Presentation Layer
Margaret Rouse is an award-winning technical writer and teacher known for her ability to explain complex technical subjects simply to a non-technical, business audience. Over…

What Does Presentation Layer Mean?
The presentation layer is layer 6 of the 7-layer Open Systems Interconnection (OSI) model. It is used to present data to the application layer (layer 7) in an accurate, well-defined and standardized format.
The presentation layer is sometimes called the syntax layer.
Techopedia Explains Presentation Layer
The presentation layer is responsible for the following:
- Data encryption/decryption
- Character/string conversion
- Data compression
- Graphic handling
The presentation layer mainly translates data between the application layer and the network format. Data can be communicated in different formats via different sources. Thus, the presentation layer is responsible for integrating all formats into a standard format for efficient and effective communication.
The presentation layer follows data programming structure schemes developed for different languages and provides the real-time syntax required for communication between two objects such as layers, systems or networks. The data format should be acceptable by the next layers; otherwise, the presentation layer may not perform correctly.
Network devices or components used by the presentation layer include redirectors and gateways.
Related Terms
- Open Systems Interconnection Model
- Application Layer
- Session Layer
- Data Link Layer
- Transport Layer
- Physical Layer
- Network Layer
- Local Area Network
- Wide Area Network
- User Interface
Related Reading
- An Introduction to the OSI Model
About Techopedia’s Editorial Process
Techopedia’s editorial policy is centered on delivering thoroughly researched, accurate, and unbiased content. We uphold strict sourcing standards, and each page undergoes diligent review by our team of top technology experts and seasoned editors. This process ensures the integrity, relevance, and value of our content for our readers.
- Data Management

Margaret Rouse
Margaret is an award-winning writer and educator known for her ability to explain complex technical topics to a non-technical business audience. Over the past twenty years, her IT definitions have been published by Que in an encyclopedia of technology terms and cited in articles in the New York Times, Time Magazine, USA Today, ZDNet, PC Magazine, and Discovery Magazine. She joined Techopedia in 2011. Margaret’s idea of a fun day is to help IT and business professionals to learn to speak each other’s highly specialized languages.
Most Popular Terms
Digital strategy.
What is Digital Strategy? The definition of digital strategy is a comprehensive plan that uses digital technologies to achieve specific...
Nicole Willing Technology Journalist
Public Data
What is Public Data? Public data is digital information collected by government agencies. This type of data can be accessed...
Margaret Rouse Technology Specialist
Quantization
What is Quantization? Quantization is a process aimed at simplifying data representation by reducing precision – the number of bits...
Vangie Beal Technology Expert
Related News

10+ Best AI-Powered Games in 2024: Artificial Intelligence in Gaming

Most Reliable EV Cars in 2024

£27K For Teacherless Education: Is AI the New Classroom Reality?

Nook vs. Kindle: Which E-Reader Dominates in 2024?

Fortnite Birthday Event 2024: Start Time, Quests & Rewards

Video Game Addiction: Symptoms, Statistics & Treatment
Popular categories show all.
Trending News Latest Guides Reviews Term of the Day
By signing up, you agree to our Terms of Use and acknowledge the data practices in our Privacy Policy. You may unsubscribe at any time.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Presentation Layer in OSI model
Prerequisite : OSI Model
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network. The main responsibility of this layer is to provide or define the data format and encryption. The presentation layer is also called as Syntax layer since it is responsible for maintaining the proper syntax of the data which it either receives or transmits to other layer(s).
Functions of Presentation Layer :
The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-
- Presentation layer format and encrypts data to be sent across the network.
- This layer takes care that the data is sent in such a way that the receiver will understand the information (data) and will be able to use the data efficiently and effectively.
- This layer manages the abstract data structures and allows high-level data structures (example- banking records), which are to be defined or exchanged.
- This layer carries out the encryption at the transmitter and decryption at the receiver.
- This layer carries out data compression to reduce the bandwidth of the data to be transmitted (the primary goal of data compression is to reduce the number of bits which is to be transmitted).
- This layer is responsible for interoperability (ability of computers to exchange and make use of information) between encoding methods as different computers use different encoding methods.
- This layer basically deals with the presentation part of the data.
- Presentation layer, carries out the data compression (number of bits reduction while transmission), which in return improves the data throughput.
- This layer also deals with the issues of string representation.
- The presentation layer is also responsible for integrating all the formats into a standardized format for efficient and effective communication.
- This layer encodes the message from the user-dependent format to the common format and vice-versa for communication between dissimilar systems.
- This layer deals with the syntax and semantics of the messages.
- This layer also ensures that the messages which are to be presented to the upper as well as the lower layer should be standardized as well as in an accurate format too.
- Presentation layer is also responsible for translation, formatting, and delivery of information for processing or display.
- This layer also performs serialization (process of translating a data structure or an object into a format that can be stored or transmitted easily).
Features of Presentation Layer in the OSI model: Presentation layer, being the 6th layer in the OSI model, plays a vital role while communication is taking place between two devices in a network.
List of features which are provided by the presentation layer are:
- Presentation layer could apply certain sophisticated compression techniques, so fewer bytes of data are required to represent the information when it is sent over the network.
- If two or more devices are communicating over an encrypted connection, then this presentation layer is responsible for adding encryption on the sender’s end as well as the decoding the encryption on the receiver’s end so that it can represent the application layer with unencrypted, readable data.
- This layer formats and encrypts data to be sent over a network, providing freedom from compatibility problems.
- This presentation layer also negotiates the Transfer Syntax.
- This presentation layer is also responsible for compressing data it receives from the application layer before delivering it to the session layer (which is the 5th layer in the OSI model) and thus improves the speed as well as the efficiency of communication by minimizing the amount of the data to be transferred.
Working of Presentation Layer in the OSI model : Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture. Upon arrival at the receiving computer, the presentation layer translates data into an acceptable format usable by the application layer. Basically, in other words, this layer takes care of any issues occurring when transmitted data must be viewed in a format different from the original format. Being the functional part of the OSI mode, the presentation layer performs a multitude (large number of) data conversion algorithms and character translation functions. Mainly, this layer is responsible for managing two network characteristics: protocol (set of rules) and architecture.
Presentation Layer Protocols : Presentation layer being the 6th layer, but the most important layer in the OSI model performs several types of functionalities, which makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there in a closed network. Presentation Layer, for performing translations or other specified functions, needs to use certain protocols which are defined below –
- Apple Filing Protocol (AFP): Apple Filing Protocol is the proprietary network protocol (communications protocol) that offers services to macOS or the classic macOS. This is basically the network file control protocol specifically designed for Mac-based platforms.
- Lightweight Presentation Protocol (LPP): Lightweight Presentation Protocol is that protocol which is used to provide ISO presentation services on the top of TCP/IP based protocol stacks.
- NetWare Core Protocol (NCP): NetWare Core Protocol is the network protocol which is used to access file, print, directory, clock synchronization, messaging, remote command execution and other network service functions.
- Network Data Representation (NDR): Network Data Representation is basically the implementation of the presentation layer in the OSI model, which provides or defines various primitive data types, constructed data types and also several types of data representations.
- External Data Representation (XDR): External Data Representation (XDR) is the standard for the description and encoding of data. It is useful for transferring data between computer architectures and has been used to communicate data between very diverse machines. Converting from local representation to XDR is called encoding, whereas converting XDR into local representation is called decoding.
- Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web browser and the server. SSL encrypts the link between a web server and a browser, which ensures that all data passed between them remains private and free from attacks.

Similar Reads
Please login to comment....
- How to Underline in Discord
- How to Block Someone on Discord
- How to Report Someone on Discord
- How to add Bots to Discord Servers
- GeeksforGeeks Practice - Leading Online Coding Platform
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Layer 6 Presentation Layer
De/Encryption, Encoding, String representation
The presentation layer (data presentation layer, data provision level) sets the system-dependent representation of the data (for example, ASCII, EBCDIC) into an independent form, enabling the syntactically correct data exchange between different systems. Also, functions such as data compression and encryption are guaranteed that data to be sent by the application layer of a system that can be read by the application layer of another system to the layer 6. The presentation layer. If necessary, the presentation layer acts as a translator between different data formats, by making an understandable for both systems data format, the ASN.1 (Abstract Syntax Notation One) used.
OSI Layer 6 - Presentation Layer
The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or display. It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file. The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. "thisisastring\0"). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest. Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer. Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages. Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted. In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer. Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer. In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format. Wikipedia
- Data conversion
- Character code translation
- Compression
- Encryption and Decryption
The Presentation OSI Layer is usually composed of 2 sublayers that are:
CASE common application service element
| ACSE | Association Control Service Element |
|---|---|
| ROSE | Remote Operation Service Element |
| CCR | Commitment Concurrency and Recovery |
| RTSE | Reliable Transfer Service Element |
SASE specific application service element
| FTAM | File Transfer, Access and Manager |
|---|---|
| VT | Virtual Terminal |
| MOTIS | Message Oriented Text Interchange Standard |
| CMIP | Common Management Information Protocol |
| JTM | Job Transfer and Manipulation |
| MMS | Manufacturing Messaging Service |
| RDA | Remote Database Access |
| DTP | Distributed Transaction Processing |
Layer 7 Application Layer
Layer 6 presentation layer, layer 5 session layer, layer 4 transport layer, layer 3 network layer, layer 2 data link layer, layer 1 physical layer.
Presentation Layer in OSI Model: Functions, Protocols, Examples, Services
What is presentation layer, functions of presentation layer, protocols of presentation layer, example of presentation layer protocols.
Network Data Representation (NDR) : NDR is an data encoding standard, and it is implement in the Distributed Computing Environment (DCE).
Presentation Layer Services
Design issues with presentation layer, related posts.

