- Request Demo

What To Include In Your Cybersecurity Board Of Directors Presentation
Executive reporting.

Most Boards today know that cybersecurity is a critical issue that simply cannot be overlooked — which means many Boards today receive regular briefings on the topic. If you’re a new CIO or CISO (or your organization has just begun this practice) it’s absolutely critical that you establish credibility when you present to your Board of Directors. If you’ve been asked to present and you’ve never briefed a Board of Directors on cybersecurity before, your questions are going to be far different than they would be if you had seven or eight presentations under your belt. So below, we’ve detailed some of the topics you should include in your cybersecurity Board of Directors presentations — for both first timers and seasoned presenters.
First-Time Cybersecurity Board Of Directors Presentation
If this is your first presentation to the Board, your goal should be to provide a very high-level overview. You’ll want to give a short background on cybersecurity, what it means, and why you (and your department) should be concerned. It’s extremely important to speak in a language that the Board can understand — which means cutting out any technical jargon . Instead, talk in terms of risk management, stock price, and bottom line.
Below are some of the topics you may want to cover in your first presentation:
- A high-level overview of different threat actors.
- How you generally approach cybersecurity: Who is in charge, how you work together, what the components are, etc.
- Risks to your cybersecurity environment (i.e., the things you’re concerned about).
- The type of data you think is most critical or sensitive.
- The types of critical operations that could be impacted by a cyber incident.
- Examples of cyber incidents that have occurred in other organizations in our sector.
- Examples of other cyber incidents that have impacted organizations more broadly that you should be aware of.
- How you think the Board members should be involved and where the Board comes into play.
- What you anticipate presenting to the Board in the future.
- The programs you have in place for cybersecurity from a strategy and technology approach.
- How you train your employees on cybersecurity.
- The cybersecurity policies you have in place today and those you’d still like to integrate.
- How you use your systems and how you know what data to collect on.
- Some of the key external threats, insider threats, and third-party risks you believe you face.
Related: Boards need more information about cybersecurity than ever before. Can you present it effectively?
Ongoing cybersecurity board of directors presentations.
Now that you’ve completed your first cybersecurity presentation to the Board of Directors, your goal should be to continuously educate the Board on critical issues. This means your focus for these presentations should shift, as the Board should be briefed on the effectiveness of the risk management tactics you’re employing. In other words, the Board should know where you are succeeding, how you are succeeding, and any areas that need strategic improvement.
Here are some topics you should focus on in your ongoing presentations to the Board:
- Technology you’ve purchased and integrated—with a focus on what it is doing for the organization.
- Technology you want to purchase and why you want to purchase it.
- “Are we ISO-27001-compliant?”
- “Do we have a vendor risk management program?”
- “Do we have any outstanding high-risk findings open from our last audit or assessment?”
- “What percentage of the NIST framework are we implementing?”
- “How quickly can we remove employee network access?”
- “How quickly can we (or our vendors) identify and respond to incidents?”
- “What percentage of our users click on spear-phishing training emails?”
- “How did we compare to our peers across certain time spans?”
- Audit & Compliance Metrics
- Operational Effectiveness Metrics
Knowing the right point to brief the Board on is critical — but there’s much more to an effective cybersecurity Board of Directors presentation. Download our ebook to learn how to take a risk-based approach to cybersecurity reporting.
A Practical Guide to Risk-Based Cybersecurity Reporting

Learn how to revolutionize the reporting process at every level of your organization.
Get the Weekly Cybersecurity Newsletter
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

12 tips for effectively presenting cybersecurity to the board
Don't let your board presentation miss the mark. follow these best practices and common mistakes to avoid when communicating cybersecurity risk to the board..

