

Essay on Computer Network
Students are often asked to write an essay on Computer Network in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Computer Network
Introduction to computer network.
A computer network is a group of computers linked together. It enables sharing of information and resources. They can be connected through cables, infrared, satellite, or wireless links.
Types of Computer Networks
There are several types of networks. Local Area Network (LAN) connects computers in a small area. Wide Area Network (WAN) covers a large area, like cities or countries. Metropolitan Area Network (MAN) serves a city or suburb.
Benefits of Computer Networks
Networks make communication faster and easier. They allow sharing files, software, and hardware. They also improve data security by allowing backups and recovery.
Also check:
250 Words Essay on Computer Network
Introduction.
A computer network is a digital telecommunications network that allows computers to exchange data. In computer networks, networked computing devices exchange data with each other using a data link. The interconnections between nodes are formed from a broad spectrum of telecommunication network technologies.
Types of Networks
Based on their scale and scope, computer networks can be categorized into Local Area Networks (LANs), Metropolitan Area Networks (MANs), and Wide Area Networks (WANs). LANs are often used in small geographical areas, while MANs cover larger city-wide areas, and WANs can span countries or even the globe.
Network Architecture
The architecture of a computer network includes the design principles, physical configuration, functional organization, operational procedures, and data formats used. The two primary types are client-server, where one or more computers act as servers, and peer-to-peer, where each computer has equal responsibilities.
Protocols and Standards
Networks operate based on protocols, which are agreed-upon rules determining how computers communicate. These protocols exist for various levels of network communication, forming a protocol stack. The most common stack, TCP/IP, forms the basis of the internet.
Significance of Computer Networks
Computer networks have revolutionized computing by enabling distributed systems, where multiple computers collaborate on a task. They also facilitate resource sharing, increase reliability via redundancy, and allow for scalable computing power.
In conclusion, computer networks are a pivotal aspect of information technology, enabling data exchange and collaboration across various scales and distances.
500 Words Essay on Computer Network
Introduction to computer networks.
There are several types of computer networks, each designed to serve specific purposes. Local Area Networks (LAN) connect devices within a geographically limited area, such as a home or office. Wide Area Networks (WAN) span larger geographical areas, often encompassing multiple LANs. Metropolitan Area Networks (MAN) typically cover a city or town. Personal Area Networks (PAN) are designed for individual use, usually within a range of ten meters.
Components of a Computer Network
A computer network comprises several components. The primary ones are the servers, which store and provide data; clients, which request and receive data; network interface cards (NICs), which connect each computer to the network; switches, which direct data traffic; and routers, which connect different networks together.
Network Topologies
Network topology refers to the arrangement of elements in a network. Common topologies include the bus, star, ring, mesh, and tree. Each has its advantages and disadvantages in terms of cost, complexity, reliability, and performance.
Security in Computer Networks
As computer networks become more pervasive, security concerns grow. Network security encompasses measures to protect data from unauthorized access, misuse, malfunction, destruction, or improper disclosure. Techniques include firewalls, encryption, intrusion detection systems, and secure protocols like HTTPS.
Future of Computer Networks
Computer networks have profoundly impacted our lives, transforming how we communicate and access information. As technology continues to evolve, so too will computer networks, promising even greater connectivity, speed, and functionality. Understanding the intricacies of computer networks is essential for anyone venturing into the field of Information Technology or related disciplines.
If you’re looking for more, here are essays on other interesting topics:
Apart from these, you can look at all the essays by clicking here .
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
- Random article
- Teaching guide
- Privacy & cookies

Computer networks
by Chris Woodford . Last updated: April 6, 2023.
T hank goodness for computer networks! If they'd never been invented, you wouldn't be reading this now (using the Internet ) and I wouldn't be writing it either (using a wireless home network to link up my computer equipment). There's no doubt that computer networking is extremely complex when you delve into it deeply, but the basic concept of linking up computers so they can talk to one another is pretty simple. Let's take a closer look at how it works!
Photo: Linking PCs together in a network makes it possible to solve complex problems in new ways. This, for example, is an early cluster (a simple kind of supercomputer , made from networked PCs), that was used at NASA in the mid-1990s. Google's original data centers were also, famously, built from off-the-shelf clustered PCs like these. Photo courtesy of NASA Lewis Research Center and Internet Archive .
What is a computer network?
You can do lots of things with a computer but, connect it up to other computers and peripherals (the general name given to add-on bits of computer equipment such as modems , inkjet and laser printers , and scanners) and you can do an awful lot more. [1] A computer network is simply a collection of computer equipment that's connected with wires, optical fibers , or wireless links so the various separate devices (known as nodes ) can "talk" to one another and swap data (computerized information).