Presentation Layer
The Presentation Layer is the sixth layer in the OSI model . It sits right above the Session Layer and below the Application Layer. Its main job is to handle how data is presented to the application . In other words, it ensures that the data is in a format that both the sending and receiving systems can understand.
Think of the Presentation Layer as a translator. Just like you might need a translator to understand a message in a foreign language, this layer translates data from one format to another. It ensures that the data sent from an application is correctly formatted and ready for the next layer in the OSI model to handle.
For example, when your computer sends a file over the Internet, it might be in a specific format like JPEG or PDF. The Presentation Layer translates that file into a format the receiving computer can understand and display correctly. It also ensures that any special characters or encryption are properly handled.
Functions of the Presentation Layer
The Presentation Layer has several vital functions that help ensure data is communicated effectively between systems.
Data Translation
One of the main jobs of the Presentation Layer is to translate data between different formats. When data is sent from one system to another, it might be in a format the receiving system does not understand. The Presentation Layer converts this data into an easily understood format, allowing different systems to work together smoothly.
Data Encryption/Decryption
Security is a big concern in data transmission. The Presentation Layer helps by encrypting data before it is sent. Encryption transforms data into a secure format so unauthorised people cannot easily read it. When the data reaches its destination, the Presentation Layer decrypts it, returning it to its original form to be used.
Data Compression/Decompression
The presentation layer can compress data to make data transfer faster and more efficient. Compression reduces the data's size, meaning it takes up less space and transfers more quickly. When the data arrives, the Presentation Layer decompresses it, restoring it to its original size and format.
These functions make the Presentation Layer essential for preparing data for proper communication and ensuring it is secure and efficient. This layer helps maintain smooth and reliable information exchanges across different systems by handling translation, encryption, and compression.
Examples of Presentation Layer Protocols and Formats
The Presentation Layer uses various protocols and formats to perform its tasks.
Regarding protocols, the SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are commonly used to encrypt and secure data transmitted across networks, ensuring that information remains confidential and protected from unauthorised access.
SSL and its successor, TLS, are protocols used to secure data transmission. They encrypt the data to protect it from being intercepted and read by unauthorised users. SSL/TLS ensures that information such as personal details or payment information remains private and secure as it travels across the internet.
Data Formats
Regarding data formats, the Presentation Layer is responsible for converting and optimising various data types—such as images, videos, and text—so they are displayed correctly and consistently across different platforms and devices.
JPEG and GIF
These are formats for image files. JPEG and GIF encode images for web display. The Presentation Layer helps convert these images into formats that can be viewed appropriately on different devices.
MPEG is a standard for video compression. It helps reduce the size of video files so they can be transmitted more efficiently. The Presentation Layer ensures that video data is compressed and decompressed correctly, allowing for smooth video playback.
ASCII and EBCDIC
These are character encoding standards. ASCII (American Standard Code for Information Interchange) and EBCDIC (Extended Binary Coded Decimal Interchange Code) define how text characters are represented in data. The Presentation Layer ensures that text is correctly converted from one encoding to another if needed.
These examples show how the Presentation Layer handles various data types and formats. This layer uses specific protocols and formats to ensure data is accurately translated, secured, and optimised for effective system communication.
Importance of the Presentation Layer in Networking
The Presentation Layer plays a key role in sharing data between different systems.
Ensures Proper Data Interpretation
Different systems might use different data formats. The Presentation Layer ensures that when data is sent from one system to another, it is translated into a format the receiving system can understand. This means that whether you are sending a file, a message, or any other type of data, it will be interpreted correctly on the other end.
Supports Data Security
With increasing concerns about data privacy, the Presentation Layer’s role in encryption is crucial. By encrypting data before it is sent and decrypting it when it is received, this layer helps protect sensitive information from being accessed by unauthorised individuals. This encryption ensures that data remains confidential and secure, which is especially important for secure online transactions, confidential communications, and personal information. Effective encryption within the Presentation Layer helps mitigate data breaches and unauthorised access risks, enhancing overall data security .
Improves Efficiency
The Presentation Layer also helps compress data to make transmission faster and more efficient. Compressed data takes up less space and travels more quickly across networks, making the communication process smoother and reducing the time it takes to send and receive information.
Relationship with Other Layers
The Presentation Layer doesn’t work alone; it relies on and interacts with other layers in the OSI model. Here’s how it connects with them.
Interaction with the Application Layer
The Application Layer is where software applications interact with the network. It sends data to the Presentation Layer, which prepares it for transmission. For example, when you send an email or upload a file, the Application Layer creates the data, and the Presentation Layer formats and possibly encrypts it before sending it out.
Connection with the Session Layer
The Session Layer manages sessions or connections between applications. It ensures that sessions are correctly established, maintained, and ended. Once a session is active, the Presentation Layer takes over, handling the data exchange by translating and preparing the data. It then hands the processed data back to the Session Layer for transmission.
Dependency on Lower Layers
The Presentation Layer relies on the layers below it for data transport. The Transport Layer handles the actual delivery of data across the network, ensuring it reaches the right destination. The Presentation Layer needs this layer’s services to get its formatted data to the receiving system.
The Presentation Layer deals with how data is formatted, encrypted, and compressed for system transmission. It ensures that data is prepared to be understood and used correctly by different systems. The Content Layer, on the other hand, refers to the actual data or information being conveyed, such as text, images, or video. Essentially, the Presentation Layer is concerned with how data is packaged for transfer, while the Content Layer focuses on the substance of the data itself.
In the context of an API (Application Programming Interface), the Presentation Layer handles how data is formatted and presented to the end-user or application. It takes the raw data from the API and structures it in a way that is easy to read and use. This can include converting data into formats like JSON or XML and ensuring it is displayed correctly according to the application's requirements.
The Presentation Layer offers several benefits. It ensures that data is correctly formatted so that different systems can understand it. It also provides security through data encryption, protecting sensitive information during transmission. Additionally, it improves efficiency by compressing data, which speeds up transfer times and reduces the amount of data that needs to be sent over the network.
The OSI model consists of seven layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application. Each layer has a specific role in handling data as it moves through a network, from the physical transmission of signals to the final application interactions.
Articles you might enjoy

The OSI model is a conceptual framework that defines how different software and hardware components in a network communicate.

An application, commonly called an app or program, is a form of software that allows specific tasks to be performed on a device. "App" is a common term for an application. Applications run within the operating system until the application is closed.

An API, which stands for Application Programming Interface, is vital to modern technology. It serves as a bridge that enables different software systems to communicate and interact with each other seamlessly.

Staying up-to-date with the latest trends and technologies is paramount for technology and development. Single-page applications (SPAs) have emerged as a modern web application development cornerstone. Their ability to provide seamless user experiences and dynamic interactions has propelled them to the forefront of web development methodologies.

Piqued your interest?
We'd love to tell you more.
Presentation Layer In OSI Model : A Comprehensive Guide
In the vast landscape of computer networks, the OSI (Open Systems Interconnection) model stands as a fundamental framework for understanding how data is transmitted from one device to another. Among its seven layers, the presentation layer holds an important place, acting as a translator and formatter to ensure seamless communication between different systems. Through this article, we will try to know what is presentation layer in OSI model, what is its role in the field of networking and what is its importance.
Table of Contents
What is the Presentation Layer?
The Presentation Layer, within the OSI (Open Systems Interconnection) model, is the sixth layer. It focuses on the representation of data, ensuring that information exchanged between applications is formatted appropriately for transmission and receipt across a network. This layer handles tasks such as data translation, encryption, compression, and formatting. Its primary function is to ensure that data remains readable and understandable by both the sender and receiver, regardless of differences in data formats. In essence, the Presentation Layer acts as a translator and formatter, facilitating seamless communication between different systems and enhancing the reliability and security of data transmission.
Working of Presentation Layer
The Presentation Layer acts like a language translator and document formatter in the OSI model. It takes data from applications and prepares it for transmission over the network by translating it into a language that both the sender and receiver understand. Think of it as converting a letter into a universal format before mailing it overseas. Additionally, the Presentation Layer ensures that the data looks right by formatting it properly, like adjusting the font and spacing in a document. It also adds extra security by encrypting the data if needed, making it like a secret code that only the intended recipient can understand. Lastly, it might shrink the data down to save space during transmission, similar to compressing a file before emailing it. In short, the Presentation Layer makes sure data is ready for its journey across the network, keeping it secure, readable, and efficient along the way.
Functions of the Presentation Layer
- Data Translation : Converting data from the format used by the application into a format suitable for transmission over the network, and vice versa, ensuring interoperability between different systems.
- Encryption and Decryption : Securing data during transmission by encrypting it before sending and decrypting it upon reception, ensuring confidentiality and integrity of the information.
- Data Compression : Reducing the size of data before transmission to optimize bandwidth usage and speed up the transfer process, improving network efficiency.
- Data Formatting: Formatting data according to predefined standards for transmission, including character encoding, data structure, and multimedia representation, ensuring compatibility between sender and receiver applications.
- Protocol Conversion : Adapting data between different network protocols or data formats, facilitating communication between systems with varying requirements or standards.
- Character Code Translation: Converting characters between different character sets or encoding schemes to ensure proper interpretation of text-based data across systems with different language or encoding preferences.
Protocols are Use in Presentation layer
The Presentation Layer primarily focuses on data representation and formatting rather than specific protocols. However, some protocols or standards are commonly associated with the Presentation Layer due to their role in data representation and formatting. Here are a few examples.
- MIME : MIME stands for Multipurpose Internet Mail Extensions. It’s a protocol that broadens the scope of email messages, enabling the use of text in various character sets beyond ASCII. Additionally, MIME facilitates the inclusion of attachments such as audio, video, images, and application programs within emails.
- SSL/TLS : SSL/TLS protocols provide secure communication over a computer network by encrypting data between the client and server, ensuring data confidentiality and integrity. While SSL/TLS operate at the Transport Layer, they often involve encryption and decryption processes associated with the Presentation Layer.
- ASCII (: ASCII and Unicode are character encoding standards that represent text characters using numerical codes. These standards ensure consistent representation of text characters across different systems and platforms, which is crucial for data interchange.
- JPEG, GIF, PNG : These image file formats are commonly used for encoding and transmitting images over networks. While the specifics of image compression and encoding are often handled by the Application Layer, the Presentation Layer ensures proper interpretation and formatting of these image data.
- PDF : PDF is a file format used to present and exchange documents reliably, independent of software, hardware, or operating systems. The Presentation Layer ensures proper interpretation and rendering of PDF documents for display or printing
the Presentation Layer of the OSI Model acts as a translator and formatter, ensuring that data exchanged between applications remains readable and compatible across diverse systems. By handling tasks such as data translation, encryption, compression, and formatting, it enhances the reliability, efficiency, and security of data transmission over networks. Essentially, the Presentation Layer plays a crucial role in facilitating seamless communication between different systems, ensuring that information is accurately represented and securely transmitted, thus contributing to the smooth functioning of modern networking environments.
Recommended Article
- Understanding Crossover Cable and Straight-Through Cable
- Understanding The Difference Between URI and URL
- What Are The Difference Between Analog And Digital Signal
- What Are Antennas ? | Types Of Antenna And How Do They Work
- Difference Between Hub Switch And Router
- 7 Layers of the OSI Model – Definition, Layers, and Functions
- What Is Ping Command In Computer Network
- Difference Between Webpage And Website
- Difference Between OSI and TCP/IP Model in Networking
- Latest Posts
- Bachelor of Business Administration (BBA): A Comprehensive Overview - 17 August 2024
- HTTP Full Form – Definition, Features & How It Works - 14 August 2024
- DNS Full Form – Domain Name System , Types & Features - 13 August 2024
Please Share This Share this content
- Opens in a new window X
- Opens in a new window Facebook
- Opens in a new window Pinterest
- Opens in a new window LinkedIn
- Opens in a new window WhatsApp
You Might Also Like
What is personal area network (pan) in computer network, what is bus topology features, & how does it work, what is ring topology features, & how does it work.
- Network infrastructure
OSI model (Open Systems Interconnection)
- Andrew Froehlich, West Gate Networks
- Linda Rosencrance
- Kara Gattine, Director of Editorial Operations
What is OSI model (Open Systems Interconnection)?
OSI (Open Systems Interconnection) is a reference model for how applications communicate over a network. This model focuses on providing a visual design of how each communications layer is built on top of the other, starting with the physical cabling, all the way to the application that's trying to communicate with other devices on a network.
A reference model is a conceptual framework for understanding relationships. The purpose of the OSI reference model is to guide technology vendors and developers so the digital communications products and software programs they create can interoperate and to promote a clear framework that describes the functions of a networking or telecommunications system that's in use.
Most vendors involved in telecommunications try to describe their products and services in relation to the OSI model. This helps them differentiate among the various transport protocols, addressing schemes and communications packaging methods. And, although it's useful for guiding discussion and evaluation, the OSI model is theoretical in nature and should be used only as a general guide. That's because few network products or standard tools keep related functions together in well-defined layers, as is the case in the OSI model. The Transmission Control Protocol/Internet Protocol ( TCP/IP ) suite, for example, is the most widely used network protocol, but even it doesn't map cleanly to the OSI model.
History of the OSI model
In the 1970s, technology researchers began examining how computer systems could best communicate with each other. Over the next few years, several competing models were created and published to the community. However, it wasn't until 1984 when the International Organization for Standardization (ISO) took the best parts of competing networking reference models to propose OSI as a way to finally create a framework that technology companies around the world could use as the basis of their networking technologies .
From ISO's perspective, the easiest way to create a conceptual model was to organize the models into different abstraction layers required to organize and send data between computing systems. Looking inside each abstracted layer to see the details shows one part of this network communication process. Each layer can be thought of as a separate communication module or piece of the puzzle. But, to actually accomplish the goal of sending data from one device to another, each module must work together.
How the OSI model works
Information technology (IT) networking professionals use OSI to model or conceptualize how data is sent or received over a network. Understanding this is a foundational part of most IT networking certifications, including the Cisco Certified Network Associate (CCNA) and CompTIA Network+ certification programs. As mentioned, the model is designed to break down data transmission standards, processes and protocols over a series of seven layers, each of which is responsible for performing specific tasks concerning sending and receiving data.
The main concept of OSI is that the process of communication between two endpoints in a network can be divided into seven distinct groups of related functions, or layers. Each communicating user or program is on a device that can provide those seven layers of function.
In this architecture, each layer serves the layer above it and, in turn, is served by the layer below it. So, in a given message between users, there will be a flow of data down through the layers in the source computer, across the network and then up through the layers in the receiving computer. Only the application layer at the top of the stack doesn't provide services to a higher-level layer.
The seven layers of function are provided by a combination of applications, operating systems (OSes), network card device drivers, networking hardware and protocols that enable a system to transmit a signal over a network through various physical mediums, including twisted-pair copper, fiber optics, Wi-Fi or Long-Term Evolution (LTE) with 5G .
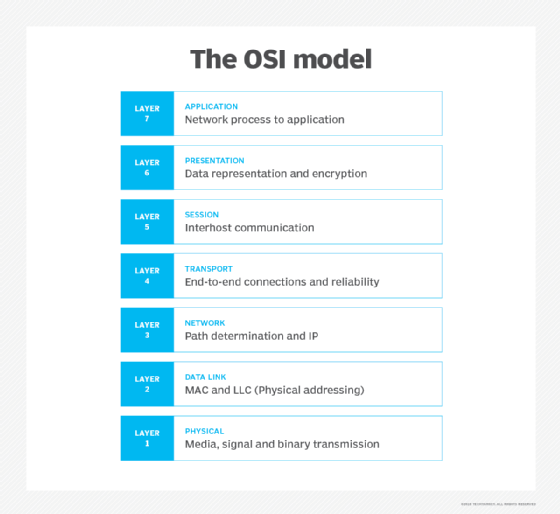
7 layers of the OSI model
What is the function of each layer of the OSI model? The seven Open Systems Interconnection layers are the following.
Layer 7. The application layer
The application layer enables the user -- human or software -- to interact with the application or network whenever the user elects to read messages, transfer files or perform other network-related tasks. Web browsers and other internet-connected apps, such as Outlook and Skype, use Layer 7 application protocols.
Layer 6. The presentation layer
The presentation layer translates or formats data for the application layer based on the semantics or syntax the application accepts. This layer also handles the encryption and decryption that the application layer requires.
Layer 5. The session layer
The session layer sets up, coordinates and terminates conversations between applications. Its services include authentication and reconnection after an interruption. This layer determines how long a system will wait for another application to respond. Examples of session layer protocols include X.225 and Zone Information Protocol (ZIP).
Layer 4. The transport layer
The transport layer is responsible for transferring data across a network and provides error-checking mechanisms and data flow controls. It determines how much data to send, where it gets sent and at what rate. TCP within the TCP/IP suite is the best-known example of the transport layer. This is where the communications select TCP port numbers to categorize and organize data transmissions across a network.
Layer 3. The network layer
The primary function of the network layer is to move data into and through other networks. Network layer protocols accomplish this by packaging data with correct network address information, selecting the appropriate network routes and forwarding the packaged data up the stack to the transport layer. From a TCP/IP perspective, this is where IP addresses are applied for routing purposes.
Layer 2. The data-link layer
The data-link , or protocol layer, in a program handles moving data into and out of a physical link in a network. This layer handles problems that occur as a result of bit transmission errors. It ensures that the pace of the data flow doesn't overwhelm the sending and receiving devices. This layer also permits the transmission of data to Layer 3, the network layer, where it's addressed and routed.
The data-link layer can be further divided into two sublayers. The higher layer, which is called logical link control (LLC), is responsible for multiplexing, flow control, acknowledgement and notifying upper layers if transmit/receive (TX/RX) errors occur.
The media access control sublayer is responsible for tracking data frames using MAC addresses of the sending and receiving hardware. It's also responsible for organizing each frame, marking the starting and ending bits and organizing timing regarding when each frame can be sent along the physical layer medium.
Layer 1. The physical layer
The physical layer transports data using electrical, mechanical or procedural interfaces. This layer is responsible for sending computer bits from one device to another along the network. It determines how physical connections to the network are set up and how bits are represented into predictable signals as they're transmitted either electrically, optically or via radio waves.
Cross-layer functions
Cross-layer functions, or services that may affect more than one layer, include the following:
- security service telecommunication as defined by the International Telecommunication Union Standardization Sector (ITU-T) X.800 recommendation;
- management functions that enable the configuration, instantiation, monitoring and terminating of the communications of two or more entities;
- Multiprotocol Label Switching ( MPLS ), which operates at an OSI model layer that lies between the Layer 2 data-link layer and the Layer 3 network layer -- MPLS can carry a variety of traffic, including Ethernet frames and IP packets;
- Address Resolution Protocol (ARP) translates IPv4 addresses (OSI Layer 3) into Ethernet MAC addresses (OSI Layer 2); and
- domain name system (DNS), which is an application layer service that's used to look up the IP address of a domain name.
Pros and cons of the OSI model
The OSI model has a number of advantages, including the following:
- It's considered a standard model in computer networking.
- The model supports connectionless , as well as connection-oriented, services. Users can take advantage of connectionless services when they need faster data transmissions over the internet and the connection-oriented model when they're looking for reliability.
- It has the flexibility to adapt to many protocols.
- The model is more adaptable and secure than having all services bundled in one layer.
The disadvantages of the OSI model include the following:
- It doesn't define any particular protocol.
- The session layer, which is used for session management, and the presentation layer, which deals with user interaction, aren't as useful as other layers in the OSI model.
- Some services are duplicated at various layers, such as the transport and data-link layers.
- Layers can't work in parallel; each layer must wait to receive data from the previous layer.
OSI model vs. TCP/IP model
The OSI reference model describes the functions of a telecommunication or networking system, while TCP/IP is a suite of communication protocols used to interconnect network devices on the internet. TCP/IP and OSI are the most broadly used networking models for communication.
The OSI and TCP/IP models have similarities and differences. The main similarity is in their construction, as both use layers, although the OSI model consists of seven layers, while TCP/IP consists of just four layers.
Another similarity is that the upper layer for each model is the application layer, which performs the same tasks in each model but may vary according to the information each receives.
The functions performed in each model are also similar because each uses a network and transport layer to operate. The OSI and TCP/IP model are mostly used to transmit data packets, although they each use different means and paths to reach their destinations.
Additional similarities between the OSI and TCP/IP models include the following:
- Both are logical models.
- Both define standards for networking.
- They each divide the network communication process in layers.
- Both provide frameworks for creating and implementing networking standards and devices.
- They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
- Both divide complex functions into simpler components.
Differences between the OSI and TCP/IP models include the following:
- OSI uses three layers -- application, presentation and session -- to define the functionality of upper layers, while TCP/IP uses only the application layer.
- OSI uses two separate layers -- physical and data-link -- to define the functionality of the bottom layers, while TCP/IP uses only the link layer.
- OSI uses the network layer to define the routing standards and protocols, while TCP/IP uses the internet layer.
Next: Explore 12 common network protocols all network engineers should know here .
Continue Reading About OSI model (Open Systems Interconnection)
- What is the difference between TCP/IP model vs. OSI model?
- Future of networking technology relies on 5G, edge computing
- 7 TCP/IP vulnerabilities and how to prevent them
- Edge computing and 5G bring the edge to remote workers
- SANs Institute OSI model overview
Related Terms
Dig deeper on network infrastructure.

