Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.

OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
| ACSE | Association Control Service Element |
|---|---|
| ROSE | Remote Operation Service Element |
| CCR | Commitment Concurrency and Recovery |
| RTSE | Reliable Transfer Service Element |
SASE specific application service element
| FTAM | File Transfer, Access and Manager |
|---|---|
| VT | Virtual Terminal |
| MOTIS | Message Oriented Text Interchange Standard |
| CMIP | Common Management Information Protocol |
| JTM | Job Transfer and Manipulation |
| MMS | Manufacturing Messaging Service |
| RDA | Remote Database Access |
| DTP | Distributed Transaction Processing |
Layer 7 Application Layer
Layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
Presentation Layer In OSI Model : A Comprehensive Guide
In the vast landscape of computer networks, the OSI (Open Systems Interconnection) model stands as a fundamental framework for understanding how data is transmitted from one device to another. Among its seven layers, the presentation layer holds an important place, acting as a translator and formatter to ensure seamless communication between different systems. Through this article, we will try to know what is presentation layer in OSI model, what is its role in the field of networking and what is its importance.
Table of Contents
What is the Presentation Layer?
The Presentation Layer, within the OSI (Open Systems Interconnection) model, is the sixth layer. It focuses on the representation of data, ensuring that information exchanged between applications is formatted appropriately for transmission and receipt across a network. This layer handles tasks such as data translation, encryption, compression, and formatting. Its primary function is to ensure that data remains readable and understandable by both the sender and receiver, regardless of differences in data formats. In essence, the Presentation Layer acts as a translator and formatter, facilitating seamless communication between different systems and enhancing the reliability and security of data transmission.
Working of Presentation Layer
The Presentation Layer acts like a language translator and document formatter in the OSI model. It takes data from applications and prepares it for transmission over the network by translating it into a language that both the sender and receiver understand. Think of it as converting a letter into a universal format before mailing it overseas. Additionally, the Presentation Layer ensures that the data looks right by formatting it properly, like adjusting the font and spacing in a document. It also adds extra security by encrypting the data if needed, making it like a secret code that only the intended recipient can understand. Lastly, it might shrink the data down to save space during transmission, similar to compressing a file before emailing it. In short, the Presentation Layer makes sure data is ready for its journey across the network, keeping it secure, readable, and efficient along the way.
Functions of the Presentation Layer
- Data Translation : Converting data from the format used by the application into a format suitable for transmission over the network, and vice versa, ensuring interoperability between different systems.
- Encryption and Decryption : Securing data during transmission by encrypting it before sending and decrypting it upon reception, ensuring confidentiality and integrity of the information.
- Data Compression : Reducing the size of data before transmission to optimize bandwidth usage and speed up the transfer process, improving network efficiency.
- Data Formatting: Formatting data according to predefined standards for transmission, including character encoding, data structure, and multimedia representation, ensuring compatibility between sender and receiver applications.
- Protocol Conversion : Adapting data between different network protocols or data formats, facilitating communication between systems with varying requirements or standards.
- Character Code Translation: Converting characters between different character sets or encoding schemes to ensure proper interpretation of text-based data across systems with different language or encoding preferences.
Protocols are Use in Presentation layer
The Presentation Layer primarily focuses on data representation and formatting rather than specific protocols. However, some protocols or standards are commonly associated with the Presentation Layer due to their role in data representation and formatting. Here are a few examples.
- MIME : MIME stands for Multipurpose Internet Mail Extensions. It’s a protocol that broadens the scope of email messages, enabling the use of text in various character sets beyond ASCII. Additionally, MIME facilitates the inclusion of attachments such as audio, video, images, and application programs within emails.
- SSL/TLS : SSL/TLS protocols provide secure communication over a computer network by encrypting data between the client and server, ensuring data confidentiality and integrity. While SSL/TLS operate at the Transport Layer, they often involve encryption and decryption processes associated with the Presentation Layer.
- ASCII (: ASCII and Unicode are character encoding standards that represent text characters using numerical codes. These standards ensure consistent representation of text characters across different systems and platforms, which is crucial for data interchange.
- JPEG, GIF, PNG : These image file formats are commonly used for encoding and transmitting images over networks. While the specifics of image compression and encoding are often handled by the Application Layer, the Presentation Layer ensures proper interpretation and formatting of these image data.
- PDF : PDF is a file format used to present and exchange documents reliably, independent of software, hardware, or operating systems. The Presentation Layer ensures proper interpretation and rendering of PDF documents for display or printing
the Presentation Layer of the OSI Model acts as a translator and formatter, ensuring that data exchanged between applications remains readable and compatible across diverse systems. By handling tasks such as data translation, encryption, compression, and formatting, it enhances the reliability, efficiency, and security of data transmission over networks. Essentially, the Presentation Layer plays a crucial role in facilitating seamless communication between different systems, ensuring that information is accurately represented and securely transmitted, thus contributing to the smooth functioning of modern networking environments.
Recommended Article
- Understanding Crossover Cable and Straight-Through Cable
- Understanding The Difference Between URI and URL
- What Are The Difference Between Analog And Digital Signal
- What Are Antennas ? | Types Of Antenna And How Do They Work
- Difference Between Hub Switch And Router
- 7 Layers of the OSI Model – Definition, Layers, and Functions
- What Is Ping Command In Computer Network
- Difference Between Webpage And Website
- Difference Between OSI and TCP/IP Model in Networking
- Latest Posts
- Bachelor of Business Administration (BBA): A Comprehensive Overview - 17 August 2024
- HTTP Full Form – Definition, Features & How It Works - 14 August 2024
- DNS Full Form – Domain Name System , Types & Features - 13 August 2024
Please Share This Share this content
- Opens in a new window X
- Opens in a new window Facebook
- Opens in a new window Pinterest
- Opens in a new window LinkedIn
- Opens in a new window WhatsApp
You Might Also Like
Different types of network topology and their details, modem in computer network features, types & working, ftp server in windows 10.
Presentation Layer
Last Edited
What is the Presentation Layer?
Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model . The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation of graphics commands, and so on. The network redirector also functions at this layer.
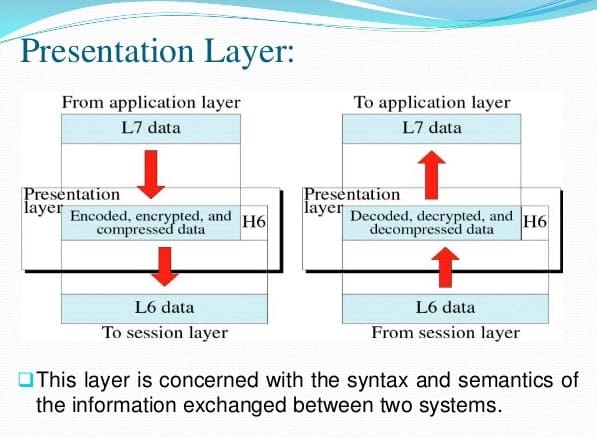
Presentation Layer functions
- Translation: Before being transmitted, information in the form of characters and numbers should be changed to bit streams. Layer 6 is responsible for interoperability between encoding methods as different computers use different encoding methods. It translates data between the formats the network requires and the format the computer.
- Encryption: Encryption at the transmitter and decryption at the receiver
- Compression: Data compression to reduce the bandwidth of the data to be transmitted. The primary role of data compression is to reduce the number of bits to be transmitted. Multimedia files, such as audio and video, are bigger than text files and compression is more important.
Role of Presentation Layer in the OSI Model
This layer is not always used in network communications because its functions are not always necessary. Translation is only needed if different types of machines need to talk with each other. Encryption is optional in communication. If the information is public there is no need to encrypt and decrypt info. Compression is also optional. If files are small there is no need for compression.
Explaining Layer 6 in video
Most real-world protocol suites, such as TCP/IP , do not use separate presentation layer protocols. This layer is mostly an abstraction in real-world networking.
An example of a program that loosely adheres to layer 6 of OSI is the tool that manages the Hypertext Transfer Protocol (HTTP) — although it’s technically considered an application-layer protocol per the TCP/IP model.
However, HTTP includes presentation layer services within it. HTTP works when the requesting device forwards user requests passed to the web browser onto a web server elsewhere in the network.
It receives a return message from the web server that includes a multipurpose internet mail extensions (MIME) header. The MIME header indicates the type of file – text, video, or audio – that has been received so that an appropriate player utility can be used to present the file to the user.
In short, the presentation layer
Makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there, in a closed network.
- ensures proper formatting and delivery to and from the application layer;
- performs data encryption; and
- manages serialization of data objects.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
What is OSI Model? – Layers of OSI Model
OSI stands for Open Systems Interconnection , where open stands to say non-proprietary. It is a 7-layer architecture with each layer having specific functionality to perform. All these 7 layers work collaboratively to transmit the data from one person to another across the globe. The OSI reference model was developed by ISO – ‘International Organization for Standardization ‘, in the year 1984.
The OSI model provides a theoretical foundation for understanding network communication . However, it is usually not directly implemented in its entirety in real-world networking hardware or software . Instead, specific protocols and technologies are often designed based on the principles outlined in the OSI model to facilitate efficient data transmission and networking operations
What is OSI Model?
- What are the 7 layers of the OSI Model?
Physical Layer – Layer 1
Data link layer (dll) – layer 2, network layer – layer 3, transport layer – layer 4, session layer – layer 5, presentation layer – layer 6, application layer – layer 7.
- What is the Flow of Data in OSI Model?
Advantages of OSI Model
- OSI Model in a Nutshell
OSI vs TCP/IP Model
The OSI model, created in 1984 by ISO , is a reference framework that explains the process of transmitting data between computers. It is divided into seven layers that work together to carry out specialised network functions , allowing for a more systematic approach to networking.

