This week: the arXiv Accessibility Forum
Help | Advanced Search

Computer Science > Machine Learning
Title: deep networks for system identification: a survey.
Abstract: Deep learning is a topic of considerable current interest. The availability of massive data collections and powerful software resources has led to an impressive amount of results in many application areas that reveal essential but hidden properties of the observations. System identification learns mathematical descriptions of dynamic systems from input-output data and can thus benefit from the advances of deep neural networks to enrich the possible range of models to choose from. For this reason, we provide a survey of deep learning from a system identification perspective. We cover a wide spectrum of topics to enable researchers to understand the methods, providing rigorous practical and theoretical insights into the benefits and challenges of using them. The main aim of the identified model is to predict new data from previous observations. This can be achieved with different deep learning based modelling techniques and we discuss architectures commonly adopted in the literature, like feedforward, convolutional, and recurrent networks. Their parameters have to be estimated from past data trying to optimize the prediction performance. For this purpose, we discuss a specific set of first-order optimization tools that is emerged as efficient. The survey then draws connections to the well-studied area of kernel-based methods. They control the data fit by regularization terms that penalize models not in line with prior assumptions. We illustrate how to cast them in deep architectures to obtain deep kernel-based methods. The success of deep learning also resulted in surprising empirical observations, like the counter-intuitive behaviour of models with many parameters. We discuss the role of overparameterized models, including their connection to kernels, as well as implicit regularization mechanisms which affect generalization, specifically the interesting phenomena of benign overfitting ...
| Subjects: | Machine Learning (cs.LG); Systems and Control (eess.SY) |
| Cite as: | [cs.LG] |
| (or [cs.LG] for this version) | |
| Focus to learn more arXiv-issued DOI via DataCite |
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Plants (Basel)

Plant Disease Detection and Classification by Deep Learning
Muhammad hammad saleem.
1 Department of Mechanical and Electrical Engineering, School of Food and Advanced Technology, Massey University, Auckland 0632, New Zealand; [email protected]
Johan Potgieter
2 Massey Agritech Partnership Research Centre, School of Food and Advanced Technology, Massey University, Palmerston North 4442, New Zealand; [email protected]
Khalid Mahmood Arif
Plant diseases affect the growth of their respective species, therefore their early identification is very important. Many Machine Learning (ML) models have been employed for the detection and classification of plant diseases but, after the advancements in a subset of ML, that is, Deep Learning (DL), this area of research appears to have great potential in terms of increased accuracy. Many developed/modified DL architectures are implemented along with several visualization techniques to detect and classify the symptoms of plant diseases. Moreover, several performance metrics are used for the evaluation of these architectures/techniques. This review provides a comprehensive explanation of DL models used to visualize various plant diseases. In addition, some research gaps are identified from which to obtain greater transparency for detecting diseases in plants, even before their symptoms appear clearly.
1. Introduction
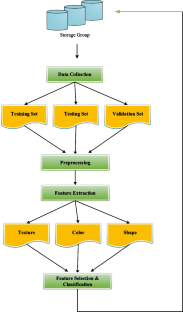
The Deep Learning (DL) approach is a subcategory of Machine Learning (ML), introduced in 1943 [ 1 ] when threshold logic was introduced to build a computer model closely resembling the biological pathways of humans. This field of research is still evolving; its evolution can be divided into two time periods-from 1943–2006 and from 2012–until now. During the first phase, several developments like backpropagation [ 2 , 3 ], chain rule [ 4 ], Neocognitron [ 5 ], hand written text recognition (LeNET architecture) [ 6 ], and resolving the training problem [ 7 , 8 ] were observed (as shown in Figure 1 ). However, in the second phase, state-of-the-art algorithms/architectures were developed for many applications including self-driving cars [ 9 , 10 , 11 ], healthcare sector [ 12 , 13 , 14 ], text recognition [ 6 , 15 , 16 , 17 ], earthquake predictions [ 18 , 19 , 20 ], marketing [ 21 ], finance [ 22 , 23 ], and image recognition [ 24 , 25 , 26 , 27 , 28 , 29 ]. Among those architectures, AlexNet [ 30 ] is considered to be a breakthrough in the field of DL as it won the ImageNet challenge for object recognition known as ImageNet Large Scale Visual Recognition Challenge (ILSVRC) in the year 2012. Soon after, several architectures were introduced to overcome the loopholes observed previously. For the evaluation of these algorithms/architectures, various performance metrics were used. Among these metrics, top-1%/top-5% error [ 24 , 26 , 30 , 31 ], precision and recall [ 25 , 32 , 33 , 34 ], F1 score [ 32 , 35 ], training/validation accuracy and loss [ 34 , 36 ], classification accuracy (CA) [ 37 , 38 , 39 , 40 , 41 ] are the most popular. For the implementation of DL models, several steps are required, from the collection of datasets to visualization mappings are explained in Figure 2 .

Summary of the evolution of deep learning from 1943–2006.

Flow diagram of DL implementation: First, the dataset is collected [ 25 ] then split into two parts, normally into 80% of training and 20% of validation set. After that, DL models are trained from scratch or by using transfer learning technique, and their training/validation plots are obtained to indicate the significance of the models. Then, performance metrics are used for the classification of images (type of particular plant disease), and finally, visualization techniques/mappings [ 55 ] are used to detect/localize/classify the images.
When DL architectures started to evolve with the passage of time, researchers applied them to image recognition and classification. These architectures have also been implemented for different agricultural applications. For example, in [ 42 ], classification of leaves was performed by using author-modified CNN and Random Forest (RF) classifier among 32 species in which the performance was evaluated through CA at 97.3%. On the other hand, it was not as efficient at detecting occluded objects [ 43 ]. Leaf and fruit counting were also performed by deep CNN in [ 44 , 45 ] and [ 46 ] respectively. For classification of crop type, [ 47 ] used author-modified CNN, [ 36 ] applied VGG 16, [ 34 ] implemented three unit LSTM, and [ 33 ] used CNN and RGB histogram technique. [ 47 ] used CA, [ 36 ] used CA and Intersection over Union (IoU), [ 34 ] used CA and F1, and [ 33 ] used F1-score as a performance metric. Among them, [ 33 , 47 ] did not provide training/validation accuracy and loss. Moreover, recognition of different plants has been done by the DL approach in [ 48 , 49 , 50 ]. [ 48 , 50 ] employed user-modified CNN while [ 49 ] used AlexNet architecture. All were evaluated on the basis of CA. [ 49 ] outperformed the other two in terms of CA. Similarly, crop/weed discrimination was performed in [ 51 , 52 ], in which the author proposed CNN be used, and two datasets were utilized for the evaluation of the model. [ 51 ] evaluated precision and recall; however, [ 52 ] obtained CA for the validation of the proposed models respectively. The identification of plants by the DL approach was studied and achieved a success rate of 91.78% [ 53 ]. On top of that, DL approaches are also used for critical tasks like plant disease detection and classification, which is the main focus of this review. There are some research papers previously presented to summarize the research based on agriculture (including plant disease recognition) by DL [ 43 , 54 ], but they lacked some of the recent developments in terms of visualization techniques implemented along with the DL and modified/cascaded version of famous DL models, which were used for plant disease identification. Moreover, this review also provides the research gaps in order to get a clearer/more transparent vision of symptoms observed due to diseases in the plants.
The remaining part of the paper is comprised of Section 2 , describing the famous and new/modified DL architectures along with visualization mapping/techniques used for plant disease detection; Section 3 , elaborating upon the Hyperspectral Imaging with DL models; and finally, Section 4 , concluding the review and providing future recommendations for achieving more advancements in the visualization, detection, and classification of plants’ diseases.
2. Plant Disease Detection by Well-Known DL Architectures
Many state-of-the-art DL models/architectures evolved after the introduction of AlexNet [ 30 ] (as shown in Figure 3 and Table 1 ) for image detection, segmentation, and classification. This section presents the researches done by using famous DL architectures for the identification and classification of plants’ diseases. Moreover, there are some related works in which new visualization techniques and modified/improved versions of DL architectures were introduced to achieve better results. Among all of them, the PlantVillage dataset has been used widely as it contains 54,306 images of 14 different crops having 26 plant diseases [ 25 ]. Moreover, they used several performance metrics to evaluate the selected DL models, which are described as below.