An explanation of TCP/IP

Transmission Control Protocol (TCP)

encapsulation (object-orientated programming)

Microsoft 365 Copilot, an AI assistant, offers several promising features. Find out how to configure Copilot with Teams workflows...
With its AI capabilities, Microsoft Copilot provides several enhancements to Microsoft Teams functionality, including meeting ...
Organizations have ramped up their use of communications platform as a service and APIs to expand communication channels between ...
Connectivity issues, misconfigured settings and human error can all cause mobile hotspot problems. IT must know how to avoid and ...
With mobile device management software, IT can better support corporate smartphones, laptops and other mobile endpoints. Learn ...
Auditing is a crucial part of mobile device security, but IT admins must ensure their approach is thorough and consistent. Learn ...
Hock Tan unscored the importance of customers at the Boston VMware User Group UserCon, but users remain uneasy about the recent ...
Extreme heat and inadequate cooling systems can lead to power failures in data centers. Calculate the duration of your UPS ...
Intel's turnaround efforts are progressing, but the chipmaker will need more than government funding and a deal that expands its ...
IT service providers pursue advisory, training and automation opportunities as customers adopt FinOps and apply its cost ...
Popular pricing models for managed service providers include monitoring only, per device, per user, all-you-can-eat or ...
Global IT consultancies take a multilayered approach to GenAI training by developing in-house programs, partnering with tech ...

- Data Structure
- Coding Problems
- C Interview Programs
- C++ Aptitude
- Java Aptitude
- C# Aptitude
- PHP Aptitude
- Linux Aptitude
- DBMS Aptitude
- Networking Aptitude
- AI Aptitude
- MIS Executive
- Web Technologie MCQs
- CS Subjects MCQs
- Databases MCQs
- Programming MCQs
- Testing Software MCQs
- Digital Mktg Subjects MCQs
- Cloud Computing S/W MCQs
- Engineering Subjects MCQs
- Commerce MCQs
- More MCQs...
- Machine Learning/AI
- Operating System
- Computer Network
- Software Engineering
- Discrete Mathematics
- Digital Electronics
- Data Mining
- Embedded Systems
- Cryptography
- CS Fundamental
- More Tutorials...
- Tech Articles
- Code Examples
- Programmer's Calculator
- XML Sitemap Generator
- Tools & Generators

Computer Network Tutorial
- Computer Network - Home
- Computer Network - Overview
- Computer Network - Applications
- Computer Network - TCP/IP
- Computer Network - OSI Model
- Computer Network - Transport, Network, & Application Layers
- Computer Network - Network Protocols & Network Software
- Computer Network - TopologiesTypes
- Computer Network - Hub
- Computer Network - Routing
- Computer Network - Routers
- Computer Network - Dynamic Routing Protocols
- Computer Network - Router
- Computer Network - Populating a Routing Table
- Computer Network - Switches
- Computer Network - Layer 2 Switching
- Computer Network - Configure Cisco Switch
- Computer Network - ICMP
- Computer Network - ICMP Messages
- Computer Network - Addressing
- Computer Network - Classless Addressing
- Computer Network - IPV4 Addressing
- Computer Network - IPV6 Addressing
- Computer Network - Logical Addressing, Notations
- Computer Network - Classful & Classless Addressing
- Computer Network - Subnetting & Supernetting
- Computer Network - Network Address Translation
- Computer Network - FLSM & VLSM
- Computer Network - Line Configuration
- Transmission Computer Network - Modes
- Computer Network - Data Link Layer
- Computer Network - Physical Layer
- Computer Network - Network Layer
- Computer Network - Session Layer
- Computer Network - Transport Layer
- Computer Network - Application Layer
- Computer Network - Presentation Layer
- Computer Network - Coaxial Cable
- Computer Network - Optical Fiber
- Computer Network - Unguided Transmission Media
- Computer Network - Virtual LAN (VLAN)
- Computer Network - VSAN
- Computer Network - Multiple Access Protocol
- Computer Network - Random Access methods
- Computer Network - Aloha Network
- Computer Network - CSMA
- Computer Network - FDMA & TDMA
- Computer Network - CDMA
- Computer Network - Ethernet Technology
- Computer Network - Types of Network Topology
- Computer Network - Data Transmission
- Computer Network - Switching Techniques
- Computer Network - Transmission Impairment
- Computer Network - Synchronous & Asynchronous Transmission
- Computer Network - Intent-Based Networking
- Computer Network - Software-Defined Networking
- Computer Network - Wireless Personal Area Network
- Computer Network - Wireless Wide Area Network
- Computer Network - P2P File Sharing
- Computer Network - Packet Switching
- Computer Network - PGP - Authentication & Confidentiality
- Computer Network - PGP - Encryption & Compression
- Computer Network - Phishing Attacks
- Computer Network - ICMP Ping
- Computer Network - Pipelining in Packet Switching
- Computer Network - Plaintext Vs. Cleartext Encryption
- Computer Network - Platform as a Service (PaaS)
- Computer Network - GPRS Architecture
- Computer Network - Identify & Prevent Phishing & Pharming
- Computer Network - Change MAC Address
- Computer Network - Network Administrator Vs. Network Engineer
Difference B/W Articles
- Computer Network - Phishing & Pharming
- Computer Network - Ping Vs. Traceroute
- Computer Network - Network Vs. System Administrator
- Computer Network - Network & Application Layer Protocols
- Computer Network - Network Security Vs. Network Administration
- Computer Network - Network Vs. Internet
- Computer Network - PDH Vs. SDH
- Computer Network - PCI Vs. PCI express
- Computer Network - PCI-E Vs. PCI-X
- Computer Network - OT Vs. IT Networks
Computer Network Practice
- Computer Network - MCQs
- Computer Network - Aptitude Questions
Home » Computer Network
Presentation Layer: What It Is, Design Issues, Functionalities
Description and Functions of Presentation Layer in the OSI model: In this tutorial, we are going to learn what the Presentation layer is and the Functions of the Presentation Layer in the OSI model in Computer Networking. We will also discuss the Design issues with the Presentation Layer and the working of the Presentation Layer with the help of its diagram. By Monika Jha Last updated : May 05, 2023
What is Presentation Layer?
The Presentation Layer is concerned with the syntax and semantics of the information exchanged between two communicating devices.
- The presentation layer takes care that the data is sent in that way the receiver of the data will understand the information (data) and will be able to use the data.
- Languages that are syntax can be different from the two communicating machines. In this condition, the presentation layer plays the role of translator between them.
- It is possible for two machines to communicate with different data representations, data structures to be exchanged can be defined in an abstract way.
- These abstract data structures will be managed by the presentation layer and this layer allows higher-level data structures (For example banking records), to be defined and exchanged.
This figure shows the relationship of the presentation layer to the session layer and application layer.