Artwork: The basic concept of a computer network: a collection of computers (and related equipment) hooked up with wired or wireless links so any machine can exchange information with any other.
Types of networks
Not all computer networks are the same. The network I'm using to link this laptop to my wireless router, printer, and other equipment is the smallest imaginable. It's an example of what's sometimes called a PAN (personal area network) —essentially a convenient, one-person network. If you work in an office, you probably use a LAN (local area network) , which is typically a few separate computers linked to one or two printers, a scanner, and maybe a single, shared connection to the Internet. Networks can be much bigger than this. At the opposite end of the scale, we talk about MANs (metropolitan area networks) , which cover a whole town or city, and WANs (wide area networks) , which can cover any geographical area. The Internet is a WAN that covers the entire world but, in practice, it's a network of networks as well as individual computers: many of the machines linked to the Net connect up through LANs operated by schools and businesses.
Computers are all about logic—and logic is all about following rules. Computer networks are a bit like the army: everything in a network has to be arranged with almost military precision and it has to behave according to very clearly defined rules. In a LAN, for example, you can't connect things together any old how: all the nodes (computers and other devices) in the network have to be connected in an orderly pattern known as the network topology . You can connect nodes in a simple line (also called a daisy chain or bus), with each connected to the next in line. You can connect them in a star shape with the various machines radiating out from a central controller known as the network server. Or you can link them into a loop (generally known as a ring). Other topologies include meshes (where each machine is directly connected to some of the others or all of them—which is called a full mesh) and trees (where small star networks are connected together in a line or bus). All the devices on a network also have to follow clearly defined rules (called protocols ) when they communicate to ensure they understand one another—for example, so they don't all try to send messages at exactly the same time, which causes confusion.
Artwork: The best-known computer network topologies: line (chain/bus), ring, star, mesh (where each node is connected to some of the others), full mesh (each node is connected to all the others), and tree (star networks connected in a line).
Permissions and security
Just because a machine is on a network, it doesn't automatically follow that every other machine and device has access to it (or can be accessed by it). The Internet is an obvious example. If you're online, you get access to billions of Web pages, which are simply files stored on other machines (servers) dotted all over the network. But you can't access every single file on every single computer hooked up to the Internet: you can't read my personal files and I can't read yours, unless we specifically choose for that to happen.
Artwork: Permissions: When you upload files to a web server, you have to decide what permissions to set: whether you, and other users, can read the file (read permission), change it (write permission), or run it (execute permission). That's why you can't automatically access every file on every web server and why you'll sometimes see a "Forbidden" error if you try to do so.
Permissions and security are central to the idea of networking: you can access files and share resources only if someone gives you permission to do so. Most personal computers that connect to the Internet allow outgoing connections (so you can, theoretically, link to any other computer), but block most incoming connections or prohibit them completely. Servers (the machines on the Internet that hold and serve up Web pages and other files) operate a more relaxed policy to incoming connections. You've probably heard of hacking , which, in one sense of the word, means gaining unauthorized access to a computer network by cracking passwords or defeating other security checks. To make a network more secure, you can add a firewall (either a physical device or a piece of software running on your machine, or both) at the point where your network joints onto another network or the Internet to monitor and prohibit any unauthorized, incoming access attempts.
What makes a network?
To make a network, you need nodes and connections (sometimes called links) between them. Linking up the nodes means making some sort of a temporary or permanent connection between them. In the last decade or so, wireless connections have become one of the most popular ways of doing this, especially in homes. In offices, wired connections are still more commonplace—not least because they are generally faster and more secure and because many newer offices have network cabling already in place.
Apart from computers, peripherals, and the connections between them, what else do you need? Each node on a network needs a special circuit known as a network card (or, more formally, a network interface card or NIC) to tell it how to interact with the network. Most new computers have network cards built in as standard. If you have an older computer or laptop, you may have to fit a separate plug-in circuit board (or, in a laptop, add a PCMCIA card) to make your machine talk to a network. Each network card has its own separate numeric identifier, known as a MAC (media access control) code or LAN MAC address. A MAC code is a bit like a phone number: any machine on the network can communicate with another one by sending a message quoting its MAC code. In a similar way, MAC codes can be used to control which machines on a network can access files and other shared resources. For example, I've set up my wireless link to the Internet so that only two MAC codes can ever gain access to it (restricting access to the network cards built into my two computers). That helps to stop other people in nearby buildings (or in the street) hacking into my connection or using it by mistake.
Photo: A typical wireless network card with its outer case removed so you can see what's inside. It consists of a pair of chips plus a radio transmitter/receiver antenna. The antenna sends data to (and receives data from) a wireless (Wi-Fi) network. The smaller chip manages that process and passes its data to the larger chip, which is called an Ethernet MAC/BBP (baseband processor). This converts the incoming data into a form your computer can understand—and turns outgoing data from your computer into a form the wireless antenna can ping out to nearby devices.
The bigger you make a network, the more extra parts you need to add to make it function efficiently. Signals can travel only so far down cables or over wireless links so, if you want to make a big network, you have to add in devices called repeaters —effectively signal boosters. You might also need bridges , switches , and routers —devices that help to link together networks (or the parts of networks, which are known as segments), regulate the traffic between them, and forward traffic from one part of a network to another part.
Photo: A wireless router like this one, made by Netgear, is the heart of many home PANs.
Understanding computer networks with layers
The osi model, the tcp/ip (darpa) model, networks on the fly, how ethernet works.
Not so long ago, computers were all made by different companies, worked in different ways, and couldn't communicate with one another. Often, they didn't even have the same sorts of plugs and sockets on their cases! During the 1980s and 1990s, everything became much more standardized and it's now possible to connect virtually any machine to any other and get them exchanging data without too much effort. That's largely because most networks now use the same system, called Ethernet . It was developed in May 1973 by US computer engineer Dr Robert ("Bob") Metcalfe (1946–), who went on to found 3Com and later became a well-known computer-industry pundit (perhaps, somewhat unfairly, best known for predicting, in 1995, a spectacular collapse of the Internet that never actually occurred).
Photo: A typical ethernet networking cable.
As Metcalfe originally designed it, Ethernet was based on three very simple ideas. First, computers would connect through the "ether" (a semi-serious, semi-scientific name for the void of emptiness that separates them) using standard coaxial cable (wires like the ones used in a television antenna connection, made up of concentric metal layers). In Ethernet-speak, the physical connection between the nodes (computers and other devices) on the network is also known as the medium . Things have moved on quite a bit since the early 1970s and the medium is now just as often a wireless radio link (you've probably heard of Wi-Fi , which is the wireless version of Ethernet). Second, all the computers and devices on a network would stay silent except for when they were sending or receiving messages. Finally, when they wanted to communicate, they'd do so by breaking up messages into small packets of data and sending them around the network by a highly efficient method known as packet switching (discussed in much more detail in our article on the Internet ).
What's in a frame?
Artwork: The main contents of an Ethernet frame are the preamble (initial "handshaking" information to let the sender and receiver synchronize), the receiver's and sender's MAC addresses, the type and length of data, the data itself, and a checksum (error correction data) at the end to make sure everything has been transmitted properly.
Find out more
- An interview with Bob Metcalfe : Manek Dubash offers this fascinating interview with the Ethernet pioneer to mark 40 years of his world-changing invention.
- Oral history of Bob Metcalfe : A much longer (almost three-hour) oral history interview with Len Shustek of The Computer History Museum.
How do computer networks detect errors?
Artwork: Checking the integrity of a large download with an MD5 code: If you've ever downloaded a Linux distribution (anything from a few hundred megabytes to several gigabytes of data), you've probably done this—or you certainly should have done! On the original download page, you'll be given an MD5 checksum code matching the file you want to download. Once your download is complete, you simply run the file through an MD5 calculator (easy in Linux, and here I'm doing it on Windows using winMd5sum) to calculate the MD5 code from the data you've downloaded. If the two MD5 codes match, you can be reasonably confident your file downloaded without any mistakes.
If you liked this article...
Don't want to read our articles try listening instead, on this website.
- History of communication
- History of computers
- Wireless Internet and Wi-Fi
For older readers
- Networking All-in-One For Dummies (7th Edition) by Doug Lowe. For Dummies, 2018. Covers topics such as how to build and secure a network, wireless and mobile devices, and everyday administration.
- Computer Networking: A Top-Down Approach by James F. Kurose and Keith W. Ross. Pearson Education, 2017. A comprehensive guide to networking written in a clear, engaging way with plenty of meaningful examples.
- Computer Networks by Andrew S. Tanenbaum and David J. Wetherall. Pearson, 2013. One of the best-known and most popular textbooks on networking, now in its fifth edition.
For younger readers
- Computer Networks by Clive Gifford. Wayland, 2015. An illustrated 32-page introduction for ages 8–10, focusing mainly on the Internet and the Web.
- Understanding Computer Networks by Matthew Anniss. Raintree/Capstone, 2015. A 48-page introduction for ages 9–12. Again, the focus is mainly on the Internet.
- Personal Virtual Networks Could Give Everyone More Control Over Their Data by Fahmida Y Rashid. IEEE Spectrum, February 14, 2020. Can network users be completely mobile and completely secure? Personal virtual networks (PVN) aim to give us the best of both worlds.
- How Internet Giants Upended the Networking-Hardware Business by Cade Metz. Wired, February 19, 2015. Facebook, Google, and Amazon have radically reinvented the hardware that connects the Internet together.
- OSI: The Internet That Wasn't by Andrew L. Russell. IEEE Spectrum, July 30, 2013. How eminently practical TCP/IP eclipsed the more conceptual, committee-driven OSI approach to networking.
- Metcalfe's Law is Wrong by Bob Briscoe, Andrew Odlyzko and Benjamin Tilly. IEEE Spectrum, July 1, 2006. Does "more users = better" always apply?
- Building Networks on the Fly by Robert Pascoe. IEEE Spectrum, March 1, 2001. How networking technologies like Bluetooth create improvised networks.
References ↑ This is a simple statement of what's sometimes called Metcalfe's Law , named for Ethernet-inventor Bob Metcalfe. ↑ This was originally published as ISO 7498:1984 , which has now been replaced by ISO/IEC 7498-1:1994 . ↑ The story is described in A Thread Across the Ocean The Heroic Story of the Transatlantic Cable by John Steele Gordon, HarperCollins, 2003 and The Cable The Wire That Changed the World by Gillian Cookson, The History Press, 2012. Please do NOT copy our articles onto blogs and other websites Articles from this website are registered at the US Copyright Office. Copying or otherwise using registered works without permission, removing this or other copyright notices, and/or infringing related rights could make you liable to severe civil or criminal penalties. Text copyright © Chris Woodford 2008, 2023. All rights reserved. Full copyright notice and terms of use . Follow us
Rate this page, tell your friends, cite this page, more to explore on our website....
- Get the book
- Send feedback

- Onsite training
3,000,000+ delegates
15,000+ clients
1,000+ locations
- KnowledgePass
- Log a ticket
01344203999 Available 24/7

What is a Computer Network? An Essential Overview
Curious about What is a Computer Network? It's a system of interconnected devices that communicate and share resources using wired or wireless connections. This blog explores the types of networks, their components, and how they impact modern communication. Let's dive in to understand the fundamentals of Computer Networks!

Exclusive 40% OFF
Training Outcomes Within Your Budget!
We ensure quality, budget-alignment, and timely delivery by our expert instructors.
Share this Resource
- CloudFlare Training
- Boomi Training Course
- IT Fundamentals Training

In a world where nearly every aspect of our lives is touched by technology, have you ever paused to wonder What is a Computer Network? This invisible force connects our devices, powers our communications, and drives the digital experiences we take for granted every day. But how does it work, and why is it so essential to modern life?
As you delve into the fascinating world of Computer Networks, you'll uncover the complexity behind what seems so effortless. But what exactly goes into building these networks? How do they manage to connect billions of devices globally, ensuring data flows smoothly from one point to another? Let’s explore the complexities of What is a Computer Network and how it shapes our digital reality.
Table of Contents
1) Decoding What is a Computer Network?
2) How Does a Computer Network Work?
3) Components of Computer Networks
4) Types of Computer Networks
5) Key Objectives of Establishing a Computer Network
6) Network Topologies
7) Conclusion
Decoding What is a Computer Network?
A Computer Network is a system where multiple devices, such as computers and servers, connect to share resources and data. These devices communicate using wired cables, wireless signals, or fibre optics. The main objective of a Computer Network is to enable efficient communication and collaboration between users by sharing files, applications, and internet access.
Networks can be small, like those in homes, or large and complex, like those in businesses or across the globe. The internet is the largest example, connecting millions of networks worldwide and allowing for global communication and resource sharing.

