing unprecedented demand for our pro bono services as our reputation for providing high caliber transactional and regulatory representation spread. The overwhelming number of assistance requests we received from the University of Chicago, City of Chicago, and even national startup and ...