Design Issues with Presentation Layer
The following are the design issues with presentation layer:
- To manage and maintain the Syntax and Semantics of the information transmitted.
- Encoding data in a standard agreed-upon way just like a string, double, date, etc.
- It Performs Standard Encoding scheme on the wire.
Functionalities of the Presentation Layer
Specific functionalities of the presentation layer are as follows:
1. Translation
- The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams because different computers use different encoding schemes.
- The Presentation layer is responsible for compatibility between these encoding methods.
- The Presentation layer at the sender's side changes the information from its sender dependent format.
- The Presentation layer at the receiving machine changes the common format into its receivers dependent format.
Example: Convert ASCII code to EBCDIC code.
2. Encryption
- The system must be able to assure privacy regarding the message or information as it also carries sensitive information.
- Encryption means that the sender transforms the original information or message to another form, this data after encryption is known as the ciphertext and this ciphertext sends the resulting message out over the network.
- Decryption concerned with the transform of the message back to its original form. This decrypted data is known as plain text.

3. Compression
- Data Compression means reduces the number of bits to be transmitted by this reduce the bandwidth of the data.
- Data Compression becomes particularly important in the transmission of multimedia such as audio, video, text, etc.
Related Tutorials
- IPV4 Addressing | Classful and Classless Addressing
- Subnetting and Supernetting in Computer Network
- Network Address Translation (NAT) in Computer Network
- Fixed Length and Variable Length Subnet Mask (FLSM & VLSM)
- Line Configuration in Computer Network
- Transmission Modes in Computer Network
- Data Link Layer: What It Is, Sublayers, Design Issues, Functions
- Physical Layer: What It Is, Design Issues, Functions
- Network Layer: What It Is, Design Issues, Responsibilities
- Session Layer: What It Is, Design Issues, Functionalities
- Transport Layer: What It Is, Design Issues, Functions, and Example
- Optical Fiber (Fiber Optics) in Computer Network
- Unguided Transmission Media in Computer Network
- Virtual LAN (VLAN) in Computer Network
- Virtual Storage Area Networking (VSAN)
Comments and Discussions!
Load comments ↻
- Marketing MCQs
- Blockchain MCQs
- Artificial Intelligence MCQs
- Data Analytics & Visualization MCQs
- Python MCQs
- C++ Programs
- Python Programs
- Java Programs
- D.S. Programs
- Golang Programs
- C# Programs
- JavaScript Examples
- jQuery Examples
- CSS Examples
- C++ Tutorial
- Python Tutorial
- ML/AI Tutorial
- MIS Tutorial
- Software Engineering Tutorial
- Scala Tutorial
- Privacy policy
- Certificates
- Content Writers of the Month
Copyright © 2024 www.includehelp.com. All rights reserved.
OSI: Layer 6 – Presentation

The presentation layer is the sixth layer (layer 6) of the seven-layer OSI model. The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or presentation to the user. It relieves the application layer from the responsibility in data representation .
This layer may translate data from a format used by the application layer into a common format at the source system. The presentation layer at the target system may re-translate the format into another appropriate format for its application layer.
Presentation Services
The presentation layer provides the following services and functions . These functions ensure that information sent from the application layer of one system will be readable by the application layer of another system.
- Character code translation – i.e. ASCII to EBCDIC
- Data conversion and format – the use of standard image, sound, and video formats
- Data compression – de-duplicates the number of bits that need to be transmitted on the network
- Data encryption – encrypt data for security purposes
Some of the protocols that function at this layer include:
- Apple Filing Protocol (AFP)
- Independent Computing Architecture (ICA)
- Lightweight Presentation Protocol (LPP)
- NetWare Core Protocol (NCP)
- Network Data Representation (NDR)
- eXternal Data Representation (XDR)
- X.25 Packet Assembler/Disassembler Protocol (PAD)
Related Posts

HTML5 Canvas: Text

ASP Functions and Subroutines

Hosting DNS Servers for Your Domain
Designing Active Directory for a SOHO Network

Ethernet Crossover Cable

What is the Active Directory Schema?
About the author, leave a comment cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Paul is a passionate programmer who enjoys writing about all things technical. He likes getting into the nitty-gritty of technology and describing it in a way that anybody can understand.

What Is Synacor YouTube TV?

Why Did Apbassing Quit YouTube?