For those preparing for competitive exams like GATE, a strong understanding of networking concepts, including the OSI model, is crucial. To deepen your knowledge in this area and other key computer science topics, consider enrolling in the GATE CS Self-Paced course . This course offers comprehensive coverage of the syllabus, helping you build a solid foundation for your exam preparation.
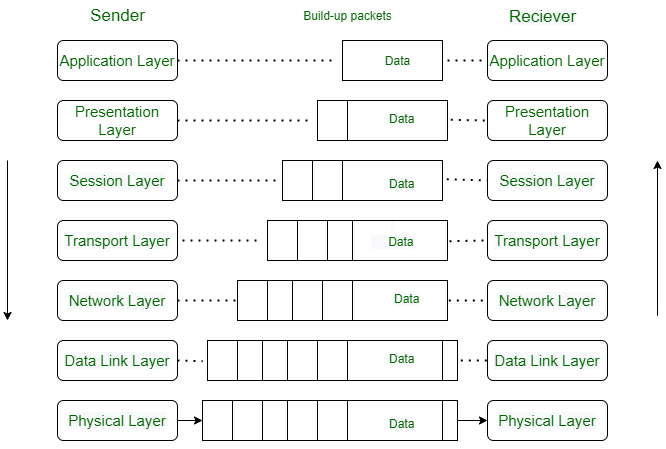
Data Flow In OSI Model
When we transfer information from one device to another, it travels through 7 layers of OSI model. First data travels down through 7 layers from the sender’s end and then climbs back 7 layers on the receiver’s end.
Data flows through the OSI model in a step-by-step process:
- Application Layer: Applications create the data.
- Presentation Layer: Data is formatted and encrypted.
- Session Layer: Connections are established and managed.
- Transport Layer: Data is broken into segments for reliable delivery.
- Network Layer : Segments are packaged into packets and routed.
- Data Link Layer: Packets are framed and sent to the next device.
- Physical Layer: Frames are converted into bits and transmitted physically.
Each layer adds specific information to ensure the data reaches its destination correctly, and these steps are reversed upon arrival.
Let’s look at it with an Example:
Luffy sends an e-mail to his friend Zoro.
Step 1: Luffy interacts with e-mail application like Gmail , outlook , etc. Writes his email to send. (This happens in Layer 7: Application layer )
Step 2: Mail application prepares for data transmission like encrypting data and formatting it for transmission. (This happens in Layer 6: Presentation Layer )
Step 3: There is a connection established between the sender and receiver on the internet. (This happens in Layer 5: Session Layer )
Step 4: Email data is broken into smaller segments. It adds sequence number and error-checking information to maintain the reliability of the information. (This happens in Layer 4: Transport Layer )
Step 5: Addressing of packets is done in order to find the best route for transfer. (This happens in Layer 3: Network Layer )
Step 6: Data packets are encapsulated into frames, then MAC address is added for local devices and then it checks for error using error detection. (This happens in Layer 2: Data Link Layer )
Step 7: Lastly Frames are transmitted in the form of electrical/ optical signals over a physical network medium like ethernet cable or WiFi.
After the email reaches the receiver i.e. Zoro, the process will reverse and decrypt the e-mail content. At last, the email will be shown on Zoro’s email client.
What Are The 7 Layers of The OSI Model?
The OSI model consists of seven abstraction layers arranged in a top-down order:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
The lowest layer of the OSI reference model is the physical layer. It is responsible for the actual physical connection between the devices. The physical layer contains information in the form of bits. It is responsible for transmitting individual bits from one node to the next. When receiving data, this layer will get the signal received and convert it into 0s and 1s and send them to the Data Link layer, which will put the frame back together.

Functions of the Physical Layer
- Bit Synchronization: The physical layer provides the synchronization of the bits by providing a clock. This clock controls both sender and receiver thus providing synchronization at the bit level.
- Bit Rate Control: The Physical layer also defines the transmission rate i.e. the number of bits sent per second.
- Physical Topologies: Physical layer specifies how the different, devices/nodes are arranged in a network i.e. bus, star, or mesh topology.
- Transmission Mode: Physical layer also defines how the data flows between the two connected devices. The various transmission modes possible are Simplex, half-duplex and full-duplex.
Note: Hub, Repeater, Modem, and Cables are Physical Layer devices. Network Layer, Data Link Layer, and Physical Layer are also known as Lower Layers or Hardware Layers .
The data link layer is responsible for the node-to-node delivery of the message. The main function of this layer is to make sure data transfer is error-free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of the DLL to transmit it to the Host using its MAC address . The Data Link Layer is divided into two sublayers:
- Logical Link Control (LLC)
- Media Access Control (MAC)
The packet received from the Network layer is further divided into frames depending on the frame size of the NIC(Network Interface Card). DLL also encapsulates Sender and Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.
Functions of the Data Link Layer
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit a set of bits that are meaningful to the receiver. This can be accomplished by attaching special bit patterns to the beginning and end of the frame.
- Physical Addressing: After creating frames, the Data link layer adds physical addresses ( MAC addresses ) of the sender and/or receiver in the header of each frame.
- Error Control: The data link layer provides the mechanism of error control in which it detects and retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both sides else the data may get corrupted thus, flow control coordinates the amount of data that can be sent before receiving an acknowledgment.
- Access Control: When a single communication channel is shared by multiple devices, the MAC sub-layer of the data link layer helps to determine which device has control over the channel at a given time.