Cybersecurity is a top concern for boards of directors.
In fact, 42% of the nearly 500 leaders surveyed by the National Association of Corporate Directors listed cybersecurity risks as one of the five most pressing concerns they’re facing — just behind changes in the regulatory climate and an economic slowdown.
As a result, security executives are increasingly going before boards to brief them on the risks they face and strategies to mitigate them.
“More boards are saying, ‘Talk to us, tell us what we need to know,’” says Gary Hayslip, CISO of internet security company Webroot and a veteran board member.
Yet, many board members find that they’re not getting the information they need from their chief information security officers.
“Board members are talking about cyber risk, and risk and audit committees are spending a lot of time grilling the CISOs, and they’re generally dissatisfied with the experience,” says David Chinn, a senior partner with management consulting firm McKinsey & Co.
There are steps that CISOs can take to avoid such negative reviews. Here, several experienced leaders share their advice for presenting to the board:
1. Do more prep work
Executives are expected to prepare written reports for distribution to board members in the weeks ahead of presenting to the board in person. Some think that advance work is enough, but experienced executives and leadership advisors say CISOs (especially those with limited time before boards) need to do more focused prep work or even receive specific training.
Before Hayslip presented to a new board for the first time, he asked his CFO to connect him with a director who would be willing to help him prepare for his presentation. “If I’m going to report to the board and I have never spoken to them before, I don’t want to come into that boardroom cold. I don’t know what kind of questions they’ll ask. I don’t know what they want to know. So I’ll talk to my peers, ask other executives who report to the board and get their feedback — who is there, what are they like, what questions they ask — so I’ll know who I’m going to talk to and how they like to have data presented,” he says.
2. Offer an assessment
Hayslip says that prep work along with his subsequent experiences presenting to boards has taught him something about what directors want to know — that is, an assessment of the company’s cybersecurity posture and how it needs to improve.
“Tell them where you are and where you need to be. And every time you come in, you share information about new risks and new opportunities to improve, building on the information presented in the prior [presentation],” he says. “Tell them, this is where we’re at, here’s where we’re immature and where the risks are, and from a threat profile this is what we should be prioritizing and why … and where we stand against competitors.”
3. Be transparent
Assessments shouldn’t obfuscate the risks to the enterprise, experts say, so CISOs should be upfront and present relevant information in a straightforward, accessible manner.
“Many organizations have a threat intelligence department, and they’re packaging up that information for the board so board members feel like they’re in the know,” says Chinn. “Board members want to know the enterprise risk, the business impact of that risk, to what extent their investments have turned into controls and whether it yielded a meaningful reduction in risk.”
He cites as a strong example of how to offer such information one organization where the CISO implemented a self-service application that board members could use to access that information on demand.
4. Anticipate the (tricky) questions
The boardroom is no place for surprises. So Rob Clyde, chair of the board of directors with IT governance association ISACA, advises CISOs to anticipate the questions they’ll get from board members — particularly the questions that are most difficult to answer, such as “How good is our security?” and “Are we safe?”
CISOs often struggle to appropriately answer those types of questions and as a result tend to provide inadequate or confusing responses when answering on the fly, Clyde says.
He advises CISOs to think ahead and develop go-to responses. He also recommends CISOs use a cybersecurity maturity framework, such as the one offered by ISACA’s CMMI Institute, to offer an articulate, insightful response to those tricky questions.
Similarly, he says CISOs shouldn’t surprise the board, other executives and the CEO with their responses to such questions. Clyde says CISOs should share their responses to the anticipated questions with their CEOs; in fact, CISOs should be sure that their CEOs are briefed on any information they’ll present so they’re not putting their CEOs in any awkward situations.
5. Be honest about limits
On a related note, experienced executives says CISOs should be realistic when responding to questions about organizational risk and cybersecurity posture — even if they fear their responses might make them look ineffective. “Some boards will ask, ‘Are we 100 percent secure?’ You should never answer in the affirmative or answer it inaccurately by giving unfounded assurances,” Clyde says.
6. But don’t scare the board either
CISOs see the growing volume and increasing sophistication of cybersecurity attacks , so it’s not surprising they seek to share such information with their boards while explaining the resources they need to counteract all those threats.
“You have some CISOs who go in and list all the bad things that are happening and make it seem like the sky is falling,” Hayslip says, “but that [climate of] fear, uncertainly and doubt doesn’t really work for the board, and a CISO might get away with it once but all he’s going to do is tick off the board if he does it again.”
Boards certainly want data, he says, but they want that information in ways that allow them to make informed decisions about where to best place their security investments to mitigate their greatest risks.
7. Get a champion
James Carder, CISO of security solutions company LogRhythm, cultivated a relationship with a board member who had a technical background and sought him out as a mentor who could help him prepare for board meetings, review material being submitted to the board, and advocate for security strategies on his behalf.
He advises other CISOs to do the same.
“Get a champion on the board. They’ll give you feedback before you present to the board, [advising on] what words are important and what will resonate with the rest of the members. And that champion can have the conversations on security with the board when you’re not there and drive the changes you want,” Carder says.
8. Get to the point
CISOs are used to presentations at conferences where there’s a buildup to the main point, but that kind of approach doesn’t work well for boards that put a premium on time.
“Don’t hold the punchline. Get to the point right from the start. The board wants to know up front why you’re there,” Clyde says. “And if there’s something the board needs to take action on — for example, they need to consider buying cybersecurity insurance or figure out a policy on whether to pay ransom if there’s a ransomware attack — identify that and identify that right up front.”
He says CISOs can provide supporting information as time allows, realizing that the board members can access any needed information in the written material submitted in advance of the meeting.
9. Skip the tech talk
Carder says he once over-communicated his security work to the board, a mistake he knew he made when board members repeatedly had to stop his presentation to ask about the terms he was using used and concepts he was describing.
“I assumed they knew certain security tech terminology,” he says, “and then I realized that I was over-communicating all these details vs. being concise and communicating the risks.”
Carder is now more conscious of leaving deeply technical information out of his presentation; there are no details about the latest exploits or the newest data loss prevention technologies or choice SIEM vendors or intrusion detection products. Instead, he focuses the conversation on high-level points around security and presents the information in plain business terms.
10. Present the business value
Many CISOs have trouble calculating the business ROI of their security investments, yet what boards want to know is the business impact of their security risks and investments.
That’s what Hayslip aims to deliver. “I show how my programs impact teams that make money; it’s showing how we’re helping them do what they do,” he says.
He once worked at a company that had some 50 machines taken offline each month due to malware , so he invested in technologies to reduce that monthly average. When he went before the board, Hayslip didn’t focus on the cost of the new technologies but rather in the value that investment brought to the organization through lower remediation costs and reduced downtime.
“That’s the kind of value story you have to talk about, plus the fact you’re reducing risk,” he says.
11. Determine measures of success
CISOs should reflect on whether they’re adequately conveying information to their boards, knowing that how well they’re communicating the business impacts of their security strategies correlates with how much support and funding they’ll get for their security strategy, Chinn says.
Chinn knows one CISO who judged his success in this area by how his board members react when corporate data breaches make the news.
“He says he knows he’s doing a good job informing the board when board members ask intelligent questions or no questions at all after news of a breach, because it shows they trust him as CISO,” Chinn says.
12. Capitalize on the opportunity
CISOs should present to the full board, Clyde says, noting that many CISOs present not to the full boards of directors but to audit and risk committees. And they should take the initiative to get on their boards’ agendas if they’re not already.
Moreover, CISOs should see their time in front of boards as opportunities to evangelize on the importance of a strong cybersecurity program as well as to educate on the strengths, gaps and strategies of the organization’s cybersecurity function. ISACA recommends that CISOs meet with their boards at least once a year, Clyde says.
“It’s about building up trust,” Hayslip says. “The board can see you’re getting things done, and they know not only that you know your job but that you understand the business, and you’re aligning your security program to support that.”
Related content
Boost security and control at every stage of the cloud application lifecycle, ciso budget survey: modest increases in 2024, white house brands bgp routing a ‘national security concern’ as it unveils reform roadmap, attackers are exploiting vulnerabilities at a record pace—here’s what to do about it, from our editors straight to your inbox.

Mary K. Pratt is a freelance writer based in Massachusetts.
More from this author
6 things hackers know that they don’t want security pros to know that they know, the cyber assault on healthcare: what the change healthcare breach reveals, better metrics can show how cybersecurity drives business success, fake network traffic is on the rise — here’s how to counter it, ai poisoning is a growing threat — is your security regime ready, the rise in ciso job dissatisfaction – what’s wrong and how can it be fixed, 6 best practices for third-party risk management, was ist zero trust, show me more, two weeks on from pavel durov's arrest, telegram ramps up moderation of ‘illegal content’.

New malicious MS Office macro clusters discovered

Adobe evolves its risk management strategy with homegrown framework

CSO Executive Sessions: Guardians of the Games - How to keep the Olympics and other major events cyber safe

CSO Executive Session India with Dr Susil Kumar Meher, Head Health IT, AIIMS (New Delhi)

CSO Executive Session India with Charanjit Bhatia, Head of Cybersecurity, COE, Bata Brands

CSO Executive Sessions: Hong Kong Baptist University’s Allan Wong on security leadership

CSO Executive Sessions: EDOTCO’s Mohammad Firdaus Juhari on safeguarding critical infrastructure in the telecommunications industry

Sponsored Links
- Visibility, monitoring, analytics. See Cisco SD-WAN in a live demo.
- OpenText Financial Services Summit 2024 in New York City!