How To Upload MP3 to YouTube

Validating your Active Directory Schema Version

Introducing Windows Server 2012

CSS Grouping and Nesting Selectors
What is the Presentation Layer in Programming?
Trevor Page
Get the Best Java Roadmap
Download the roadmap.
The presentation layer is one of the three main layers in object-oriented programming.
The three main layers include:
- Presentation Layer
- Business Layer
Now, these three layers are typically related to enterprise web applications. It's a design pattern used to help separate your code out in three distinct areas that (if need be) can easily be switched out with another programming language or technology.
So if you keep all of your presentation layer code in one area of your application, switching presentation layer technologies shouldn't be too difficult.
Same rules apply to the business and data layers. If you separated your code out properly, switching databases shouldn't be too big of an issue.
Having said that, we'll be focusing on the presentation layer.
The four big players (in terms of technology) in the presentation layer are as follows:
Let’s dive into the overviews of each of these big players, shall we?
HTML (HyperText Markup Language) is a technology used to communicate with web browsers. All browsers follow the rules laid out in HTML (currently in its 5th iteration).
HTML defines a bunch of different HTML elements known as tags that are put together to make up the basic layout of a web page. These tags are used to define things like the title of the webpage (which appears in the tab of your browser), the actual text that appears on the page, images, buttons and more.
Thankfully HTML isn’t too tough to learn as it’s more of a game of memorizing the most popular tags and using them to create your simple web pages. HTML is not a programming language, as it doesn’t define variables, data types, control structure or the like. This is also what makes it fairly easy to learn.
We’ll be diving into examples of HTML “code” later, so stay tuned.
CSS (cascading style sheets) is used to add some “pizazz” to your web pages. CSS is used to add a design look and feel to your web pages through the use of its cascading rules. We won’t get into the exact rules that CSS uses to apply its designs just yet, but again, stay tuned for a more in depth explanation.
All you need to know is that CSS is used to make a web page look nice. You can use it to choose which parts of the web page should be which color, how big or small elements should be, what fonts should be used and more.
If you’ve ever landed on a web page that wasn’t able to properly load its CSS, you’d likely think that the website was completely broken. It is often fixed by forcing the page to reload and then the CSS usually gets picked up the second time and everything loads properly and the website goes back to looking great. This situation is quite rare, but I thought I’d mention it because it’s a great example of just how powerful CSS is.
JavaScript is used to make your web pages interactive. It allows you to put some real programming functionality into web pages (as HTML is not a programming language and thus cannot add real programming elements to a page).
Examples of what JavaScript can do is when you’re logging into an application and you forget to provide information in one of the fields. JavaScript can detect that you’ve forgotten to type in your username or password and can provide you with a prompt explaining that you need to fill in your username and password before you can continue.
JavaScript shouldn’t be confused with Java, as they are two different technologies. Java is part of the business layer and has no place in the presentation layer. Java is known as a server side language, as it exists and runs on servers. JavaScript is known as a client side technology, and thus lives where the “clients” are, which is inside the actual web browsers.
A good way to think of the difference between the two languages is that when you land on a web page and it loads in your browser, it will also load any JavaScript code inside the page and you’ll actually be able to access that code and read it. Whereas, you’d never be able to read the Java code, as it’s not loaded in your browser because it’s a server side technology.
That simple distinction between the two languages makes for two very different languages in terms of their use and functionality.
The syntax for JavaScript, however, is fairly similar to Java. This is nice since you’ll be able to look at a piece of JavaScript code and more or less understand what’s going on. So you should be able to pick up the JavaScript language a lot quicker if you already have a good command of the Java language.
JQuery is a technology that’s used in tandem with JavaScript. JQuery makes your life as a web programmer so much easier for one reason, it allows you to write code once and have it work across all the browsers.
In today’s world we have so many browsers that can be downloaded for free and used to peruse the web. This actually makes building websites a bit challenging, as every browser has made up their own minds on how to “render” an HTML web page.
This means that a webpage loaded on Safari might not look the same as if it’s loaded on Internet Explorer, or Firefox, or Chrome.
These inconsistencies drive web programmers crazy, so that’s why jQuery was introduced. It allows you to write your JavaScript in a sort of “browser agnostic” way. You can write it once, and jQuery will execute the code appropriately depending on which browser it’s loaded it. VERY COOL!
The best part of all of these technologies is that they are all free to use.
And thankfully, they are also free to learn via these tutorials!
Do you want to get a job as a full-stack developer? Consider joining our Online Web Developer Bootcamp.
Free Java Roadmap
Discover exactly what you need to learn and where to start in order to become a professional coder.
Coders Campus
Launch your coding career..
© 2021 • Crafty Codr Inc • Terms • Privacy
151 Lyndhurst Drive, Kitchener, Ontario N2B 1B7 Canada
Presentation Layer
In subject area: Computer Science
The Presentation Layer in the OSI model is defined as the layer that enables interaction between different application layer implementations by translating data formats and languages to facilitate communication.
AI generated definition based on: Security for Microsoft Windows System Administrators , 2011
Common questions
- What is the responsibility of the presentation layer?
- Can the presentation layer manipulate data before displaying it to users? If so, how?
- What is the purpose of the Open Systems Interconnection seven layer model?
- What is the role of the presentation layer in software development?
Chapters and Articles
You might find these chapters and articles relevant to this topic.
Network Security
Derrick Rountree , in Security for Microsoft Windows System Administrators , 2011
The presentation layer (Layer 6) of the OSI model allows for interaction between different application layer implementations. The presentation layer provides somewhat of a translation between two different types of applications. Application layer implementations can use different formats and speak different “languages,” as long as the presentation layer translates the data for them.
Extending OSI to Network Security
In Hack the Stack , 2006
The Presentation Layer
Layer 6 is known as the presentation layer . The main purpose of the presentation layer is to deliver and present data to the application layer. This data must be formatted so that the application layer can understand and interpret it. The presentation layer is responsible for items such as:
Encryption and decryption of messages
Compression and expansion of messages, format translation
Handling protocol conversion
Introduction to IP Network Security
Eric Knipp , ... Edgar Danielyan Technical Editor , in Managing Cisco Network Security (Second Edition) , 2002
Layer 6: The Presentation Layer
The presentation layer establishes the way in which information is presented, typically for display or printing. Data encryption and character set conversion (such as ASCII to EBCDIC) are usually associated with this layer. The primary reason for someone to attend a class is that the presentation of information is designed to help that person learn. Students could, theoretically, pick up the literature and learn the material on their own; however, the value comes with the instructor s interpretation of the material. The instructor translates the information in such a way that students understand it. The presentation layer provides this functionality in computer systems.
The presentation layer translates information in a way that the application layer understands. Likewise, this layer translates information from the application layer to the session layer. Some examples of presentation layer protocols are SSL, HTTP/ HTML (agent), FTP (server), AppleTalk Filing Protocol,Telnet, and so on.
Domain 4: Communication and Network Security (Designing and Protecting Network Security)
Eric Conrad , ... Joshua Feldman , in CISSP Study Guide (Third Edition) , 2016
Layer 6 – Presentation
The Presentation Layer presents data to the application (and user) in a comprehensible way. Presentation Layer concepts include data conversion, character sets such as ASCII, and image formats such as GIF (Graphics Interchange Format), JPEG (Joint Photographic Experts Group), and TIFF (Tagged Image File Format).
Protocols and Communications Models
Edward Insam PhD, BSc , in TCP/IP Embedded Internet Applications , 2003
Presentation layer
The presentation layer is responsible for presenting the data to the application layer. This may include some form of format or character translation. This guarantees a common representation of the data while in transit. For example, all character sets used in the application layer could be converted to ASCII strings with escape sequences. The layer is also responsible for data encryption/decryption and for compression and decompression. Methods at each end agree before a communication on a common scheme for transmission. In many practical implementations, lower layers may implement one or more of the functions that might be associated with the presentation layer.
Application layer systems
Dimitrios Serpanos , Tilman Wolf , in Architecture of Network Systems , 2011
The presentation layer , which corresponds to OSI layer 6, handles the representation of information used in the communication between end-system applications. Data can be encoded in a number of different ways, and the presentation layer ensures that they are translated appropriately for transmission on the network and to be useful to the end-system application.
Services provided by the presentation layer are:
Translation: The translation service provided by the presentation layer is important for end systems and end-system applications that use different representations for data. For example, text can be represented by a number of different codes (e.g., ASCII, EBCDIC). If the two sides of a communication use a different encoding, a translation is necessary to avoid corruption of data. Similarly, different hardware architectures use varying representations for numbers (e.g., big-endian, little-endian), and translation is necessary to ensure correct interpretation by the application. Note that translation services can also be implemented for more complex data structures (e.g., strings, XML content).
Encryption/compression: Encryption/decryption and compression/decompression can be seen as one form of translation. However, these functions do not simply translate from one data format to another, but convert data into an intermediate format (ciphertext or compressed data) for transmission over the network. Note that encryption can also be performed in other layers of the protocol stack (see Chapter 10 ).
OSI Model and Then Some
In Next Generation SSH2 Implementation , 2009
Presentation Layer (6)
The presentation layer receives the data from the application layer and translates it into a format and syntax that's readable by other computers. In order for the other systems to recognize this data, it's converted into a generic format that is not application specific. This layer doesn't care what the actual data is. It's merely a translation stage for data formats. Thus, as the application passes the data down the stack, it's translated from what the application understands to a generic format. The system that ends up receiving this data does the reverse process by translating the generic data format into a format understood by that computer. Various operating system and applications may expect the data to be presented a certain way. The presentation layer provides the ability to translate the data to suit the applications needs. Some of the format types found in this layer are as follows: ASCII, EBCDIC, JPEG, MPEG, TIFF, Binary, and so on. This layer is also able to provide encryption and compression if the application layer asks it to do so.
Networking, Security, and the Firewall
Brad Woodberg , ... Ralph Bonnell , in Configuring Juniper Networks NetScreen & SSG Firewalls , 2007
The presentation layer controls the presentation or formatting of the data content. At this point in the OSI model, there is no data communication per se. The focus of this layer is having a common ground to present data between applications. For example, let's take image files. Billions of image files are transferred every day. Each of these files contains an image that ultimately will be displayed or stored on a computer. However, each image file must be the proper specified file format. This way, the application that reads the image file understands the type of data and the format contained in it. A JPEG file and a PNG file may contain the same image, but each uses a separate format. A JPEG file cannot be interpreted as a PNG, and vice versa. Additionally, file-level encryption occurs at the presentation layer.
Networking in CCTV
Vlado Damjanovski , in CCTV (Third Edition) , 2014
6. The Presentation layer
The Presentation layer describes the syntax of data being transferred. This layer describes how floating point numbers can be exchanged between hosts with different math formats. The Presentation layer performs certain functions that are requested sufficiently often to warrant finding a general solution for them, rather than letting each user solve the problems. In particular, unlike all the lower layers, which are just interested in moving bits reliably from here to there, the Presentation layer is concerned with the syntax and semantics of the information transmitted.
A typical example of a Presentation service is encoding data in a standard, agreed-upon way. Most user programs do not exchange random binary bit strings; they exchange things such as people’s names, dates, amounts of money, and invoices. These items are represented as character strings, integers, floating point numbers, and data structures composed of several simpler items. Different computers have different codes for representing character strings, integers, and so on. In order to make it possible for computers with different representation to communicate, the data structures to be exchanged can be defined in an abstract way, along with a standard encoding to be used “on the wire.” The Presentation layer handles the job of managing these abstract data structures and converting from the representation used inside the computer to the network standard representation.
The Presentation layer is also concerned with other aspects of information representation. For example, data compression can be used here to reduce the number of bits that have to be transmitted, and cryptography is frequently required for privacy and authentication.
Introduction
This chapter examines attacks against the Presentation layer (layer 6) and addresses methods to protect against such attacks.
The Presentation layer deals primarily with data presentation. For instance, if one host uses Extended Binary–coded Decimal Interchange Code (EBCDIC) for character sets and its communication partner uses American Standard Code for Information Interchange (ASCII), the Presentation layer converts the data according to each hosts’ needs. This is especially helpful when you have a heterogeneous network, because different hosts might represent data in diverse manners. Such functionality alleviates the need for application programmers to embed such code into their work. Other functionality within the Presentation layer includes data compression, data encryption, manipulating Extensible Markup Language (XML) objects, and other data handling deemed necessary. The Presentation layer provides insulation between the various forms of data representation encountered in multivendor environments, much like the ASN.1 notation employed in the Simple Network Management Protocol (SNMP).
To begin this chapter, we examine two protocols—Network Basic Input/Output System (NetBIOS) and Server Message Block (SMB). Next, we review some of the vulnerabilities within NetBIOS. We then examine Kerberos and its weaknesses, session hijacking, and how to capture passwords and break weak encryption schemes.
Related terms:
- Physical Layer
- Business Intelligence
- Internet Protocol
- Application Layer
- Open System Interconnection Model
- Data Link Layer
- Enterprise Data Warehousing
- Integration Layer
- Transport Layer
- Data Warehouse

UiPath Blog
Digital Transformation
Industry Solutions
Community Blog
Resource Center
What is the Presentation Layer, Anyway?

If you’ve ever heard the term “presentation layer” thrown around in discussions of computers or software, you may have been able to make a pretty good guess at what it is. In the world of robotic process automation (RPA) , the presentation layer becomes a major topic, so let’s take a minute to flesh it out.

In technical speech, the presentation layer is the sixth of seven layers of OSI code that translates data stored in another layer into something a human can interpret. It’s the presentation layer that knows to put the right information into the appropriate fields of a customer record, for example: Name, Date of Birth, Address, etc. The presentation layer is where you’ll find the code for making a program look nice as well. Most importantly to this discussion, the presentation layer is where RPA functions .
One of the main goals of RPA software is for it to behave just like a human being would in any situation. Since most human workers interact with data through the presentation layer of a software program, that’s what RPA robots do. This key component of RPA allows a business to keep its existing information systems while trying new things. You don’t need to overhaul everything in order to make new uses for the information you have.
With the presentation layer aspect of RPA, a company can gain a certain amount of technology independence . Your IT professionals are more important than ever, but RPA software like UiPath allows more people to interact with the data and the systems that make them better workers. An employee doesn’t have to wait for a “deep tech” solution if she can set up her own automation workflow. In addition, as existing systems get more and more out of date (though still vital to a company’s processes), there will be fewer and fewer computer programmers able to rework them. It’s similar to the idea that very few computer repair shops can fix a machine that runs floppy disks: the knowledge is simply lost over time. By using a presentation layer approach, you can cut that dependency and trust that any new IT hires will be able to keep pace.
There are other benefits to the RPA presentation layer approach, some of which are outlined in the 2011 Forrester report, “The Role of IT in Business-Driven Process Automation.” RPA’s ability to work with the presentation layer is, essentially, what makes it so useful in the world of automation.
Client Service Representative , Arts People
Related articles