Note: Packet in the Data Link layer is referred to as Frame. Data Link layer is handled by the NIC (Network Interface Card) and device drivers of host machines. Switch & Bridge are Data Link Layer devices.
The network layer works for the transmission of data from one host to the other located in different networks. It also takes care of packet routing i.e. selection of the shortest path to transmit the packet, from the number of routes available. The sender & receiver’s IP address es are placed in the header by the network layer.
Functions of the Network Layer
- Routing: The network layer protocols determine which route is suitable from source to destination. This function of the network layer is known as routing.
- Logical Addressing: To identify each device inter-network uniquely, the network layer defines an addressing scheme. The sender & receiver’s IP addresses are placed in the header by the network layer. Such an address distinguishes each device uniquely and universally.
Note: Segment in the Network layer is referred to as Packet . Network layer is implemented by networking devices such as routers and switches.
The transport layer provides services to the application layer and takes services from the network layer. The data in the transport layer is referred to as Segments . It is responsible for the end-to-end delivery of the complete message. The transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found.
At the sender’s side: The transport layer receives the formatted data from the upper layers, performs Segmentation , and also implements Flow and error control to ensure proper data transmission. It also adds Source and Destination port number s in its header and forwards the segmented data to the Network Layer.
Note: The sender needs to know the port number associated with the receiver’s application. Generally, this destination port number is configured, either by default or manually. For example, when a web application requests a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default ports assigned.
At the receiver’s side: Transport Layer reads the port number from its header and forwards the Data which it has received to the respective application. It also performs sequencing and reassembling of the segmented data.
Functions of the Transport Layer
- Segmentation and Reassembly: This layer accepts the message from the (session) layer, and breaks the message into smaller units. Each of the segments produced has a header associated with it. The transport layer at the destination station reassembles the message.
- Service Point Addressing: To deliver the message to the correct process, the transport layer header includes a type of address called service point address or port address. Thus by specifying this address, the transport layer makes sure that the message is delivered to the correct process.
Services Provided by Transport Layer
- Connection-Oriented Service
- Connectionless Service
1. Connection-Oriented Service: It is a three-phase process that includes:
- Connection Establishment
- Data Transfer
- Termination/disconnection
In this type of transmission, the receiving device sends an acknowledgment, back to the source after a packet or group of packets is received. This type of transmission is reliable and secure.
2. Connectionless service: It is a one-phase process and includes Data Transfer. In this type of transmission, the receiver does not acknowledge receipt of a packet. This approach allows for much faster communication between devices. Connection-oriented service is more reliable than connectionless Service.
Note: Data in the Transport Layer is called Segments . Transport layer is operated by the Operating System. It is a part of the OS and communicates with the Application Layer by making system calls. The transport layer is called as Heart of the OSI model. Device or Protocol Use : TCP, UDP NetBIOS, PPTP
This layer is responsible for the establishment of connection, maintenance of sessions, and authentication, and also ensures security.
Functions of the Session Layer
- Session Establishment, Maintenance, and Termination: The layer allows the two processes to establish, use, and terminate a connection.
- Synchronization: This layer allows a process to add checkpoints that are considered synchronization points in the data. These synchronization points help to identify the error so that the data is re-synchronized properly, and ends of the messages are not cut prematurely and data loss is avoided.
- Dialog Controller: The session layer allows two systems to start communication with each other in half-duplex or full-duplex.
Note: All the below 3 layers(including Session Layer) are integrated as a single layer in the TCP/IP model as the “Application Layer”. Implementation of these 3 layers is done by the network application itself. These are also known as Upper Layers or Software Layers. Device or Protocol Use : NetBIOS, PPTP.
Let us consider a scenario where a user wants to send a message through some Messenger application running in their browser. The “ Messenger ” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, optionally encrypted (if the data is sensitive), and converted into bits (0’s and 1’s) so that it can be transmitted.

Communication in Session Layer
The presentation layer is also called the Translation layer . The data from the application layer is extracted here and manipulated as per the required format to transmit over the network.
Functions of the Presentation Layer
- Translation: For example, ASCII to EBCDIC .
- Encryption/ Decryption: Data encryption translates the data into another form or code. The encrypted data is known as the ciphertext and the decrypted data is known as plain text. A key value is used for encrypting as well as decrypting data.
- Compression: Reduces the number of bits that need to be transmitted on the network.
Note: Device or Protocol Use: JPEG, MPEG, GIF.
At the very top of the OSI Reference Model stack of layers, we find the Application layer which is implemented by the network applications. These applications produce the data to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user.
Example : Application – Browsers, Skype Messenger, etc.
Note: The application Layer is also called Desktop Layer. Device or Protocol Use : SMTP .
Functions of the Application Layer
The main functions of the application layer are given below.
- Network Virtual Terminal(NVT): It allows a user to log on to a remote host.
- File Transfer Access and Management(FTAM): This application allows a user to access files in a remote host, retrieve files in a remote host, and manage or control files from a remote computer.
- Mail Services: Provide email service.
- Directory Services: This application provides distributed database sources and access for global information about various objects and services.
Note: The OSI model acts as a reference model and is not implemented on the Internet because of its late invention. The current model being used is the TCP/IP model.
OSI Model – Layer Architecture
|
|
|
|
|
|
|---|---|---|---|---|
| 7 | Helps in identifying the client and synchronizing communication. | Message | ||
| 6 | Data from the application layer is extracted and manipulated in the required format for transmission. | Message | , , | |
| 5 | Establishes Connection, Maintenance, Ensures Authentication and Ensures security. | Message (or encrypted message) | ||
| 4 | Take Service from Network Layer and provide it to the Application Layer. | Segment | ||
| 3 | Transmission of data from one host to another, located in different networks. | Packet | ||
| 2 | Node to Node Delivery of Message. | Frame | , | |
| 1 | Establishing Physical Connections between Devices. | Bits | , , , Cables |
TCP/IP protocol ( Transfer Control Protocol/Internet Protocol ) was created by U.S. Department of Defense’s Advanced Research Projects Agency (ARPA) in 1970s.
Some key differences between the OSI model and the TCP/IP Model are:
- TCP/IP model consists of 4 layers but OSI model has 7 layers. Layers 5,6,7 of the OSI model are combined into the Application Layer of TCP/IP model and OSI layers 1 and 2 are combined into Network Access Layers of TCP/IP protocol.
- The TCP/IP model is older than the OSI model, hence it is a foundational protocol that defines how should data be transferred online.
- Compared to the OSI model, the TCP/IP model has less strict layer boundaries.
- All layers of the TCP/IP model are needed for data transmission but in the OSI model, some applications can skip certain layers. Only layers 1,2 and 3 of the OSI model are necessary for data transmission.

