
- Adding or removing role assignments using Azure Portal
Go back to AZ-304 Tutorials
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
However, Azure’s role-based access control (RBAC) refers to the authorization system for managing access to Azure resources. And, to grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope.

Prerequisites
For adding or removing role assignments, you must have:
- Firstly, Microsoft.Authorization/roleAssignments/write
- Secondly, Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
Access control (IAM)
Access control (IAM) is the page that is for assigning roles to grant access to Azure resources. It’s also known as identity and access management and appears in several locations in the Azure portal. There are questions for assigning roles to help in understanding about the Access control (IAM) page.
- Who needs access? This refers to a user, group, service principal, or managed identity.
- What role do they need? Permissions are grouped together into roles, so you can select from a list of several built-in roles orcan use custom roles.
- Where do they need access? This refers to the set of resources that the access applies to. However, “where” can be a management group, subscription, resource group, or a single resource such as a storage account.
Adding a role assignment
- Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to.
- Secondly, click the specific resource for that scope.
- Then, Click Access control (IAM).
- Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
- After that, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
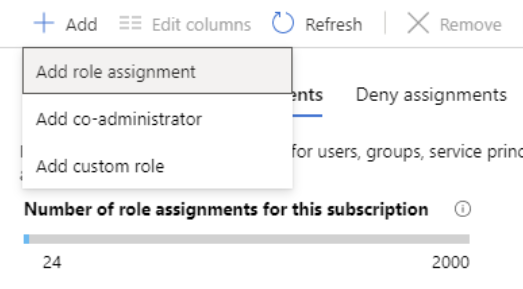
- Then, in the Role drop-down list, select a role such as Virtual Machine Contributor.
- There in the Select list, select a user, group, service principal, or managed identity. And, if you don’t see the security principal in the list, you can type in the Select box to search the directory for display names, email addresses, and object identifiers.
- Lastly, click Save to assign the role.
Assigning a user as an administrator of a subscription
For giving users the role of an administrator of an Azure subscription, first assign them the Owner role at the subscription scope. As the Owner role gives the user full access to all resources in the subscription, including the permission to grant access to others. However, these steps are the same as any other role assignment.
- Firstly, in the Azure portal, click All services and then Subscriptions.
- Then, click the subscription where you want to grant access.
- Thirdly, click Access control (IAM).
- After that, click the Role assignments tab to view the role assignments for this subscription.
- Then, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
- And, in the Role drop-down list, select the Owner role.
- Then, in the Select list, select a user.

Adding a role assignment for a managed identity
For adding role assignments for a managed identity use the Access control (IAM) page. However, when you use the Access control (IAM) page, you start with the scope and then select the managed identity and role. In this section, you will learn about an alternate way to add role assignments for a managed identity. Using these steps, you start with the managed identity and then select the scope and role.
System-assigned managed identity
- Use these steps for assigning a role to a system-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a system-assigned managed identity. Then, in the left menu, click Identity.
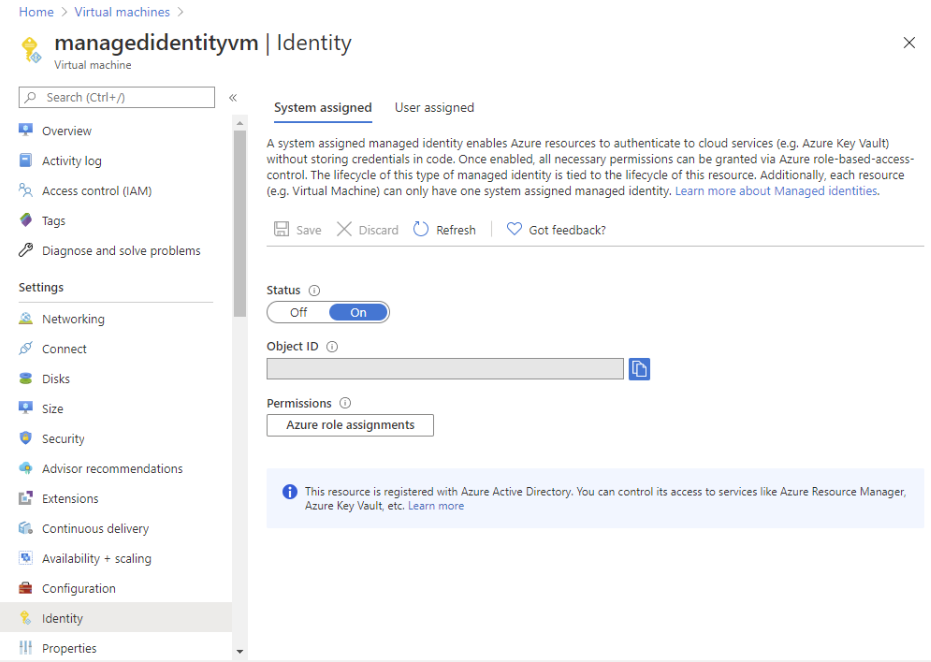
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected system-assigned managed identity then you will see the list of role assignments.