Summary of the evolution of various deep learning models from 2012 until now.
Comparison of state-of-the-art deep learning models.
| Deep Learning Models | Parameters | Key Features and Pros/Cons |
|---|---|---|
| LeNet | 60k | First CNN model. Few parameters as compared to other CNNmodels. Limited capability of computation |
| AlexNet | 60M | Known as the first modern CNN. Best image recognition performance at its time. Used ReLU to achieve better performance. Dropout technique was used to avoid overfitting |
| OverFeat | 145M | First model used for detection, localization, and classification of objects through a single CNN. Large number of parameters as compared to AlexNet |
| ZFNet | 42.6M | Reduced weights (as compared to AlexNet) by considering 7 × 7 kernels and improved accuracy |
| VGG | 133M–144M | 3 × 3 receptive fields were considered to include more number of non-linearity functions which made decision function discriminative. Computationally expensive model due to large number of parameters |
| GoogLeNet | 7M | Fewer number of parameters as compared to AlexNet model. Better accuracy at its time |
| ResNet | 25.5M | Vanishing gradient problem was addressed. Better accuracy than VGG and GoogLeNet models |
| DenseNet | 7.1M | Dense connections between the layers. Reduced number of parameters with better accuracy |
| SqueezeNet | 1.25M | Similar accuracy as AlexNet with 50 times lesser parameters. Considered 1 × 1 filters instead of 3 × 3 filters. Input channels were decreased. Large activation maps of convolution layers |
| Xception | 22.8M | A depth-wise separable convolution approach. Performed better than VGG, ResNet, and Inception-v3 models |
| MobileNet | 4.2M | Considered the depth-wise separable convolution concept. Reduced parameters significantly. Achieved accuracy near to VGG and GoogLeNet |
| Modified/Reduced MobileNet | 0.5/0.54M | Lesser number of parameters as compared to MobileNet. Similar accuracy as compared to MobileNet |
| VGG-Inception | 132M | A cascaded version of VGG and inception module. The number of parameters were reduced by substituting 5 × 5 convolution layers with two 3 × 3 layers. Testing accuracy was increased as compared to many well-known DL models like AlexNet, GoogLeNet, Inception-v3, ResNet, and VGG-16. |
2.1. Implementation of DL Models
2.1.1. without visualization technique.
In [ 56 ], CNN was used for the classification of diseases in maize plants and histogram techniques to show the significance of the model. In [ 57 ], basic CNN architectures like AlexNet, GoogLeNet and ResNet were implemented for identifying the tomato leaf diseases. Training/validation accuracy were plotted to show the performance of the model; ResNet was considered as the best among all the CNN architectures. In order to detect the diseases in banana leaf, LeNet architecture was implemented and CA, F1-score were used for the evaluation of the model in Color and Gray Scale modes [ 32 ]. Five CNN architectures were used in [ 58 ], namely, AlexNet, AlexNetOWTbn, GoogLeNet, Overfeat, and VGG architectures in which VGG outclassed all the other models. In [ 35 ], eight different plant diseases were recognized by three classifiers, Support Vector Machines (SVM), Extreme Learning Machine (ELM), and K-Nearest Neighbor (KNN)), used with the state-of-the-art DL models like GoogLeNet, ResNet-50, ResNet-101, Inception-v3, InceptionResNetv2, and SqueezeNet. A comparison was made between those models, and ResNet-50 with SVM classifier got the best results in terms of performance metrics like sensitivity, specificity, and F1-score. According to [ 59 ], a new DL model—Inception-v3—was used for the detection of cassava disease. In [ 60 ], plant diseases in cucumber were classified by the two basic versions of CNN and got the highest accuracy, equal to 0.823. The traditional plant disease recognition and classification method was replaced by Super-Resolution Convolutional Neural Network (SRCNN) in [ 61 ]. For the classification of tomato plant disease, AlexNet and SqueezeNet v1.1 models were used in which AlexNet was found to be the better DL model in terms of accuracy [ 62 ]. A comparative analysis was presented in [ 63 ] to select the best DL architecture for detection of plant diseases. Moreover in [ 64 ], six tomato plant diseases were classified by using AlexNet and VGG-16 DL architectures, and a detailed comparison was provided with the help of classification accuracy. In the above approaches, no visualization technique was applied to spot the symptoms of diseases in the plants.
2.1.2. With Visualization Techniques
The following approaches employed DL models/architectures and also visualization techniques which were introduced for a clearer understanding of plants’ diseases. For example, [ 55 ] introduced the saliency map for visualizing the symptoms of plant disease; [ 27 ] identified 13 different types of plant disease with the help of CaffeNet CNN architecture, and achieved CA equal to 96.30%, which was better than the previous approach like SVM. Moreover, several filters were used to indicate the disease spots. Similarly, [ 25 ] used AlexNet and GoogLeNet CNN architectures by using the publicly available PlantVillage dataset. The performance was evaluated by means of precision (P), recall (R), F1 score, and overall accuracy. The uniqueness of this paper was the implication of three scenarios (color, grayscale, and segmented) for evaluating the performance metrics and comparison of the two famous CNN architectures. It was concluded that GoogLeNet outperformed AlexNet. Moreover, visualization activation in the first layers clearly showed the spots of diseases. In [ 65 ], a modified LeNet model was used to detect olive plant diseases. The segmentation and edges maps were used to spot the diseases in the plants. Detection of four cucumber diseases was done in [ 66 ] and accuracy was compared with Random Forest, Support Vector Machines, and AlexNet models. Moreover, the image segmentation method was used to view the symptoms of diseases in the plants. A new DL model was introduced in [ 67 ] named teacher/student network and proposed a novel visualization method to identify the spots of plant diseases. DL models with some detectors were implemented in [ 68 ], in which the diseases in plants were marked along with their prediction percentage. Three detectors, named Faster-RCNN, RFCN and SSD, were used with the famous architectures like AlexNet, GoogLeNet, VGG, ZFNet, ResNet-50, ResNet-101 and ResNetXt-101 for a comparative study which outlined the best among all the selected architectures. It was concluded that ResNet-50 with the detector R-FCN gave the best results. Furthermore, a kind of bounding box was drawn to identify the particular type of disease in the plants. In [ 69 ], a banana leaf disease and pest detection was performed by using three CNN models (ResNet-50, Inception-V2 and MobileNet-V1) with Faster-RCNN and SSD detectors. According to [ 70 ], different combinations of CNN were used and presented heat maps as input to the diseased plants’ images and provided the probability related to the occurrence of a particular type of disease. Moreover, ROC curve evaluates the performance of the model. Furthermore, feature maps for rice disease were also included in the paper. LeNet model was used in [ 71 ] to detect and classify diseases in the soybean plant. In [ 72 ], a comparison between AlexNet and GoogLeNet architectures for tomato plant diseases was done, in which GoogLeNet performed better than the AlexNet; also, it proposed occlusion techniques to recognize the regions of diseases. The VGG-FCN and VGG-CNN models were implemented in [ 73 ], for the detection of wheat plant diseases and visualization of features in each block. In [ 74 ], VGG-CNN model was used for the detection of Fusarium wilt in radish and K-means clustering method was used to show the marks of diseases. A semantic segmentation approach by CNN was proposed in [ 75 ] to detect the disease in cucumber. In [ 76 ], an approach based on the individual symptoms/spots of diseases in the plants was introduced by using a DL model for detecting plant diseases. A Deep CNN framework was developed for identification, classification, and quantification of eight soybean stresses in [ 77 ]. In [ 78 ], rice plant diseases were identified by CNN, and feature maps were obtained to identify the patches of diseases. A deep residual neural network was extended in [ 79 ] for the development of a mobile application in which a clear identification of diseases in plants was done by the hot spot. An algorithm based on the hot spot technique was also used in [ 80 ], in which those spots were extracted by modification in the segmented image to attain color constancy. Furthermore, each obtained hot-spot was described by two descriptors, one was used to evaluate the color information of the disease and other was used to identify the texture of the hot-spots. The cucumber plant diseases were identified in [ 81 ] by using the dilation convolutional neural network. A state-of-the-art visualization technique was proposed in [ 82 ] by correlation coefficient and DL models like AlexNet and VGG-16 architectures. In [ 83 ], color space and various vegetation indices combined with CNN model (LeNet) to detect the diseases in grapes. To summarize, Table 2 outlines some of the visualization mapping/techniques.
Visualization mapping/techniques used in several approaches.
| Visualization Techniques/Mappings | References |
|---|---|
| Visualization of features having filter from first to final layer | [ ] |
| Visualize activations in first convolutional layer | [ ] |
| Saliency map visualization | [ ] |
| Classification and localization of diseases by bounding boxes | [ ] |
| Heat maps were used to identify the spots of the disease | [ ] |
| Feature map for the diseased rice plant | [ ] |
| Symptoms visualization method | [ ] |
| Feature and spatial core maps | [ ] |
| Color space into HSV and K-means clustering | [ ] |
| Feature map for spotting the diseases | [ ] |
| Image segmentation method | [ ] |
| Reconstruction of images on discriminant regions, segmentation of images by binary threshold theorem, and heat map construction | [ ] |
| Saliency map visualization | [ ] |
| Saliency map, 2D and 3D contour, mesh graph image | [ ] |
| Activation visualization | [ ] |
| Segmentation map and edge map | [ ] |
For the practical experimentation of detection of plants’ diseases, an actual/real background/environment should be considered in order to evaluate the performance of the DL model more accurately. In most of the above approaches, the selected datasets considered plain backgrounds which are not realistic scenarios for identification and classification of the diseases [ 25 , 27 , 32 , 56 , 57 , 58 , 60 , 61 , 65 , 72 , 77 , 78 ], except for a few of them that have considered the original backgrounds [ 35 , 59 , 68 , 70 , 73 , 74 ]. The output of the visualization techniques used in several researches are shown in Figure 4 , Figure 5 , Figure 6 , Figure 7 , Figure 8 , Figure 9 , Figure 10 and Figure 11 .

Feature maps after the application of convolution to an image: ( a ) real image, ( b ) first convolutional layer filter, ( c ) rectified output from first layer, ( d ) second convolutional layer filter, ( e ) output from second layer, ( f ) output of third layer, ( g ) output of fourth layer, ( h ) output of fifth layer [ 27 ].

Tomato plant disease detection by heat map: on left hand side ( a ) tomato early blight, ( b ) tomato septoria leaf spot, ( c ) tomato late blight and ( d ) tomato leaf mold) and saliency map; on right hand side ( a ) tomato healthy, ( b ) tomato late blight, ( c ) tomato early blight, ( d ) tomato septoria leaf spot, ( e ) tomato early blight, ( f ) tomato leaf mold) [ 55 ].

Detection of maize disease (indicated by red circles) by heat map [ 70 ].

Bounding box indicates the type of diseases along with the probability of their occurrence [ 68 ]. A bounding box technique was used in Figure 7 in which ( a ) represents the one type of disease along with its rate of occurrence, ( b ) indicates three types of plant disease (miner, temperature, and gray mold) in a single image, ( c , d ) shows one class of disease but contains different patterns on the front and back side of the image, ( e , f ) displays different patterns of gray mold in the starting and end stages [ 68 ].

( a ) Teacher/student architecture approach; ( b ) segmentation using a binary threshold algorithm [ 67 ].

Comparison of Teacher/student approach visualization map with the previous approaches [ 67 ].

Activation visualization for detection of apple plant disease to show the significance of a VGG-Inception model (the plant disease is indicated by the red circle) [ 85 ].