Don’t Bore the Board: 5 CISO Hacks for Highly Effective Presentations

Several years ago, we invited board members to speak candidly about presentations from company executives. Those free-flowing conversation more than lived up to what was billed as a “Don’t Bore the Board” panel discussion. The panel members’ engaging insights remain instructive to chief information security officers (CISOs) today as security leaders strive to hone their increasingly important board presentation approaches.
One corporate director confided that he paid less attention to the technical aspects of the CISO’s presentation, and instead scrutinized his CISO’s demeanor during presentations to obtain a gut-feel sense of the CISO’s confidence in his own ability to manage security risks. Another board member stressed that she focused nearly all her attention during CISO presentations on the information pertaining to the security budget.
As these forthright comments accumulated, it became clear that developing an understanding of the unique personality traits of individual directors, and the board as a whole, marked a crucial determinant of board-presentation success.
There is an increasing requirement for CISOs to engage in meaningful conversations with the board. Given the high-profile breaches in the news month after month, and the acknowledgement of most organizations that cyber risks are a key enterprise risk to be managed, there is no absence of interest or attention. CISOs must leverage these opportunities to provide transparency on the current state of security with their organization, as well as communicate budget, staffing and key decisions that will impact the direction going forward.
One of the most effective ways to improve board presentations is by discussing what works and what doesn’t with fellow C-suite presenters. CFOs, CIOs, chief risk officers and chief audit executives will have discerning observations about the board’s preferences regarding reports, slide decks, follow-up protocols and more. It can also be highly effective to present with a peer on occasion. We’ve seen CISOs and compliance officers speak to the board together to paint a vivid picture of cybersecurity, providing complementary perspectives that show collaboration on the topic. We’ve also joined CISOs during board presentations – providing external insights on industry cybersecurity risks and sharing relevant benchmarks. These approaches often result in a more conversational discussion, which enables the board to understand and actively engage in the conversation.
While each CISO has their own style and approach to communicating with the board, here are some common elements we observe from those that do so well:
- Know the audience: Each board has a unique personality. Its identifying characteristics relate to how the members consume and process information – and may consist of wanting comprehensive supporting details, avoiding technical descriptions and jargon, not wanting detailed supporting evidence, or even adhering to a hard limit on the number of slides included in a deck. To help ensure that communication styles are in harmony, determine if there are security-savvy board members, monitor when new members join the board and learn how subcommittees are structured to facilitate consistent reporting across related governance areas (e.g., risk and audit committees). Whenever possible, spend one-on-one time with directors, and especially committee members, during breaks, meals and informal interactions. Those chats provide a chance to solicit candid feedback and should enrich your knowledge of their backgrounds and preferences.
- Understand the broader context and speak in business terms: Many CISOs understandably struggle to frame their discussions in business terms. It’s natural to lean on the technical aspects of information security when discussing risks in a high-pressure setting. To avoid the pitfall of venturing too far down the technical path, prepare for presentations by addressing a list of business questions first and then considering how those dynamics affect cybersecurity: Is business performance up or down? How is information security affected by current business performance? How does security relate to key business initiatives?
- Introduction and key themes
- Progress toward “target state” security maturity (or tracking of the security road map)
- Top risks, with relevant key risk indicators (KRIs) and metrics
- Emerging risks and industry trends
- Incidents and other notable events
- Open discussion
- Select the right metrics: This is another pivotal board reporting component that’s ripe for misjudgment. Bypass overly technical and activity-centered measures (e.g., we created 1,200 accounts per month to support our access provisioning process) in favor of metrics that illustrate your performance in managing the company’s most relevant data security risks. (A side note: Protiviti’s Cyber Risk Quantification (CRQ) methodology provides insights for metric quantification.) If ransomware concerns are a top security concern, find KRIs that assess those threats. If malicious insider activity is a key risk, find metrics that reflect your organization’s progress in alleviating that problem. Keep in mind the powerful nature of industry spending benchmarks.
- Get in front of incidents: While more board members recognize the inevitable nature of security breaches, CISOs should tactfully discuss breaches to continually familiarize the board with the risk as well as incident response strategies and procedures. Discuss recent public breaches and explain how a similar attack would be managed within your organization. Highlight the range of potential outcomes of an event and how the organization would take steps to minimize the impact. Also, consider talking about near misses within the organization – a sensitive topic, but one that can deliver an eye-opening educational experience to board members.
Above all, CISOs should put themselves in the minds of their board members: What do they want to know and learn when they’re listening to me? Corporate directors want useful information that helps them fulfill their fiduciary responsibility to provide governance and oversight of the organization. The CISO should be well-prepared to meet these expectations with insightful, relevant communications that the board will value.
To learn more about our CISO Next initiative , contact us . Also, read related posts on The Protiviti View .
Share this:
Add comment, cancel reply.
Subscribe Now
- Protiviti Technology Insights
- Protiviti SAP blog
- Robert Half Finance & Accounting blog
- Robert Half Technology blog
- AuditBeacon.com
Related Posts
- Harnessing Operational Excellence: A Path to Enhanced Legal Department Services in the Energy and Utilities Sector
- How Telcos Can Manage Rising Third-Party Risks
- The SEC’s Cyber Disclosure Rules: Lessons Learned So Far In Year One
- Manufacturers Can Build Resilience With AI-Powered Crisis Simulations
- The Quantum Race Is On – What Does It Mean for Governments and Their Top Secrets?
- Leveraging AI In Finance—Move From Theory To Practice
Subscribe to blog
- Digital Transformation
- Technology and Cyber Security
- Risk Management
- Regulatory Compliance
- Finance/Internal Audit
- Business Performance Improvement
- Organizational Perspectives
- Data and Analytics
- Technology, Media and Telecommunications (TMT)
- Manufacturing & Distribution
- Energy & Utilities
- Consumer Products & Services
- Financial Services
BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
How to create a cybersecurity board report (3 best practices).

Edward Kost
Your board of directors expects to be regularly updated about your data breach prevention efforts, but board members often lack the necessary technical insight to understand the cyber risk mitigation processes making up your cybersecurity posture. CISOs are tasked with bridging the gap between awareness of your organization’s security efforts and stakeholder KPIs with the support of an invaluable tool - a cybersecurity board report.
This post outlines three best practices for creating a cybersecurity board report that effectively represents the efficacy of your cybersecurity strategy.
Learn how UpGuard simplifies Vendor Risk Management >
Best Practice 1: Understand the Structure of a Board Report
There isn’t a set cyber board report structure that needs to be followed. In fact, obsessing too much over the report’s structure increases the risk of not meeting the board-level requirement. A better approach is to think in terms of broad stakeholder metrics. Understand the primary areas your board members are concerned about, and structure your report to address them.
Don’t overcomplicate the design of your cybersecurity board report. Keep it simple, straightforward, and concise.
The most basic structure of a cyber board report consists of three parts - cyber risk outlook, business strategy outlook, and operations outlook, the three primary variables of business success or failure.