- For changing the subscription, click the Subscription list. Then, click Add role assignment.
- Then, use the drop-down lists to select the set of resources that the role assignment applies to such as Subscription, Resource group, or resource. And, if you don’t have role assignment write permissions for the selected scope, an inline message will be displayed.
- After that, in the Role drop-down list, select a role such as Virtual Machine Contributor.
User-assigned managed identity
- Use these steps for assigning a role to a user-assigned managed identity by starting with the managed identity.
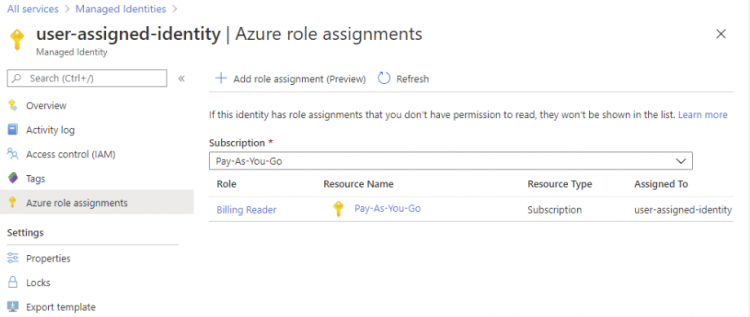
- Firstly, in the Azure portal, open a user-assigned managed identity. Then, in the left menu, click Identity.
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected user-assigned managed identity then you will see the list of role assignments.
Removing a role assignment
In Azure RBAC, for removing access from an Azure resource, you first remove a role assignment. Use these steps to remove a role assignment.
- Firstly, Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.
- Then, click the Role assignments tab to view all the role assignments for this subscription.
- After that, in the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove.
- Then, Click Remove.
- Lastly, in the remove role assignment message that appears, click Yes.
However, if you see a message that inherited role assignments cannot be removed, then you are trying to remove a role assignment at a child scope. So, you should open Access control (IAM) at the scope where the role was assigned and try again.

Reference: Microsoft Documentation
Prepare for Assured Success

| { | |
| "description": "Grant service principal X reader access on application Z.", | |
| "client_type" : "application", | |
| "client_principal_name": "service-principal-x-prod", | |
| "server_app_registration_name": "app-registration-z-prod", | |
| "role_name": "reader" | |
| }, |
You can use the script like this:
- Download the script and the config file.