How Does a Computer Network Work?
A Computer Network is a sophisticated web of interconnected devices, and understanding how it works involves grasping the basics of data transmission, protocols, and network devices. The process begins with data encapsulation, where information is wrapped in multiple layers (headers and trailers) that contain crucial routing and control information.
Protocols, such as Transmission Control Protocol (TCP) and Internet Protocol (IP), govern this communication. TCP ensures data integrity and reliable transmission, while IP handles addressing and routing across the network.
Routing plays a pivotal role in directing data through the network. Routers, the traffic controllers of the digital highway, analyse destination addresses and determine the most efficient path for data packets. Switches further facilitate this journey by managing the flow of information within local segments, whereas hubs, now largely outdated, were once used to distribute data to multiple devices.
Essential network devices, including routers, switches, and hubs, collaborate to enable seamless connectivity. Routers connect different networks, switches facilitate communication within a network, and hubs serve as central points for data distribution. Each device contributes to efficient data flow, creating a dynamic network ecosystem.
Ultimately, a Computer Network operates as a collaborative orchestra, with each device playing a distinct role in ensuring that data travels swiftly and accurately from source to destination. This orchestrated symphony of protocols and devices forms the backbone of our interconnected digital world, enabling the instantaneous exchange of information that defines modern communication and collaboration.
Unlock your potential in Linux Server management with our expert-led Ubuntu Linux Server Administration Training – join now!
Components of Computer Networks
A Computer Network comprises several critical components, each playing a distinct role in shaping the network's functionality, efficiency, and security.
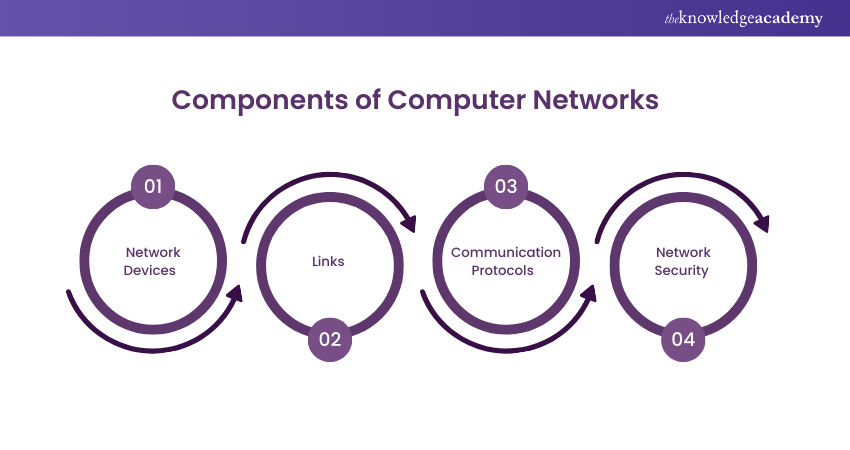
1) Network Devices
Network devices are the backbone of any Computer Network, facilitating communication and resource sharing. These devices include routers, switches, hubs, and access points. Routers direct data between different networks, while switches manage data flow within a network.
Though less common today, Hubs serve as central points for connecting devices. Access points enable wireless connectivity. Collectively, these devices create a cohesive network infrastructure that enables seamless communication and resource utilisation.
2) Links
Links form the physical or logical connections between network devices. Physical links involve cables, such as Ethernet or fibre optics, directly connecting devices. Logical links, on the other hand, are established through protocols and address assignments, creating a virtual connection. The quality and speed of links significantly impact the network's overall performance.
3) Communication Protocols
Communication protocols are rules governing data exchange between devices on a network. Protocols define how data is formatted, transmitted, received, and acknowledged.
Common protocols include Transmission Control Protocol (TCP), Internet Protocol (IP), and Hypertext Transfer Protocol (HTTP). Adhering to standardised protocols ensures interoperability among diverse devices and systems, fostering efficient and secure communication.
4) Network Security
Network security is important as it protects data and resources from unauthorised access, attacks, and breaches. This includes implementing firewalls, encryption mechanisms, and intrusion detection systems.
Security protocols like Secure Sockets Layer (SSL) and Virtual Private Network (VPN) are crucial in securing data during transmission. Robust network security ensures the integrity, confidentiality, and availability of information, safeguarding the network against potential threats.
Unlock the secrets of domain names and web hosting with our Introduction To Domain Names and Web Hosting Training - empower your online journey now!
Types of Computer Networks
Computer Networks come in diverse forms, each tailored to specific needs and scale. The array of Types of Computer Networks can be categorised based on their geographical scope and purpose.
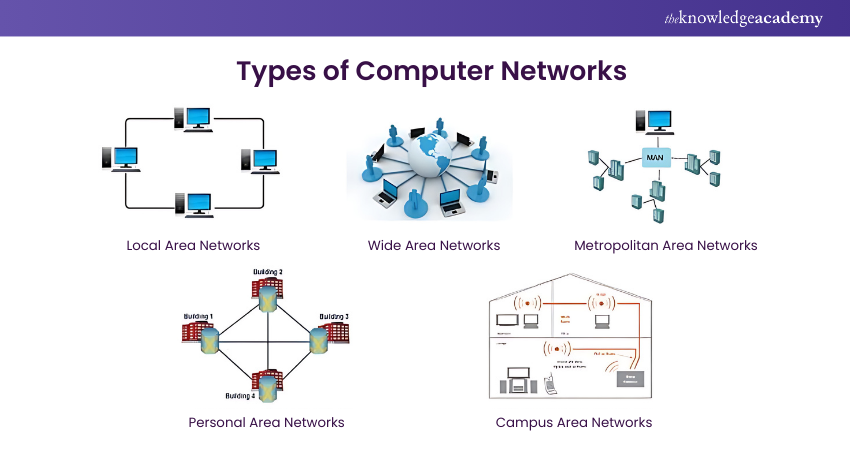
1) Local Area Networks (LANs)
A LAN connects devices within a small geographic area, such as a home, office, or school. It enables fast data sharing and communication between connected devices, typically using Ethernet or Wi-Fi.
2) Wide Area Networks (WANs)
A WAN spans a large geographic area, connecting multiple LANs across cities, countries, or even continents. It uses various transmission technologies and is often managed by telecommunications providers.
3) Metropolitan Area Networks (MANs)
A MAN covers a city or large campus, bridging multiple LANs within a metropolitan area. It offers high-speed connections for public or private use, often using fibre-optic or wireless links.
4) Personal Area Networks (PANs)
A PAN is a small network designed for personal devices, like smartphones, tablets, and laptops, typically within a range of a few meters. Bluetooth and USB are common technologies used in PANs.
5) Campus Area Networks (CANs)
A CAN connects multiple LANs within a limited geographic area, such as a university or corporate campus. It provides high-speed communication between buildings and is managed internally by the organisation.
6) Storage Area Networks (SANs)
A SAN is a specialised network that provides access to consolidated, block-level storage. It enables multiple servers to access shared storage devices, enhancing storage efficiency and data management.
7) Enterprise Private Networks (EPNs)
An EPN is a private network built and maintained by an organisation to securely connect various locations and departments. It ensures secure communication and resource sharing across the enterprise.
8) Service Provider Networks
These networks are managed by companies that lease network capacity and services to customers. They typically include telecommunications companies, data carriers, internet service providers, and cable television providers, offering essential connectivity and communication services.
9) Cloud Networks
A type of WAN, cloud networks utilise infrastructure provided by cloud-based services, like Amazon Web Services. This approach has become a standard for modern networking, offering scalable and flexible network solutions delivered through the cloud.
10) Virtual Private Networks (VPN)
By using a VPN, one can establish a private, encrypted connection across a public network, like the internet. It allows users to safely and remotely access a private network, protecting data from unauthorised access.
Secure your network with our VPN Training and enhance your Cyber Security skills today - register now!
Key Objectives of Establishing a Computer Network
In Computer Networks, establishing connectivity goes beyond mere technological interlinking; it revolves around achieving objectives that enhance overall system efficiency and foster collaboration. Here are the key objectives:
1) Shared Resource Utilisation
One of the primary objectives of a Computer Network is the efficient utilisation of shared resources. These resources can include hardware components like printers, scanners, and storage devices. By interconnecting devices, networks enable multiple users to access and use these resources simultaneously, optimising their utilisation.
2) Ensuring Resource Accessibility and Reliability
Networks are designed to ensure seamless resource accessibility, promoting data retrieval and utilisation reliability. Whether accessing files on a shared server or utilising a centrally connected printer, the objective is to guarantee that resources are readily available and dependable for all network users.
3) Efficient Performance Oversight
Computer Networks incorporate mechanisms to monitor and manage network performance. This involves tracking data transfer speeds, identifying potential bottlenecks, and ensuring consistent performance across the network. Efficient oversight contributes to a smooth and responsive network experience.
4) Economical Operations
Networks aim to streamline operations by reducing redundancy and optimising resource usage. This objective aligns with cost-effectiveness, ensuring the network infrastructure operates efficiently without unnecessary expenditures. Consolidating resources and centralising management contribute to economical network operations.
5) Expanded Storage Capability
Networks provide expanded storage capabilities through centralised servers and cloud solutions. This objective addresses the growing need for scalable storage solutions, allowing organisations to accommodate increasing data volumes without resorting to individual device upgrades.
6) Enhanced Collaboration and Communication Streamlining
A fundamental goal of Computer Networks is to enhance collaboration and streamline communication. Shared access to files, collaborative document editing, and real-time communication tools are integral. The network acts as a facilitator for efficient teamwork, breaking down geographical barriers.
7) Error Minimisation
Networks incorporate error detection and correction mechanisms to minimise data transmission errors. Robust protocols and algorithms ensure data integrity during transmission, contributing to the reliability and accuracy of information exchange.
8) Secure Remote Access
Enabling secure remote access is a crucial objective, especially in the modern work landscape. Networks implement security protocols to safeguard data during remote access, allowing users to connect securely to the network from different locations.
Enhance your IT expertise by mastering CloudFlare Training - secure, optimise, and accelerate your web applications today!
Network Topologies
Network Topologies define the physical or logical layout of interconnected devices in a Computer Network, influencing communication, scalability, and fault tolerance. Several common Network Topologies are employed based on specific requirements and considerations:
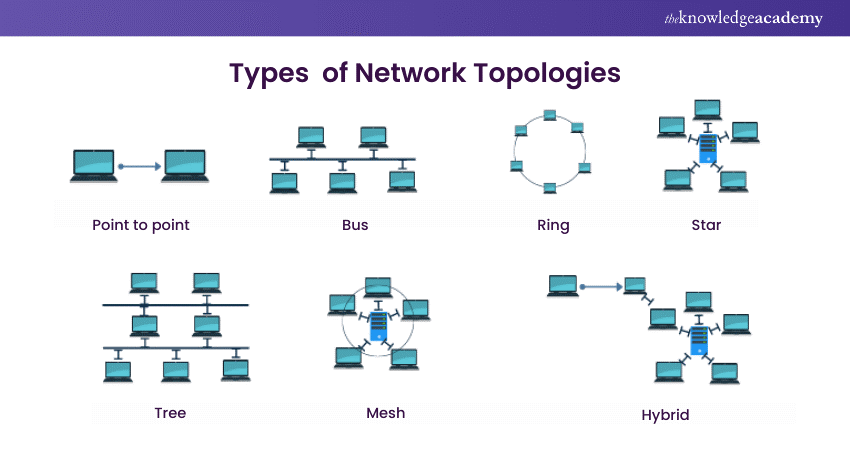
1) Point-to-point Network Topology
Two devices are directly connected in a point-to-point Network Topology, creating a dedicated communication channel. It's a simple and efficient setup used in telecommunications, providing a direct link for data exchange.
2) Bus Topology
In a bus topology, devices share a single communication line or "bus." Data travels along this central cable, and each device on the network receives the data. While simple and cost-effective, bus topologies can experience performance issues as the number of connected devices increases.
3) Star Topology
Each device is connected directly to a central hub or switch in a Star Topology. The hub acts as a central point for data exchange. Star topologies offer easy scalability and efficient fault isolation since the failure of one connection doesn't affect others. However, they may require more cabling.
4) Ring Topology
In a Ring Network Topology, devices form a closed loop, and data travels in one direction. Each device is connected to precisely two neighbours. While this structure simplifies network management, a failure in any single connection can disrupt the entire network.