Following this simple structure will make your report adaptable to your reporting objectives while also covering the broadest scope of board member concerns in terms of cybersecurity.
1. Cyber Risk Outlook
This section overviews the organization’s current risk exposure across internal and third-party attack surfaces. It’s imperative also to cover third-party vendor risk exposures since exploited third-party vulnerabilities account for almost 60% of data breaches.
Not covering third-party risk exposure in your board report communicates to board members that you don’t fully understand the cybersecurity risks contributing to data breaches.
The cyber risk reporting component should address the following information:
- Your organization’s most critical security risks and their respective remediation efforts (security controls).
- The effectiveness of your cybersecurity framework’s efforts in ensuring vendor cyber risks remain within risk tolerance and risk appetite limits.
- Details of any significant cybersecurity incidents and associated incident responses since the last reporting period. Including details of their business impact and resulting degree of reputational damage.
- The initiatives being prioritized to mitigate dangerous cyber attacks and cyber threats topping the list of board member concerns, such as ransomware and phishing attacks.
- An overview of your organization’s overall cybersecurity performance represented by benchmarking against your industry average and competitor’s efforts.
- Risk management performance overview (including Vendor Risk Management (VRM), Third-Party Risk Management, etc.).
- How your security teams are tracking against corporate cybersecurity metrics.
- Risk assessment and patching efforts that were undertaken as a response to unexpected threat landscape disruptions, such as zero-day vulnerabilities and hackers compromising third-party service information security.
Don’t conflate the comprehensive nature of this list with a need to make the cyber risk outlook section of your report lengthy. With the exception of the CIO, most board members are not technically minded, so demonstrating alignment with NIST CSF likely won’t impress them.
The best hack for communicating complex cybersecurity concepts as concisely as possible is to use visuals. Graphics eradicate the need for long-winded explanations, making your presentation easier for board members to follow while referencing the report.
To demonstrate how the communication of detailed cybersecurity efforts can be significantly simplified, here are a few examples of visuals mapping to some of the cyber risk reporting items in the list above.
Cybersecurity Performance Benchmarking Against Industry Average and Top Competitors.

Overview of Security Risk Criticality Distribution Across Four Primary Attack Vector Categories

Vendor Risk Overview Across Five Risk Categories

Vendor Risk Management Performance Overview

Learn more about UpGuard’s reporting features >
2. Business Strategy Outlook
The strategic outlook component outlines how your cybersecurity program will adapt to new business risks in the evolving threat landscape.
These could include:
- New cyber threats changing your cybersecurity priorities, such as a rise in ransomware attacks triggering a revision of your current ransomware defense strategy .
- Risks preventing the achievement of business objectives, like a critical third-party vendor’s security posture falling below acceptable levels.
- An increased likelihood of suffering a supply chain attack , like when a fourth-party vendor is breached .
- New regulations or executive orders mandating specific security controls, like Multi-Factor Authentication (MFA).
Learn how to create a cyber report for senior management >
3. Operations Outlook
The operations outlook section dives deeper into the performance of risk management frameworks ( VRM , TPRM , etc . ) and compliance efforts against relevant regulations.
Operational performance can be summarised with maturity models or by demonstrating adherence to Key Performance Indicators.
Platforms like UpGuard simplify the complicated processes of collecting evidence of regulation and framework alignment for board reports and meetings. Watch the video below for an overview of how easy it can be.
Get a free trial of UpGuard >
Best Practice 2: Express Impact in Financial Terms
If you want your cyber board report to be effective, it needs to speak a language all board members, regardless of where they are situated in the world - money.
Even with visuals concisely representing risk information, board members will only truly appreciate your cyber risk mitigation effort when its impact is quantified in dollars.
You should already have outlined some semblance of a Cyber Risk Qaunatifacion process while calculating your risk appetite .
Learn about Cyber Risk Quantification (CRQ) >
CRQ methods can be used to justify new cybersecurity investments in this report by demonstrating the likely financial impact of critical assets being compromised.

Learn how to write the executive summary of a cyber report >

Best Practice 3: Don’t Use Cyber Jargon
Board members are not equipped to interpret cybersecurity complexities. That’s why you have a CISO and a cybersecurity reporting tool in place .
As a cybersecurity professional, you must suppress your proclivity towards technical explanations in the board report. A trick to keeping your report palatable for the average non-techie is to take advantage of every opportunity to express concepts in visuals and numbers.
Numbers and visual elements are your best friends in a cyber board report.
Security ratings are invaluable in this area, representing a concept as advanced as your organization’s cybersecurity posture as a single number value.
Security ratings are calculated with a complicated algorithm considering the impact of multiple critical attack vectors, with the final quantified value represented as a rating ranging from 0 to 950 (the maximum cybersecurity rating).
Learn how to create a vendor risk summary report >

Learn more about UpGuard’s security ratings >
In a board report, security ratings can be used to benchmark your organization’s cyber performance against industry standards and also represent the efficacy of your cybersecurity efforts over time - information that’s very valuable in a boardroom setting.

Cybersecurity Board Reporting by UpGuard
UpGuard’s cyber report generation feature allows you to create a report optimized to meet the primary reporting expectations of board members in just one click. Once generated, Board summary reports can be exported into editable PowerPoint slides to also remove the stress of preparing your board report presentation.

Reviewed by

Kaushik Sen
Ready to see upguard in action, ready to save time and streamline your trust management process, join 27,000+ cybersecurity newsletter subscribers.
Related posts
The top cybersecurity websites and blogs of 2024.

14 Cybersecurity Metrics + KPIs You Must Track in 2024
What are security ratings cybersecurity risk scoring explained, why is cybersecurity important, what is typosquatting (and how to prevent it), introducing upguard's new sig lite questionnaire.

- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
- Advanced Persistent Threats (APTs)
- Cyber Attack
- Data Breach
- Insider Threat
- Social Engineering
- Supply Chain Attack
- Vulnerability
- DOWNLOAD REPORTS
- REPORT OPPORTUNITIES
- PUBLISH YOUR OWN REPORT
- Marketing Kit

Russia APT28 Cyber Attacks German Air Traffic Control
Iran pays millions to stop data leak related to banks, how to combat apt cyber threats: a comprehensive guide, record breaking ransomware attacks on schools and colleges in 2023.
- Expert Insights & Resources
- Expert Commentary
- How-To Guide
CISO’s Guide to Presenting Cybersecurity to Board Directors