- Update the config files to your needs
- Trigger the script via PowerShell
If you are interested, this is how the script looks like:
| param ( | |
| [string] $TenantId, | |
| [string] $ConfigFilePath | |
| ) | |
| $ErrorActionPreference = "Stop" | |
| Write-Host Start Azure AD role assignment script | |
| Write-Host "-Tenant Id:" $TenantId -ForegroundColor Gray | |
| Write-Host "-Config File Path:" $ConfigFilePath -ForegroundColor Gray | |
| Write-Host Installing and importing AzureAD Module | |
| if (Get-Module -ListAvailable -Name AzureAD) { | |
| Import-Module -Name "AzureAD" | |
| } | |
| else { | |
| Install-Module -Name "AzureAD" -Force | |
| } | |
| Write-Host Connecting to Azure AD Tenant within current security context | |
| $azure_context = Get-AzContext | |
| $account_id = $azure_context.Account.Id | |
| Write-Host "-Account Id:" $azure_context.Account.Id -ForegroundColor Gray | |
| Connect-AzureAD -TenantId $TenantId -AccountId $account_id | |
| Write-Host Loading role assignments from config file | |
| $role_assignments = (Get-Content $ConfigFilePath -Raw) | ConvertFrom-Json | |
| Write-Host Looping each configured role assignment | |
| foreach($role_assignment in $role_assignments) | |
| { | |
| Write-Host Applying role assigment... started -ForegroundColor Green | |
| Write-Host "-Description:" $role_assignment.description -ForegroundColor Gray | |
| Write-Host "-Client principal Name:" $role_assignment.client_principal_name -ForegroundColor Gray | |
| Write-Host "-Server App Registration Name:" $role_assignment.server_app_registration_name -ForegroundColor Gray | |
| Write-Host "-Role Name:" $role_assignment.role_name -ForegroundColor Gray | |
| Write-Host Getting the server application registration | |
| $aad_filter = "DisplayName eq '" + $role_assignment.server_app_registration_name + "'" | |
| $server_application_registration = Get-AzureADApplication -Filter $aad_filter | |
| if (!$server_application_registration) { throw "Cannot find configured server application registration with name '" + $role_assignment.server_app_registration_name + "'" } | |
| Write-Host Getting the server service principal id | |
| $aad_filter = "AppId eq '" + $server_application_registration.AppId + "'" | |
| $server_service_principal = Get-AzureADServicePrincipal -Filter $aad_filter | |
| $server_service_principal_id = $server_service_principal.ObjectId | |
| Write-Host "-Server service principal Id: " $server_service_principal_id -ForegroundColor Gray | |
| Write-Host Getting the Id for the configured application role | |
| $role_id = ($server_application_registration.AppRoles | Where-Object DisplayName -eq $role_assignment.role_name).Id | |
| if (!$role_id) { throw "Cannot find configured application role with name '" + $role_assignment.role_name + "'" } | |
| Write-Host "-Role Id: " $role_id -ForegroundColor Gray | |
| if(($role_assignment.client_type -ne "application") -and ($role_assignment.client_type -ne "user")) { throw "Incorrect client_type '" + $role_assignment.client_type + "' provided." } | |
| switch ($role_assignment.client_type) | |
| { | |
| "application" | |
| { | |
| Write-Host Getting the configured client service principal | |
| $aad_filter = "DisplayName eq '" + $role_assignment.client_principal_name + "'" | |
| $client_service_principal = (Get-AzureADServicePrincipal -Filter $aad_filter) | |
| if (!$client_service_principal) { throw "Cannot find configured client service principal with name '" + $role_assignment.client_principal_name + "'" } | |
| $client_service_principal_id = $client_service_principal.ObjectId | |
| $client_service_principal_name = $client_service_principal.DisplayName | |
| Write-Host "-Client service principal Id:" $client_service_principal_id -ForegroundColor Gray | |
| Write-Host Assigning the Azure Ad role to the configured service principal | |
| try | |
| { | |
| New-AzureADServiceAppRoleAssignment -Id $role_id -ResourceId $server_service_principal_id -ObjectId $client_service_principal_id -PrincipalId $client_service_principal_id | |
| } | |
| catch | |
| { | |
| if( $_.Exception.Message -like '*Permission being assigned already exists on the object*') | |
| { | |
| Write-Host Permission already exists | |
| } | |
| else | |
| { | |
| Write-Error $_.Exception.Message | |
| } | |
| } | |
| } | |
| "user" | |
| { | |
| Write-Host Getting the configured client user | |
| $user = Get-AzureADUser -searchstring $role_assignment.client_principal_name | |
| if (!$user) { throw "Cannot find configured client users with name '" + $role_assignment.client_principal_name + "'" } | |
| $user_id = $user.ObjectId | |
| Write-Host "-User Id:" $user_id -ForegroundColor Gray | |
| Write-Host Assigning the Azure Ad role to the configured user | |
| try | |
| { | |
| New-AzureADUserAppRoleAssignment -Id $role_id -ResourceId $server_service_principal_id -ObjectId $user_id -PrincipalId $user_id | |
| } | |
| catch | |
| { | |
| if( $_.Exception.Message -like '*Permission being assigned already exists on the object*') | |
| { | |
| Write-Host Permission already exists | |
| } | |
| else | |
| { | |
| Write-Error $_.Exception.Message | |
| } | |
| } | |
| } | |
| } | |
| Write-Host Applying role assigment... done -ForegroundColor Green | |
| } |
I hope that this script helps you to accelerate your security automation.