UiPath named a Leader in Gartner® Magic Quadrant™ for six years in a row

UiPath named a Leader in Gartner® Magic Quadrant™ for five years in a row

Meet the first country in EMEA with an RPA Developer National Qualification
Get articles from automation experts in your inbox.
Sign up today and we'll email you the newest articles every week.
Thank you for subscribing!
Thank you for subscribing! Each week, we'll send the best automation blog posts straight to your inbox.
What is the presentation layer in the OSI model?
- Share on Facebook
- Share on Twitter
- Share on LinkedIn
The presentation layer is the sixth layer in the OSI model and is responsible for converting different file formats. This allows two systems to communicate. Other tasks carried out by the sixth layer include data compression and encryption.
What is the presentation layer?
The presentation layer is the sixth layer of the OSI model. It is primarily used to convert different file formats between the sender and the receiver . The OSI model is a reference model that is used to define communication standards between two devices within a network . The development of this standard began in the 1970s and it was officially published at the beginning of the following decade. This standard enables seamless interaction between different technical systems.
The model is made up of a total of seven different layers, all having their own clearly defined tasks. While there are clear boundaries between the layers, the layers interact with each other, with each layer building off the one below it. The different layers are as follows:
- Physical layer
- Data link layer
- Network layer
- Transport layer
- Session layer
- Presentation layer
- Application layer
What does the presentation layer do?
The presentation layer interacts closely with the application layer, which is located directly above it. The presentation layer’s main task is to present data in such a way that it can be understood and interpreted from both the system sending the data and the system receiving it. After this has been accomplished, the application layer then determines how the data should be structured and what sort of data and values are permissible.
Using these entries, a command set or an abstract transfer syntax is then automatically created. The presentation layer now has the task of transferring the data in such a way that it is readable without changing the information contained within it.
The presentation layer is often also responsible for the encryption and decryption of data . The information is first encrypted on the sender’s side and then sent to the receiver in an encrypted state. Keys and encryption methods are then exchanged in the presentation layer. The recipient is then able to decrypt the unreadable data and convert it into a format that can be understood and interpreted.
Which format does the presentation layer use?
If data is shown during a transfer, we often use the term transfer syntax. These are separated into the abstract transfer syntax , in which the transferred values are written, and the concrete syntax, which contains a definition of the value coding.
The receiver can only process and understand the data they receive if they receive all of the information from the presentation layer. The most common definition language is Abstract Syntax Notation One (ASN.1) , which is also recommended by the ISO. The ISO is an organisation that is responsible for developing international standards in technology, management and manufacturing.
The presentation layer has many different formats. The most common text formats are the ASCII (American Standard Code for Information Interchange) and EBCDIC (Extended Binary-Coded Decimal Interchange Code). The most common image formats are GIF, JPEG and TIFF. Widely used video formats include MIDI, MPEG and QuickTime.
Presentation layer protocols
There are many different presentation layer protocols as well as transfer and encryption technologies in the presentation layer. These include:
Skipping the presentation layer
The tasks which are carried out by the presentation layer are not always necessary for communication between two systems. In instances where both systems use the same formats, data conversion is not necessary. Additionally, encryption and compression are not required for every interaction and can also be carried out in another layer of the OSI model. If this is the case, the presentation layer can be skipped and the application layer (7) can communicate directly with the session layer (5) instead .
IONOS is the new price performance leader in cloud computing, as unveiled by Cloud Mercato in July 2024.
Computer Network
- Introduction
- Architecture
- Computer Network Types
- Transmission Modes
- TCP/IP Model
Physical Layer
- Digital Transmission
- Transmission Media
- Guided Media
- UnGuided Media
- Multiplexing
- Switching Modes
- Switching Techniques
- Data Link layer
- Error Detection
- Error Correction
- Data Link Controls
- Network Layer
- Network Addressing
- Network Layer Protocols
- Routing Algorithm
- Distance Vector
- Link State Routing
- Transport Layer
- Transport Layer Protocols
- Application Layer
- Client & Server Model
Application Protocols
Network security.
- Digital Signature
- What is Router
- OSI vs TCP/IP
- IPv4 vs IPv6
- ARP Packet Format
- Working of ARP
- FTP Commands
- I2P Protocol
- Sliding Window Protocol
- SPI Protocol
- ARP Commands
- ARP Request
- ARP - Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN Protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT Protocol
- OSPF Protocol
- Stop & Wait Protocol
- IMAP Protocol
- POP Protocol
- Go-Back-N ARQ
- Connection-Oriented vs Connectionless Service
- CDMA vs GSM
- What is MAC Address
- Modem vs Router
- Switch vs Router
- USB 2.0 vs USB 3.0
- CSMA CA vs CSMA CD
- Multiple Access Protocols
- IMAP vs. POP3
- SSH Meaning
- Status Code 400
- MIME Protocol
- What is a proxy server and how does it work
- How to set up and use a proxy server
- What is network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology vs Ring topology
- Bus topology vs Star topology
- Circuit Switching vs Packet switching
- star vs ring topology
- Router vs Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- ASA features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID) in Computer Network
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM) in Computer Network
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- How does BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Functions, Advantages and Disadvantages of the Physical Layer
- Types of Internet Connection
- Noisy and Noiseless Channel
- Advantages and Disadvantages of Bus Topology
- Advantages and Disadvantages of Ring Topology
- Advantages and Disadvantages of Star Topology
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security and Software security
- Information security and Network security
- Security Engineer and Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
- Difference Between Infrastructure and Infrastructure Less Network
- Collision Avoidance in Wireless Networks
- Difference Engine and Analytical Engine
- Hotspot 2.0
- Intrusion Prevention System (IPS)
- Modes of Connection Bluetooth
- Noisy Channel protocols
- Parzen Windows density Estimation Technique
- Principle of Information System Security
- What are Bots, Botnets, and Zombies
- Windows Memory Management
- Wireless dos attack on Wifi
- Design Principles of Security in Distributed Systems
- MAC Filtering
- Principles of Network Applications
- Time-to-Live (TTL)
- What is 1000 BASE-T
- What is the difference between 802.11ac and 802.11ax
- Differentiate between Circuit Switching, Message Switching, and Packet Switching
- What is Web 3.0
- Collision Detection in CSMA/CD
- Ipv4 Header in Computer Networks
- Layered Architecture in Computer Networks
- Define URL in Computer Networks
- MAN in Computer Networks
- Routing Protocols in Computer Networks
- Flooding in Computer Network
- CRC in Computer Network
- Application of Computer Network
- Computer Network Architect
- Design Issues for the Layers of Computer Networks
- What is AMD (Advanced Micro Devices)
- Protocol in Computer Network
- Computer Network Projects
- Different Types of Routers
- Wireless Distribution System (WDS)
- Network Time Protocol
- Address Resolution Protocol (ARP) and its types in Computer Network
- Automatic Repeat ReQuest (ARQ) in Computer Networks
- Bluetooth in Computer Networks
- Circuit Switching in Computer Network
- Computer Hardware and Networking Course
- Ring Topology in a Computer Network
- Token Ring in Computer Networks
- Medium Access Control in Computer Network
- Need for Computer Network
- Repeater in Computer Network
- Computer Networking: a Top Down Approach
- What is Multiplexing in Computer Network
- Body Area Network (BAN)
- INS AND OUT OF DATA STREAMING
- Streaming stored video
- Cellular Network
- How can devices on a Network be identified
- How Does the Internet Work
- Authentication Server
- What is Cloud Backup and How does it Work
- Communication Protocols In System Design
- Extensible Authentication Protocol (EAP)
- Role-Based Access Control (RBAC)
- Network Enumeration Tools
- Network Protocol Testing
- Windows Networking Commands
- Advantages and Disadvantages of WLAN
- Anonymous File Transfer Protocol (AFTP)
- Automatic Private IP Addressing
- What is Deep Web
- USB-C (USB Type C)
- User Authentication
- What is a vCard
- ipv4 Headers
- Difference between Token ring and Ethernet Token Ring
- Server Message Block protocol (SMB protocol)
- Session Border Controllers (SBC)
- Short Message Service Center (SMSC)
- What is a Mail Server
- What are Communication Networks
- Initialization Vector
- What is Fiber Optics
- Open Networking
- Access Ports Vs Trunk Ports
- Edge Routers
- IPTV (Internet Protocol Television)
- Wireless Internet Service Provider (WISP)
- Wireless Backhaul
- Define Protocol in Computer Network
- Virtual Network Adapter
- Virtual Routing and Forwarding
- Virtual Switches(vSwitches)
- VLAN (Virtual LAN)
- Wireless Mesh Network (WMN)
- What is Gateway in Computer Network
- Radio Access Network (RAN)
- What is File Sharing
- Passive Optical Network (PON)
- Private IP address
- Public Key Certificate
- What is Bridge in Computer Network
- Ping Sweep (ICMP Sweep)
- Print Server
- WIFI Pineapple
- Walled Garden
- Wireless ISP (wireless Internet service provider or WISP)
- Bridge vs Repeater
- Hardware Security Module (HSM)
- Public Switched Telephone Network
- Analog Telephone Adapter (ATA)
- Host Bus Adapter (HBA)
- ISCSI initiator
- Simplest Protocol
- Telecommunication Networks
- What is WPS in Wi-Fi
- What are the Most Important Email Security Protocols
- What is Data Governance and Why does it Matter
- Carrier Network
- Most Secure Network Protocol
- Network SMB
- BGP vs. EIGRP: What's the Difference
- Wireless Security: WEP, WPA, WPA2 and WPA3 differences
- Cloud Radio Access Network (C-RAN)
- Bits Per Second (bps or bit/sec)
- Blade Server
- command-and-control server (C&C server)
- Computer Network MCQ
- Computer Network MCQ Part2
Interview Questions
- Networking Questions
| The presentation layer is the 6 layer from the bottom in the OSI model. This layer presents the incoming data from the application layer of the sender machine to the receiver machine. It converts one format of data to another format of data if both sender and receiver understand different formats; hence this layer is also called the translation layer. It deals with the semantics and syntax of the data, so this layer is also called the syntax layer. It uses operations such as data compression, data encryption & decryption, data conversion, etc. Data is sent from sender to receiver, but what if the sender device and receiver device understand different formats of code? For example, suppose one device understands ASCII code and another device understands EBCDIC code. In that case, the data must be translated into a code that the recipient understands to determine what data has been sent. The presentation layer is responsible for translating ASCII codes to EBCDIC or vice versa. With the help of the presentation layer, the receiver understands the data effectively and uses it efficiently. Whatever data is being transmitted between the sender and the receiver, that data must be secure because an intruder can hack the data passing between the sender and the receiver. Hackers can modify the data and send the modified data to the receiver to create false communication. The presentation layer is responsible for encrypting and decrypting data to avoid data leakage and data modification.The plaintext data at the source is encrypted into ciphertext (unreadable format), then it is sent to the receiver, where the ciphertext is decrypted into plaintext. Now, if the hacker tries to hack the data, the hacker receives an encrypted, unreadable form, and if the hacker tries to send modified data, the receiver can detect the modification during decryption; thereby, the data remains safe. If the file size is large, it becomes difficult to transmit the large file over the network. File size can be decreased by compressing the file for easy transmission of data. Compression is the method of diminishing the size of a file to transmit data easily in less time. When the compressed data reaches the receiver, the data is reconstructed back to the original size, and this process is called decompression. The presentation layer in the OSI model is classified into two sublayers: This sublayer offers services to layer-7, i.e., the application layer, and requests services from layer-5, i.e., the session layer. It supports various application services, such as Reliable Transfer Service Element (RTSE), Remote Operation Service Element (ROSE), Association Control Service Element (ACSE), and Commitment Concurrency and Recovery (CCR). This sublayer offers application-specific protocols, such as Message Oriented Text Interchange Standard (MOTIS), Remote Database Access (RDA), File Transfer Access and Manager (FTAM), Common Management Information Protocol (CMIP), Virtual Terminal (VT), Distributed Transaction Processing (DTP), Job Transfer and Manipulation (JTM), and others. It is a presentation layer protocol in the OSI model, which was formed by Citrix Systems. It is used for transferring data from server to client. It is a very thin protocol as it does not require much overhead in order to transmit data from the server over to the client. It is well-optimized for the WAN. It is the protocol that is used to implement the presentation layer of the OSI model. It provides different kinds of data representation, such as images, video, audio, numbers, etc. It is used for Microsoft Remote Procedure Call (Microsoft RPC) and Distributed Computing Environment (DCE) / Remote Procedure Calls (RPC). It is a communication protocol that was specifically designed for macOS by Apple, Inc. It provides file services for Classic Mac OS and macOS. This protocol is used to share files over the network. It is a protocol that is associated with the client-server operating system. The user can access the directory, print, message, file, clock synchronization, etc., with the help of this protocol. It supports many platforms, such as Linux, Classic Mac OS, Windows NT, Mac OS X, and Microsoft Windows. It is a telecommunications equipment that splits a stream of data into separate packets and formats packet headers for asynchronous communication on X.25 networks. It receives packets from the network and converts them into a stream of data. The PAD provides many asynchronous terminal connectivities to a host computer. It is a computer network protocol that is used to transfer data between two systems. It was first published in 1987. XDR is used by various systems such as NDMP, Network File System, NetCDF, ZFS, Open Network Computer Remote Procedure Call, and others. It is a protocol that offers ISO presentation services over TCP/IP based networks. This protocol explains an approach to provide stream-line support for OSI over TCP/IP based networks. |
Latest Courses

We provides tutorials and interview questions of all technology like java tutorial, android, java frameworks
Contact info
G-13, 2nd Floor, Sec-3, Noida, UP, 201301, India
[email protected] .

Online Compiler
Application Architecture Guide - Chapter 10 - Presentation Layer Guidelines
Note - The patterns & practices Microsoft Application Architecture Guide, 2nd Edition is now live at http://msdn.microsoft.com/en-us/library/dd673617.aspx .
- J.D. Meier, Alex Homer, David Hill, Jason Taylor, Prashant Bansode, Lonnie Wall, Rob Boucher Jr, Akshay Bogawat
- 1 Objectives
- 3 Presentation Layer Components
- 5 Design Considerations
- 6 Presentation Layer Frame
- 8 Composition
- 9 Exception Management
- 12 Navigation
- 13 Presentation Entities
- 14 Request Processing
- 15 User Experience
- 16 UI Components
- 17 UI Process Components
- 18 Validation
- 19 Pattern Map
- 20 Pattern Descriptions
- 21.1 Mobile Applications
- 21.2 Rich Client Applications
- 21.3 Rich Internet Applications (RIA)
- 21.4 Web Applications
- 22 patterns & practices Solution Assets
- 23 Additional Resources
- Understand how the presentation layer fits into typical application architecture.
- Understand the components of the presentation layer.
- Learn the steps for designing the presentation layer.
- Learn the common issues faced while designing the presentation layer.
- Learn the key guidelines for designing the presentation layer.
- Learn the key patterns and technology considerations for designing the presentation layer.
The presentation layer contains the components that implement and display the user interface and manage user interaction. This layer includes controls for user input and display, in addition to components that organize user interaction. Figure 1 shows how the presentation layer fits into a common application architecture.