OSI vs TCP/IP
Why Does The OSI Model Matter?
Even though the modern Internet doesn’t strictly use the OSI Model (it uses a simpler Internet protocol suite), the OSI Model is still very helpful for solving network problems. Whether it’s one person having trouble getting their laptop online, or a website being down for thousands of users, the OSI Model helps to identify the problem. If you can narrow down the issue to one specific layer of the model, you can avoid a lot of unnecessary work.
Imperva Application Security
Imperva security solutions protect your applications at different levels of the OSI model. They use DDoS mitigation to secure the network layer and provide web application firewall (WAF), bot management, and API security to protect the application layer.
To secure applications and networks across the OSI stack, Imperva offers multi-layered protection to ensure websites and applications are always available, accessible, and safe. The Imperva application security solution includes:
- DDoS Mitigation: Protects the network layer from Distributed Denial of Service attacks.
- Web Application Firewall (WAF) : Shields the application layer from threats.
- Bot Management: Prevents malicious bots from affecting the application.
- API Security: Secures APIs from various vulnerabilities and attacks.
The OSI Model defines the communication of a computing system into 7 different layers. Its advantages include:
- It divides network communication into 7 layers which makes it easier to understand and troubleshoot.
- It standardizes network communications, as each layer has fixed functions and protocols.
- Diagnosing network problems is easier with the OSI model .
- It is easier to improve with advancements as each layer can get updates separately.
Disadvantages of OSI Model
- Complexity: The OSI Model has seven layers, which can be complicated and hard to understand for beginners.
- Not Practical: In real-life networking, most systems use a simpler model called the Internet protocol suite (TCP/IP), so the OSI Model isn’t always directly applicable.
- Slow Adoption: When it was introduced, the OSI Model was not quickly adopted by the industry, which preferred the simpler and already-established TCP/IP model.
- Overhead: Each layer in the OSI Model adds its own set of rules and operations, which can make the process more time-consuming and less efficient.
- Theoretical: The OSI Model is more of a theoretical framework, meaning it’s great for understanding concepts but not always practical for implementation.
In conclusion, the OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer has specific responsibilities and interacts with the layers directly above and below it, ensuring seamless communication and data exchange across diverse network environments. Understanding the OSI model helps in troubleshooting network issues, designing robust network architectures, and facilitating interoperability between different networking products and technologies.
Frequently Asked Questions on OSI Model – FAQs
Is osi layer still used.
Yes, the OSI model is still used by networking professionals to understand data abstraction paths and processes better.
What is the highest layer of the OSI model?
Layer 7 or Application layer is highest layer of OSI model.
What is layer 8?
Layer 8 doesn’t actually exist in the OSI model but is often jokingly used to refer to the end user. For example: a layer 8 error would be a user error.
Please Login to comment...
Similar reads.
- 105 Funny Things to Do to Make Someone Laugh
- Best PS5 SSDs in 2024: Top Picks for Expanding Your Storage
- Best Nintendo Switch Controllers in 2024
- Xbox Game Pass Ultimate: Features, Benefits, and Pricing in 2024
- #geekstreak2024 – 21 Days POTD Challenge Powered By Deutsche Bank
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

- Data Structure
- Coding Problems
- C Interview Programs
- C++ Aptitude
- Java Aptitude
- C# Aptitude
- PHP Aptitude
- Linux Aptitude
- DBMS Aptitude
- Networking Aptitude
- AI Aptitude
- MIS Executive
- Web Technologie MCQs
- CS Subjects MCQs
- Databases MCQs
- Programming MCQs
- Testing Software MCQs
- Digital Mktg Subjects MCQs
- Cloud Computing S/W MCQs
- Engineering Subjects MCQs
- Commerce MCQs
- More MCQs...
- Machine Learning/AI
- Operating System
- Computer Network
- Software Engineering
- Discrete Mathematics
- Digital Electronics
- Data Mining
- Embedded Systems
- Cryptography
- CS Fundamental
- More Tutorials...
- Tech Articles
- Code Examples
- Programmer's Calculator
- XML Sitemap Generator
- Tools & Generators

Computer Network Tutorial
- Computer Network - Home
- Computer Network - Overview
- Computer Network - Applications
- Computer Network - TCP/IP
- Computer Network - OSI Model
- Computer Network - Transport, Network, & Application Layers
- Computer Network - Network Protocols & Network Software
- Computer Network - TopologiesTypes
- Computer Network - Hub
- Computer Network - Routing
- Computer Network - Routers
- Computer Network - Dynamic Routing Protocols
- Computer Network - Router
- Computer Network - Populating a Routing Table
- Computer Network - Switches
- Computer Network - Layer 2 Switching
- Computer Network - Configure Cisco Switch
- Computer Network - ICMP
- Computer Network - ICMP Messages
- Computer Network - Addressing
- Computer Network - Classless Addressing
- Computer Network - IPV4 Addressing
- Computer Network - IPV6 Addressing
- Computer Network - Logical Addressing, Notations
- Computer Network - Classful & Classless Addressing
- Computer Network - Subnetting & Supernetting
- Computer Network - Network Address Translation
- Computer Network - FLSM & VLSM
- Computer Network - Line Configuration
- Transmission Computer Network - Modes
- Computer Network - Data Link Layer
- Computer Network - Physical Layer
- Computer Network - Network Layer
- Computer Network - Session Layer
- Computer Network - Transport Layer
- Computer Network - Application Layer
- Computer Network - Presentation Layer
- Computer Network - Coaxial Cable
- Computer Network - Optical Fiber
- Computer Network - Unguided Transmission Media
- Computer Network - Virtual LAN (VLAN)
- Computer Network - VSAN
- Computer Network - Multiple Access Protocol
- Computer Network - Random Access methods
- Computer Network - Aloha Network
- Computer Network - CSMA
- Computer Network - FDMA & TDMA
- Computer Network - CDMA
- Computer Network - Ethernet Technology
- Computer Network - Types of Network Topology
- Computer Network - Data Transmission
- Computer Network - Switching Techniques
- Computer Network - Transmission Impairment
- Computer Network - Synchronous & Asynchronous Transmission
- Computer Network - Intent-Based Networking
- Computer Network - Software-Defined Networking
- Computer Network - Wireless Personal Area Network
- Computer Network - Wireless Wide Area Network
- Computer Network - P2P File Sharing
- Computer Network - Packet Switching
- Computer Network - PGP - Authentication & Confidentiality
- Computer Network - PGP - Encryption & Compression
- Computer Network - Phishing Attacks
- Computer Network - ICMP Ping
- Computer Network - Pipelining in Packet Switching
- Computer Network - Plaintext Vs. Cleartext Encryption
- Computer Network - Platform as a Service (PaaS)
- Computer Network - GPRS Architecture
- Computer Network - Identify & Prevent Phishing & Pharming
- Computer Network - Change MAC Address
- Computer Network - Network Administrator Vs. Network Engineer
Difference B/W Articles
- Computer Network - Phishing & Pharming
- Computer Network - Ping Vs. Traceroute
- Computer Network - Network Vs. System Administrator
- Computer Network - Network & Application Layer Protocols
- Computer Network - Network Security Vs. Network Administration
- Computer Network - Network Vs. Internet
- Computer Network - PDH Vs. SDH
- Computer Network - PCI Vs. PCI express
- Computer Network - PCI-E Vs. PCI-X
- Computer Network - OT Vs. IT Networks
Computer Network Practice
- Computer Network - MCQs
- Computer Network - Aptitude Questions
Advertisement
Home » Computer Network
Presentation Layer: What It Is, Design Issues, Functionalities
Description and Functions of Presentation Layer in the OSI model: In this tutorial, we are going to learn what the Presentation layer is and the Functions of the Presentation Layer in the OSI model in Computer Networking. We will also discuss the Design issues with the Presentation Layer and the working of the Presentation Layer with the help of its diagram. By Monika Jha Last updated : May 05, 2023

What is Presentation Layer?
The Presentation Layer is concerned with the syntax and semantics of the information exchanged between two communicating devices.
- The presentation layer takes care that the data is sent in that way the receiver of the data will understand the information (data) and will be able to use the data.
- Languages that are syntax can be different from the two communicating machines. In this condition, the presentation layer plays the role of translator between them.
- It is possible for two machines to communicate with different data representations, data structures to be exchanged can be defined in an abstract way.
- These abstract data structures will be managed by the presentation layer and this layer allows higher-level data structures (For example banking records), to be defined and exchanged.
This figure shows the relationship of the presentation layer to the session layer and application layer.