Segmentation and edge map for olive leaf disease detection [ 65 ].
In Figure 4 , feature maps from the first to the fifth hidden layer are shown as the neuron in a feature map having identical features at different positions of an image. Starting from the first layer (a), the features in feature maps represent separate pixels to normal lines, whereas the fifth layer shows some particular parts of the image (h).
Two types of visualization maps are shown in Figure 5 , namely, heat map and saliency map techniques. The heat maps identify the diseases shown as red boxes in the input image, but it should be noted that one disease marked in (d) has not been detected. This problem was resolved in the saliency map technique after the application of the guided back-propagation [ 55 ]; all the spots of plant disease were successfully identified thanks to a method which is superior to the heat map.
Figure 6 represents the heat map to detect the disease in maize plants. First, the image was represented in the form of the probability of each portion containing disease. Then, the probabilities were placed into the form of a matrix in order to denote the outcome of all the areas of the input image.
A new visualization technique was proposed in [ 67 ] as shown in Figure 8 and Figure 9 . In Figure 8 a, the input image was regenerated for student/teacher architecture [ 67 ], and a single channel heat map was produced after the application of simple aggregation on the channels of the regenerated image ( Figure 8 b). Then, a simple binary threshold algorithm was applied to obtain sharp symptoms of diseases in the plant. Then, [ 67 ] indicated the significance of the proposed technique by comparing it with the other visualization techniques as shown in Figure 9 . On the left hand side, LRP-Z, LRP-Epsilon, and gradient did not identify plant diseases clearly. However, the Deep Taylor approach produced better results but indicated some portion of the leaf disease. On the right hand side, an imperfect localization of the plant disease was shown in grad-cam techniques which was resolved in the proposed technique by the use of a decoder [ 67 ].
In order to find the significance of CNN architectures to differentiate between various diseases of plants, the feature maps were obtained as shown in Figure 10 . The result proves a good performance of the proposed CNN model as it clearly identifies the disease in plants [ 85 ].
In Figure 11 the segmentation and edged maps were obtained to identify the diseases in plants. It is noted that the yellow colored area is marked as white surface in the segmentation map to show the affected part of the leaf.
2.2. New/Modified DL Architectures for Plant-Disease Detection
According to some of the research papers, new/modified DL architectures have been introduced to obtain better/transparent detection of plant disease, such as [ 86 ] presented improved GoogLeNet and Cifar-10 models and their performance compared with AlexNet and VGG. It was found that improved versions of these state-of-the-art models produced a remarkable accuracy of 98.9%. In [ 87 ], a new DL model was introduced to obtain more accurate detection of plant diseases as compared to SVM, AlexNet, GoogLeNet, ResNet-20, and VGG-16 models. This model achieved 97.62% accuracy for classifying apple plant diseases. Moreover, the dataset extended in 13 different ways (rotation of 90°, 180°, 270° and mirror symmetry (horizontal symmetry), change in contrast, sharpness and brightness). Moreover, the whole dataset was transformed into Gaussian noise and PCA jittering as well. Furthermore, the selection of dataset was explained by the help of plots to prove the significance of extending the dataset. A new CNN model named LeafNet was introduced in [ 88 ] to classify the tea leaf diseases and achieved higher accuracy than Support Vector Machine (SVM) and Multi-Layer Perceptron (MLP). In [ 89 ], two DL models named modified MobileNet and reduced MobileNet were introduced, and their accuracy was near to the VGG model; the reduced MobileNet actually got 98.34% classification accuracy and had a fewer number of parameters as compared to VGG which saves time in training the model. A state-of-the-art DL model was proposed in [ 90 ] named PlantdiseaseNet which was remarkably suitable for the complex environment of an agricultural field. In [ 85 ], five types of apple plant diseases were classified and detected by the state-of-the-art CNN model named VGG-inception architecture. It outclassed the performance of many DL architectures like AlexNet, GoogLeNet, several versions of ResNet, and VGG. It also presented inter object/class detection and activation visualization; it was also mentioned for its clear vision of diseases in the plants.
A bar chart presented in Figure 12 indicates, from the most to the least frequently used, DL models for plant disease detection and classification. It can be clearly seen that the AlexNet model has been used in most of the researches. GoogLeNet, VGG-16, and ResNet-50 are the next most commonly used DL models. Similarly, there are some improved/cascaded versions (Improved Cifar-10, VGG-Inception, Cascaded AlexNet with GoogLeNet, reduced/modified MobileNet, modified LeNet, and modified GoogLeNet), which have been used for plant disease identification.

Deep learning models used in the particular number of research papers.
Summing up Section 2 , all the DL approaches along with the selected plant species and performance metrics are shown in Table 3 .
Comparison of several DL approaches in terms of various performance metrics.
| DL Architectures/Algorithms | Datasets | Selected Plant/s | Performance Metrics (and Their Results) | Refs |
|---|---|---|---|---|
| CNN | PlantVillage | Maize | CA (92.85%) | [ ] |
| AlexNet, GoogLeNet, ResNet | PlantVillage | Tomato | CA by ResNet which gave the best value (97.28%) | [ ] |
| LeNet | PlantVillage | Banana | CA (98.61%), F1 (98.64%) | [ ] |
| AlexNet, ALexNetOWTBn, GoogLeNet, Overfeat, VGG | PlantVillage and in-field images | Apple, blueberry, banana, cabbage, cassava, cantaloupe, celery, cherry, cucumber, corn, eggplant, gourd, grape, orange, onion | Success rate of VGG (99.53%) which is the best among all | [ ] |
| AlexNet, VGG16, VGG 19, SqueezeNet, GoogLeNet, Inceptionv3, InceptionResNetv2, ResNet50, Resnet101 | Real field dataset | Apricot, Walnut, Peach, Cherry | F1(97.14), Accuracy (97.86 ± 1.56) of ResNet | [ ] |
| Inceptionv3 | Experimental field dataset | Cassava | CA (93%) | [ ] |
| CNN | Images taken from the research center | Cucumber | CA (82.3%) | [ ] |
| Super-Resolution Convolutional Neural Network (SCRNN) | PlantVillage | Tomato | Accuracy (~90%) | [ ] |
| CaffeNet | Downloaded from the internet | Pear, cherry, peach, apple, grapevine | Precision (96.3%) | [ ] |
| AlexNet and GoogLeNet | PlantVillage | Apple, blueberry, bell pepper, cherry, corn, peach, grape, raspberry, potato, squash, soybean, strawberry, tomato | CA (99.35%) of GoogLeNet | [ ] |
| AlexNet, GoogLeNet, VGG- 16, ResNet-50,101, ResNetXt-101, Faster RCNN, SSD, R-FCN, ZFNet | Image taken in real fields | Tomato | Precision (85.98%) of ResNet-50 with Region based Fully Convolutional Network(R-FCN) | [ ] |
| CNN | Bisque platform of Cy Verse | Maize | Accuracy (96.7%) | [ ] |
| DCNN | Images were taken in real field | Rice | Accuracy (95.48%) | [ ] |
| AlexNet, GoogLeNet | PlantVillage | Tomato | Accuracy (0.9918 ± 0.169) of GoogLeNet | [ ] |
| VGG-FCN-VD16 and VGG-FCN-S | Wheat Disease Database 2017 | Wheat | Accuracy (97.95%) of VGG-FCN-VD16 | [ ] |
| VGG-A, CNN | Images were taken in real field | Radish | Accuracy (93.3%) | [ ] |
| AlexNet | Images were taken in real field | Soybean | CA (94.13%) | [ ] |
| AlexNet and SqueezeNet v1.1 | PlantVillage | Tomato | CA (95.65%) of AlexNet | [ ] |
| DCNN, Random forest, Support Vector Machine and AlexNet | PlantVillage dataset, Forestry Image dataset and agricultural field in China | Cucumber | CA (93.4%) of DCNN | [ ] |
| Teacher/student architecture | PlantVillage | Apple, bell pepper, blueberry, cherry, corn, orange, grape, potato, raspberry, peach, soybean, strawberry, tomato, squash | Training accuracy and loss (~99%,~0–0.5%), validation accuracy and loss (~95%, ~10%) | [ ] |
| Improved GoogLeNet, Cifar-10 | PlantVillage and various websites | Maize | Top-1 accuracy (98.9%) of improved GoogLeNet | [ ] |
| MobileNet, Modified MobileNet, Reduced MobileNet | PlantVillage dataset | 24 types of plant | CA (98.34%) of reduced MobileNet | [ ] |
| VGG-16, ResNet-50,101,152, Inception-V4 and DenseNets-121 | PlantVillage | Apple, bell pepper, blueberry, cherry, corn, orange, grape, potato, raspberry, peach, soybean, strawberry, tomato, squash | Testing accuracy (99.75%) of DenseNets | [ ] |
| User defined CNN, SVM, AlexNet, GoogLeNet, ResNet-20 and VGG-16 | Images were taken in real field | Apple | CA (97.62%) of proposed CNN | [ ] |
| AlexNet and VGG-16 | PlantVillage | Tomato | CA (AlexNet) | [ ] |
| LeafNet, SVM, MLP | Images were taken in real field | Tea leaf | CA (90.16%) of LeafNet | [ ] |
| 2D-CNN-BidGRU | Real wheat field | wheat | F1 (0.75) and accuracy (0.743) | [ ] |
| OR-AC-GAN | Real environment | Tomato | Accuracy (96.25%) | [ ] |
| 3D CNN | Real environment | Soybean | CA (95.73%), F1-score (0.87) | [ ] |
| DCNN | Real environment | Wheat | Accuracy (85%) | [ ] |
| ResNet-50 | Real environment | Wheat | Balanced Accuracy (87%) | [ ] |
| GPDCNN | Real environment | Cucumber | CA (94.65%) | [ ] |
| VGG-16, AlexNet | PlantVillage, CASC-IFW | Apple, banana | CA (98.6%) | [ ] |
| LeNet | Real environment | Grapes | CA (95.8%) | [ ] |
| PlantDiseaseNet | Real environment | Apple, bell-pepper, cherry, grapes, onion, peach, potato, plum, strawberry, sugar-beets, tomato, wheat | CA (93.67%) | [ ] |
| LeNet | PlantVillage | Soybean | CA (99.32%) | [ ] |
| VGG-Inception | Real environment | Apple | Mean average accuracy (78.8%) | [ ] |
| Resnet-50, Inception-V2, MobileNet-V1 | Real environment | Banana | Mean average accuracy (99%) of ResNet-50 | [ ] |
| Modified LeNet | PlantVillage | Olives | True positive rate (98.6 ± 1.47%) | [ ] |
3. Hyper-Spectral Imaging with DL Models
For early detection of plant diseases, several imaging techniques like multispectral imaging [ 91 ], thermal imaging, fluorescence and hyperspectral imaging are used [ 92 ]. Among them, hyperspectral imaging (HSI) is the focus of recent research. For example, [ 93 ] used hyperspectral imaging (HSI) to detect tomato plant diseases by identifying the region of interest, and a feature ranking-KNN (FR-KNN) model produced a satisfactory result for the detection of diseased and healthy plants. In the recent approach, HSI was used for the detection of an apple disease. Moreover, the redundancy issue was resolved by an unsupervised feature selection procedure known as Orthogonal Subspace Projection [ 94 ]. In [ 95 ], leaf diseases on peanuts were detected by HSI by identifying sensitive bands and hyperspectral vegetation index. The tomato disease detection was done by SVM classifiers based on HSI, and their performance was evaluated by F1-score, accuracy, specificity, and sensitivity [ 96 ].
Recently, HSI has been used with machine learning (ML) for the detection of plant diseases. For example, [ 97 ] described ML techniques for hyperspectral imaging for many agricultural applications. Moreover, ML with HSI have been used for three ML models, implemented by using hyperspectral measurement technique for the detection of leaf rust disease [ 98 ]. For wheat disease detection, [ 99 ] used Random Forest (RF) classifier with multispectral imaging technique and achieved accuracy of 89.3%. Plants’ diseases were also detected by SVM based on hyperspectral data and achieved accuracy of more than 86% [ 100 ]. There are some other ML approaches based on HSI [ 101 ], but this review is focused on DL approaches based on HSI, presented below.
The DL has been used to classify the hyperspectral images for many applications. For medical purposes, this technology is very useful as it is used for the classification of head/neck cancer in [ 102 ]. In [ 103 ], a DL approach based on HSI was proposed through contextual information as it provides spectral and spatial features. A new 3D-CNN architecture allowed for a fast, accurate, and efficient approach to classify the hyperspectral images in [ 104 ]. This architecture not only used the spectral information (as used in previous CNN techniques [ 105 ]) but also ensured that the spatial information was also taken into account. In [ 106 ], the feature extraction procedure was used with CNN for hyperspectral image classification and used dropout and L2 regularization methods in order to prevent overfitting. Just like CNN models used for hyperspectral imaging classification, RNN models are also used with HSI as described in [ 107 , 108 ]. In the domain of plant disease detection, some researches utilized Hyperspectral Imaging (HSI) along with DL models to observe clearer vision for symptoms of plant diseases. A hybrid method to classify the hyperspectral images was proposed in [ 109 ] consisting of DCNN, LR, and PCA and got better results compared to the previous methods for classification tasks. In [ 110 ], a detailed review of DL with HSI technique was provided. In order to avoid the overfitting and improve accuracy, a detailed comparison provided between several DL models like 1D/2D-CNN (2D-CNN better result), LSTM/GRU (both faced overfitting), 2D-CNN-LSTM/GRU (still overfitting) was observed. Therefore, a new hybrid approach from Convolutional and Bidirectional Gated Recurrent Network named 2D-CNN-BidLSTM/GRU was proposed for the hyperspectral images, which resolved the problem of overfitting and achieved 0.75 F1-score and 0.73 accuracy for wheat diseases detection [ 111 ]. According to [ 112 ], a hyperspectral proximal-sensing procedure based on the newest DL technique named Generative Adversarial Nets (GAN) was proposed in order to detect tomato plant disease before its clear symptoms appeared (as shown in Figure 13 ). In [ 84 ], a 3D-CNN approach was proposed for hyperspectral images to identify the Charcoal rot disease in soybeans and the CNN model was evaluated by accuracy (95.76%) and F1-score (0.87). The saliency map visualization was used, and the most delicate wavelength resulted as 733 nm, which approximately lies in the region of the wavelength of NIR. For the detection of potato virus, [ 113 ] described it by DL on the hyperspectral images and achieved acceptable values of precision (0.78) and recall (0.88). In [ 114 ], a DL model named multiple Inception-Resnet model was developed by using both spatial and spectral data on hyperspectral UAV images to detect the yellow rust in wheat (as shown in Figure 14 ). This model achieved an 85% accuracy, which is quite a lot higher than the RF-classifier (77%).