Seasoned CISOs/CSOs understand the importance of effectively communicating cyber risk and the need for investment in cybersecurity defense to the board of directors. To ensure cybersecurity becomes a strategic part of the corporate culture, it is crucial for CISOs to present the topic in a clear, concise, and compelling manner. In this article, I will share my advice on best practices that can help CISOs successfully raise awareness and secure the necessary support from their organization’s board.
One key aspect of successful communication is understanding the business objectives and risk appetite of the organization. It is essential to align cybersecurity initiatives with these objectives in order to demonstrate the value they can bring to the company. The board should be presented with data-driven evidence of cyber risks and potential consequences, along with an overview on the return on investment (ROI) in cybersecurity defense. This will help bridge the gap between technical and business perspectives, fostering an environment where cybersecurity is taken seriously and becomes a strategic priority.
Another crucial element is to focus on quantifiable metrics and avoid using vague or overly technical jargon. Board members are not necessarily experts in cybersecurity, so it is important to present information in a way that is easily digestible and resonates with them. Utilize real-world examples, case studies, and industry benchmarks to drive home the importance of investing in cybersecurity defense and creating a culture where everyone plays a role in protecting the organization from cyber threats.
Understanding the Board’s Perspective
As a CISO, it’s essential to comprehend the board’s viewpoint when presenting cybersecurity initiatives. Board members are typically focused on the company’s overall strategic direction, financial performance, and risk management. Thus, it’s critical to align your cybersecurity presentation with their priorities.
First, understand what concerns the board members the most. This could range from potential financial losses due to cyberattacks to reputational damage resulting from a breach. According to a Board of Directors Cyber Attitudes report, board members are particularly interested in quantifiable metrics and risk assessments that provide an accurate view of the company’s cybersecurity posture.
Ensure that your presentation demonstrates the return on investment (ROI) of your cybersecurity initiatives. Highlight the correlation between robust cybersecurity measures and attaining the company’s business objectives – whether it’s reducing downtime or enhancing customer trust.
Lastly, establish a dialogue with the board and be prepared to address their questions and concerns. Regular communication keeps the board informed about the cybersecurity landscape and fosters a deeper understanding of the risks and strategies involved, ultimately making cybersecurity a strategic part of the corporate culture.
Developing a Clear Cybersecurity Strategy
As a CISO/CSO, creating and presenting a clear cybersecurity strategy to the board of directors is crucial in fostering awareness of cyber risks and encouraging investment in cybersecurity defense. A comprehensive approach encompasses aligning with business objectives, identifying key cyber risks, and setting priorities for investment.
Aligning with Business Objectives
One of the essential aspects of a successful cybersecurity strategy is to ensure that it aligns with your organization’s overall business objectives. This connection helps the board of directors to understand the significance of cybersecurity in achieving the company’s goals. Begin by:
- Mapping cybersecurity initiatives to specific business objectives, such as increasing revenue or improving customer trust.
- Demonstrating how a strong cybersecurity posture supports and enhances the organization’s competitive advantage.
- Communicating the potential financial and reputational impact of cybersecurity incidents and how the strategy is designed to mitigate those risks.
Identifying Key Cyber Risks
In presenting a cybersecurity strategy, it is crucial to identify the key cyber risks facing your organization. A thorough assessment of these risks will enable the board to understand the need for investment in cybersecurity. When identifying key cyber risks, consider:
- Current and emerging threat landscape in your industry.
- Vulnerability assessments highlighting areas where your organization’s defenses may be lacking.
- Regulatory and compliance considerations, including potential fines and penalties for non-compliance or data breaches.
- Assessing your organization’s cybersecurity maturity and identifying areas in need of improvement.
Setting Priorities for Investment
With a clear understanding of the business objectives and key cyber risks, the next step is to prioritize investment in cybersecurity initiatives. Highlighting the most significant risks and potential impact will help the board to allocate resources wisely. When setting priorities for investment, take into account the following:
- Cost-benefit analysis of different cybersecurity initiatives, considering factors such as potential risk reduction and return on investment.
- Urgency and scalability of identified risks, with a focus on addressing high-priority issues without delay while keeping future growth and evolving threats in mind.
- Alignment with industry best practices and security benchmarks and compliance standards to demonstrate commitment to a strong cybersecurity posture.
- Identifying appropriate metrics to track progress and success, allowing the board to monitor the effectiveness of cybersecurity investments.
By developing a clear cybersecurity strategy that aligns with business objectives, identifies key cyber risks, and sets priorities for investment, you will be in a better position to communicate the importance of cybersecurity to the board of directors and foster a cyber-aware corporate culture.
Effective Communication with the Board
Effective communication is a crucial aspect of delivering a successful cybersecurity presentation to the board of directors. By considering the following strategies, you can ensure that your message is both clear and impactful.
Using Clear and Concise Language
It is essential to avoid over-technical security language when speaking with the board. Instead, use layman terms and familiar analogies that board members can grasp quickly. This approach will help them understand complex security concepts and make informed decisions without being overwhelmed by technical jargon. Examples of simple language include:
- Referring to “malware” as “malicious software” or “harmful programs”
- Using “data breach” instead of “unauthorized access to sensitive information”
These adjustments will make your communication more accessible and enable board members to grasp the importance of cybersecurity risk management.
Visualizing Cybersecurity Data
Visual aids can support your message and enhance comprehension among board members when presenting cybersecurity data. Using charts, graphs, and other visual elements helps to highlight trends, patterns, and vulnerabilities within your company’s cybersecurity landscape. For example, you may consider using:
- Pie charts to represent the proportion of various types of cyber threats faced by the organization
- Line charts to indicate the growth or decline of security incidents over a specific period
These visualizations help board members to better understand complex data, making it easier for them to engage with your presentation and make well-informed decisions.
Connecting Cyber Risks to Business Impact
For a cybersecurity presentation to resonate with board members, it’s crucial to relate cyber risks directly to the organization’s business objectives and overall strategy. By showcasing the potential financial, operational, and reputational impacts of a cyber incident, you can drive home the significance of cybersecurity in sustaining long-term business success.
Some ways to relate cyber risks to business impact include:
- Demonstrating the financial loss resulting from a data breach or ransomware attack
- Highlighting how a cyber incident can affect client trust, leading to a loss of customers and market share
- Stressing the importance of compliance with industry regulations and the potential consequences of non-compliance
By connecting the cybersecurity discussion to tangible business impacts, you’re more likely to garner support for investment in cybersecurity initiatives and promote a security-centric corporate culture.
Building a Cybersecurity Culture
Creating a strong cybersecurity culture within the organization is essential for managing cyber risk effectively. As a CISO, it is your responsibility to ensure that every employee understands the importance of cybersecurity and their role in maintaining the company’s security posture. Here are three key areas to focus on:
Promoting Employee Awareness
First and foremost, emphasize the importance of employee awareness through tailored security training and awareness programs. The human factor is involved in more than 85% of data breaches, as noted in the 2021 Verizon Data Breach Investigations Report . To build a successful cybersecurity culture, make security awareness training engaging and rewarding, and encourage a growth mindset. This can be achieved by gamifying training sessions, providing incentives for participation, and recognizing employees who demonstrate positive security behaviors.
Leadership Involvement
Strong leadership involvement is necessary for fostering a cybersecurity culture from the top down. Encourage the board of directors and the top management to champion cybersecurity initiatives, and communicate the importance of cybersecurity to the entire organization. As a CISO, leading by example is crucial in demonstrating the commitment to cybersecurity to employees.
Continuous Improvement
Establish a continuous improvement process for your cybersecurity program by regularly reviewing and updating policies, procedures, and technologies. Involve employees in the process by encouraging them to provide feedback and report security incidents without fear of retaliation. Benchmark your cybersecurity performance against industry standards and objective metrics to identify areas of improvement and track progress over time.
By focusing on these three key areas, you can build a strong cybersecurity culture within your organization, which will ultimately help you raise awareness of cyber risk, gain the willingness of the board of directors to invest in cybersecurity defense, and make cybersecurity a strategic part of the corporate culture.
Measuring Success
As a successful CISO, measuring the success of your cybersecurity program is crucial to ensure continuous improvement and demonstrating the value of cybersecurity initiatives to the board of directors.
Using Key Performance Indicators
Establishing Key Performance Indicators (KPIs) can help quantify the effectiveness of your cybersecurity program. KPIs should be aligned with the organization’s overall objectives and risk appetite. Some examples of KPIs that you can use to measure the success of your cybersecurity efforts include:
- Number of security incidents detected and resolved within a given period
- Reduction in the duration of time to detect and respond to incidents
- Percentage of employees completing security awareness training
- Number of vulnerabilities identified and remediated
These KPIs should be presented to the board of directors in a clear and easy-to-understand manner. This will help them grasp the significance of the data and make informed decisions regarding cybersecurity investments and strategic priorities.
Conducting Regular Reviews
Regular reviews of your cybersecurity program are essential to measure its effectiveness and identify areas for improvement. Schedule periodic meetings with the board of directors to discuss the progress of your cybersecurity program, share KPI data, and address any questions or concerns that may arise. During these meetings:
- Provide an overview of the current cyber threat landscape, specifically highlighting threats relevant to your industry and organization
- Discuss any recent security incidents and the actions taken to mitigate them
- Share insights on emerging technologies and best practices in the cybersecurity industry that could benefit the organization
- Seek feedback from board members to ensure their input is incorporated into the ongoing development and refinement of your cybersecurity program
By regularly reviewing your cybersecurity program with the board of directors, you can help keep cybersecurity at the forefront of their decision-making, foster a culture of cyber risk awareness, and drive the necessary investments to strengthen your organization’s security posture.
RELATED ARTICLES MORE FROM AUTHOR
Adapting cybersecurity practices to modern threats, stopping last year’s data spill from becoming today’s headlines, seven deadly myths of ddos protection, no posts to display, new reports.