Design Issues with Presentation Layer
The following are the design issues with presentation layer:
- To manage and maintain the Syntax and Semantics of the information transmitted.
- Encoding data in a standard agreed-upon way just like a string, double, date, etc.
- It Performs Standard Encoding scheme on the wire.
Functionalities of the Presentation Layer
Specific functionalities of the presentation layer are as follows:
1. Translation
- The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams because different computers use different encoding schemes.
- The Presentation layer is responsible for compatibility between these encoding methods.
- The Presentation layer at the sender's side changes the information from its sender dependent format.
- The Presentation layer at the receiving machine changes the common format into its receivers dependent format.
Example: Convert ASCII code to EBCDIC code.
2. Encryption
- The system must be able to assure privacy regarding the message or information as it also carries sensitive information.
- Encryption means that the sender transforms the original information or message to another form, this data after encryption is known as the ciphertext and this ciphertext sends the resulting message out over the network.
- Decryption concerned with the transform of the message back to its original form. This decrypted data is known as plain text.
3. Compression
- Data Compression means reduces the number of bits to be transmitted by this reduce the bandwidth of the data.
- Data Compression becomes particularly important in the transmission of multimedia such as audio, video, text, etc.
Related Tutorials
- IPV4 Addressing | Classful and Classless Addressing
- Subnetting and Supernetting in Computer Network
- Network Address Translation (NAT) in Computer Network
- Fixed Length and Variable Length Subnet Mask (FLSM & VLSM)
- Line Configuration in Computer Network
- Transmission Modes in Computer Network
- Data Link Layer: What It Is, Sublayers, Design Issues, Functions
- Physical Layer: What It Is, Design Issues, Functions
- Network Layer: What It Is, Design Issues, Responsibilities
- Session Layer: What It Is, Design Issues, Functionalities
- Transport Layer: What It Is, Design Issues, Functions, and Example
- Optical Fiber (Fiber Optics) in Computer Network
- Unguided Transmission Media in Computer Network
- Virtual LAN (VLAN) in Computer Network
- Virtual Storage Area Networking (VSAN)
Comments and Discussions!
Load comments ↻
- Marketing MCQs
- Blockchain MCQs
- Artificial Intelligence MCQs
- Data Analytics & Visualization MCQs
- Python MCQs
- C++ Programs
- Python Programs
- Java Programs
- D.S. Programs
- Golang Programs
- C# Programs
- JavaScript Examples
- jQuery Examples
- CSS Examples
- C++ Tutorial
- Python Tutorial
- ML/AI Tutorial
- MIS Tutorial
- Software Engineering Tutorial
- Scala Tutorial
- Privacy policy
- Certificates
- Content Writers of the Month
Copyright © 2024 www.includehelp.com. All rights reserved.
Presentation Layer: Protocols, Examples, Services | Functions of Presentation Layer
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts. Now, we will explain about what is presentation layer with its protocols, example, service ; involving with major functions of presentation Layer with ease. At the end of this article, you will completely educate about What is Presentation Layer in OSI Model without any hassle.
What is Presentation Layer?
Presentation layer is capable to handle abstract data structures, and further it helps to defined and exchange of higher-level data structures.
Presentation Layer Tutorial Headlines:
Let’s get started, functions of presentation layer.
Presentation layer performs various functions in the OSI model ; below explain each one –
Protocols of Presentation Layer
Example of presentation layer protocols:.
Here, we will discuss all examples of presentation layer protocols; below explain each one –
Multipurpose Internet Mail Extensions (MIME) : MIME protocol was introduced by Bell Communications in 1991, and it is an internet standard that provides scalable capable of email for attaching of images, sounds and text in a message.
Network News Transfer Protocol (NNTP) : This protocol is used to make connection with Usenet server and transmit all newsgroup articles in between system over internet.
Apple Filing Protocol (AFP ) : AFP protocol is designed by Apple company for sharing all files over the entire network .
NetWare Core Protocol (NCP) : NCP is a Novell client server model protocol that is designed especially for Local Area Network (LAN). It is capable to perform several functions like as file/print-sharing, clock synchronization, remote processing and messaging.
Network Data Representation (NDR) : NDR is an data encoding standard, and it is implement in the Distributed Computing Environment (DCE).
Tox : The Tox protocol is sometimes regarded as part of both the presentation and application layer , and it is used for sending peer-to-peer instant-messaging as well as video calling.
eXternal Data Representation (XDR) : This protocol provides the description and encoding of entire data, and it’s main goal is to transfer data in between dissimilar computer architecture.
Presentation Layer Services
Design issues with presentation layer, faqs (frequently asked questions), what is meant by presentation layer in osi model.
Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model that is the lowest layer, where all application programmer consider data structure and presentation, beyond of simply sending the data into form of datagram otherwise packets in between the hosts.
What protocols are used in the presentation layer?
Can you explain some presentation layer examples, what are the main functions of the presentation layer, what are services of presentation layer in osi.
Presentation layer has a responsibility for formatting, translation, and delivery of the information for getting to process otherwise display .
Now, i hope that you have completely learnt about what is presentation layer with its protocols, example, service ; involving with major functions of presentation Layer with ease. If this post is useful for you, then please share it along with your friends, family members or relatives over social media platforms like as Facebook, Instagram, Linked In, Twitter, and more.
Also Read: Data Link Layer: Protocols, Examples | Functions of Data Link Layer
Related posts.
- Network infrastructure
OSI model (Open Systems Interconnection)
- Andrew Froehlich, West Gate Networks
- Linda Rosencrance
- Kara Gattine, Director of Editorial Operations
What is OSI model (Open Systems Interconnection)?
OSI (Open Systems Interconnection) is a reference model for how applications communicate over a network. This model focuses on providing a visual design of how each communications layer is built on top of the other, starting with the physical cabling, all the way to the application that's trying to communicate with other devices on a network.
A reference model is a conceptual framework for understanding relationships. The purpose of the OSI reference model is to guide technology vendors and developers so the digital communications products and software programs they create can interoperate and to promote a clear framework that describes the functions of a networking or telecommunications system that's in use.
Most vendors involved in telecommunications try to describe their products and services in relation to the OSI model. This helps them differentiate among the various transport protocols, addressing schemes and communications packaging methods. And, although it's useful for guiding discussion and evaluation, the OSI model is theoretical in nature and should be used only as a general guide. That's because few network products or standard tools keep related functions together in well-defined layers, as is the case in the OSI model. The Transmission Control Protocol/Internet Protocol ( TCP/IP ) suite, for example, is the most widely used network protocol, but even it doesn't map cleanly to the OSI model.
History of the OSI model
In the 1970s, technology researchers began examining how computer systems could best communicate with each other. Over the next few years, several competing models were created and published to the community. However, it wasn't until 1984 when the International Organization for Standardization (ISO) took the best parts of competing networking reference models to propose OSI as a way to finally create a framework that technology companies around the world could use as the basis of their networking technologies .
From ISO's perspective, the easiest way to create a conceptual model was to organize the models into different abstraction layers required to organize and send data between computing systems. Looking inside each abstracted layer to see the details shows one part of this network communication process. Each layer can be thought of as a separate communication module or piece of the puzzle. But, to actually accomplish the goal of sending data from one device to another, each module must work together.
How the OSI model works