Sample images of OR-AC-GAN (a hyperspectral imaging model) [ 112 ].

Hyperspectral images by UAV: ( a ) RGB color plots, ( b ) Random-Forest classifier, and ( c ) proposed multiple Inception-ResNet model [ 114 ].
From this section, we can conclude that, although there are some DL models/architectures developed for hyperspectral image classification in the application of plant disease detection, this is still a fertile area of research and should lead to improvements for better detection of plants’ diseases [ 115 ] in different situations, like various conditions of illumination, considering real background, etc.
In Figure 13 , the resultant images are taken from the proposed method described in [ 112 ]. The green-colored portion indicates the healthy part of the plant; the red portion denotes the infected portion. Note that ( a ) and ( b ) are the healthy plant images as there is no red color indication, whereas ( c ) has infected disease which can be seen in its corresponding figure ( d ).
A comparison of proposed DCNN with RF classifier and RGB colored hyperspectral images are shown in Figure 14 . The red color label indicates the portion infected by rust. It should be observed that the rust plots were identified in an almost similar manner (see (b) and (c) of first row), but in the healthy plot, there was a large portion covered by the red label in (b) as compared to (c), which shows a wrong classification by RF model [ 114 ].
4. Conclusions and Future Directions
This review explained DL approaches for the detection of plant diseases. Moreover, many visualization techniques/mappings were summarized to recognize the symptoms of diseases. Although much significant progress was observed during the last three to four years, there are still some research gaps which are described below:
- In most of the researches (as described in the previous sections), the PlantVillage dataset was used to evaluate the accuracy and performance of the respective DL models/architectures. Although this dataset has a lot of images of several plant species with their diseases, it has a simple/plain background. However, for a practical scenario, the real environment should be considered.
- Hyperspectral/multispectral imaging is an emerging technology and has been used in many areas of research (as described in Section 3 ). Therefore, it should be used with the efficient DL architectures to detect the plants’ diseases even before their symptoms are clearly apparent.
- A more efficient way of visualizing the spots of disease in plants should be introduced as it will save costs by avoiding the unnecessary application of fungicide/pesticide/herbicide.
- The severity of plant diseases changes with the passage of time, therefore, DL models should be improved/modified to enable them to detect and classify diseases during their complete cycle of occurrence.
- DL model/architecture should be efficient for many illumination conditions, so the datasets should not only indicate the real environment but also contain images taken in different field scenarios.
- A comprehensive study is required to understand the factors affecting the detection of plant diseases, like the classes and size of datasets, learning rate, illumination, and the like.
Abbreviations
The abbreviations used in this manuscript are given as under:
| ML | Machine Learning |
| DL | Deep Learning |
| CNN | Convolutional Neural network |
| DCNN | Deep Convolutional Neural Network |
| ILSVRC | ImageNet Large Scale Visual Recognition Challenge |
| RF | Random Forest |
| CA | Classification Accuracy |
| LSTM | Long Short-Term Memory |
| IoU | Intersection of Union |
| NiN | Network in Network |
| RCN | Region based Convolutional Neural Network |
| FCN | Fully Convolutional Neural Network |
| YOLO | You Only Look Once |
| SSD | Single Shot Detector |
| PSPNet | Pyramid Scene Parsing Network |
| IRRCNN | Inception Recurrent Residual Convolutional Neural Network |
| IRCNN | Inception Recurrent Convolutional Neural Network |
| DCRN | Densely Connected Recurrent Convolutional Network |
| INAR-SSD | Single Shot Detector with Inception module and Rainbow concatenation |
| R2U-Net | Recurrent Residual Convolutional Neural Network based on U-Net model |
| SVM | Support Vector Machines |
| ELM | Extreme Learning Machine |
| KNN | K-Nearest Neighbor |
| SRCNN | Super-Resolution Convolutional Neural Network |
| R-FCN | Region-based Fully Convolutional Networks |
| ROC | Receiver Operating Characteristic |
| PCA | Principal Component Analysis |
| MLP | Multi-Layer Perceptron |
| LRP | Layer-wise Relevance Propagation |
| HSI | Hyperspectral Imaging |
| FRKNN | Feature Ranking K-Nearest Neighbor |
| RNN | Recurrent Neural Network |
| ToF | Time-of-Flight |
| LR | Logistic Regression |
| GRU | Gated Recurrent Unit |
| AN | Generative Adversarial Nets |
| GPDCNN | Global Pooling Dilated Convolutional Neural Network |
| 2D-CNN-BidGRU | 2D-Convolutional-Bidirectional Gated Recurrent Unit Neural Network |
| OR-AC-GAN | Outlier Removal-Auxiliary Classifier-Generative Adversarial Nets |
Author Contributions
Conceptualization, M.H.S. and K.M.A.; methodology, M.H.S. and K.M.A.; writing—original draft preparation, M.H.S. and K.M.A.; writing—review and editing, M.H.S., J.P., and K.M.A; visualization, M.H.S., J.P., and K.M.A; supervision, J.P., and K.M.A.; project administration, J.P., and K.M.A.
This research was funded by the Ministry of Business, Innovation and Employment (MBIE), New Zealand, Science for Technological Innovation (SfTI) National Science Challenge.
Conflicts of Interest
The authors declare no conflict of interest.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Criminal Identification System using Facial Recognition