Cheers Toon
UPCOMING TRAININGS
CHECK OUT OUR TRAININGS
Azure Integration Services
Azure migration.
- Azure Governance
Azure Security
Azure foundations, recent posts.
- Looking back at INTEGRATE 2024
- Azure Service Bus vs Event Grid Pull Delivery
- Trying the new Microsoft Applied Skills
- Finally a correct way to configure RBAC for DevOps agents!
- What do the new API Management v2 tiers mean for you?
- Announcement
- API Management
- Architecture
- Azure App Service
- Azure Data Factory
- Azure DevOps
- Azure Event Grid
- Azure Functions
- Azure Kubernetes Service
- Azure Policy
- Azure Resource Graph
- Azure Resource Manager
- Azure Service Bus
- Azure Stream Analytics
- BizTalk Server
- Container Apps
- Geen categorie
- Home Automation
- Microsoft Learn
- Service Bus
MEET THE YOUR AZURE COACH TEAM
Your Azure Coach is specialized in organizing Azure trainings that are infused with real-life experience. All our coaches are active consultants, who are very passionate and who love to share their Azure expertise with you.
Toon Vanhoutte
Azure integration services & serverless.

Wim Matthyssen
Azure infra, security & governance, azure development and ai/ml, azure identity and security, stéphane eyskens, cloud-native azure architecture, geert baeke, azure kubernetes service & containerization, maik van der gaag, azure infrastructure as code & devops, bart verboven, sammy deprez, azure ai, ml & cognitive services, sander van de velde.

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...
Azure RBAC: role assignments and ARM templates

This post is about Azure's role assignments and ARM templates. Role assignments can be thought of as "permissions for Azure".
If you're deploying to Azure, there's a good chance you're using ARM templates to do so. Once you've got past "Hello World", you'll probably find yourself in a situation when you're deploying multiple types of resource to make your solution. For instance, you may be deploying an App Service alongside Key Vault and Storage .
One of the hardest things when it comes to deploying software and having it work, is permissions. Without adequate permissions configured, the most beautiful code can do nothing . Incidentally, this is a good thing. We're deploying to the web; many people are there, not all good. As a different kind of web-head once said:

Azure has great power and suggests you use it wisely .
Access management for cloud resources is critical for any organization that uses the cloud. Azure role-based access control (Azure RBAC) helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to. Designating groups or individual roles responsible for specific functions in Azure helps avoid confusion that can lead to human and automation errors that create security risks. Restricting access based on the need to know and least privilege security principles is imperative for organizations that want to enforce security policies for data access.
This is good advice. With that in mind, how can we ensure that the different resources we're deploying to Azure can talk to one another?
Role (up for your) assignments
The answer is roles. There's a number of roles that exist in Azure that can be assigned to users, groups, service principals and managed identities. In our own case we're using managed identity for our resources. What we can do is use "role assignments" to give our managed identity access to given resources. Arturo Lucatero gives a great short explanation of this:
Whilst this explanation is delightfully simple, the actual implementation when it comes to ARM templates is a little more involved. Because now it's time to talk "magic" GUIDs. Consider the following truncated ARM template, which gives our managed identity (and hence our App Service which uses this identity) access to Key Vault and Storage:
Let's take a look at these three variables:
The three variables above contain the subscription resource ids for the roles Storage Blob Data Contributor , Key Vault Secrets Officer and Key Vault Crypto Officer . The first question on your mind is likely: "what is ba92f5b4-2d11-453d-a403-e96b0029c9fe and where does it come from?" Great question! Well, each of these GUIDs represents a built-in role in Azure RBAC. The ba92f5b4-2d11-453d-a403-e96b0029c9fe represents the Storage Blob Data Contributor role.