2024 VPN Risk Report [Zscaler ThreatLabz]

2024 Cloud Security Report [Check Point]

2024 Cloud Security Report [ISC2]

2024 Cloud Security Report [Fortinet]
Editor picks, popular posts, list of countries which are most vulnerable to cyber attacks, top 5 cloud security related data breaches, top 5 pci compliance mistakes and how to avoid them, recent posts, alternative search engines to google for achieving data privacy, sales force acquires cloud based data security startup own for $1.9..., identity verification: the key to the security of sporting events.
- Terms of Service
- Advertise With Us
- Internships
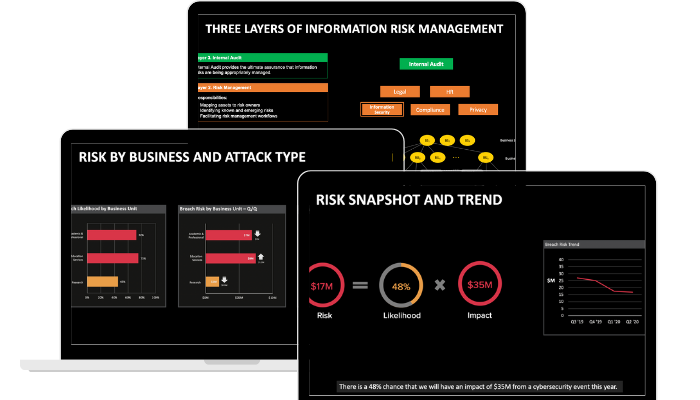
9 Slides Every CISO Should Use in Their Board Presentation
As a cybersecurity leader, you generally receive only a short window for your recurring board presentation. In that time, you need to communicate key risks and remediation tactics, explain your desired goals, and answer any questions; all with a largely non-technical audience.
Download this template to get:
- 9 Board level slides that you can customize based on your unique context
- Detailed guidance on what the board is looking for and how to tell a compelling story
- 10+ additional supporting slides to make the connection between information and compliance risk and Board-level business risks

This presentation template is divided into four sections designed to earn and retain the Board’s confidence in you and provide assurance that the Infosec function is effectively managing information risk.
1. Summarize the last meeting and refresh your Board about your cybersecurity framework
Summarize the takeaways from the previous Board presentation. Follow-up on unresolved issues or any unanswered questions from the previous meeting. Refresh the Board on your security framework.
2. Present your risk dashboard and review events and changes in risk landscape
Update the Board on the overall risk landscape for your organization, including and notable events. Highlight risks that require immediate action. Present mitigation strategies and explain how the Board can help.
3. Review progress against your strategic Infosec roadmap
Present Infosec’s progress towards your strategic objectives that you presented earlier to the Board. Be Transparent about any setbacks and say how you are managing through these.
4. Review any special topic
Discuss any topics that fall outside the scope of the other agenda topics. For example, relevant topics include M&A activity, a data breach, etc.
This customizable presentation template will help you organize your presentation to the board of directors. If you are a new CISO and presenting to your board for the first time, you should use a variation of this template which can be downloaded here .
Cybersecurity Board Presentation PPT Template
Get the powerpoint.
Balbix's security posture transformation platform is the industry’s first system to leverage specialized artificial intelligence (AI) to provide comprehensive and continuous predictive assessment of breach risk.
Register for AI-Era Cyber Risks: Ponemon and Balbix Insights
Presentation
9 Slides Every CISO Must Use in Their 2024 Board Presentation
As a CISO or security leader, you have limited time for your regular board presentation.
Thank you for your request.
Here is the link to the document you requested.
You need to address the most pressing concerns and explain your objectives during that time.
This presentation template is divided into four sections that aim to gain and maintain the board’s confidence in you and ensure that the Infosec function effectively manages information risk.
In 2024, most boards will want answers to the following questions:
- What is the organization doing to address security risks and opportunities with GenAI?
- How does the organization manage regulatory risks like those from the SEC?
- What are the critical cyber metrics that the board needs to be aware of?
- What will the business impact of a cybersecurity incident/breach be?
With this template, you’ll get:
- 9 board-level slides that you can personalize based on your unique context
- Up-to-date guidance on what the board is looking for and how to tell a compelling story
- Additional slides to connect cyber risks to other types of risks for the audit committee
- Become a Sponsor
- Become a Speaker
- Remote Sessions
- Testimonials
- Privacy Policy