We all know that our Face is a unique and crucial part of the human body structure that identifies a person. Therefore, we can use it to trace the identity of a criminal person. With the advancement in technology, we are placed CCTV at many public places to capture the criminal's crime. Using the previously captured faces and criminal's images that are available in the police station, the criminal face recognition system of can be implemented. In this paper, we propose an automatic criminal identification system for Police Department to enhance and upgrade the criminal distinguishing into a more effective and efficient approach. Using technology, this idea will add plus point in the current system while bringing criminals spotting to a whole new level by automating tasks. Technology working behind it will be face recognition, from the footage captured by the CCTV cameras; our system will detect the face and recognize the criminal who is coming to that public place. The captured images of the person coming to that public place get compared with the criminal data we have in our database. If any person's face from public place matches, the system will display their image on the system screen and will give the message with their name that the criminal is found and present in this public place. This system matching more than 80% of the captured images with database images.
Related Papers
International journal for research in applied science and engineering technology ijraset
IJRASET Publication
: Criminals information usually have the personal details about that person with pictures and other important details. For recognizing any kind Criminal we will be needing some details of that person, which is provided be a person who has witness the crime . In many of the cases the pixels of the already recorded image is very poor and very difficult to identify face. To sort this problem I am making a software. In which identification can be done in many ways like finger print, eyes, etc. One of the applications is face identification. Face is a primary focus of attention in social meetings which plays a very major role in carrying identification Firstly We will be matching the face with the available database. Secondly Putting the analytical component for finding same features from many images to get the similar of the targeted image This will help the law to find or criminal of the case . The results will shows about 90% of input photo will be matched with the stored data. This paper is to propose the criminal face identification system in which the images stored in the database will be matched to the image stored in another database to find out the criminals.
shraddha wadvekar
As the world has seen exponential development over the last decade, there is an atypical increase in the crime rate and also the number of criminals is increasing at an alarming rate, this leads toward a great concern about the security issues. The individualistic characters of the human face can be extracted by face recognition. Face recognition is a simple and agile bio-metric technology. Face detection and recognition is the technology which is used to identify a person from a video or image. With the advancement in technology, the extracting features of the human face are become simpler. This paper presents a real time face recognition using a automated surveillance camera. In this system, we can detect and recognize the faces of the criminals in a video stream obtained from a camera in real-time. Criminal records generally consists personal details and the photograph of the criminal. So, we can use these photograph along with his details. The video captured from the surveillanc...
Pattern Recognition and Image Analysis
Sourav Patil
International Journal of Advance Research, Ideas and Innovations in Technology
Ijariit Journal , Archana Naik
The individualistic characters of the human face can be extracted by face recognition. The human face detection and recognition finds a major role in the application as video surveillance, face image database management. Face recognition is a simple and agile biometric technology. This technology uses the most obvious human identifier to the face. The face recognition finds its application in security, health care, criminal identification, places where human recognition is the necessity. With the advancement in technology, the extracting features of the human face are become simpler. This paper discusses on a different algorithm to recognize the human face. The purpose is to identify the criminal face and retrieve the information stored in the database for the identified criminal. The process is categorized into two major steps. First, the face is extracted from the image, distinguishing factors in the face are extracted and stored in the database. The second step is to compare the resultant image with the existing image and return the data related to that image from the database.
Milan Bhikadiya
Face recognition is one of the most challenging topics in computer vision today. It has applications ranging from security and surveillance to entertainment websites. Face recognition software are useful in banks, airports, and other institutions for screening customers. Germany and Australia have deployed face recognition at borders and customs for Automatic Passport Control. Human face is a dynamic object having high degree of variability in its appearance which makes face recognition a difficult problem in computer vision. In this field, accuracy and speed of identification is a main issue. Many challenges exist for face recognition. The robustness of the system can be obstructed by humans who alter their facial features through wearing colored contact lenses, growing a mustache, putting on intense make-up, etc. Ethical concerns are also related to the process of recording, studying, and recognizing faces. Many individuals do not approve of surveillance systems which take numerous photographs of people who have not authorized this action. The goal of this paper is to evaluate face detection and recognition techniques and provide a complete solution for image based face detection and recognition with higher accuracy, better response rate and an initial step for video surveillance. Solution is proposed based on performed tests on various face rich databases in terms of subjects, pose, emotions and light.
— in this paper We present a system for real-time, saved images And Video Recorded in this three Method We Can detecting and recognizing faces of a criminal at public place Or Checkpoint such that the system easy to learn And to implementation ,the three method that used in the system make recognition very accuracy , where if we running it will appear Login window in this screen should insert (username And Password) to enter in the main window, in the main window we must firstly insert images to Database and Then choose the way that want to recognition, if the system recognition the Face, the system will show the name of the criminal and in the same time the system will appear Danger Sound Refer that the Criminals Recognition and Matched in the Database , Besides that we can make Easy update(Rename ,Delete) to the Database without complexed. 1. Introduction Face recognition is one of the most active and widely used technique [1][2] because of its reliability and accuracy in the process of recognizing and verifying a person's identity. The need is becoming important since people are getting aware of security and privacy. For the Researchers Face Recognition is among the tedious work. It is all because the human face is very robust in nature; in fact, a person's face can change very much during short periods of time (from one day to another) and because of long periods of time (a difference of months or years). One problem of face recognition is the fact that different faces could seem very similar; therefore, a discrimination task is needed. On the other hand, when we analyze the same face, many characteristics may have changed. These changes might be because of changes in the different parameters. The parameters are: illumination, variability in facial expressions, the presence of accessories (glasses, beards, etc.); poses, age, finally background. We can divide face recognition [3][4] techniques into two big groups, the applications that required face identification and the ones that need face verification. The difference is that the first one uses a face to match with other one on a database; on the other hand, the verification technique tries to verify a human face from a given sample of that face. Face recognition has been an active research area over the last 30 years. It has been studied by scientists from different areas of psychophysical sciences and those from different areas of computer sciences. Psychologists and neuroscientists mainly deal with the human perception part of the topic, whereas engineers studying on machine recognition of human faces deal with the computational aspects of face recognition. Face recognition has applications mainly in the fields of biometrics, access control, law enforcement, and security and surveillance systems. 2. Biometric Measures Biometric systems are automated methods for identifying people through physiological or behavioral characteristics. Face recognition As compared with other biometrics systems using fingerprint/palm-print and iris, face recognition has distinct advantages because of its noncontact process. Face images can be(system would allow a person to be identified by walking in front of a camera and captured from a distance without touching the person being identified, and the identification does not require interacting with the person. In addition, face recognition serves the crime deterrent purpose because face images that have been recorded and archived can later help identify a person .
International Journal of Advanced Trends in Computer Science and Engineering
WARSE The World Academy of Research in Science and Engineering , Michael Bryan Lumaban
Closed-Circuit Television (CCTV) is a device generally used for security, and it is widely installed and utilized in shopping malls, grocery stores, offices, industries, housing, factories, transportation units, and other public places. CCTV can be further optimized to integrate facial recognition so as not only to utilize it to document crimes but to detect criminals at large and alert law enforcers via text message on their presence. This research used descriptive and system development methods and employed RAD methodology in developing a CCTV-Based Surveillance System with a face recognition feature. The study explored the application of the thee face recognition algorithms, namely Local Binary Pattern Histogram, Eigenface, and Fisherface. The LBPH algorithm was determined to have the highest face recognition rate, with a 95.92% accuracy rate. The developed system adopted the LBPH algorithm. The validation process was performed to assess compliance with ISO 25010-2015 Software Quality Requirements for the established framework. Ilagan City 's staff and IT experts from the Philippine National Police (PNP) gave an overall weighted mean of 4.82 with a qualitative definition of Very High Enforcement. This study sought the implementation of the developed system in the PNP to help detect the presence of the criminals in an area and deter crime from happening.
International Journal of Engineering Research and Technology (IJERT)
IJERT Journal
https://www.ijert.org/criminal-face-recognition-system https://www.ijert.org/research/criminal-face-recognition-system-IJERTV4IS030165.pdf Face recognition is one of the most challenging topics in computer vision today. It has applications ranging from security and surveillance to entertainment websites. Face recognition software are useful in banks, airports, and other institutions for screening customers. Germany and Australia have deployed face recognition at borders and customs for Automatic Passport Control. Human face is a dynamic object having high degree of variability in its appearance which makes face recognition a difficult problem in computer vision. In this field, accuracy and speed of identification is a main issue. Many challenges exist for face recognition. The robustness of the system can be obstructed by humans who alter their facial features through wearing colored contact lenses, growing a mustache, putting on intense make-up, etc. Ethical concerns are also related to the process of recording, studying, and recognizing faces. Many individuals do not approve of surveillance systems which take numerous photographs of people who have not authorized this action. The goal of this paper is to evaluate face detection and recognition techniques and provide a complete solution for image based face detection and recognition with higher accuracy, better response rate and an initial step for video surveillance. Solution is proposed based on performed tests on various face rich databases in terms of subjects, pose, emotions and light.
International Journal for Research in Applied Science & Engineering Technology (IJRASET)
In these days, assessment camera structure wins as a security system at high speed since this structure can screen from remote spots using Web camera joined to video screen by network. Besides, computerized supplies like Web camera, and hard circle drive are proficiently fabricated, and are sold for minimal price. Likewise, execution gain of these mechanized sorts of stuff improves at a fast rate. Current perception camera structure shows dynamic pictures from some oversight areas shot by various Web cameras all the while. Then, this system makes spectator's mind and body tired considering the way that he/she wants to watch enormous number of dynamic pictures been persistently strengthened. Moreover, this structure has a troublesome issue, which is an observer slips over mark of bad behavior. This study eliminates Motion Region from moving individual, and measures Motion Quantity for assessing his/her dynamic state. Also, this recommendation method finds the distinctive place of questionable activity, and checks the degree of risk of the questionable development. I.
IRJET Journal
This paper helps in real time face recognition using a automated face surveillance camera. The proposed system consists of 4 steps, it include training of real time images face detection using Haar based classifier comparison of trained real time images with images from the surveillance camera result based on the comparison between them. An most important application of interest is automated surveillance, the objective of automated surveillance to recognize people who around watch list. The ambition of this paper is to compare an image with several images which has been already trained. In this paper, we represent a methodology for face detection strongly in real time environment. Haar cascading is one of the algorithm for face detection. In that we use Haar like classifiers to track faces on OpenCV platform. The correctness of the face recognition is very high. The proposed system can successfully recognize more faces which is useful for quickly searching suspected persons as the computation time is very low. In India, we have a system to recognizing citizen called Aadhaar. If we use this as acitizenship database then we can differentiate between citizen and foreigner as well as we will be able to investigate whether the identified person is criminal or not.
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
Icon-LBG 2016 The Third International Conference On Law, Business and Governance 2016
Robby Yuli Endra
CERN European Organization for Nuclear Research - Zenodo
Jeet Kansagara
ARTIFICIALLY INTELLIGENT FACE DETECTION AND INVESTIGATION SYSTEM BASED ON OPENCV-FINAL-THESIS-2019
Bill Kiyimba
International Journal of Scientific Research in Science, Engineering and Technology
International Journal of Scientific Research in Science, Engineering and Technology IJSRSET
International Journal of Advanced Scientific Innovation
IJASI Journal
International Journal of Scientific Research in Computer Science, Engineering and Information Technology
International Journal of Scientific Research in Computer Science, Engineering and Information Technology IJSRCSEIT
Indian Journal
Mushtaq Ahmed
International Journal of Scientific Research in Science, Engineering and Technology IJSRSET , Raghu Shakil F, Prof. Saurabh Shah
Intelligent Decision Technologies
Asm Moslehuddin
International Journal on Recent and Innovation Trends in Computing and Communication
Dr. Kshitij Shinghal
Wasit Journal of Pure sciences
International Journal of Advance Research in Computer Science and Management Studies [IJARCSMS] ijarcsms.com
IJCSMC Journal
Proceedings of the 2022 International Conference on Advancements in Interdisciplinary Research towards Smart and Sustainable Society (AIR2022)
Arjun Menon , Kumari Shivani Singh , raushan kumar
Rasha Basim Yousif
Indonesian Journal of Electrical Engineering and Computer Science
Ambrose Azeta
International Journal of Engineering and Advanced Technology
Arvinda Kushwaha
Prof. Dr. Saad Mekhilef
International Journal of Advanced Research in Computer Science
Darshan S Honnappanavar
Fawzia Mansur
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
A Novel Approach for Accurate Identification in Masked and Unmasked Scenarios using Glowworm Swarm Optimization and Neural Networks
- Published: 31 August 2024
Cite this article