How can I look these up? Well, there's two ways; there's an article which documents them here or you could crack open the Cloud Shell and look up a role by GUID like so:
Or by name like so:
As you can see, the Actions section of the output above (and in even more detail on the linked article ) provides information about what the different roles can do. So if you're looking to enable one Azure resource to talk to another, you should be able to refer to these to identify a role that you might want to use.
Creating a role assignment
So now we understand how you identify the roles in question, let's take the final leap and look at assigning those roles to our managed identity. For each role assignment, you'll need a roleAssignments resource defined that looks like this:
Let's go through the above, significant property by significant property (it's also worth checking the official reference here ):
- type - the type of role assignment we want to create, for a key vault it's "Microsoft.KeyVault/vaults/providers/roleAssignments" , for storage it's "Microsoft.Storage/storageAccounts/providers/roleAssignments" . The pattern is that it's the resource type, followed by "/providers/roleAssignments" .
- dependsOn - before we can create a role assignment, we need the service principal we desire to permission (in our case a managed identity) to exist
- properties.roleDefinitionId - the role that we're assigning, provided as an id. So for this example it's the keyVaultCryptoOfficer variable, which was earlier defined as [subscriptionResourceId('Microsoft.Authorization/roleDefinitions', 'ba92f5b4-2d11-453d-a403-e96b0029c9fe')] . (Note the use of the GUID)
- properties.principalId - the id of the principal we're adding permissions for. In our case this is a managed identity (a type of service principal).
- properties.scope - we're modifying another resource; our key vault isn't defined in this ARM template and we want to specify the resource we're granting permissions to.
- properties.principalType - the type of principal that we're creating an assignment for; in our this is "ServicePrincipal" - our managed identity.
There is an alternate approach that you can use where the type is "Microsoft.Authorization/roleAssignments" . Whilst this also works, it displayed errors in the Azure tooling for VS Code . As such, we've opted not to use that approach in our ARM templates.
Many thanks to the awesome John McCormick who wrangled permissions with me until we bent Azure RBAC to our will.
- Role (up for your) assignments
- Creating a role assignment
- Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers
- Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand
- OverflowAI GenAI features for Teams
- OverflowAPI Train & fine-tune LLMs
- Labs The future of collective knowledge sharing
- About the company Visit the blog
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.

Why did Role assignment creation failed?
I changed role
why did role assiment creation failed? How to solve this?
- 1 Command doesn't seem to be correct. What is pichanagm in the scope? – Vlad DX Commented Nov 11, 2023 at 19:58
- Also, pay attention to the warning: Option '--sdk-auth' has been deprecated and will be removed in a future release. – Vlad DX Commented Nov 11, 2023 at 19:59
- @VladDX Resource group. – MikiBelavista Commented Nov 12, 2023 at 9:01
Initially I got the same error , when I tried the same command as you:

The error "Role assignment creation failed." usually occurs if you are passing invalid values or parameters to create the service principal and rbac for sp. Refer this MsDoc for passing valid scope.
Note that: --sdk-auth has been deprecated and will be removed in a future release.
To resolve the error , make sure to pass valid scope /subscriptions/SubID/resourceGroups/ruk

Service Principal got created:

Contributor role assigned to the Service Principal:

Make use of az login to sign in and perform the action as --sdk-auth option will be removed in future release.
az ad sp | Microsoft
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged azure or ask your own question .
- The Overflow Blog
- Where does Postgres fit in a world of GenAI and vector databases?
- Mobile Observability: monitoring performance through cracked screens, old...
- Featured on Meta
- Announcing a change to the data-dump process
- Bringing clarity to status tag usage on meta sites
- What does a new user need in a homepage experience on Stack Overflow?