How to Communicate Cybersecurity to the Board of Directors
CNN Analyst Col. Cedric Leighton (U.S. Air Force, Ret.) kicked off a recent SecureWorld web conference with a level-set on where cybersecurity stands on reporting to the board.
The board wants to know more about cybersecurity
The good news is that the board of directors wants to play a part.
"Your board wants to be active on this, but you have to help do some translation for them around cybersecurity and train them to some degree."
The challenge for security leaders is remembering that the board faces continuous inputs on cyber risk from many directions. It might be coming from other business leaders, the mainstream media, or even social media.
Part of the CISO role is to help the organization separate the wheat from the chaff to see how much of that information is correct and how much of it matters to the organization.
"I think you need to transform yourself into a sort of intelligence officer, where you have a clear understanding of threats and can present those," Leighton says.
This leads to an important question: When you report this intelligence to the board, do you know what they are looking for or care most about? You should, and it should inform how you approach things.
Cybersecurity reporting, each board is different
In a poll question during the web conference, attendees were asked what their boards care about when it comes to security. This was a multiple-choice question:
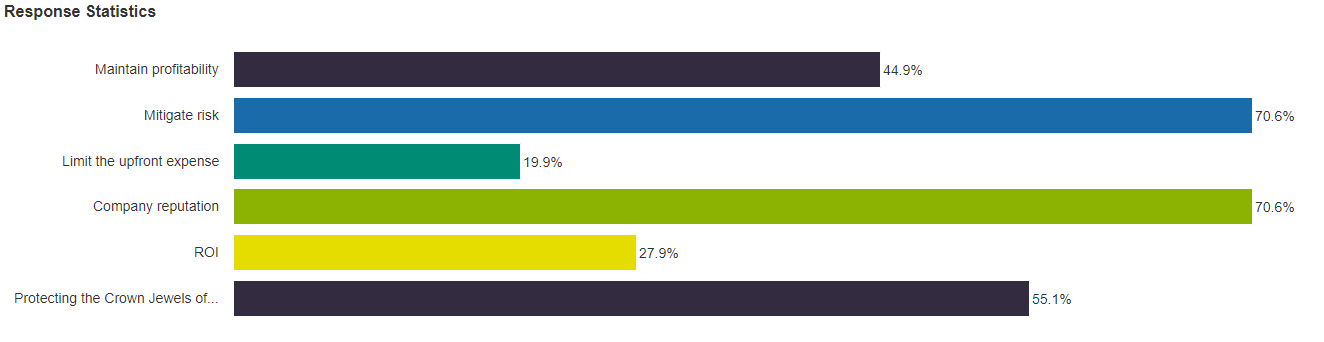
Mike Maziarz, Chief Marketing Officer of SecurityScorecard, says the results verify the idea that each board is different. Maziarz was the second presenter in the web conference.
What is a CMO doing on a cybersecurity web conference?
"If you wonder why the marketing guy is here, it's because my role is to share messages effectively over multiple channels, and I'm excited to share some of my insights when it comes to communicating with the board."
Strategies for communicating cybersecurity to the board
For starters, he says there are three key things to keep in mind:
1. Boards can't improve what they don't understand. 2. You can learn to speak their language. 3. You can unlock board engagement and better decision making with an easy to understand framework and related benchmarks.
Maziarz suggests going back to the basics as a starting point by reminding the board of the following:
- Adversaries do not play by the rules.
- A hacker's mindset is unique.
- They're adopting tech faster than we are.
- They'll usually attack the weakest link, not the lock.
And when you are in the room presenting to the board—or discussing security investment with your CFO, for example—try to see the question behind their question.

Another consideration: how well your message travels. How does it resonate through the C-suite to the boardroom even when you are no longer in the room?
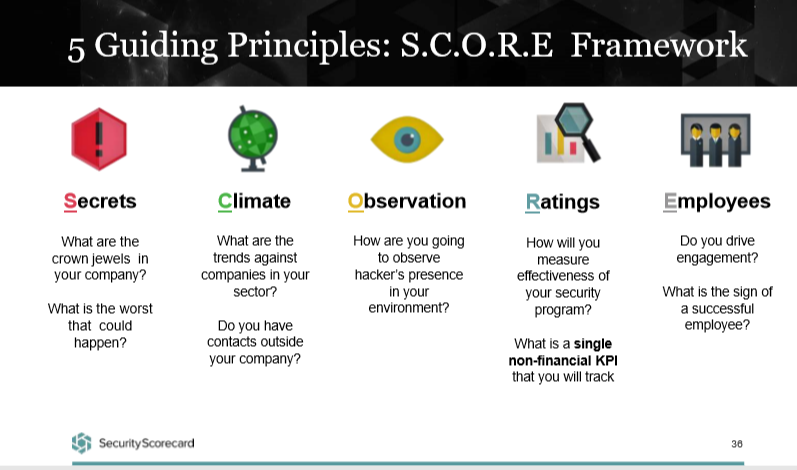
Maziarz also shared the S.C.O.R.E. framework his CISO uses to present to the board. The acronym stands for Secrets, Climate, Observations, Ratings, and Employees.
Turning your cybersecurity mission into a story for the board
Mitch Parker, CISO at Indiana University Health, presented next in the web conference, and he says you must create a story for the board around security.
You should start by figuring out who your board members are and what they value individually, if possible.
"If you do not do your research, you will be eaten alive," says Parker.
He suggests following them on social media and looking at them on LinkedIn. Are they sharing or liking certain kinds of articles or posts that reveal their hot button issues? Whatever you say about security will be viewed through each board member's point of view.
Next, he says you must understand your organization and where the board of directors and your CEO want to take it. You can build your presentation on cybersecurity around those themes.
"You want to first talk about your core initiatives. Talk about the core initiatives that tie into the core missions and value to the organization. Talk about what they directly support, even though they might not be core to your mission, the core to the organization.
Talk about what they are, talk about how they fit, talk about the most important ones, because realistically, if you're working in security, you're part of every core issue, even if it's a minor part. And you've got to show your part of those core initiatives."
And here's another thing you can practice before any board presentation: Be ready to explain what your team does without mentioning tools or technical solutions, and be able to do this in about 30 seconds.
On-demand cybersecurity webinar: presenting to the board
Do you need to present cybersecurity to the board? Do you need to prepare your CEO or your CIO to do it? Watch this complimentary web conference (on demand) to make sure you are on track: Communicating Cybersecurity to the Board.
The web conference is full of actionable information you can implement immediately to prepare for your next critical presentation on cybersecurity.