- Kosuri Naresh Babu ORCID: orcid.org/0009-0001-2215-345X 1 &
- Suneetha Manne ORCID: orcid.org/0000-0002-8917-276X 2
Recognition and classification are among the most important applications of machine learning. This recognition process is used to identify objects and humans. In particular, it plays a major role in authentication processes by identifying features such as human eyes, fingerprints, and facial patterns. Among these features, facial recognition is an evolving technology used in smartphones, attendance systems in offices, and healthcare centers. Several research efforts have been conducted to perform facial recognition using machine learning and deep learning algorithms. These algorithms have performed well on faces without masks, but they have struggled with masked faces, as most facial features are hidden by the mask. Therefore, an improved algorithm is needed for performing facial recognition on faces with and without masks. Since the COVID-19 outbreak, research has been focused on using deep learning algorithms to identify masked faces. However, these algorithms were typically trained on faces both with and without masks. In this paper, we propose a facial recognition approach for recognizing faces with and without masks. The common regions of the face in both scenarios are identified by cropping the image. These cropped regions are then subjected to feature extraction using histogram properties, SURF, and SIFT features. The dominant features are identified using a swarm intelligence approach called Glowworm Swarm Optimization. These dominant features are then trained using a neural network with a regression function. Finally, the performance of the proposed method will be evaluated based on accuracy, sensitivity, and specificity and compared to existing approaches, such as SURF, with different variations for facial recognition with and without masks.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Explore related subjects
- Artificial Intelligence
Data Availability
The data used to support the findings of created new data set, this study is available from the corresponding author upon request.
Abbreviations
Generalized Regression Neural Network
Adaptive Histogram Equalization
Histogram Modification Function
Scale-Invariant Feature Transform
Speeded-Up Robust Features
Unsupervised Speeded-Up Robust Features
Hybrid Glowworm Swarm Optimization
Glowworm Swarm Optimization
Hemathilaka, Susith & Aponso, Achala. (2021). An Analysis of Face Recognition under Face Mask Occlusions. 41–48. https://doi.org/10.5121/csit.2021.111804 .
Aware, Mrunal & Labade, Prasad & Tambe, Manish & Jagtap, Aniket & Beldar, Chinmay. (2021). Attendance Management System using Face-Recognition. International Journal of Scientific Research in Computer Science, Engineering and Information Technology. 336–341. https://doi.org/10.32628/CSEIT217370 .
Alexiou, Michail & Papadakis Ktistakis, Iosif & Goodman, Garrett. (2021). Towards a Masked Face Recognition Algorithm: A Novel Rule Based Hybrid Algorithm. 1–6. https://doi.org/10.1109/SEEDA-CECNSM53056.2021.9566244 .
Baskaran, Kaaviya & P, Baskaran & V, Rajaram & Kumaratharan, Narayanaswamy. (2020). IoT Based COVID Preventive System for Work Environment. 65–71. https://doi.org/10.1109/I-SMAC49090.2020.9243471 .
Arora M, Naithani S, Areeckal A (2022) A web-based application for face detection in real-time images and videos. J Phys: Conf Ser 2161:012071. https://doi.org/10.1088/1742-6596/2161/1/012071
Article Google Scholar
Jiang, Andy & Sun, Yu. (2023). A Mobile Application to Mark Attendance using a Combined Backend of the Firestore Database and Amazon AWS Services. 87–98. https://doi.org/10.5121/csit.2023.130108 .
Pichetjamroen, Sasakorn & Rattanalerdnusorn, Ekkachan & Vorakulpipat, Chalee & Pichetjamroen, Achara. (2021). Multi-Factor based Face Validation Attendance System with Contactless Design in Training Event. 637–640. https://doi.org/10.1109/ECTI-CON51831.2021.9454779 .
Asaju, Christine & Vadapalli, Hima. (2021). Affects Analysis: A Temporal Approach to Estimate Students’ Learning. 1–7. https://doi.org/10.1109/IMITEC52926.2021.9714657 .
Mundial, I.Q., ul Hassan, M., Tiwana, M.I., Qureshi, W.S., &Alanazi, E.A. (2020). Towards Facial Recognition Problem in COVID-19 Pandemic. 2020 4rd International Conference on Electrical, Telecommunication and Computer Engineering (ELTICOM), 210–214.
Nursetiawati S, Josua DP, Atmanto D, Oktaviani F, Fardani AL (2020) Science Education in the Family Environment with the Experimental Method of Facial Cosmetics Plant Fertilization in the Covid-19 Pandemic Era. JurnalPendidikan IPA Indonesia 9:561–573
Tseng, F., Cheng, Y., Wang, Y., & Suen, H. (2022). Real-time Facial Expression Recognition via Dense & Squeeze-and-Excitation Blocks. Human-centric Computing and Information Sciences, 12. https://doi.org/10.22967/HCIS.2022.12.039
Awan, S.A., Ali, S., Hussain, I.,., Hassan, B., & Ashfaq Ashraf, S.M. (2021). Proficient Masked Face Recognition Method Using Deep Learning Convolution Neural Network in Covid-19 Pandemic. International Journal of Circuits, Systems and Signal Processing.
Savchenko A, Savchenko LV, Makarov I (2022) Classifying Emotions and Engagement in Online Learning Based on a Single Facial Expression Recognition Neural Network. IEEE Trans Affect Comput 13:2132–2143
Bradford, B., Yesberg, J.A., Jackson, J., & Dawson, P.A. (2020). Live Facial Recognition: Trust and Legitimacy as Predictors of Public Support for Police Use of New Technology. The British Journal of Criminology.
Srinivas, M.A., Kambam, V.R., Pinnu, S.K., Edla, S., &Komera, A.K. (2022). Facial Expression Recognition based Restaurant Scoring System Using Deep Learning. Emperor Journal of Applied Scientific Research.
Rifaee, M.A., Al Rawajbeh, M., AlOkosh, B., &AbdelFattah, F. (2022). A New approach to Recognize Human Face Under Unconstrained Environment. International Journal of Advances in Soft Computing and its Applications.
Enadula, S.M., SriramEnadula, A., &Burri, R.D. (2021). Recognition of Student Emotions in an Online Education System. 2021 Fourth International Conference on Electrical, Computer and Communication Technologies (ICECCT), 1–4.
Recto, I.J., & Devaraj, M. (2022). Synthetic Occluded Masked Face Recognition using Convolutional Neural Networks. 2022 IEEE International Conference on Industry 4.0, Artificial Intelligence, and Communications Technology (IAICT), 124–129.
Sekhar JNC, Domathoti B, Santibanez Gonzalez EDR (2023) Prediction of Battery Remaining Useful Life Using Machine Learning Algorithms. Sustainability 15(21):15283. https://doi.org/10.3390/su152115283
Nurhopipah, A., Rifai Azziz, I., &Suhaman, J. (2022). Behind the Mask: Detection and Recognition Based-on Deep Learning. (Indonesian Journal of Computing and Cybernetics Systems). Vol.16, No.1, pp. 67–78. https://doi.org/10.22146/ijccs.72075
Birkle, J., Weber, R., Möller, K., & Wagner-Hartl *, V. (2022). Psychophysiological Parameters for Emotion recognition – Conception and first evaluation of a measurement environment. Intelligent Human Systems Integration (IHSI 2022). https://doi.org/10.54941/ahfe100958
Gupta, S., Kumar, P., &Tekchandani, R. (2022). Facial emotion recognition based real-time learner engagement detection system in online learning context using deep learning models. Multimedia Tools and Applications, 1 - 30. https://doi.org/10.1007/s11042-022-13558-9
Bhattacharya, Pronaya & Handa, Anand & Zuhair, Mohd. (2021). Face Detection System for Health Care Units Using Raspberry PI. https://doi.org/10.1109/ICIEM51511.2021.9445367 .
Mittal, Parangat & Pandey, Kartikeya & Tawani, Peeyush & Rohilla, Rajesh. (2021). CNN-based Person Recognition System for Masked Faces in a post-pandemic world. 1–6. https://doi.org/10.1109/INCET51464.2021.9456416 .
Hu Y, Jiang Z, Zhu K (2022) An Optimized CNN Model for Engagement Recognition in an E-Learning Environment. Appl Sci 12(16):8007. https://doi.org/10.3390/app12168007
Download references
Acknowledgements
Not Applicable.
Author declared that no funding was received for this Research and Publication.
Author information
Authors and affiliations.
Dept of CSE-AIML, Geethanjali College of Engineering and Technology, JNTUK, Kakinada, Hyderabad, 501301, India
Kosuri Naresh Babu
Dept of IT, Velagapudi Ramakrishna Siddhartha Engineering College, Vijayawada, 520007, India
Suneetha Manne
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Kosuri Naresh Babu .
Ethics declarations
Ethical approval.
This article does not contain any studies with human participant and Animals performed by author.
Conflicts of Interest
The authors declare that there are no conflicts of interest regarding the publication of this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions

About this article
Babu, K.N., Manne, S. A Novel Approach for Accurate Identification in Masked and Unmasked Scenarios using Glowworm Swarm Optimization and Neural Networks. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-20093-2
Download citation
Received : 15 December 2023
Revised : 09 August 2024
Accepted : 14 August 2024
Published : 31 August 2024
DOI : https://doi.org/10.1007/s11042-024-20093-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Facial recognition
- Pandemic environment
- Without masks
- Neural network
Advertisement
- Find a journal
- Publish with us
- Track your research
- Radio Frequency
- Radio Waves
- Radio Communication
- Engineering
- Telecommunications Engineering
- Radio Frequency Identification
THE RFID TECHNOLOGY AND ITS APPLICATIONS: A REVIEW
- September 2012
- 2(3):109-120

- Chandigarh University
- This person is not on ResearchGate, or hasn't claimed this research yet.

- J C Bose University of Science and Technology YMCA Faridabad
Abstract and Figures

Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- S. Chandana
- C. J. Dhanyashree
- K. L. Ashwini

- Int J Antenn Propag

- Xiaojuan Ren

- B V Ramakrishna

- Haijun Zhang
- Chao Ouyang
- Dingding Zuo
- Charusha Chandran

- M. Aiswarya
- Ritika Gupta
- Parth Yadav
- Sanskriti Saxena
- Mohan Singh
- เกียรติศักดิ์ สละยอง
- ฐิติพงษ์ เลิศวิริยะประภา
- กิตติศักดิ์ แพบัว
- อรรถพร คุ้มจินดา
- K. V. Gunalan
- R. A. Sashidhar
- R. Srimathi
- Nithya Venkatesan
- Chandu Vaidya
- Sanket Makode
- Kshitij Mahajan
- Kalpana Bhure
- Muhammad Hasan Shaikh
- Fariha Rubab
- Saifullah Syed Asaad
- Yawar Rehman

- Elisabeth Ilie-Zudor
- Zsolt Kemény

- Anuran Chattaraj

- W. A. THOMAS
- H. A. SPALDING
- ZARKO PAVLOVICH

- Int J Tech Pol Manag

- Benjamin Tueck
- ASSEMBLY AUTOM
- Karen Conneely
- TECHNOVATION

- Fatma Akpinar
- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
Department of Education
From insight to impact with professor christopher cleveland.
Our new "Insight to Impact" series invites faculty from the Education Department to share how their recent research can be applied in practical ways that improve education systems. Here, we look at Professor Cleveland's research papers, "Understanding Individualized Education Program (IEP) Goals at Scale" and "The Effects of Response to Intervention on Disability Identification and Achievement."
The Research
Understanding Individualized Education Program (IEP) Goals at Scale
07/2024 | Annenberg Institute EdWorkingPapers | Christopher Cleveland , Jessica Markham.
Students with disabilities represent 15% of U.S. public school students. Individualized Education Programs (IEPs) inform how students with disabilities experience education. Very little is known about the aspects of IEPs as they are historically paper-based forms. In this study, we develop a coding taxonomy to categorize IEP goals into 10 subjects and 40 skills. We apply the taxonomy to digital IEP records for an entire state to understand the variety of IEP goal subjects and skills prescribed to students with different disabilities. This study highlights the utility of studying digital IEP records for informing practice and policy.
From Insight to Impact
Traditional information captured in state and district administrative data about the experiences of students with disabilities is insufficient to understand the nuances of experiences as further reflected in student IEPs.
States and districts can systematize the collection of IEPs through digital systems or well-managed online PDF systems to integrate with research tools that allow for the synthesis of patterns across IEPs.
The patterns of information identified in different parts of the IEP can be used to inform professional development, support efforts, and compliance.
The Effects of Response to Intervention on Disability Identification and Achievement
08/2024 | Annenberg Institute EdWorkingPapers | Nicholas Ainsworth, Christopher Cleveland , Andrew Penner.
Currently 15 percent of U.S. students receive special education services, a widespread intensive intervention with variable effects on students. Spurred by changes in federal policy, many states and districts have begun adopting the Response to Intervention (RTI) approach to identifying students to receive special education services. RTI seeks to provide a system for targeting interventions to children facing early academic challenges and identifying children with specific learning disabilities (SLD). This paper uses a difference-in-differences design to examine the effects of RTI adoption across Oregon on elementary students’ disability identification and state-standardized achievement test scores. RTI adoption reduced special education identification by 1.4 percentage points (11%) and SLD identification by 0.5 percentage points (15%). RTI also caused moderately large reading test score gains for Black students (0.15 SD) and did not reduce other students’ achievement. These findings suggest RTI is a promising approach to supporting struggling students.
Systematic approaches, such as RTI, can support students’ literacy development and special education identification if implemented with efficacy.
States and districts should collect implementation data on RTI to allow for the evaluation of these efforts
States and districts should be mindful of the resource reallocation and professional development issues that are part of shifting to a new method of educating and identifying students with a disability.
Bibliometric Analysis and Core Target Identification of Network Pharmacology on Neuroinflammation in Cns Disorders: Trends, Collaborations, and Future Directions
39 Pages Posted: 29 Aug 2024
Yifeng Zhang
Shandong Second Medical University
affiliation not provided to SSRN
Weihua Wang
Yanqiang wang.
Purpose: This study aims to evaluate the research landscape of the relationship between neuroinflammatory damage and network pharmacology in neurological diseases over the past 13 years globally. It seeks to identify core targets for treating neuroinflammatory damage using network pharmacology and to analyze the primary research areas and emerging treatment trends.Method: Studies published between January 1, 2012, and May 23, 2024, on neuroinflammation in CNS disorders involving network pharmacological correlates were retrieved from the Web of Science Core Collection. Visualization and scientometric analysis were then performed using CiteSpace and VOSviewer, and the targets identified in the retrieved literature underwent network interaction analysis to screen for the key targets in the treatment of neuroinflammation.Results: A total of 156 papers were included, with the United States, China, and Germany identified as leading research hubs. The top three institutions were Beijing University of Chinese Medicine, Case Western Reserve University, and the University System of Ohio. "Nucleic Acids Research" was the most frequently cited journal, while the "Journal of Ethnopharmacology" published the most papers. Co-occurrence analysis revealed 13 major clusters, including apoptosis, Panax notoginseng, dihydrochalcones, quercetin, KV1.3, systems biology, microarray analysis, neuropathic pain, network medicine, cholinergic system, different proportions compatibility, AGE-RAGE signaling pathway, and traumatic brain injury. STAT3, JUN, AKT1, TP53, ESR1, SRC, RELA, NFKB1, CREB1, MAPK1, IL6, CTNNB1, EGFR, MAPK3, BCL2, PIK3CA, TNF, IL1B, PIK3R1, EP300, and MAPK8 are among neuroinflammation involved in central nervous system disorders 21 core targets involved in network pharmacology.Conclusion: The study indicates that the number of publications in this field is likely to continue increasing over the next decade. Future research trends are shifting away from the traditional "one drug, one target, one disease" model towards the study of "multi-target drugs" for neuroinflammation in central nervous system disorders. This shift is crucial for achieving clinical precision and efficient treatment.
Note: Funding Declaration: This work was supported by Yuan Du Scholars, Affiliated Hospital of Shandong Second Medical University Horizontal Project (WYFYKY-HX202307, 202201), National Natural Science Foundation of China (81870943), Health China•BuChang ZhiYuan Public welfare projects for heart and brain health under Grant No.HIGHER2023072, Shandong Second Medical University Affiliated Hospital Technology Development Project (2023FYM001, 2023FYM006). Conflict of Interests: None.
Keywords: Neuroinflammation 1, Core Target 2, Bibliometric Analysis 3, Network Pharmacology 4, Precision treatment 5
Suggested Citation: Suggested Citation
Shandong Second Medical University ( email )
Weifang China
affiliation not provided to SSRN ( email )
No Address Available
Yanqiang Wang (Contact Author)
Do you have a job opening that you would like to promote on ssrn, paper statistics, related ejournals, data science, data analytics & informatics ejournal.
Subscribe to this fee journal for more curated articles on this topic
Neurology eJournal
Subscribe to this free journal for more curated articles on this topic
Pharmacology & Toxicology eJournal
- Skip to main content
- Skip to search
- Skip to footer
Products and Services

CCNP Enterprise certification
Demonstrate your expertise in enterprise infrastructure, assurance, security, and more. Configure, troubleshoot, and manage the networks of the largest companies in the world with the Cisco Certified Network Professional (CCNP) Enterprise certification.
Empower the world's biggest networks

CCNP Enterprise
Earning a CCNP Enterprise certification demonstrates your ability to scale and maintain enterprise networks to meet growing demands. Showcase your expertise in enterprise infrastructure, virtualization, assurance, security, and automation to influential employers.
Dual stack architecture
Understand Cisco's solutions for managing networks, including configuring the quality of service settings, and switching between hardware and software.
Virtualization
Demonstrate your understanding of virtualization software, virtual machines, and virtual switches. Showcase your ability to divide and manage data paths and create virtual networks.
Infrastructure
Set up and troubleshoot communication protocols. Set up wireless networks and configure features like network time protocol and Network Address Translation/Port Address Translation (NAT/PAT).
Network assurance
Be able to diagnose and fix network problems. Configure and verify various networking features for optimal performance.
How it works
No formal prerequisites.
Learners often have three to five years of experience implementing enterprise network solutions.
Common learner profiles
Professional-level certifications expand on the foundations of associate-level certifications. They cover more advanced topics and allow candidates to hone in on a specific focus area of their choice. Many professional-level certification candidates are looking to prove they’re the best of the best in a specialized field.