5) Tree Topology
Tree topology is a hierarchical network structure where devices are arranged in a tree-like format. A central hub connects multiple secondary hubs or devices, forming a branching structure. This design enhances scalability and allows for efficient data flow and network expansion.
6) Mesh Topology
Mesh topologies involve direct connections between every device, creating redundancy and multiple communication paths. This redundancy enhances fault tolerance, as data can take alternative routes if one path fails. However, the extensive cabling and setup complexity are considered.
7) Hybrid Topology
Hybrid topologies combine elements of two or more topologies to meet specific needs. For example, a network might incorporate aspects of both star and bus topologies. This approach allows organisations to tailor their networks to balance efficiency, scalability, and fault tolerance.
Empower your IT career by gaining crucial skills through our expert-led IT Support and Solution Training – Sign up today!
Conclusion
Uncovering What is a Computer Network reveals the powerful web connecting our world. These systems, from their core components to diverse types and topologies, are the heartbeat of modern communication. As our reliance on connectivity grows, understanding networks is key to navigating and shaping the future.
Gain insights into Networking with our Introduction to Networking Training – Join today!
Frequently Asked Questions
Computer Networks enable seamless communication, resource sharing, and connectivity. They form the backbone of our digital world, powering everything from online services to global collaboration.
Network components like routers, switches, and protocols ensure efficient data transmission, secure connections, and seamless communication. Every component plays an essential role in maintaining the network's stability, speed, and reliability.
The Knowledge Academy takes global learning to new heights, offering over 30,000 online courses across 490+ locations in 220 countries. This expansive reach ensures accessibility and convenience for learners worldwide.
Alongside our diverse Online Course Catalogue, encompassing 17 major categories, we go the extra mile by providing a plethora of free educational Online Resources like News updates, Blogs , videos, webinars, and interview questions. Tailoring learning experiences further, professionals can maximise value with customisable Course Bundles of TKA .
The Knowledge Academy’s Knowledge Pass , a prepaid voucher, adds another layer of flexibility, allowing course bookings over a 12-month period. Join us on a journey where education knows no bounds.
The Knowledge Academy offers various IT Support and Solution Training , including Introduction to Networking Training, Ubuntu Linux Server Administration Training and VPN Training. These courses cater to different skill levels, providing comprehensive insights into Star Topology .
Our IT Infrastructure & Networking Blogs cover a range of topics related to Computer Network, offering valuable resources, best practices, and industry insights. Whether you are a beginner or looking to advance your Knowledge of Computer Networks, The Knowledge Academy's diverse courses and informative blogs have got you covered.
Upcoming IT Infrastructure & Networking Resources Batches & Dates
Fri 18th Oct 2024
Fri 29th Nov 2024
Fri 13th Dec 2024
Fri 7th Feb 2025
Fri 4th Apr 2025
Fri 6th Jun 2025
Fri 8th Aug 2025
Fri 3rd Oct 2025
Fri 5th Dec 2025
Get A Quote
WHO WILL BE FUNDING THE COURSE?
My employer
By submitting your details you agree to be contacted in order to respond to your enquiry
- Business Analysis
- Lean Six Sigma Certification
Share this course
Our biggest summer sale.