- Staging Ground Reviewer Motivation
- Feedback requested: How do you use tag hover descriptions for curating and do...
Hot Network Questions
- Can stockfish provide analysis with non-standard pieces like knooks?
- What is this device in my ceiling making out of battery chirps?
- How to count mismatches between two rows, column by column R?
- My supervisor wants me to switch to another software/programming language that I am not proficient in. What to do?
- Who was the "Dutch author", "Bumstone Bumstone"?
- What is the highest apogee of a satellite in Earth orbit?
- Is it possible to have a planet that's gaslike in some areas and rocky in others?
- Can the SLS's mobile launch platform be rotated at the launch complex to keep the rocket on the leeward side of the tower in case of high winds?
- Why did the Fallschirmjäger have such terrible parachutes?
- Rings demanding identity in the categorical context
- How can judicial independence be jeopardised by politicians' criticism?
- ESTA is not letting me pay
- Why are complex coordinates outlawed in physics?
- In Top, *how* do conjugate homorphisms of groups induce homotopies of classifying maps?
- Can Shatter damage Manifest Mind?
- Does the order of ingredients while cooking matter to an extent that it changes the overall taste of the food?
- How specific does the GDPR require you to be when providing personal information to the police?
- What is the purpose of these 33-ohm series resistors on the RMII side of the LAN8742A?
- Is there a way to resist spells or abilities with an AOE coming from my teammates, or exclude certain beings from the effect?
- What are some refutations to the etymological fallacy?
- Writing an i with a line over it instead of an i with a dot and a line over it
- Has a tire ever exploded inside the Wheel Well?
- Motion of the COM of 2-body system
- Why was this lighting fixture smoking? What do I do about it?
- Español – América Latina
- Português – Brasil
- GKE Enterprise
- Documentation
- GKE on Azure
Create Azure role assignments
This page shows how you grant permissions to GKE on Azure so that it can access Azure APIs. You need to perform these steps when setting up a new GKE on Azure cluster or when updating permissions for an existing cluster. These permissions are necessary for GKE on Azure to manage Azure resources on your behalf, such as virtual machines, networking components, and storage.
Obtain service principal and subscription IDs
To grant permissions to GKE on Azure, you need to obtain your Azure service principal and subscription ID. The Azure service principal and subscription ID are associated with the Azure AD application you created for GKE on Azure. For details, see Create an Azure Active Directory application .
A service principal is an identity in Azure Active Directory (AD) that is used to authenticate to Azure and access its resources. An Azure subscription is a logical container that provides you with authorized access to Azure products and services. A subscription ID is a unique identifier associated with your Azure subscription.
To save your service principal and subscription IDs for quick reference, you can store them in shell variables. To create these shell variables, run the following command:
Replace APPLICATION_NAME with the name of your Azure AD application.
Create three custom roles
To grant GKE on Azure the permissions to manage your Azure resources, you need to create three custom roles and assign them to the service principal. Only the minimum permissions are added in the following instructions. You can add more permissions if you need to.
You need to create custom roles for the following types of access:
- Subscription-level access : Permissions that apply to the entire Azure subscription, allowing management of all Azure resources within that subscription.
- Cluster resource group-level access : Permissions specific to managing Azure resources within a particular resource group that contains your GKE on Azure clusters.
- Virtual network resource group-level access : Permissions specific to managing Azure resources within a resource group that contains your Azure virtual network resources.
Create role for subscription-level access
Create a file named GKEOnAzureAPISubscriptionScopedRole.json .
Open GKEOnAzureAPISubscriptionScopedRole.json in an editor and add the following permissions:
Create the new custom role:
Assign the role to the service principal using the following command:
Create role for cluster resource group-level access
Create a file named GKEOnAzureClusterResourceGroupScopedRole.json .
Open GKEOnAzureClusterResourceGroupScopedRole.json in an editor and add the following permissions:
Create role for virtual network resource group-level access
Create a file named GKEOnAzureAPIVNetResourceGroupScopedRole.json .