Information technology (IT) networking professionals use OSI to model or conceptualize how data is sent or received over a network. Understanding this is a foundational part of most IT networking certifications, including the Cisco Certified Network Associate (CCNA) and CompTIA Network+ certification programs. As mentioned, the model is designed to break down data transmission standards, processes and protocols over a series of seven layers, each of which is responsible for performing specific tasks concerning sending and receiving data.
The main concept of OSI is that the process of communication between two endpoints in a network can be divided into seven distinct groups of related functions, or layers. Each communicating user or program is on a device that can provide those seven layers of function.
In this architecture, each layer serves the layer above it and, in turn, is served by the layer below it. So, in a given message between users, there will be a flow of data down through the layers in the source computer, across the network and then up through the layers in the receiving computer. Only the application layer at the top of the stack doesn't provide services to a higher-level layer.
The seven layers of function are provided by a combination of applications, operating systems (OSes), network card device drivers, networking hardware and protocols that enable a system to transmit a signal over a network through various physical mediums, including twisted-pair copper, fiber optics, Wi-Fi or Long-Term Evolution (LTE) with 5G .
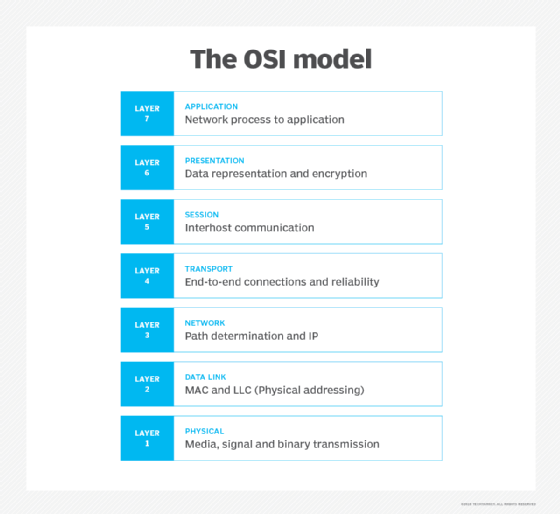
7 layers of the OSI model
What is the function of each layer of the OSI model? The seven Open Systems Interconnection layers are the following.
Layer 7. The application layer
The application layer enables the user -- human or software -- to interact with the application or network whenever the user elects to read messages, transfer files or perform other network-related tasks. Web browsers and other internet-connected apps, such as Outlook and Skype, use Layer 7 application protocols.
Layer 6. The presentation layer
The presentation layer translates or formats data for the application layer based on the semantics or syntax the application accepts. This layer also handles the encryption and decryption that the application layer requires.
Layer 5. The session layer
The session layer sets up, coordinates and terminates conversations between applications. Its services include authentication and reconnection after an interruption. This layer determines how long a system will wait for another application to respond. Examples of session layer protocols include X.225 and Zone Information Protocol (ZIP).
Layer 4. The transport layer
The transport layer is responsible for transferring data across a network and provides error-checking mechanisms and data flow controls. It determines how much data to send, where it gets sent and at what rate. TCP within the TCP/IP suite is the best-known example of the transport layer. This is where the communications select TCP port numbers to categorize and organize data transmissions across a network.
Layer 3. The network layer
The primary function of the network layer is to move data into and through other networks. Network layer protocols accomplish this by packaging data with correct network address information, selecting the appropriate network routes and forwarding the packaged data up the stack to the transport layer. From a TCP/IP perspective, this is where IP addresses are applied for routing purposes.
Layer 2. The data-link layer
The data-link , or protocol layer, in a program handles moving data into and out of a physical link in a network. This layer handles problems that occur as a result of bit transmission errors. It ensures that the pace of the data flow doesn't overwhelm the sending and receiving devices. This layer also permits the transmission of data to Layer 3, the network layer, where it's addressed and routed.
The data-link layer can be further divided into two sublayers. The higher layer, which is called logical link control (LLC), is responsible for multiplexing, flow control, acknowledgement and notifying upper layers if transmit/receive (TX/RX) errors occur.
The media access control sublayer is responsible for tracking data frames using MAC addresses of the sending and receiving hardware. It's also responsible for organizing each frame, marking the starting and ending bits and organizing timing regarding when each frame can be sent along the physical layer medium.
Layer 1. The physical layer
The physical layer transports data using electrical, mechanical or procedural interfaces. This layer is responsible for sending computer bits from one device to another along the network. It determines how physical connections to the network are set up and how bits are represented into predictable signals as they're transmitted either electrically, optically or via radio waves.
Cross-layer functions
Cross-layer functions, or services that may affect more than one layer, include the following:
- security service telecommunication as defined by the International Telecommunication Union Standardization Sector (ITU-T) X.800 recommendation;
- management functions that enable the configuration, instantiation, monitoring and terminating of the communications of two or more entities;
- Multiprotocol Label Switching ( MPLS ), which operates at an OSI model layer that lies between the Layer 2 data-link layer and the Layer 3 network layer -- MPLS can carry a variety of traffic, including Ethernet frames and IP packets;
- Address Resolution Protocol (ARP) translates IPv4 addresses (OSI Layer 3) into Ethernet MAC addresses (OSI Layer 2); and
- domain name system (DNS), which is an application layer service that's used to look up the IP address of a domain name.
Pros and cons of the OSI model
The OSI model has a number of advantages, including the following:
- It's considered a standard model in computer networking.
- The model supports connectionless , as well as connection-oriented, services. Users can take advantage of connectionless services when they need faster data transmissions over the internet and the connection-oriented model when they're looking for reliability.
- It has the flexibility to adapt to many protocols.
- The model is more adaptable and secure than having all services bundled in one layer.
The disadvantages of the OSI model include the following:
- It doesn't define any particular protocol.
- The session layer, which is used for session management, and the presentation layer, which deals with user interaction, aren't as useful as other layers in the OSI model.
- Some services are duplicated at various layers, such as the transport and data-link layers.
- Layers can't work in parallel; each layer must wait to receive data from the previous layer.
OSI model vs. TCP/IP model
The OSI reference model describes the functions of a telecommunication or networking system, while TCP/IP is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP and OSI are the most broadly used networking models for communication.
The OSI and TCP/IP models have similarities and differences. The main similarity is in their construction, as both use layers, although the OSI model consists of seven layers, while TCP/IP consists of just four layers.
Another similarity is that the upper layer for each model is the application layer, which performs the same tasks in each model but may vary according to the information each receives.
The functions performed in each model are also similar because each uses a network and transport layer to operate. The OSI and TCP/IP model are mostly used to transmit data packets, although they each use different means and paths to reach their destinations.
Additional similarities between the OSI and TCP/IP models include the following:
- Both are logical models.
- Both define standards for networking.
- They each divide the network communication process in layers.
- Both provide frameworks for creating and implementing networking standards and devices.
- They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
- Both divide complex functions into simpler components.
Differences between the OSI and TCP/IP models include the following:
- OSI uses three layers -- application, presentation and session -- to define the functionality of upper layers, while TCP/IP uses only the application layer.
- OSI uses two separate layers -- physical and data-link -- to define the functionality of the bottom layers, while TCP/IP uses only the link layer.
- OSI uses the network layer to define the routing standards and protocols, while TCP/IP uses the internet layer.
Next: Explore 12 common network protocols all network engineers should know here .
Continue Reading About OSI model (Open Systems Interconnection)
- What is the difference between TCP/IP model vs. OSI model?
- Future of networking technology relies on 5G, edge computing
- 7 TCP/IP vulnerabilities and how to prevent them
- Edge computing and 5G bring the edge to remote workers
- SANs Institute OSI model overview
Related Terms
Dig deeper on network infrastructure.