We cannot process your enquiry without contacting you, please tick to confirm your consent to us for contacting you about your enquiry.
By submitting your details you agree to be contacted in order to respond to your enquiry.
We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.
Or select from our popular topics
- ITIL® Certification
- Scrum Certification
- ISO 9001 Certification
- Change Management Certification
- Microsoft Azure Certification
- Microsoft Excel Courses
- Explore more courses
Press esc to close
Fill out your contact details below and our training experts will be in touch.
Fill out your contact details below
Thank you for your enquiry!
One of our training experts will be in touch shortly to go over your training requirements.
Back to Course Information
Fill out your contact details below so we can get in touch with you regarding your training requirements.
* WHO WILL BE FUNDING THE COURSE?
Preferred Contact Method
No preference
Back to course information
Fill out your training details below
Fill out your training details below so we have a better idea of what your training requirements are.
HOW MANY DELEGATES NEED TRAINING?
HOW DO YOU WANT THE COURSE DELIVERED?
Online Instructor-led
Online Self-paced
WHEN WOULD YOU LIKE TO TAKE THIS COURSE?
Next 2 - 4 months
WHAT IS YOUR REASON FOR ENQUIRING?
Looking for some information
Looking for a discount
I want to book but have questions
One of our training experts will be in touch shortly to go overy your training requirements.
Your privacy & cookies!
Like many websites we use cookies. We care about your data and experience, so to give you the best possible experience using our site, we store a very limited amount of your data. Continuing to use this site or clicking “Accept & close” means that you agree to our use of cookies. Learn more about our privacy policy and cookie policy cookie policy .
We use cookies that are essential for our site to work. Please visit our cookie policy for more information. To accept all cookies click 'Accept & close'.
CS 243, Fall 2019: Advanced Computer Networks
This is a graduate-level course on computer networks. It provides a comprehensive overview on advanced topics in network protocols and networked systems. The course will cover both classic papers on computer networks and recent research results. It will examine a wide range of topics including routing, congestion control, network architectures, network management, datacenter networks, software-defined networking, and programmable networks, with an emphasis on core networking concepts and principles and their usage in practice. The course will include lectures, in-class presentations, paper discussions, and a research project.
- Instructor: Minlan Yu (MD 137)
- Lecture time: MW 1:30pm-2:45pm
- Location: TBD
- Office hour: We have unlimited office hours to discuss course projects. Please just email the instructor to schedule the time. We also have walk-in office hour time on Monday 12:30-1:30, MD 137
- Discussion list: Piazza
- Recommended prep: system programming at the level of CS 61 or CS 143 or CS 145.
- Project: 50%
- Reviews: 30%
- Class presentation: 20%
Review format
Class presentation, presentation format, project timeline, project proposal presentation, midterm project report, final project presentations, final project report, code submission, evaluation testbed, diversity and inclusion, accommodations for disabilities.
Last updated: 2019-10-16 11:59:11 -0400 [ validate xhtml ]
The Usefulness of Computer Networks for Students Essay (Critical Writing)
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
Computer network is the interconnection of many resourceful computers through domains which provide users with the possibility to freely share ideas, information and other useful resources. In my class setup, computer network has played a big role in construction of knowledge among my fellow learners. One major role which computer network plays in imparting knowledge is implemented through sharing of ideas.
According to Resnick (1996), learning is described as an active process where knowledge is constructed from various experiences in the world, thus making ideas rather than getting them. Through computer network, my fellow learners share various ideas they have made in the process and this became available to all of us. We are able to access various ideas, disseminate, and improve them which results in the splendid end product.
Computer network has also enabled us to collaborate in real-time through chatting and using newsgroup forums where we communicate freely among learners which results into enhancement and construction of new knowledge. The network has enabled us to make computer simulations in various projects we are undertaking and which are tested by other learners who act as users of the constructed simulations.
The feedback obtained from the users helps us improve on our simulations through active participation on the internet. In the absence of computer network in the school environment, learners can use physical discussion forums where we can meet in study rooms, meeting places and still share ideas thus extending distributed constructionism.
Learners can also record their findings and work with electronic tapes, e.g. flash disks, compact disks and post them via postal mails to their colleagues. Mobile phones text messages can also be used to share ideas and resources hence promoting distributed constructionism.
Computer network and the Internet act as Rorschach test for educational philosophy whereby it can be interpreted into many ways. Through my own educational philosophy, I see the internet as a way of life throughout the world.
To defend my philosophical view, the internet has enabled the entire world to become a global village whereby users share their daily life experience hence making the internet as a virtual way of life. The information shared on the internet can be used by various users depending on their area of interest.
Pea’s idea of enabling educators to facilitate individuals from tool-free cognition is a feasible and realistic idea which can be adopted at any level of learning (Pea, 1993). Distributed intelligence and cognition are defined as a theoretical approach that focuses on interaction between individuals and other factors that are depend on how they are approached and implemented.
The theory is realistic in that no individual is an island of his own information and students get to know things through interaction with other people. This can range from interaction with cultural influences, material artifacts and with any other social activity. To facilitate Pea’s idea, educators need to understand the level of grade they are teaching.
Lower grade students need to use simple simulations and resources which they can easily understand as opposed to adult learners who can understand complex simulations. Learners who will have access to information will learn faster than those who will have limited information.
Computers cannot replace the role of adults in guiding the children for 100%, but they can play a very big role in imparting knowledge to youngsters. This notion is applicable where computer intelligence is as a result of A customized software which has been programmed by various technocrats through distributed constructionism, tested by various users and finally presented to the educators for the purpose of teaching children.
The use of computer intelligence should not be limited to children and their ZPD only, but should also be applied to adults as well. The determinant factor when using computer intelligence should be the selection of learning tools.
In this case, educators should select learning tools depending on the level of the learners to facilitate distributed cognition. Educators should also break down a problem in question into simple manageable levels for the learners to understand.
In my learning environment, I have personally experienced computers substituting the skilled other. In this case, computer simulations were used to state and represent a problem. This was done by using whiteboard diagrams which broke the problem down into manageable levels that can be understood.
Pea, R.D. (1993). Practices of distributed intelligence and designs for education. In G. Salomon (Ed.), Distributed cognitions, Psychological and educational considerations (pp. 47-87) . NY: Cambridge University Press. peaDistrib.pdf
Resnick, M. (1996). Distributed Constructionism. Proceedings of the International Conference on the Learning Sciences Association for the Advancement of Computing in Education Northwestern University . Retrieved from
- Article Review on Technology in Education
- The changing role of technology in higher education
- Anthophyta. Plant Analysis
- The Foucauldian concept of discourse In book Social Constructionism by Vivian Burr
- Social Constructionism and Microaggressions
- The Educational Promise of Social Media
- How the technology impact education
- The Impact of Technology in Education
- The use of innovative technologies for teaching new Spanish vocabulary
- Computer Technology in Education
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2019, May 29). The Usefulness of Computer Networks for Students. https://ivypanda.com/essays/the-usefulness-of-computer-networks-for-students-critical-writing/
"The Usefulness of Computer Networks for Students." IvyPanda , 29 May 2019, ivypanda.com/essays/the-usefulness-of-computer-networks-for-students-critical-writing/.
IvyPanda . (2019) 'The Usefulness of Computer Networks for Students'. 29 May.
IvyPanda . 2019. "The Usefulness of Computer Networks for Students." May 29, 2019. https://ivypanda.com/essays/the-usefulness-of-computer-networks-for-students-critical-writing/.
1. IvyPanda . "The Usefulness of Computer Networks for Students." May 29, 2019. https://ivypanda.com/essays/the-usefulness-of-computer-networks-for-students-critical-writing/.
Bibliography
IvyPanda . "The Usefulness of Computer Networks for Students." May 29, 2019. https://ivypanda.com/essays/the-usefulness-of-computer-networks-for-students-critical-writing/.
IvyPanda uses cookies and similar technologies to enhance your experience, enabling functionalities such as:
- Basic site functions
- Ensuring secure, safe transactions
- Secure account login
- Remembering account, browser, and regional preferences
- Remembering privacy and security settings
- Analyzing site traffic and usage
- Personalized search, content, and recommendations
- Displaying relevant, targeted ads on and off IvyPanda
Please refer to IvyPanda's Cookies Policy and Privacy Policy for detailed information.
Certain technologies we use are essential for critical functions such as security and site integrity, account authentication, security and privacy preferences, internal site usage and maintenance data, and ensuring the site operates correctly for browsing and transactions.
Cookies and similar technologies are used to enhance your experience by:
- Remembering general and regional preferences
- Personalizing content, search, recommendations, and offers
Some functions, such as personalized recommendations, account preferences, or localization, may not work correctly without these technologies. For more details, please refer to IvyPanda's Cookies Policy .
To enable personalized advertising (such as interest-based ads), we may share your data with our marketing and advertising partners using cookies and other technologies. These partners may have their own information collected about you. Turning off the personalized advertising setting won't stop you from seeing IvyPanda ads, but it may make the ads you see less relevant or more repetitive.
Personalized advertising may be considered a "sale" or "sharing" of the information under California and other state privacy laws, and you may have the right to opt out. Turning off personalized advertising allows you to exercise your right to opt out. Learn more in IvyPanda's Cookies Policy and Privacy Policy .
24/7 writing help on your phone
To install StudyMoose App tap and then “Add to Home Screen”
What is Computer Network?
Save to my list
Remove from my list
Introduction

FractalApps Requirements Analysis
Proposed solution.
What is Computer Network?. (2016, Apr 24). Retrieved from https://studymoose.com/what-is-computer-network-essay
"What is Computer Network?." StudyMoose , 24 Apr 2016, https://studymoose.com/what-is-computer-network-essay
StudyMoose. (2016). What is Computer Network? . [Online]. Available at: https://studymoose.com/what-is-computer-network-essay [Accessed: 13 Sep. 2024]
"What is Computer Network?." StudyMoose, Apr 24, 2016. Accessed September 13, 2024. https://studymoose.com/what-is-computer-network-essay
"What is Computer Network?," StudyMoose , 24-Apr-2016. [Online]. Available: https://studymoose.com/what-is-computer-network-essay. [Accessed: 13-Sep-2024]
StudyMoose. (2016). What is Computer Network? . [Online]. Available at: https://studymoose.com/what-is-computer-network-essay [Accessed: 13-Sep-2024]
- Network Simulation for Network Technology Investigation Pages: 27 (7853 words)
- Image Processing By Neural Network Computer Science Essay Pages: 5 (1299 words)
- Introduction to Computer Organization and Computer Evolution Pages: 15 (4222 words)
- Ai Application On Human Computer Interaction Computer Science Essay Pages: 9 (2407 words)
- Vodafone mobile network Pages: 6 (1795 words)
- Too Far Ahead of the IT Curve: Peachtree Network Issues Pages: 6 (1674 words)
- Task dependencies in developing project network diagram Pages: 3 (658 words)
- Tourism Network and Supply Components Pages: 11 (3100 words)
- A network is simply several pointsnodes that are connected to Pages: 6 (1720 words)
- Network Administrator Career Episode Pages: 6 (1667 words)

👋 Hi! I’m your smart assistant Amy!
Don’t know where to start? Type your requirements and I’ll connect you to an academic expert within 3 minutes.
Home — Essay Samples — Information Science and Technology — Computer — The role of Computer Networks in modern world
The Role of Computer Networks in Modern World
- Categories: Computer Computer Software
About this sample

Words: 777 |
Published: Mar 14, 2019
Words: 777 | Pages: 2 | 4 min read

Cite this Essay
To export a reference to this article please select a referencing style below:
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Dr. Karlyna PhD
Verified writer
- Expert in: Information Science and Technology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
2 pages / 767 words
2 pages / 989 words
4 pages / 2031 words
2 pages / 798 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online

Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Computer
Internet of Things (IoT) is a system of integrated technology that authorizes interaction of distinctively connected computing devise which could be rooted with other interfaces like humans or machines, associated via wired and [...]
Computer technology has had a deep impact on the education sector. The following are the importance of ICT in education as retrieved from several journals and databases. 1. Computers are a brilliant aid in teaching. [...]
One of the primary input device used with a computer that looks similar to those found on electric type-writers is a computer keyboard, but with some additional keys. Keyboard allows you to input letter, number and other symbol [...]
Though most students use computers for video games and social media, computers also hold a huge role in education in today’s world. Most high schools prepare students for college by having computer labs; where students can gain [...]
USB, the Universal Serial Bus has been around for decades and is a heavily used standard in the world of personal computers. Memory sticks, external drives, mice, and web cameras are all interfaced over USB. In this article we [...]
Other name of Malware is malevolent programming. This product was created by digital assailants with the point of adopting strategy or reason for harm to a PC or system. A few people call it by the name of PC infection. However, [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
What is Computer Networking?
Computer networking is like having a group of friends who all have phones and can call or text each other. In computer networking, instead of phones, we have computers and instead of phone lines, we use cables, Wi-Fi, or other methods to connect them. When computers are connected to a network, they can share information and resources, like files, printers, and internet connections. This allows them to communicate with each other quickly and easily, just like friends talking on their phones.
A computer network consists of various kinds of nodes. Servers, networking hardware, personal computers, and other specialized or general-purpose hosts can all be nodes in a computer network. Hostnames and network addresses are used to identify them. In this article, we are going to discuss computer networking in detail.