Open GKEOnAzureAPIVNetResourceGroupScopedRole.json in an editor and add the following permissions:
What's next
- Create a client certificate
Except as otherwise noted, the content of this page is licensed under the Creative Commons Attribution 4.0 License , and code samples are licensed under the Apache 2.0 License . For details, see the Google Developers Site Policies . Java is a registered trademark of Oracle and/or its affiliates.
Last updated 2024-08-30 UTC.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Assign Azure roles using Azure PowerShell
- 13 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes how to assign roles using Azure PowerShell.
We recommend that you use the Azure Az PowerShell module to interact with Azure. To get started, see Install Azure PowerShell . To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az .
Prerequisites
To assign roles, you must have:
- Microsoft.Authorization/roleAssignments/write permissions, such as Role Based Access Control Administrator
- PowerShell in Azure Cloud Shell or Azure PowerShell
- The account you use to run the PowerShell command must have the Microsoft Graph Directory.Read.All permission.
Steps to assign an Azure role
To assign a role consists of three elements: security principal, role definition, and scope.
Step 1: Determine who needs access
You can assign a role to a user, group, service principal, or managed identity. To assign a role, you might need to specify the unique ID of the object. The ID has the format: 11111111-1111-1111-1111-111111111111 . You can get the ID using the Azure portal or Azure PowerShell.
For a Microsoft Entra user, get the user principal name, such as [email protected] or the user object ID. To get the object ID, you can use Get-AzADUser .
For a Microsoft Entra group, you need the group object ID. To get the object ID, you can use Get-AzADGroup .
Service principal
For a Microsoft Entra service principal (identity used by an application), you need the service principal object ID. To get the object ID, you can use Get-AzADServicePrincipal . For a service principal, use the object ID and not the application ID.
Managed identity
For a system-assigned or a user-assigned managed identity, you need the object ID. To get the object ID, you can use Get-AzADServicePrincipal .
Step 2: Select the appropriate role
Permissions are grouped together into roles. You can select from a list of several Azure built-in roles or you can use your own custom roles. It's a best practice to grant access with the least privilege that is needed, so avoid assigning a broader role.
To list roles and get the unique role ID, you can use Get-AzRoleDefinition .
Here's how to list the details of a particular role.
For more information, see List Azure role definitions .
Step 3: Identify the needed scope
Azure provides four levels of scope: resource, resource group , subscription, and management group . It's a best practice to grant access with the least privilege that is needed, so avoid assigning a role at a broader scope. For more information about scope, see Understand scope .
Resource scope
For resource scope, you need the resource ID for the resource. You can find the resource ID by looking at the properties of the resource in the Azure portal. A resource ID has the following format.
Resource group scope
For resource group scope, you need the name of the resource group. You can find the name on the Resource groups page in the Azure portal or you can use Get-AzResourceGroup .
Subscription scope
For subscription scope, you need the subscription ID. You can find the ID on the Subscriptions page in the Azure portal or you can use Get-AzSubscription .
Management group scope
For management group scope, you need the management group name. You can find the name on the Management groups page in the Azure portal or you can use Get-AzManagementGroup .
Step 4: Assign role
To assign a role, use the New-AzRoleAssignment command. Depending on the scope, the command typically has one of the following formats.
Assign role examples
Assign a role for all blob containers in a storage account resource scope.
Assigns the Storage Blob Data Contributor role to a service principal with object ID 55555555-5555-5555-5555-555555555555 and Application ID 66666666-6666-6666-6666-666666666666 at a resource scope for a storage account named storage12345 .
Assign a role for a specific blob container resource scope
Assigns the Storage Blob Data Contributor role to a service principal with object ID 55555555-5555-5555-5555-555555555555 and Application ID 66666666-6666-6666-6666-666666666666 at a resource scope for a blob container named blob-container-01 .
Assign a role for a group in a specific virtual network resource scope
Assigns the Virtual Machine Contributor role to the Pharma Sales Admins group with ID aaaaaaaa-aaaa-aaaa-aaaa-aaaaaaaaaaaa at a resource scope for a virtual network named pharma-sales-project-network .
Assign a role for a user at a resource group scope
Assigns the Virtual Machine Contributor role to [email protected] user at the pharma-sales resource group scope.