An explanation of TCP/IP

Transmission Control Protocol (TCP)

encapsulation (object-orientated programming)

Microsoft 365 Copilot, an AI assistant, offers several promising features. Find out how to configure Copilot with Teams workflows...
With its AI capabilities, Microsoft Copilot provides several enhancements to Microsoft Teams functionality, including meeting ...
Organizations have ramped up their use of communications platform as a service and APIs to expand communication channels between ...
Auditing is a crucial part of mobile device security, but IT admins must ensure their approach is thorough and consistent. Learn ...
With the right software, almost any mobile device can be a payment terminal. Learn about the mobile point-of-sale options beyond ...
To keep corporate and user data safe, IT must continuously ensure mobile app security. Mobile application security audits are a ...
Rocky Linux and AlmaLinux are new distributions created after Red Hat announced the discontinuation of CentOS. These ...
The Broadcom CEO says public cloud migration trauma can be cured by private cloud services like those from VMware, but VMware ...
New capabilities for VMware VCF can import and manage existing VMware services through a single console interface for a private ...
Popular pricing models for managed service providers include monitoring only, per device, per user, all-you-can-eat or ...
Global IT consultancies take a multilayered approach to GenAI training by developing in-house programs, partnering with tech ...
IT service providers are upskilling a large portion of their workforces on the emerging technology. The campaign seeks to boost ...
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
OSI model - What's the presentation and session layer for?
So I feel I pretty well understand the application layer, and everything below (and including) the transport layer.
The session and presentation layers, though, I don't fully understand. I've read the simplistic descriptions in Wikipedia, but it doesn't have an example of why separating out those layers is useful.
- What is the session layer? What does it do, and under what circumstances is it better to have a session layer than simply talk to the transport with your app?
- What is the presentation layer? (same questions as above)
7 Answers 7
The session layer is meant to store states between two connections, like what we use cookies for when working with web programming.
The presentation layer is meant to convert between different formats. This was simpler when the only format that was worried about was character encoding, ie ASCII and EBCDIC. When you consider all of the different formats that we have today(Quicktime, Flash, Pdf) centralizing this layer is out of the question.
TCP/IP doesn't make any allocation to these layers, since they are really out of the scope of a networking protocol. It's up to the applications that take advantage of the stack to implement these.
The reasons there aren't any examples on wikipedia is that there aren't a whole lot of examples of the OSI network model, period.
OSI has once again created a standard nobody uses, so nobody really know how one should use it.
Layers 5-6 are not commonly used in today's web applications, so you don't hear much about them. The TCP/IP stack is slightly different than a pure OSI Model.
One of the reasons TCP/IP is used today instead of OSI is it was too bloated and theoretical, the session and presentation layer aren't really needed as separate layers as it turned out.
I think that presentation layer protocols define the format of data. This means protocols like XML or ASN.1. You could argue that video/audio codecs are part of the presentation layer Although this is probably heading towards the application layer.
I can't help you with the session layer. That has always baffled me.
To be honest, there are very vague boundaries in everything above the transport layer. This is because it is usually handled by a single software application. Also, these layers are not directly associated with transporting data from A to B. Layers 4 and below each have a very specific purpose in moving the data e.g. switching, routing, ensuring data integrity etc. This makes it easier to distinguish between these layers.
Presentation Layer The Presentation Layer represents the area that is independent of data representation at the application layer - in general, it represents the preparation or translation of application format to network format, or from network formatting to application format. In other words, the layer “presents” data for the application or the network. A good example of this is encryption and decryption of data for secure transmission - this happens at Layer 6.
Session Layer When two devices, computers or servers need to “speak” with one another, a session needs to be created, and this is done at the Session Layer. Functions at this layer involve setup, coordination (how long should a system wait for a response, for example) and termination between the applications at each end of the session.
For the presentation layer :because most of communication done between heterogeneous systems (Operating Systems,programing langages,cpu architectures)we need to use a unified idepedent specification .like ANS1 ans BRE.
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged networking model stack osi or ask your own question .
- The Overflow Blog
- The evolution of full stack engineers
- One of the best ways to get value for AI coding tools: generating tests
- Featured on Meta
- Bringing clarity to status tag usage on meta sites
- Join Stack Overflow’s CEO and me for the first Stack IRL Community Event in...
- Feedback requested: How do you use tag hover descriptions for curating and do...
- Staging Ground Reviewer Motivation
- What does a new user need in a homepage experience on Stack Overflow?
Hot Network Questions
- What are the intermediate semisimple groups of type A?
- Why were there so many OSes that had the name "DOS" in them?
- Expansion in Latex3 when transforming an input and forwarding it to another function
- Why do "modern" languages not provide argv and exit code in main?
- Did Queen (or Freddie Mercury) really not like Star Wars?
- How do I go about writing a tragic ending in a story while making it overall satisfying to the reader?
- Practice test paper answers all seem incorrect, but provider insists they are ... what am i missing?
- When should I put a biasing resistor - op-amps
- Guesstimate a multiple choice exam
- Inspector tells me that the electrician should have removed green screw from the panel
- Subtle racism in the lab: how to respond
- What is the shortest viable hmac for non-critical applications?
- Is this a misstatement of Euclid in Halmos' Naive Set Theory book?
- Does the Supremacy Clause allow states to retain abortion rights enshrined in each states' constitution?
- Text processing: Filter & re-publish HTML table
- How can I get the bounding box of a path (drawn with hobby)?
- Can the Fourier transform of a test function vanish on an interval?
- Why would the GPL be viral, while EUPL isn't, according to the EUPL authors?
- Best memory / storage solution for high read / write throughput application(s)?
- Wrong explanation for why "electron can't exist in the nucleus"?
- Increasing vs non decreasing
- What sci-fi show was Ernie watching in the show My Three Sons?
- Was using an older version of a legal card from a nonlegal set ever not legal?
- Please help me identify my Dad's bike collection (80's-2000's)