Computer Networking
What is a Computer Network?
A computer network is a system that connects many independent computers to share information (data) and resources. The integration of computers and other different devices allows users to communicate more easily. A computer network is a collection of two or more computer systems that are linked together. A network connection can be established using either cable or wireless media. Hardware and software are used to connect computers and tools in any network.
What Do Computer Networks Do?
Computer Networks are one of the important aspects of Computer Science. In the early days, it is used for data transmission on telephone lines and had a very limited use, but nowadays, it is used in a variety of places.
Computer Networks help in providing better connectivity that helps nowadays. Modern computer networks have the following functionality:
- Computer Networks help in operating virtually
- Computer Networks integrate on a large scale
- Computer Networks respond very quickly in case of conditions change
- Computer Networks help in providing data security
Key Components of a Computer Network
In simple terms, a computer network is made up of two main parts: devices (called nodes) and connections (called links). The links connect the devices to each other. The rules for how these connections send information are called communication protocols. The starting and ending points of these communications are often called ports .

Key Components of Computer Network
1. Network Devices
Basic hardware interconnecting network nodes, such as Network Interface Cards (NICs), Bridges, Hubs, Switches, and Routers, are used in all networks. In addition, a mechanism for connecting these building parts is necessary, which is usually galvanic cable and optical cable are less popular (“optical fiber”)The following are the network devices :
- NIC (Network Interface Card): A network card, often known as a network adapter or NIC (network interface card), is computer hardware that enables computers to communicate via a network. It offers physical access to networking media and, in many cases, MAC addresses serve as a low-level addressing scheme. Each network interface card has a distinct identifier. This is stored on a chip that is attached to the card.
- Repeater: A repeater is an electrical device that receives a signal, cleans it of unwanted noise, regenerates it, and retransmits it at a higher power level or to the opposite side of an obstruction, allowing the signal to travel greater distances without degradation. In the majority of twisted pair Ethernet networks, Repeaters are necessary for cable lengths longer than 100 meters in some systems. Repeaters are based on physics.
- Hub: A hub is a device that joins together many twisted pairs or fiber optic Ethernet devices to give the illusion of a formation of a single network segment. The device can be visualized as a multiport repeater. A network hub is a relatively simple broadcast device. Any packet entering any port is regenerated and broadcast out on all other ports, and hubs do not control any of the traffic that passes through them. Packet collisions occur as a result of every packet being sent out through all other ports, substantially impeding the smooth flow of communication.
- Bridges: Bridges broadcast data to all the ports but not to the one that received the transmission. Bridges, on the other hand, learn which MAC addresses are reachable through specific ports rather than copying messages to all ports as hubs do. Once a port and an address are associated, the bridge will only transport traffic from that address to that port.
- Switches: A switch differs from a hub in that it only forwards frames to the ports that are participating in the communication, rather than all of the ports that are connected. The collision domain is broken by a switch, yet the switch depicts itself as a broadcast domain. Frame-forwarding decisions are made by switches based on MAC addresses.
- Routers: Routers are networking devices that use headers and forwarding tables to find the optimal way to forward data packets between networks. A router is a computer networking device that links two or more computer networks and selectively exchanges data packets between them. A router can use address information in each data packet to determine if the source and destination are on the same network or if the data packet has to be transported between networks. When numerous routers are deployed in a wide collection of interconnected networks, the routers share target system addresses so that each router can develop a table displaying the preferred pathways between any two systems on the associated networks.
- Gateways: To provide system compatibility, a gateway may contain devices such as protocol translators, impedance-matching devices, rate converters, fault isolators, or signal translators. It also necessitates the development of administrative procedures that are acceptable to both networks. By completing the necessary protocol conversions, a protocol translation/mapping gateway joins networks that use distinct network protocol technologies.
Links are the ways information travels between devices, and they can be of two types:
- Wired: Communication done in a wired medium . Copper wire, twisted pair, or fiber optic cables are all options. A wired network employs wires to link devices to the Internet or another network, such as laptops or desktop PCs.
- Wireless: Wireless means without wire, media that is made up of electromagnetic waves (EM Waves) or infrared waves. Antennas or sensors will be present on all wireless devices. For data or voice communication, a wireless network uses radio frequency waves rather than wires.
3. Communication Protocols
A communication protocol is a set of rules that all devices follow when they share information. Some common protocols are TCP/IP, IEEE 802, Ethernet, wireless LAN, and cellular standards. TCP/IP is a model that organizes how communication works in modern networks. It has four functional layers for these communication links:
- Network Access Layer : This layer controls how data is physically transferred, including how hardware sends data through wires or fibers.
- Internet Layer : This layer packages data into understandable packets and ensures it can be sent and received.
- Transport Layer : This layer keeps the communication between devices steady and reliable.
- Application Layer : This layer allows high-level applications to access the network to start data transfer.
Most of the modern internet structure is based on the TCP/IP model, although the similar seven-layer OSI model still has a strong influence.
IEEE 802 is a group of standards for local area networks (LAN) and metropolitan area networks (MAN). The most well-known member of the IEEE 802 family is wireless LAN, commonly known as WLAN or Wi-Fi.
4. Network Defense
While nodes, links, and protocols are the building blocks of a network, a modern network also needs strong defenses. Security is crucial because huge amounts of data are constantly being created, moved, and processed. Some examples of network defense tools are firewalls, intrusion detection systems ( IDS ), intrusion prevention systems ( IPS ), network access control ( NAC ), content filters, proxy servers, anti-DDoS devices, and load balancers.
How Does a Computer Network Work?
Computer Networks simply work using nodes and links. Data communication equipment is simply termed as Nodes. For example, Modems , Hubs, Switches, etc. whereas links in Computer networks can be referred to as a connection between two nodes. We have several types of links like cable wires, optical fibers , etc.
Whenever a Computer Network is working, nodes have the work of sending and receiving data via the links. Computer Network provides some set of protocols that help in following the rules and protocols.
Criteria of a Good Network
- Performance: It can be measured in many ways, including transmit time and response time. Transit time is the amount of time required for a message to travel from one device to another. Response time is the elapsed time between an inquiry and a response. The performance of the network depends on a number of factors, including the number of users, the type of medium & Hardware.
- Reliability: In addition to accuracy is measured by frequency of failure, the time it takes a link to recover from failure, and the network’s robustness in catastrophe.
- Security: Network security issues include protecting data from unauthorized access, protecting data from damage and development, and implementing policies and procedures for recovery from breaches and data loss.
Goals of Computer Networking
- Programs do not have to execute on a single system because of resource and load sharing
- Reduced costs – Multiple machines can share printers, tape drives, and other peripherals
- Reliability – If one machine fails, another can take its place
- Scalability (it’s simple to add more processors or computers)
- Communication and mail (people living apart can work together)
- Information Access (remote information access, access to the internet, e-mail, video conferencing, and online shopping)
- Entertainment that is interactive (online games, videos, etc.)
- Social Networking
Types of Computer Networks
Division based on area covered.
- Local Area Network (LAN): A LAN is a network that covers an area of around 10 kilometers. For example, a college network or an office network. Depending upon the needs of the organization, a LAN can be a single office, building, or Campus. We can have two PCs and one printer in-home office or it can extend throughout the company and include audio and video devices. Each host in LAN has an identifier, an address that defines hosts in LAN. A packet sent by the host to another host carries both the source host’s and the destination host’s address.
- Metropolitan Area Network (MAN): MAN refers to a network that covers an entire city. For example: consider the cable television network.
- Point To Point : Connects two connecting devices through transmission media.
- Switched: A switched WAN is a network with more than two ends.
Based on Types of Communication
- Point To Point networks: Point-to-Point networking is a type of data networking that establishes a direct link between two networking nodes. A direct link between two devices, such as a computer and a printer, is known as a point-to-point connection.
- Multipoint : is the one in which more than two specific devices share links. In the multipoint environment, the capacity of the channel is shared, either spatially or temporally. If several devices can use the link simultaneously, it is a spatially shared connection.
- Broadcast networks: In broadcast networks , a signal method in which numerous parties can hear a single sender. Radio stations are an excellent illustration of the “Broadcast Network” in everyday life. The radio station is a sender of data/signal in this scenario, and data is only intended to travel in one direction. Away from the radio transmission tower, to be precise.
Based on the Type of Architecture
- P2P Networks: Computers with similar capabilities and configurations are referred to as peers. The “peers” in a peer-to-peer network are computer systems that are connected to each other over the Internet. Without the use of a central server, files can be shared directly between systems on the network.
- Client-Server Networks: Each computer or process on the network is either a client or a server in a client-server architecture (client/server). The client asks for services from the server, which the server provides. Servers are high-performance computers or processes that manage disc drives (file servers), printers (print servers), or network traffic (network servers)
- Hybrid Networks: The hybrid model uses a combination of client-server and peer-to-peer architecture. Eg: Torrent.
Types of Computer Network Architecture
Computer Network Architecture is of two types. These types are mentioned below.
- Client-Server Architecture: Client-Server Architecture is basically the architecture where the clients and the server are connected as two clients can communicate with each other and the devices present work as servers in the network.
- Peer-to-Peer Architecture: Peer-to-Peer Architecture , computers are connected to each other and each computer is equally capable of working as there is no central server here. Each device present here can be used as a client or server.
Types of Enterprise Computer Networks
There are three main types of Enterprise Computer Networks which are mentioned below.
- Local Area Network (LAN): Local Area Networks are small-scale networks used in small companies or as test networks. It has a limited size.
- Wide Area Networks (WAN): Wide Area Networks are networks that are used for a larger area than local area networks and are used for long-distance communication.
- Service Provider Networks: Service Provider Networks are the networks that help in wireless communication, high-speed internet access, etc.
Key Objectives of Creating and Deploying a Computer Network
No industry—whether it’s education, retail, finance, tech, government, or healthcare—can function without well-designed computer networks. The larger the organization, the more complex the network becomes. Before starting the challenging job of creating and setting up a computer network, here are some key objectives to consider.
1. Resource Sharing
Today’s enterprises are spread across the globe, with critical assets being shared across departments, geographies, and time zones. Clients are no more bound by location. A network allows data and hardware to be accessible to every pertinent user. This also helps with interdepartmental data processing. For example, the marketing team analyzes customer data and product development cycles to enable executive decisions at the top level.
2. Resource Availability & Reliability
A network ensures that resources are not stuck in isolated areas and can be accessed from multiple locations. High reliability comes from having various sources of supply. Important resources are backed up across multiple machines, so they remain accessible even if there are hardware problems.
3. Performance Management
As a company grows, its workload increases. Adding one or more processors to the network boosts the overall performance of the system and allows it to handle this growth. Storing data in well-designed databases can significantly speed up searching and retrieving information.
4.Cost Savings
Big mainframe computers are costly, so it’s smarter to add processors strategically throughout the system. This boosts performance and saves money. Networks let employees access information quickly, saving operational time and costs. Centralized network administration means fewer investments are needed for IT support .
5. Increased Storage Capacity
Network-attached storage devices are great for employees who handle lots of data. For instance, the data science team doesn’t each need their own data storage for the large number of records they process. Centralized repositories are more efficient. As businesses deal with record amounts of customer data, the ability to expand storage capacity is crucial .
6. Streamlined Collaboration & Communication
Networks greatly influence how companies operate daily. Employees can share files, see each other’s work, sync calendars, and exchange ideas more efficiently. Internal messaging systems like Slack facilitate easy flow of information and conversations within modern enterprises. However, emails remain the formal mode of communication with clients, partners, and vendors.
7. Reduction of Errors
Networks decrease errors by ensuring everyone gets information from one source, even if they’re in different places. Backed-up data ensures consistency and continuity. Standard versions of customer and employee manuals can be easily accessed by many people without much trouble .
8. Secured Remote Access
Computer networks offer flexibility, which is crucial during uncertain times like now when natural disasters and pandemics are affecting the world. A secure network guarantees that users can access and work on sensitive data safely, even when they’re not at the company’s location. Mobile devices registered to the network can also provide multiple layers of authentication, ensuring that unauthorized users can’t access the system.
What is Network Topology?
The structure of the network and how each component is connected to the others are defined by the network topology. Different types of network topology are mentioned below:
Bus Topology
Ring Topology
Star Topology
Mesh Topology
Tree Topology
Every computer and network device is connected to a single cable in a bus topology network. Linear Bus topology is defined as having exactly two terminals.
- Installation is simple
- Compared to mesh, star, and tree topologies, the bus utilizes less cabling
Disadvantages
- Difficulty in reconfiguring and isolating faults
- A bus cable malfunction or break interrupts all communication
For more, you can refer to the Advantages and Disadvantages of Bus Topology.