Alternately, you can specify the fully qualified resource group with the -Scope parameter:
Assign a role for a user using the unique role ID at a resource group scope
There are a couple of times when a role name might change, for example:
- You are using your own custom role and you decide to change the name.
- You are using a preview role that has (Preview) in the name. When the role is released, the role is renamed.
Even if a role is renamed, the role ID does not change. If you are using scripts or automation to create your role assignments, it's a best practice to use the unique role ID instead of the role name. Therefore, if a role is renamed, your scripts are more likely to work.
The following example assigns the Virtual Machine Contributor role to the [email protected] user at the pharma-sales resource group scope.
Assign a role for an application at a resource group scope
Assigns the Virtual Machine Contributor role to an application with service principal object ID 77777777-7777-7777-7777-777777777777 at the pharma-sales resource group scope.
Assign a role for a user at a subscription scope
Assigns the Reader role to the [email protected] user at a subscription scope.
Assign a role for a user at a management group scope
Assigns the Billing Reader role to the [email protected] user at a management group scope.
- List Azure role assignments using Azure PowerShell
- Tutorial: Grant a group access to Azure resources using Azure PowerShell
- Manage resources with Azure PowerShell
Was this page helpful?
Additional resources

IMAGES
VIDEO
COMMENTS
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes how to assign roles using the Azure portal.
Role assignments enable you to grant a principal (such as a user, a group, a managed identity, or a service principal) access to a specific Azure resource. This article describes the details of role assignments.
Learn the steps to assign Azure roles to users, groups, service principals, or managed identities using Azure role-based access control (Azure RBAC).
The way you control access to resources using RBAC is to create role assignments. This is a key concept to understand - it's how permissions are enforced. A role assignment consists of three elements: security principal, role definition, and scope. User - An individual who has a profile in Azure Active Directory.
The Initial Attempt We create a new AzDO yaml pipeline to do the following: Use the Azure CLI task Use the Service Connection created above Use an incline script to perform the required role ...
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
Scripting Azure AD application role assignments When using Azure Active Directory for adding role-based access control to your web applications and APIs, it is highly recommended to use application roles. This allows you to define custom application roles and these can be assigned to users and applications. A clean way to secure your applications!
We're excited to share the public preview of delegating Azure role assignment management using conditions. This preview gives you the ability to enable others to assign Azure roles but add restrictions on the roles they can assign and who they can assign roles to.
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope. This article describes how to assign roles using Azure CLI.
This consolidated JSON file includes action definitions, roles, and assignments, making implementation seamless through Azure CLI or PowerShell commands, ensuring precise and efficient access ...
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function.
ARM templates can help define Azure Role-Based Access Control. By creating role assignments, users can grant Managed Identities access to resources.
The error "Role assignment creation failed." usually occurs if you are passing invalid values or parameters to create the service principal and rbac for sp. Refer ...
Role assignment conditions can also be used in conjuction with Custom security attributes in Azure Entra ID to make role assignment easier by reducing the number of individual role assignments.
Learn how to create Azure custom roles using the Azure portal and Azure role-based access control (Azure RBAC). This includes how to list, create, update, and delete custom roles.
Create Azure role assignments This page shows how you grant permissions to GKE on Azure so that it can access Azure APIs. You need to perform these steps when setting up a new GKE on Azure cluster or when updating permissions for an existing cluster. These permissions are necessary for GKE on Azure to manage Azure resources on your behalf, such as virtual machines, networking components, and ...
Azure role-based access control (Azure RBAC) is the way that you manage access to Azure resources. In this tutorial, you grant a user access to create and manage virtual machines in a resource group.
Learn how to grant access to Azure resources for users, groups, service principals, or managed identities using Azure PowerShell and Azure role-based access control (Azure RBAC).
Step 1: Setting Up the Azure OpenAI Instance. Create a Resource Group. In our case I called it DeployOpenAI. Next we will deploy the Open AI instance by going to All Services and Searching for Open AI . Create the Instance by placing it in your same resource Group. Accept all the defaults and press next until Resource is deployed.