Three-tier architecture is a well-established software application architecture that organizes applications into three logical and physical computing tiers: the presentation tier, or user interface; the application tier, where data is processed; and the data tier, where application data is stored and managed.
The chief benefit of three-tier architecture is that because each tier runs on its own infrastructure, each tier can be developed simultaneously by a separate development team. And can be updated or scaled as needed without impacting the other tiers.
For decades three-tier architecture was the prevailing architecture for client-server applications. Today, most three-tier applications are targets for modernization that uses cloud-native technologies such as containers and microservices and for migration to the cloud.
Connect and integrate your systems to prepare your infrastructure for AI.
Register for the guide on app modernization
Presentation tier
The presentation tier is the user interface and communication layer of the application, where the end user interacts with the application. Its main purpose is to display information to and collect information from the user. This top-level tier can run on a web browser, as desktop application, or a graphical user interface (GUI), for example. Web presentation tiers are developed by using HTML, CSS, and JavaScript. Desktop applications can be written in various languages depending on the platform.
Application tier
The application tier, also known as the logic tier or middle tier, is the heart of the application. In this tier, information that is collected in the presentation tier is processed - sometimes against other information in the data tier - using business logic, a specific set of business rules. The application tier can also add, delete, or modify data in the data tier.
The application tier is typically developed by using Python, Java, Perl, PHP or Ruby, and communicates with the data tier by using API calls.
The data tier, sometimes called database tier, data access tier or back-end, is where the information that is processed by the application is stored and managed. This can be a relational database management system such as PostgreSQL , MySQL, MariaDB, Oracle, Db2, Informix or Microsoft SQL Server, or in a NoSQL Database server such as Cassandra, CouchDB , or MongoDB .
In a three-tier application, all communication goes through the application tier. The presentation tier and the data tier cannot communicate directly with one another.
Tier versus layer
In discussions of three-tier architecture, layer is often used interchangeably – and mistakenly – for tier , as in 'presentation layer' or 'business logic layer'.
They aren't the same. A 'layer' refers to a functional division of the software, but a 'tier' refers to a functional division of the software that runs on infrastructure separate from the other divisions. The Contacts app on your phone, for example, is a three - layer application, but a single-tier application, because all three layers run on your phone.
The difference is important because layers can't offer the same benefits as tiers.
Again, the chief benefit of three-tier architecture is its logical and physical separation of functionality. Each tier can run on a separate operating system and server platform - for example, web server, application server, database server - that best fits its functional requirements. And each tier runs on at least one dedicated server hardware or virtual server, so the services of each tier can be customized and optimized without impacting the other tiers.
Other benefits (compared to single- or two-tier architecture) include:
- Faster development : Because each tier can be developed simultaneously by different teams, an organization can bring the application to market faster. And programmers can use the latest and best languages and tools for each tier.
- Improved scalability : Any tier can be scaled independently of the others as needed.
- Improved reliability : An outage in one tier is less likely to impact the availability or performance of the other tiers.
- Improved security : Because the presentation tier and data tier can't communicate directly, a well-designed application tier can function as an internal firewall, preventing SQL injections and other malicious exploits.
In web development, the tiers have different names but perform similar functions:
- The web server is the presentation tier and provides the user interface. This is usually a web page or website, such as an ecommerce site where the user adds products to the shopping cart, adds payment details or creates an account. The content can be static or dynamic, and is developed using HTML, CSS, and JavaScript.
- The application server corresponds to the middle tier, housing the business logic that is used to process user inputs. To continue the ecommerce example, this is the tier that queries the inventory database to return product availability, or adds details to a customer's profile. This layer often developed using Python, Ruby, or PHP and runs a framework such as Django, Rails, Symphony, or ASP.NET.
- The database server is the data or backend tier of a web application. It runs on database management software, such as MySQL, Oracle, DB2, or PostgreSQL.
While three-tier architecture is easily the most widely adopted multitier application architecture, there are others that you might encounter in your work or your research.
Two-tier architecture
Two-tier architecture is the original client-server architecture, consisting of a presentation tier and a data tier; the business logic lives in the presentation tier, the data tier or both. In two-tier architecture the presentation tier - and therefore the end user - has direct access to the data tier, and the business logic is often limited. A simple contact management application, where users can enter and retrieve contact data, is an example of a two-tier application.
N-tier architecture
N-tier architecture - also called or multitier architecture - refers to any application architecture with more than one tier. But applications with more than three layers are rare because extra layers offer few benefits and can make the application slower, harder to manage and more expensive to run. As a result, n-tier architecture and multitier architecture are usually synonyms for three-tier architecture.
Move to cloud faster with IBM Cloud Pak solutions running on Red Hat OpenShift software—integrated, open, containerized solutions certified by IBM®.
Seamlessly modernize your VMware workloads and applications with IBM Cloud.
Modernize, build new apps, reduce costs, and maximize ROI.
IBM Consulting® application modernization services, which are powered by IBM Consulting Cloud Accelerator, offers skills, methods, tools, and initiatives that help determine the right strategy based on your portfolio. To modernize and containerize legacy system applications and accelerate the time-to-value of hybrid cloud environments.
Discover what application modernization is, the common benefits and challenges, and how to get started.
Learn about how relational databases work and how they compare to other data storage options.
Explore cloud native applications and how they drive innovation and speed within your enterprise.
Modernize your legacy three-tier applications on your journey to cloud. Whether you need assistance with strategy, processes, or capabilities—or want full-service attention—IBM can help. Start using containerized middleware that can run in any cloud—all bundled in IBM Cloud Paks.

IMAGES
VIDEO
COMMENTS
The presentation layer resides at Layer 6 of the Open Systems Interconnection (OSI) communications model and ensures that communications that pass through it are in the appropriate form for the recipient application. In other words, the presentation layer presents the data in a readable format from an application layer perspective.
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over ...
The presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. On the sending system it is responsible for conversion to standard, transmittable formats. [7] On the receiving system it is responsible for the translation, formatting, and delivery of ...
The presentation layer follows data programming structure schemes developed for different languages and provides the real-time syntax required for communication between two objects such as layers, systems or networks. The data format should be acceptable by the next layers; otherwise, the presentation layer may not perform correctly.
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
The presentation layer interacts closely with the application layer, which is located directly above it. The presentation layer's main task is to present data in such a way that it can be understood and interpreted from both the system sending the data and the system receiving it. After this has been accomplished, the application layer then determines how the data should be structured and ...
In subject area: Computer Science. The Presentation Layer in the OSI model is defined as the layer that enables interaction between different application layer implementations by translating data formats and languages to facilitate communication. AI generated definition based on: Security for Microsoft Windows System Administrators, 2011.
The Presentation Layer, within the OSI (Open Systems Interconnection) model, is the sixth layer. It focuses on the representation of data, ensuring that information exchanged between applications is formatted appropriately for transmission and receipt across a network. This layer handles tasks such as data translation, encryption, compression ...
Presentation Layer is the Layer 6 of the seven-layer Open Systems Interconnection (OSI) reference model. The presentation layer structures data that is passed down from the application layer into a format suitable for network transmission. This layer is responsible for data encryption, data compression, character set conversion, interpretation ...
Understanding the layers of the Open Systems Interconnect (OSI) model can help users conceptualize data communication over a network. Layer 6 in the OSI model - the presentation layer - translates, compresses, and encrypts data across networks. In this article, we'll explain what the presentation layer is, how it works, and its functions and protocols.
Explore the crucial role of the Presentation Layer in the OSI Model, where data encoding, encryption, and formatting take center stage. Learn how this layer ...
The presentation layer is the sixth layer of the Open Systems Interconnection (OSI), model. In computer networking, the OSI model is a concept that describes the transmission of data from one computer to another. Each layer in the model is a packet of protocols, or procedures that govern data transmission, which allow the layer to execute ...
Presentation Layer - Layer 6 . The presentation layer is also called the Translation layer . The data from the application layer is extracted here and manipulated as per the required format to transmit over the network. ... The Application Layer of OSI (Open System Interconnection) model, is the top layer in this model and takes care of ...
Functionalities of the Presentation Layer. Specific functionalities of the presentation layer are as follows: 1. Translation. The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams ...
What is Presentation Layer? Definition: Presentation layer is 6th layer in the OSI model, and its main objective is to present all messages to upper layer as a standardized format.It is also known as the "Translation layer". This layer takes care of syntax and semantics of messages exchanged in between two communication systems. Presentation layer has responsible that receiver can ...
Presentation layer: The OSI presentation layer is the sixth layer and translates data across the network. Application layer: Topmost seventh layer which stipulates the interface methods for the ...
The seven Open Systems Interconnection layers are the following. Layer 7. The application layer. The application layer enables the user -- human or software -- to interact with the application or network whenever the user elects to read messages, transfer files or perform other network-related tasks.
The separation of concerns is a key principle, making it easier to understand, maintain, and extend the system. Key Concepts: Layers: Presentation Layer: Responsible for handling user input and ...
0. The presentation layer delivers information to the application layer for display. The presentation layer, in some cases, handles data translation to allow use on a particular system. The user interface shows you the data once the presentation layer has done any translations it needs to.
Presentation layer definition. The presentation layer is the sixth layer in the Open System Interconnection (OSI) model. It serves as the data translator for the network — it takes data formats from different sources and presents it to the application layer in an accurate, well-defined, and standardized manner.
The session layer is meant to store states between two connections, like what we use cookies for when working with web programming. The presentation layer is meant to convert between different formats. This was simpler when the only format that was worried about was character encoding, ie ASCII and EBCDIC. When you consider all of the different ...
In a logical multilayer architecture for an information system with an object-oriented design, the following four are the most common: . Presentation layer (a.k.a. UI layer, view layer, presentation tier in multitier architecture); Application layer (a.k.a. service layer [8] [9] or GRASP Controller Layer [10]); Business layer (a.k.a. business logic layer (BLL), domain logic layer)
Presentation tier. The presentation tier is the user interface and communication layer of the application, where the end user interacts with the application. Its main purpose is to display information to and collect information from the user.