Getting started
To earn this certification, you'll need to pass two exams:
- A core exam
- One of seven CCNP Enterprise concentration exams
You'll have access to many resources — from guided learning to self-study and a community forum — that are designed to help you pass your exams.

Unlock your career potential
Your CCNP Enterprise certification proves you can work with complex IT infrastructures - and that opens doors at some of the world’s largest companies.
Potential roles
Network automation engineer.
Use programming and automation tools to streamline network operations.
Systems engineer
Be the expert behind any project that optimizes systems for an organization.
Network support technician
Resolve connectivity issues, troubleshoot devices, and ensure networks are operating smoothly.
Alumni testimonials
Certifications give olivia credibility with employers.

"The knowledge that I’ve got from studying for those certifications gave me the confidence that I’ll always be able to get a job if I need to."
Olivia Wolf, Systems engineer
CCNA, CCNP Enterprise, DevNet Associate
Christoph's certifications earned him a salary boost

"Preparing for certification increased my knowledge and confidence, which ultimately translated to better work performance. As a result, I’ve received generous salary increases."
Christoph Neulinger, Senior network engineer
Getting certified has been a game-changer for AJ

"Cisco Certifications really helped to advance my career."
AJ Murray, Network engineer
Maintain your certification
Your certification is valid for three years. You can renew with Continuing Education credits or retake exams before they expire.
Professional-level Essentials Event: Enterprise
Watch our expert’s guidance and advice on planning your path towards your CCNP Enterprise certification success.
CCNP Enterprise summary
Get a quick primer on the CCNP Enterprise certification and exams.
The CCNP story
Learn why we created the CCNP certifications, and find out how you can use them to plan, support, and grow your career.
Enhance your learning journey
Stay up to date.
Get the latest news about Cisco certifications, plus tools and insights to help you get where you want to go.
Enterprise certifications community
Not sure where to begin? Head to the Cisco Enterprise certifications community to get advice and connect with experts.

IMAGES
VIDEO
COMMENTS
PDF | History, Basics, Development, Applications, Recent Improvements and Analysis of Automatic Identification System (AIS) | Find, read and cite all the research you need on ResearchGate
In the fifth paper titled 'From national to sector level biometric systems: the case of Ghana,' John Effah and Emmanuel Owosu-Oware focus on biometric identification systems, observing that research has focused on systems that are national or sectoral (relating to healthcare, voting, or other types of functional applications), but limited ...
Abstract. Technologies and services towards smart-vehicles and Intelligent-Transportation-Systems (ITS), continues to revolutionize many aspects of human life. This paper presents a detailed survey of current techniques and advancements in Automatic-Number-Plate-Recognition (ANPR) systems, with a comprehensive performance comparison of various ...
The Integrated Automated Fingerprint Identification System ... He is also the Founder of the popular SPMF open-source data mining library, which has been cited in over 430 research papers since 2010. He has published over 140 research papers in refereed international conferences and journals, which have received over 1,300 citations. ...
In this paper, we will present and early implementation of a system for cloud-based object recog-nition. The primary use of the system is to provide an object recognition as a ser-vice for a wide ...
Organizations should manage patient identification systems as an ongoing process, from front-end ... Research on health information systems is defined as an interdisciplinary ... the hypotheses. Data were collected in Neioumazloum Hospital over two consecutive years (2016-2017) to study the old-paper-based system and a further two years (2018 ...
Conventionally, the identification of users is performed using passwords and PIN numbers. However, due to the rapid changes in technology, these security measure's abuse and theft are also increasing. This led to the birth of the biometric security system, in which the identity verification of individuals is performed based on the feature vectors, which are derived from the physiological and ...
1. Introduction. System identification - to estimate models of dynamical systems from observed input-output data - has been around for more than half a century, with the term coined in Zadeh (Citation 1956).Many articles and textbooks on the topic have been written, e.g. Ljung (Citation 1999), Söderström and Stoica (Citation 1983) and Pintelon and Schoukens (Citation 2001).
Face recognition system based on PCA and feedforward neural networks. Face recognition is one of the most important image processing research topics which is widely used in personal identification, verification and security applications. In this paper, a face recognition system, based on the principal... more. Download.
Deep networks for system identification: a Survey. Gianluigi Pillonetto, Aleksandr Aravkin, Daniel Gedon, Lennart Ljung, Antônio H. Ribeiro, Thomas B. Schön. View a PDF of the paper titled Deep networks for system identification: a Survey, by Gianluigi Pillonetto and 5 other authors. Deep learning is a topic of considerable current interest.
System identification describes a set of methods, which uses experimental input/output data from a system, in order to identify its dynamical properties. Depending on the class of systems under ...
In this paper, System Identification is accomplished using various adaptive filters. System Identification is the one which is used in identifying the unknown model of a system and it is the mathematical modeling of the plant or process. ... NLMS and RLS. In: IEEE student conference on research and development (SCOReD), 16-17 Dec 2013. Google ...
IJCRT2401113 International Journal of Creative Research Thoughts (IJCRT) www.ijcrt.org a877 FACE DETECTION AND RECOGNITION FOR CRIMINAL IDENTIFICATION SYSTEM 1Prof. Kiran Yesugade, 2Apurva Pongade, 3Shruti Karad, 4Divya Ingale, 5Shravani Mahabare 1Professor, 2 Student, 3 4 ... This paper introduces a new way of identifying potential criminals ...
Abstract. This paper presents a survey of a number of techniques for the identification of dynamic systems using computer techniques. The techniques discussed are particularly suited to digital or hybrid computer implementation. It is not intended to be a complete survey of the vast field of system identification, nor even the area of parameter ...
In criminal identification, face detection and recognition are used to identify suspects and match them to surveillance footage or images from crime scenes. ... Published in: 2023 8th International Conference on Communication and Electronics Systems (ICCES) Article #: Date of Conference: 01-03 June 2023 Date Added to IEEE Xplore: 01 August 2023 ...
In this paper, an automatic bird species recognition system has been developed and methods for their identification has been investigated. Automatic identification of bird sounds without physical intervention has been a formidable and onerous endeavor for significant research on the taxonomy and various other sub fields of ornithology. In this paper, a two-stage identification process is ...
An Introductory Example. System identification is the theory and art of estimating models of dynamical systems, based on observed inputs and outputs. Consider as a concrete example the Swedish aircraft fighter Gripen; see Fig. 1. From one of the earlier test flights, some data were recorded as depicted in Fig. 2 .
Abstract. This paper focuses on developing a deep learning-based system for spoken language identification (SLID). Through the utilization of state-ofthe-art deep learning techniques, a robust model capable of accurately distinguishing spoken languages from audio inputs is developed.
Plant diseases affect the growth of their respective species, therefore their early identification is very important. Many Machine Learning (ML) models have been employed for the detection and classification of plant diseases but, after the advancements in a subset of ML, that is, Deep Learning (DL), this area of research appears to have great potential in terms of increased accuracy.
The results will shows about 90% of input photo will be matched with the stored data. This paper is to propose the criminal face identification system in which the images stored in the database will be matched to the image stored in another database to find out the criminals. Download Free PDF.
Recognition and classification are among the most important applications of machine learning. This recognition process is used to identify objects and humans. In particular, it plays a major role in authentication processes by identifying features such as human eyes, fingerprints, and facial patterns. Among these features, facial recognition is an evolving technology used in smartphones ...
Radio Fre quency Identification (RFID) is a generic term for technologies that use radio waves. to automatically identify people or objects from a distance of several inches to hundreds of feet ...
Our new "Insight to Impact" series invites faculty from the Education Department to share how their recent research can be applied in practical ways that improve education systems. Here, we look at Professor Cleveland's research papers, "Understanding Individualized Education Program (IEP) Goals at Scale" and "The Effects of Response to Intervention on Disability Identification and Achievement."
Future research trends are shifting away from the traditional "one drug, one target, one disease" model towards the study of "multi-target drugs" for neuroinflammation in central nervous system disorders. This shift is crucial for achieving clinical precision and efficient treatment.
Use the small, powerful Cisco Catalyst and Meraki campus LAN compact switches to extend enterprise-class services to wherever you want, far from the wiring closet.
This paper presents a two-dimensional analytical model to study contaminant transport in the cut-off wall and aquitard system, considering advection, dispersion and adsorption processes. These processes were coupled by the continuity of contaminant mass fluxes and concentration the interface between the cut-off wall and aquitard.
In this paper, We developed a novel ECL sensor of the 6-MC/S 2 O 8 2− system by using 2-NSA as co-reaction accelerator. 2-NSA was first proposed as co-reaction accelerator, promoting the generation of additional oxidant SO 4 − from S 2 O 8 2−, thus amplifying the ECL signal. Moreover, this research provides a highly sensitive platform for ...
Assembling such a global stocktake of effective climate policy interventions is so far hampered by two main obstacles: First, even though there is a plethora of data on legislative frameworks and pledged national emission reductions (8-10), systematic and cross-nationally comparable data about the specific types and mixes of implemented policy instruments are lacking.
"Center of Election Innovation and Research" executive director David Becker speaks about threats to election integrity, Sunday on CBS's "Face The Nation." NANCY CORDES, CBS NEWS: Give us a lay of ...
Olivia Wolf, Systems engineer. CCNA, CCNP Enterprise, DevNet Associate. View Olivia's story. Christoph's certifications earned him a salary boost "Preparing for certification increased my knowledge and confidence, which ultimately translated to better work performance. As a result, I've received generous salary increases."