The topology is named ring topology because one computer is connected to another, with the final one being connected to the first. Exactly two neighbors for each device. A signal is passed along the ring in one direction. Each ring incorporates a repeater.
- Data transmission is relatively straightforward because packets only move in one direction
- There is no requirement for a central controller to manage communication between nodes
- Easy installation & Reconfiguration
- Simplified Faulty connections
- In a Unidirectional Ring, a data packet must traverse through all nodes
- All computers must be turned on in order for them to connect with one another
For more, you can refer to the Advantages and Disadvantages of Ring Topology.

Each device in a star topology has a dedicated point-to-point link to a central controller, which is commonly referred to as the HUB. There is no direct connection between the devices. Traffic between the devices is not allowed in this topology. As an exchange, the controller is used.
- When attaching or disconnecting devices, there are no network interruptions
- It’s simple to set up and configure
- Identifying and isolating faults is simple
- Less Expensive than mesh
- Easy to install & configure
- Nodes attached to the hub, switch, or concentrator is failed if they fail
- Because of the expense of the hubs, it is more expensive than linear bus topologies
- More cable is required compared to a bus or ring
- Too much dependency on Hub
For more, you can refer to the Advantages and Disadvantages of Star Topology .
Example: Used in high-speed LANs

Every device in a mesh topology has dedicated point-to-point connectivity to every other device. The term “dedicated” refers to the fact that the link exclusively transports data between the two devices it links. To connect n devices, a fully connected mesh network contains n *(n-1)/2 physical channels.
- Data can be sent from multiple devices at the same time. This topology can handle a lot of traffic.
- Even if one of the connections fails, a backup is always available. As a result, data transit is unaffected.
- Physical boundaries prevent other users from gaining access to messages.
- Point to Point links make fault transmission & fault isolation easy.
- The amount of cabling and the number of I/O ports that are necessary.
- The sheer bulk of wiring can be greater than the available space can accommodate.
- It is difficult to install and reconfigure.
For more, you can refer to the Advantages and Disadvantages of Mesh Topology .
Example: connection of telephone regional office in which each regional office needs to be connected to every other regional office.

The topology of a tree is similar to that of a star. Nodes in a tree, like those in a star, are connected to a central hub that manages network traffic. It has a root node, which is connected to all other nodes, producing a hierarchy. Hierarchical topology is another name for it. The number of Star networks is connected via Bus in Tree Topology.
- Network expansion is both possible and simple.
- We partition the entire network into pieces (star networks) that are easier to manage and maintain.
- Other segments are unaffected if one segment is damaged.
- Tree topology relies largely on the main bus cable because of its basic structure, and if it fails, the entire network is handicapped.
- Maintenance becomes more challenging when more nodes and segments are added.
For more, you can refer to the Advantages and Disadvantages of Tree Topology .