Figure 1 A typical application showing the presentation layer and the components it may contain
Presentation Layer Components
- User interface (UI) components . User interface components provide a way for users to interact with the application. They render and format data for users. They also acquire and validate data input by the user.
- User process components . User process components synchronize and orchestrate user interactions. Separate user process components may be useful if you have a complicated UI. Implementing common user interaction patterns as separate user process components allows you to reuse them in multiple UIs.
The following steps describe the process you should adopt when designing the presentation layer for your application. This approach will ensure that you consider all of the relevant factors as you develop your architecture:
- Identify your client type . Choose a client type that satisfies your requirements and adheres to the infrastructure and deployment constraints of your organization. For instance, if your users are on mobile devices and will be intermittently connected to the network, a mobile rich client is probably your best choice.
- Determine how you will present data . Choose the data format for your presentation layer and decide how you will present the data in your UI.
- Determine your data-validation strategy . Use data-validation techniques to protect your system from untrusted input.
- Determine your business logic strategy . Factor out your business logic to decouple it from your presentation layer code.
- Determine your strategy for communication with other layers . If your application has multiple layers, such as a data access layer and a business layer, determine a strategy for communication between your presentation layer and other layers.
Design Considerations
There are several key factors that you should consider when designing your presentation layer. Use the following principles to ensure that your design meets the requirements for your application, and follows best practices:
- Choose the appropriate UI technology. Determine if you will implement a rich (smart) client, a Web client, or a rich Internet application (RIA). Base your decision on application requirements, and on organizational and infrastructure constraints.
- Use the relevant patterns. Review the presentation layer patterns for proven solutions to common presentation problems.
- Design for separation of concerns. Use dedicated UI components that focus on rendering and display. Use dedicated presentation entities to manage the data required to present your views. Use dedicated UI process components to manage the processing of user interaction.
- Consider human interface guidelines. Review your organization’s guidelines for UI design. Review established UI guidelines based on the client type and technologies that you have chosen.
- Adhere to user-driven design principles. Before designing your presentation layer, understand your customer. Use surveys, usability studies, and interviews to determine the best presentation design to meet your customer’s requirements.
Presentation Layer Frame
There are several common issues that you must consider as your develop your design. These issues can be categorized into specific areas of the design. The following table lists the common issues for each category where mistakes are most often made.
Table 1 Presentation Layer Frame
| * Caching volatile data. | |
| * Failing to consider use of patterns and libraries that support dynamic layout and injection of views and presentation at runtime. | |
| * Failing to catch unhandled exceptions. | |
| * Failing to design for intuitive use, or implementing overly complex interfaces. | |
| * Using an inappropriate layout style for Web pages. | |
| * Inconsistent navigation. | |
| * Defining entities that are not necessary. | |
| * Blocking the UI during long-running requests. | |
| * Displaying unhelpful error messages. | |
| * Creating custom components that are not necessary. | |
| * Implementing UI process components when not necessary. | |
| * Failing to validate all input. |
Caching is one of the best mechanisms you can use to improve application performance and UI responsiveness. Use data caching to optimize data lookups and avoid network round trips. Cache the results of expensive or repetitive processes to avoid unnecessary duplicate processing.
Consider the following guidelines when designing your caching strategy:
- Do not cache volatile data.
- Consider using ready-to-use cache data when working with an in-memory cache. For example, use a specific object instead of caching raw database data.
- Do not cache sensitive data unless you encrypt it.
- If your application is deployed in Web farm, avoid using local caches that need to be synchronized; instead, consider using a transactional resource manager such as Microsoft SQL Server® or a product that supports distributed caching.
- Do not depend on data still being in your cache. It may have been removed.
Composition
Consider whether your application will be easier to develop and maintain if the presentation layer uses independent modules and views that are easily composed at run time. Composition patterns support the creation of views and the presentation layout at run time. These patterns also help to minimize code and library dependencies that would otherwise force recompilation and redeployment of a module when the dependencies change. Composition patterns help you to implement sharing, reuse, and replacement of presentation logic and views.
Consider the following guidelines when designing your composition strategy:
- Avoid using dynamic layouts. They can be difficult to load and maintain.
- Be careful with dependencies between components. For example, use abstraction patterns when possible to avoid issues with maintainability.
- Consider creating templates with placeholders. For example, use the Template View pattern to compose dynamic Web pages in order to ensure reuse and consistency.
- Consider composing views from reusable modular parts. For example, use the Composite View pattern to build a view from modular, atomic component parts.
- If you need to allow communication between presentation components, consider implementing the Publish/Subscribe pattern. This will lower the coupling between the components and improve testability.
Exception Management
Design a centralized exception-management mechanism for your application that catches and throws exceptions consistently. Pay particular attention to exceptions that propagate across layer or tier boundaries, as well as exceptions that cross trust boundaries. Design for unhandled exceptions so they do not impact application reliability or expose sensitive information.
Consider the following guidelines when designing your exception management strategy:
- Use user-friendly error messages to notify users of errors in the application.
- Avoid exposing sensitive data in error pages, error messages, log files, and audit files.
- Design a global exception handler that displays a global error page or an error message for all unhandled exceptions.
- Differentiate between system exceptions and business errors. In the case of business errors, display a user-friendly error message and allow the user to retry the operation. In the case of system exceptions, check to see if the exception was caused by issues such as system or database failure, display a user-friendly error message, and log the error message, which will help in troubleshooting.
- Avoid using exceptions to control application logic.
Design a user input strategy based on your application input requirements. For maximum usability, follow the established guidelines defined in your organization, and the many established industry usability guidelines based on years of user research into input design and mechanisms.
Consider the following guidelines when designing your input collection strategy:
- Use forms-based input controls for normal data-collection tasks.
- Use a document-based input mechanism for collecting input in Microsoft Office–style documents.
- Implement a wizard-based approach for more complex data collection tasks, or for input that requires a workflow.
- Design to support localization by avoiding hard-coded strings and using external resources for text and layout.
- Consider accessibility in your design. You should consider users with disabilities when designing your input strategy; for example, implement text-to-speech software for blind users, or enlarge text and images for users with poor sight. Support keyboard-only scenarios where possible for users who cannot manipulate a pointing device.
Design your UI layout so that the layout mechanism itself is separate from the individual UI components and UI process components. When choosing a layout strategy, consider whether you will have a separate team of designers building the layout, or whether the development team will create the UI. If designers will be creating the UI, choose a layout approach that does not require code or the use of development-focused tools.
Consider the following guidelines when designing your layout strategy:
- Use templates to provide a common look and feel to all of the UI screens.
- Use a common look and feel for all elements of your UI to maximize accessibility and ease of use.
- Consider device-dependent input, such as touch screens, ink, or speech, in your layout. For example, with touch-screen input you will typically use larger buttons with more spacing between them than you would with mouse or keyboard inputs.
- When building a Web application, consider using Cascading Style Sheets (CSS) for layout. This will improve rendering performance and maintainability.
- Use design patterns, such as Model-View-Presenter (MVP), to separate the layout design from interface processing.
Design your navigation strategy so that users can navigate easily through your screens or pages, and so that you can separate navigation from presentation and UI processing. Ensure that you display navigation links and controls in a consistent way throughout your application to reduce user confusion and hide application complexity.
Consider the following guidelines when designing your navigation strategy:
- Use well-known design patterns to decouple the UI from the navigation logic where this logic is complex.
- Design toolbars and menus to help users find functionality provided by the UI.
- Consider using wizards to implement navigation between forms in a predictable way.
- Determine how you will preserve navigation state if the application must preserve this state between sessions.
- Consider using the Command Pattern to handle common actions from multiple sources.
Presentation Entities
Use presentation entities to store the data you will use in your presentation layer to manage your views. Presentation entities are not always necessary; use them only if your datasets are sufficiently large and complex to require separate storage from the UI controls.
Consider the following guidelines when designing presentation entities:
- Determine if you require presentation entities. Typically, you may require presentation entities only if the data or the format to be displayed is specific to the presentation layer.
- If you are working with data-bound controls, consider using custom objects, collections, or datasets as your presentation entity format.
- If you want to map data directly to business entities, use a custom class for your presentation entities.
- Do not add business logic to presentation entities.
- If you need to perform data type validation, consider adding it in your presentation entities.
Request Processing
Design your request processing with user responsiveness in mind, as well as code maintainability and testability.
Consider the following guidelines when designing request processing:
- Use asynchronous operations or worker threads to avoid blocking the UI for long-running actions.
- Avoid mixing your UI processing and rendering logic.
- Consider using the Passive View pattern (a variant of MVP) for interfaces that do not manage a lot of data.
- Consider using the Supervising Controller pattern (a variant of MVP) for interfaces that manage large amounts of data.
User Experience
Good user experience can make the difference between a usable and unusable application. Carry out usability studies, surveys, and interviews to understand what users require and expect from your application, and design with these results in mind.
Consider the following guidelines when designing for user experience:
- When developing a rich Internet application (RIA), avoid synchronous processing where possible.
- When developing a Web application, consider using Asynchronous JavaScript and XML (AJAX) to improve responsiveness and to reduce post backs and page reloads.
- Do not design overloaded or overly complex interfaces. Provide a clear path through the application for each key user scenario.
- Design to support user personalization, localization, and accessibility.
- Design for user empowerment. Allow the user to control how he or she interacts with the application, and how it displays data to them.
UI Components
UI components are the controls and components used to display information to the user and accept user input. Be careful not to create custom controls unless it is necessary for specialized display or data collection.
Consider the following guidelines when designing UI components:
- Take advantage of the data-binding features of the controls you use in the UI.
- Create custom controls or use third-party controls only for specialized display and data-collection tasks.
- When creating custom controls, extend existing controls if possible instead of creating a new control.
- Consider implementing designer support for custom controls to make it easier to develop with them.
- Consider maintaining the state of controls as the user interacts with the application instead of reloading controls with each action.
UI Process Components
UI process components synchronize and orchestrate user interactions. UI processing components are not always necessary; create them only if you need to perform significant processing in the presentation layer that must be separated from the UI controls. Be careful not to mix business and display logic within the process components; they should be focused on organizing user interactions with your UI.
Consider the following guidelines when designing UI processing components:
- Do not create UI process components unless you need them.
- If your UI requires complex processing or needs to talk to other layers, use UI process components to decouple this processing from the UI.
- Consider dividing UI processing into three distinct roles: Model, View, and Controller/Presenter, by using the MVC or MVP pattern.
- Avoid business rules, with the exception of input and data validation, in UI processing components.
- Consider using abstraction patterns, such as dependency inversion, when UI processing behavior needs to change based on the run-time environment.
- Where the UI requires complex workflow support, create separate workflow components that use a workflow system such as Windows Workflow or a custom mechanism.
Designing an effective input and data-validation strategy is critical to the security of your application. Determine the validation rules for user input as well as for business rules that exist in the presentation layer.
Consider the following guidelines when designing your input and data validation strategy:
- Validate all input data on the client side where possible to improve interactivity and reduce errors caused by invalid data.
- Do not rely on client-side validation only. Always use server-side validation to constrain input for security purposes and to make security-related decisions.
- Design your validation strategy to constrain, reject, and sanitize malicious input.
- Use the built-in validation controls where possible, when working with .NET Framework.
- In Web applications, consider using AJAX to provide real-time validation.
Pattern Map
Key patterns are organized by key categories, as detailed in the Presentation Layer Frame in the following table. Consider using these patterns when making design decisions for each category.
Table 2 Pattern Map
| * Cache Dependency | |
| * Composite View | |
| * Exception Shielding | |
| * Template View | |
| * Front Controller | |
| * Entity Translator | |
| * Asynchronous Callback | |
| * Model-View-Controller (MVC) |
- For more information on the Page Cache pattern, see “Enterprise Solution Patterns Using Microsoft .NET” at http://msdn.microsoft.com/en-us/library/ms998469.aspx
- For more information on the Model-View-Controller (MVC), Page Controller, Front Controller, Template View, Transform View, and Two-Step View patterns, see “Patterns of Enterprise Application Architecture (P of EAA)” at http://martinfowler.com/eaaCatalog/
- For more information on the Composite View, Supervising Controller, and Presentation Model patterns, see “Patterns in the Composite Application Library” at http://msdn.microsoft.com/en-us/library/cc707841.aspx
- For more information on the Chain of responsibility and Command pattern, see “data & object factory” at http://www.dofactory.com/Patterns/Patterns.aspx
- For more information on the Asynchronous Callback pattern, see “Creating a Simplified Asynchronous Call Pattern for Windows Forms Applications” at http://msdn.microsoft.com/en-us/library/ms996483.aspx
- For more information on the Exception Shielding and Entity Translator patterns, see “Useful Patterns for Services” at http://msdn.microsoft.com/en-us/library/cc304800.aspx
Pattern Descriptions
- Asynchronous Callback. Execute long-running tasks on a separate thread that executes in the background, and provide a function for the thread to call back into when the task is complete.
- Cache Dependency. Use external information to determine the state of data stored in a cache.
- Chain of Responsibility. Avoid coupling the sender of a request to its receiver by giving more than one object a chance to handle the request.
- Composite View . Combine individual views into a composite representation.
- Command Pattern. Encapsulate request processing in a separate command object with a common execution interface.
- Entity Translator. An object that transforms message data types into business types for requests, and reverses the transformation for responses.
- Exception Shielding. Prevent a service from exposing information about its internal implementation when an exception occurs.
- Front Controller . Consolidate request handling by channeling all requests through a single handler object, which can be modified at run time with decorators.
- Model-View-Controller . Separate the UI code into three separate units: Model (data), View (interface), and Presenter (processing logic), with a focus on the View. Two variations on this pattern include Passive View and Supervising Controller, which define how the View interacts with the Model.
- Page Cache. Improve the response time for dynamic Web pages that are accessed frequently but change less often and consume a large amount of system resources to construct.
- Page Controller . Accept input from the request and handle it for a specific page or action on a Web site.
- Passive View . Reduce the view to the absolute minimum by allowing the controller to process user input and maintain the responsibility for updating the view.
- Presentation Model . Move all view logic and state out of the view, and render the view through data-binding and templates.
- Supervising Controller . A variation of the MVC pattern in which the controller handles complex logic, in particular coordinating between views, but the view is responsible for simple view-specific logic.
- Template View . Implement a common template view, and derive or construct views using this template view.
- Transform View . Transform the data passed to the presentation tier into HTML for display in the UI.
- Two-Step View . Transform the model data into a logical presentation without any specific formatting, and then convert that logical presentation to add the actual formatting required.
Technology Considerations
The following guidelines will help you to choose an appropriate implementation technology. The guidelines also contain suggestions for common patterns that are useful for specific types of application and technology.
Mobile Applications
Consider the following guidelines when designing a mobile application:
- If you want to build full-featured connected, occasionally connected, and disconnected executable applications that run on a wide range of Microsoft Windows®–based devices, consider using the Microsoft Windows Compact Framework.
- If you want to build connected applications that require Wireless Application Protocol (WAP), compact HTML (cHTML), or similar rendering formats, consider using ASP.NET Mobile Forms and Mobile Controls.
- If you want to build applications that support rich media and interactivity, consider using Microsoft Silverlight® for Mobile.
Rich Client Applications
Consider the following guidelines when designing a rich client application:
- If you want to build applications with good performance and interactivity, and have design support in Microsoft Visual Studio®, consider using Windows Forms.
- If you want to build applications that fully support rich media and graphics, consider using Windows Presentation Foundation (WPF).
- If you want to build applications that are downloaded from a Web server and then execute on the client, consider using XAML Browser Applications (XBAP).
- If you want to build applications that are predominantly document-based, or are used for reporting, consider designing a Microsoft Office Business Application.
- If you decide to use Windows Forms and you are designing composite interfaces, consider using the Smart Client Software Factory.
- If you decide to use WPF and you are designing composite interfaces, consider using the Composite Application Guidance for WPF.
- If you decide to use WPF, consider using the Presentation Model (Model-View-ViewModel) pattern.
- If you decide to use WPF, consider using WPF Commands to communicate between your View and your Presenter or ViewModel.
- If you decide to use WPF, consider implementing the Presentation Model pattern by using DataTemplates over User Controls to give designers more control.
Rich Internet Applications (RIA)
Consider the following guidelines when designing an RIA:
- If you want to build browser-based, connected applications that have broad cross-platform reach, are highly graphical, and support rich media and presentation features, consider using Silverlight.
- If you decide to use Silverlight, consider using the Presentation Model (Model-View-ViewModel) pattern.
Web Applications
Consider the following guidelines when designing a Web application:
- If you want to build applications that are accessed through a Web browser or specialist user agent, consider using ASP.NET.
- If you want to build applications that provide increased interactivity and background processing, with fewer page reloads, consider using ASP.NET with AJAX.
- If you want to build applications that include islands of rich media content and interactivity, consider using ASP.NET with Silverlight controls.
- If you are using ASP.NET and want to implement a control-centric model with separate controllers and improved testability, consider using the ASP.NET MVC Framework.
- If you are using ASP.NET, consider using master pages to simplify development and implement a consistent UI across all pages.
patterns & practices Solution Assets
- Web Client Software Factory at http://msdn.microsoft.com/en-us/library/bb264518.aspx
- Smart Client Software Factory at http://msdn.microsoft.com/en-us/library/aa480482.aspx
- Composite Application Guidance for WPF at http://msdn.microsoft.com/en-us/library/cc707819.aspx
- Smart Client - Composite UI Application Block at http://msdn.microsoft.com/en-us/library/aa480450.aspx
Additional Resources
- For more information, see Microsoft Inductive User Interface Guidelines at http://msdn.microsoft.com/en-us/library/ms997506.aspx .
- For more information, see User Interface Control Guidelines at http://msdn.microsoft.com/en-us/library/bb158625.aspx .
- For more information, see User Interface Text Guidelines at http://msdn.microsoft.com/en-us/library/bb158574.aspx .
- For more information, see Design and Implementation Guidelines for Web Clients at http://msdn.microsoft.com/en-us/library/ms978631.aspx .
- For more information, see Web Presentation Patterns at http://msdn.microsoft.com/en-us/library/ms998516.aspx .
Navigation menu
Page actions.
- View source
Personal tools
- Community portal
- Current events
- Recent changes
- Random page
- What links here
- Related changes
- Special pages
- Printable version
- Permanent link
- Page information
- This page was last edited on 22 January 2010, at 07:50.
- Privacy policy
- About Guidance Share
- Disclaimers