U.S. Agencies Warn of Ongoing Iranian Cyber Threats

Hong Kong Clerk Defrauded of $25 Million in Sophisticated Deepfake Scam

Convergence: Putting the Responsibility Where It Should Lie

Subscribe to Email Updates

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/itl/smallbusinesscyber/nist-cybersecurity-fundamentals-presentation
Small Business Cybersecurity Corner
Nist cybersecurity fundamentals presentation.
Download the Slides
Managing a small business is always challenging but keeping up with cybersecurity threats can be overwhelming. How do you learn about the latest threats? How do you educate your staff about best practices? NIST has prepared a training presentation (draft) that you can use to self-teach and help your team learn at the same time. Please download the slides so you can use them at your convenience.
Each slide includes speaker’s notes – so you will be able to understand and share the material and find links to resources to learn more. You can go through the materials as quickly or slowly as you need, knowing that the recommendations come from the Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST).
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover should trouble strike.
We welcome your feedback on this draft presentation and will incorporate improvements in the future.

COMMENTS
The 15-Minute, 7-Slide Security Presentation for Your Board of Directors. Help the board understand why cybersecurity is critical to the business. When the request comes in to give a cybersecurity presentation to the board, security leaders should jump at the chance to educate the executives. However, a lengthy, in- depth presentation is more ...
This means that cybersecurity risk at an enterprise level is not only a board discussion, but also a personal liability for board members. "Communication and reporting is more an art than a science," Olyaei says. "Security leaders must be able to educate, assure, empower and inform the board within the specific period of time allotted to ...
Diligent Effective CS Presentations to the Board Top Tips & Checklist 3 Your Cybersecurity Board Presentation Checklist Effective CISO Presentations to the Board: Top Tips & Checklist Come equipped with a dashboard view "In many board meetings, we get 10 minutes of fame if we're lucky, sometime that might be even further reduced
Below are some of the topics you may want to cover in your first presentation: A high-level overview of different threat actors. Risks to your cybersecurity environment (i.e., the things you're concerned about). The type of data you think is most critical or sensitive.
1. Level the conversation. Set expectations for your board and overview the conversation. The goal of the next 15 - 20 minutes will be to establish where their enterprise is on cyber risk, where it should be, and how it will get there. 2. Quantify the cyber risk spectrum.
3. Be transparent. Assessments shouldn't obfuscate the risks to the enterprise, experts say, so CISOs should be upfront and present relevant information in a straightforward, accessible manner ...
Vietnam. Virgin Islands (British) Virgin Islands (U.S.) Wallis And Futuna Islands. Western Sahara. Yemen. Zambia. Zimbabwe. Download Presenting to BOD, built by SANS Instructor Lance Spitzner, a slide deck on how to prepare for and present to Board of Directors on Cybersecurity.
4 Key Sections In Your Board Presentations. There are 4 key parts to your board presentation: 1. Summarize the last meeting and refresh your Board about your cybersecurity framework. Summarize the takeaways from the previous Board presentation. Follow-up on unresolved issues or any unanswered questions from the previous meeting.
We've seen CISOs and compliance officers speak to the board together to paint a vivid picture of cybersecurity, providing complementary perspectives that show collaboration on the topic. We've also joined CISOs during board presentations - providing external insights on industry cybersecurity risks and sharing relevant benchmarks.
Published: 15 April 2024 Summary. This Tool provides cybersecurity leaders with a series of presentation templates for the board of directors, based on the Gartner outcome-driven metrics approach, to communicate the business value of security and to treat cybersecurity as a business decision.
Sample CISO Operational Plan for Information Security. 4. Any Special topics that the board needs to be aware of. Include any special topics that fall outside the scope of the other agenda topics but are worthy of board awareness and/or discussion. These could be M&A activity with significant infosec aspects, leadership changes, or compliance ...
Best Practice 1: Understand the Structure of a Board Report. There isn't a set cyber board report structure that needs to be followed. In fact, obsessing too much over the report's structure increases the risk of not meeting the board-level requirement. A better approach is to think in terms of broad stakeholder metrics.
Developing a Clear Cybersecurity Strategy. As a CISO/CSO, creating and presenting a clear cybersecurity strategy to the board of directors is crucial in fostering awareness of cyber risks and encouraging investment in cybersecurity defense. A comprehensive approach encompasses aligning with business objectives, identifying key cyber risks, and ...
Format: How CISOs choose to present the materials to the board. The format of an update is usually a brief summary with an appendix. For example, CISOs may provide the board with a three-page summary that has a 30-page appendix including details and metrics. Other formats may include a presentation/memo or a pre-read.
Determining presentation goals and style. When creating your presentation, you should only include relevant information and focus on being concise with your explanations. Succinctly presenting cybersecurity performance makes it easier for board members to absorb the information that you are sharing with them.
This presentation template is divided into four sections designed to earn and retain the Board's confidence in you and provide assurance that the Infosec function is effectively managing information risk. 1. Summarize the last meeting and refresh your Board about your cybersecurity framework. Summarize the takeaways from the previous Board ...
Don't let your board presentation miss the mark. Follow these best practices and common mistakes to avoid when communicating cybersecurity risk to the board. Written by Mary K. Pratt — Contributing writer, CSO. Cybersecurity is a top concern for boards of directors.
9 board-level slides that you can personalize based on your unique context. Up-to-date guidance on what the board is looking for and how to tell a compelling story. Additional slides to connect cyber risks to other types of risks for the audit committee. This customizable powerpoint template will help you gain the Board's confidence and ...
Five Board Questions That Security and Risk Leaders Must Be Prepared to Answer. How to Build an Effective Cybersecurity and Technology Risk Presentation for Your Board of Directors. Develop Key Risk Indicators and Security Metrics That Influence Business Decision Making *Note that some documents may not be available to all Gartner clients.
Strategies for communicating cybersecurity to the board. For starters, he says there are three key things to keep in mind: 1. Boards can't improve what they don't understand. 2. You can learn to speak their language. 3. You can unlock board engagement and better decision making with an easy to understand framework and related benchmarks.
Join your peers for the unveiling of the latest insights at Gartner conferences. It's critical that security and risk management leaders supply board-relevant and business-aligned content that is not hampered by overly technical references. Gartner has developed a framework for an effective board presentation on cybersecurity and technology ...
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover ...
Costly data breaches affecting major corporations have become a regular facet of the 24-hour news cycle, prompting heightened pressure from shareholders and regulators. As a result, corporate directors are becoming increasingly conscious of information security and are taking a more active role in risk oversight and governance. This whitepaper arms CISOs and their teams with five principles ...