Tree-Topology
What is Internet?
The Internet is a larger network that allows computer networks controlled by enterprises, governments, colleges, and other organizations all over the world to communicate with one another. As a result, there is a tangle of cables, computers, data centers, routers , servers, repeaters, satellites , and Wi-Fi towers that allow digital data to go around the world.
The Internet is a vast network of networks that functions as a networking infrastructure. It links millions of computers throughout the world, creating a network in which any computer can talk with any other computer as long as they are both linked to the Internet. The Internet is a global network of interconnected computers that communicate and share information using a standardized Internet Protocol Suite.
How to Connect to the Internet?
We can connect to the internet in the following ways:
- Dial-Up: In order to access the Internet, in this type of connection, users must connect their phone line to a computer. This link prevents the user from using tier home phone service to make or receive calls.
- Broadband: Broadband is a high-speed internet connection that is frequently utilized nowadays and is provided by cable or phone companies.
- Wireless Connections: Internet access is accomplished by radio waves , thus it is possible to connect to the Internet from any location. Wi-Fi and mobile service providers are examples of wireless connections.
Advantages of the Internet
- Source of Entertainment: Online gaming, talking, browsing, music, movies, dramas, and TV series are quickly becoming the most popular ways to pass the time.
- Source of Information: There is no better place to conduct research than the internet. We can learn about the latest trends, communicate with experts without having to physically visit them, and seek professional advice over the Internet.
- E-Commerce: With the advancement of internet technology, large online E-commerce enterprises such as Amazon, Ali Baba, myntra, etc. have emerged.
- Working from home, collaborating with others, and having access to a global workforce are all advantages.
- Keeps Updated: Because there are hundreds of thousands of newsgroups and services that keep you updated with every tick of the clock, the Internet is a source of the most recent news.
Disadvantages of the Internet
- Time Wastage: Most people believe that spending too much time on the internet is unhealthy for young people and leads to obesity.
- Money Laundering: Aside from reputable sites, there are some Social Media Advertising sites that try to steal your personal information, credit card information, and even your pin code. You can easily become a victim of money scams if they get this information.
- Exposure to Private Data: It is now quite easy to decipher someone’s chat or email communication thanks to the hacking community. As we all know, data is transmitted in packets, which hackers can simply detect and reconstruct.
- Harassment & Threatening: Bullies exist online, just as they do in real life, and they can lower your self-esteem by harassing and threatening you. Some of these individuals may be persons who are aware of some of your personal details and dislike you and may use this information to harass you.
In conclusion, computer networking is essential because it allows computers to connect and communicate with each other. This connectivity enables them to share information and resources, making tasks easier and faster. Whether it’s a small network within a home or office ( LAN ) or a large network spreading across cities and countries ( WAN ), networking helps us stay connected, work together, and access the internet. It’s like having a team where everyone can instantly share ideas and tools, making collaboration smooth and efficient. So, computer networking is all about making connections that help us stay informed, productive, and connected to the world.
Frequently Asked Questions on Computer Networking – FAQs
What is a computer networking job.
Network specialists and administrators take care of the daily tasks to keep networks running smoothly. Network architects and engineers plan and create networks like LANs (Local Area Networks), WANs (Wide Area Networks), and Intranets.
What is the full form of www?
The full form of www is World Wide Web. It is the world’s most dominant software and is commonly known as the web.
The structure of the network and how each component is connected to the others are defined by the network topology.
Please Login to comment...
Similar reads.
- School Learning
- School Programming
- 105 Funny Things to Do to Make Someone Laugh
- Best PS5 SSDs in 2024: Top Picks for Expanding Your Storage
- Best Nintendo Switch Controllers in 2024
- Xbox Game Pass Ultimate: Features, Benefits, and Pricing in 2024
- #geekstreak2024 – 21 Days POTD Challenge Powered By Deutsche Bank
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Browse Course Material
Course info.
- Prof. Hari Balakrishnan
Departments
- Electrical Engineering and Computer Science
As Taught In
- Computer Networks
Learning Resource Types
Course description.
How does the global network infrastructure work and what are the design principles on which it is based? In what ways are these design principles compromised in practice? How do we make it work better in today’s world? How do we ensure that it will work well in the future in the face of rapidly growing scale and …
How does the global network infrastructure work and what are the design principles on which it is based? In what ways are these design principles compromised in practice? How do we make it work better in today’s world? How do we ensure that it will work well in the future in the face of rapidly growing scale and heterogeneity? And how should Internet applications be written, so they can obtain the best possible performance both for themselves and for others using the infrastructure? These are some issues that are grappled with in this course. The course will focus on the design, implementation, analysis, and evaluation of large-scale networked systems.
Topics include internetworking philosophies, unicast and multicast routing, congestion control, network quality of service, mobile networking, router architectures, network-aware applications, content dissemination systems, network security, and performance issues. Material for the course will be drawn from research papers, industry white papers, and Internet RFCs.
You are leaving MIT OpenCourseWare

COMMENTS
In conclusion, computer networks are a pivotal aspect of information technology, enabling data exchange and collaboration across various scales and distances. 500 Words Essay on Computer Network Introduction to Computer Networks. A computer network is a set of interconnected computers that share resources and data.
A computer network allows for the sharing of resources such as printers, files, and data storage, as well as the ability to communicate with other computers and access the internet. Networking also enables collaboration between individuals and groups, and supports the transfer of data and information across a variety of platforms and devices.
It consists of a pair of chips plus a radio transmitter/receiver antenna. The antenna sends data to (and receives data from) a wireless (Wi-Fi) network. The smaller chip manages that process and passes its data to the larger chip, which is called an Ethernet MAC/BBP (baseband processor).
Computer Networks is an international, archival journal providing a publication vehicle for complete coverage of all topics of interest to those involved in the computer communications networking area. The audience includes researchers, managers and operators of networks as well as designers and implementors. The will consider any material for ...
Computer network: A computer network is interconnection of more computing systems and their hardwares for storing and transmitting the data. These networks can be connected either wires or wireless. Connecting the systems without wires is called wireless technology. Connecting the computers , laptops , printers and gaming devices comes under ...
A Computer Network is a system where multiple devices, such as computers and servers, connect to share resources and data. These devices communicate using wired cables, wireless signals, or fibre optics. The main objective of a Computer Network is to enable efficient communication and collaboration between users by sharing files, applications ...
Definition. A network is defined as an "interconnection of three or more communicating entities". Get a custom research paper on Computer Network Types and Classification. According to the glossary of telecommuting terms, a computer network is a network of data processing nodes which are interconnected for purposes of data communication'.
Get a custom essay on Concept and Types of the Computer Networks. According to Tamara (4), computer networks can either be private or public, depending on the type of configuration in the network. Public networks are configured with Public Internet Protocol, making them 'visible' to other connections outside the network.
Overview. This is a graduate-level course on computer networks. It provides a comprehensive overview on advanced topics in network protocols and networked systems. The course will cover both classic papers on computer networks and recent research results. It will examine a wide range of topics including routing, congestion control, network ...
The Usefulness of Computer Networks for Students Essay (Critical Writing) Computer network is the interconnection of many resourceful computers through domains which provide users with the possibility to freely share ideas, information and other useful resources. In my class setup, computer network has played a big role in construction of ...
Data Communication and Computer Networks. Executive Summary Data communication and computer networks are the essential part of our day-to-day life. It is invaded all aspects of our life, i.e., entertainment, business, education and research, space mission, PC revolution, and telecommunication. This paper discusses data communication and ...
The Computer Networks Information Technology Essay. A computer network is the interconnection of computing devices in order to share data and is built with a combination of computer hardware and software WikiAnswers- Unknown author. Computer networks are used to connect multiple computers to an internet connection, or to printers, scanners, etc ...
Introduction. A computer network is a set of linked computers together for the purpose of sharing resources. The common resource shared today is a connection to the Internet. Other resources that are shared can include a printer or a file server. The Internet as a stand-alone can be considered a computer network.
Get original essay. A Network is a connection between different devices that share information and work in real time in harmony with software and hardware technology. Especially networks are used to connect this devices and computers to the internet. We can have also scanners and printers connected to the same area and network.
A computer network is a system that connects many independent computers to share information (data) and resources. The integration of computers and other different devices allows users to communicate more easily. A computer network is a collection of two or more computer systems that are linked together.
Examples of networks may include computer networks [2], social networks [3], the network of things as the Internet of Things (IoT) [4]. The adoption of machine learning is a requirement to bring ...
Best Essays. 3132 Words. 13 Pages. Open Document. The Top Speeds of Computer Networks In this paper, the topic of computer network speeds will be discussed. The overlaying question that will be addressed in this paper will be "How fast can computer networks operate at?". The various connection types of Ethernet, Fiber Optic, and wireless ...
From business to government, computer networks are relied upon to store, process, retrieve, and transfer critical information. Increased dependence on computer networks has, however, posed a major threat. Cyber terrorism is now arguably the biggest threat facing the U.S. (Harress, 2014; Thomas, 2016).
These are some issues that are grappled with in this course. The course will focus on the design, implementation, analysis, and evaluation of large-scale networked systems. Topics include internetworking philosophies, unicast and multicast routing, congestion control, network quality of service, mobile networking, router architectures, network ...
Computer Network Essays. Computer Network Management. Introduction Computer networks are essential organizational infrastructure because they allow for the effective sharing of resources and data. To guarantee that a computer network fits the demands of the organization is safe, and can accommodate future expansion, a number of variables must ...
Essay On Computer Network Topology. Computer network topology is the way different parts of a network (like hubs, connections, peripherals, and so on) are arranged. System topologies characterize the format, virtual shape or structure of network, physically as well as logically. The path in which distinctive frameworks and hubs are associated ...
Computer networking essay. Computer networking is a technology that connects devices together to share information and resources. This technology has become a vital part of modern-day communication and technology. Computer networking is used in various fields, including businesses, education, healthcare, government, and entertainment.
Download. Computer Network also called Network is a group of computers and other devices connected to each other to share resources electronically. Networks can be as small as two computers or many thousand computers that are connected to one another. These computers are usually connected to one another through wires, satellite, and modems.
IGCSE Computer Science Revision Notes for CIE. Clear and structured resources to guide you through key topics.