IMAGES
VIDEO
COMMENTS
The presentation layer is layer 6 of the 7-layer Open Systems Interconnection (OSI) model. It is used to present data to the application layer (layer 7) in an accurate, well-defined and standardized format. The presentation layer is sometimes called the syntax layer. Techopedia Explains Presentation Layer. The presentation layer is responsible ...
Prerequisite : OSI Model Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network.
The presentation layer resides at Layer 6 of the Open Systems Interconnection (OSI) communications model and ensures that communications that pass through it are in the appropriate form for the recipient application. In other words, the presentation layer presents the data in a readable format from an application layer perspective.
The presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. On the sending system it is responsible for conversion to standard, transmittable formats. [7] On the receiving system it is responsible for the translation, formatting, and delivery of ...
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified ...
What is Presentation Layer. Definition: Presentation layer is 6th layer in the OSI model, and its main objective is to present all messages to upper layer as a standardized format.It is also known as the "Translation layer". This layer takes care of syntax and semantics of messages exchanged in between two communication systems.
Presentation Layer. The Presentation Layer is the sixth layer in the OSI model. It sits right above the Session Layer and below the Application Layer. Its main job is to handle how data is presented to the application. In other words, it ensures that the data is in a format that both the sending and receiving systems can understand.
The Presentation Layer, within the OSI (Open Systems Interconnection) model, is the sixth layer. It focuses on the representation of data, ensuring that information exchanged between applications is formatted appropriately for transmission and receipt across a network. This layer handles tasks such as data translation, encryption, compression ...
The presentation layer is a very important layer because it handles encryption, decryption, and the conversion of complex data into flat-byte strings, a format that is easily transmittable. The ...
OSI uses three layers -- application, presentation and session -- to define the functionality of upper layers, while TCP/IP uses only the application layer. OSI uses two separate layers -- physical and data-link -- to define the functionality of the bottom layers, while TCP/IP uses only the link layer.
Understanding the layers of the Open Systems Interconnect (OSI) model can help users conceptualize data communication over a network. Layer 6 in the OSI model - the presentation layer - translates, compresses, and encrypts data across networks. In this article, we'll explain what the presentation layer is, how it works, and its functions and protocols.
Functionalities of the Presentation Layer. Specific functionalities of the presentation layer are as follows: 1. Translation. The processes or running programs in two machines are usually exchanging the information in the form of numbers, character strings and so on before being transmitted. The information should be changed to bitstreams ...
OSI: Layer 6 - Presentation. The presentation layer is the sixth layer (layer 6) of the seven-layer OSI model. The presentation layer is responsible for the delivery and formatting of information to the application layer for further processing or presentation to the user. It relieves the application layer from the responsibility in data ...
The presentation layer is one of the three main layers in object-oriented programming. The three main layers include: Presentation Layer. Business Layer. Data Layer. Now, these three layers are typically related to enterprise web applications. It's a design pattern used to help separate your code out in three distinct areas that (if need be ...
In subject area: Computer Science. The Presentation Layer in the OSI model is defined as the layer that enables interaction between different application layer implementations by translating data formats and languages to facilitate communication. AI generated definition based on: Security for Microsoft Windows System Administrators, 2011.
Here are five main layers in software architecture: 1. Presentation layer. The presentation layer, also called the UI layer, handles the interactions that users have with the software. It's the most visible layer and defines the application's overall look and presentation to the end-users.
In technical speech, the presentation layer is the sixth of seven layers of OSI code that translates data stored in another layer into something a human can interpret. It's the presentation layer that knows to put the right information into the appropriate fields of a customer record, for example: Name, Date of Birth, Address, etc.
The presentation layer is the sixth layer of the Open Systems Interconnection (OSI), model. In computer networking, the OSI model is a concept that describes the transmission of data from one computer to another. Each layer in the model is a packet of protocols, or procedures that govern data transmission, which allow the layer to execute ...
The presentation layer is the sixth layer of the OSI model. It is primarily used to convert different file formats between the sender and the receiver. The OSI model is a reference model that is used to define communication standards between two devices within a network. The development of this standard began in the 1970s and it was officially ...
The presentation layer is the 6 th layer from the bottom in the OSI model. This layer presents the incoming data from the application layer of the sender machine to the receiver machine. It converts one format of data to another format of data if both sender and receiver understand different formats; hence this layer is also called the ...
Overview. The presentation layer contains the components that implement and display the user interface and manage user interaction. This layer includes controls for user input and display, in addition to components that organize user interaction. Figure 1 shows how the presentation layer fits into a common application architecture.
Presentation layer definition. The presentation layer is the sixth layer in the Open System Interconnection (OSI) model. It serves as the data translator for the network — it takes data formats from different sources and presents it to the application layer in an accurate, well-defined, and standardized manner. Real presentation layer functions